Nmap for Pentester: Output Format Scan
Nmap which is also known as Network Mapper is one of the best open-source and the handiest tool that is widely used for security auditing and network scanning by pentesters. It also provides an additional feature where the results of a network scan can be recorded in various formats.
Table of Contents
- Introduction- Scan Output Formats
- Nmap Scan Report in Normal Format
- Nmap Scan Report in XML Format
- Nmap scan Report in a Grepable Format
- Nmap Scan Report in Alias Format
Introduction- Scan Output Formats
Pentesters sometimes notice that it becomes troublesome to come up with reports in an explicit format where conducting network scans in giant organizations is extremely tedious. Many organizations make a huge mistake by not using the right set of tools to prepare the report for the output that is derived from the scans.
The Nmap tool has the capability to prepare scan results in various formats which gives the pentester multiple options like generating an HTML page, CSV formats, scripting language etc. So let us explore all the scan output options provided by nmap and look at how useful it can be to any organization depending on their need.
Nmap Scan Report in Normal Format
-oN <filespec>
In this format of the scan output, it requests that a normal output is directed to a particular filename. This option can be used to combine with any port or host scanning technique as per the need of the pen tester. The various combinations of the output scans have been demonstrated ahead in the article.
Creating a Normal Nmap report in a simple text format:
nmap -oN scan.txt 192.168.1.108

If a pentester wants to create the scan reports in Normal as well as XML form in a combination.:
nmap -oN scan.txt -oX scan.xml 192.168.1.108

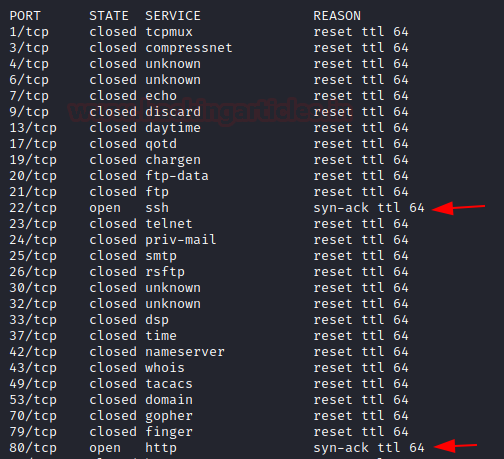
Here you see that the port numbers, the state of the ports and the type of the packet that determined the state of the port or the host.

Verbosity mode
To increase the level of verbosity for printing more information about the scan . In this scan details like open ports, estimated time of completion, etc are highlighted.
This mode is used twice or more for better verbosity: -vv, or give a verbosity level directly, like -vv, v2, v3.
nmap -vv -oN scan.txt 192.168.1.108

Debugging mode
Debugging mode is generally used when the verbose mode doesn’t provide enough details about the scan, so it digs deeper into the scanning process. The level of debug can be increased by specifying its number. Here you get details like the flags [resent in the packets, the time-to-live etc.
nmap -d2 -oN scan.txt 192.168.1.108

Another such command:
nmap -dd -oN scan.txt 192.168.1.108


Nmap Scan Report in XML Format
-oX <filespec>
It stands for Extensible Markup Language which is a tree-structured file format that is supported by Nmap.
The results from the Nmap scan can be exported into an XML file and can be further used for analysis or another additional task.
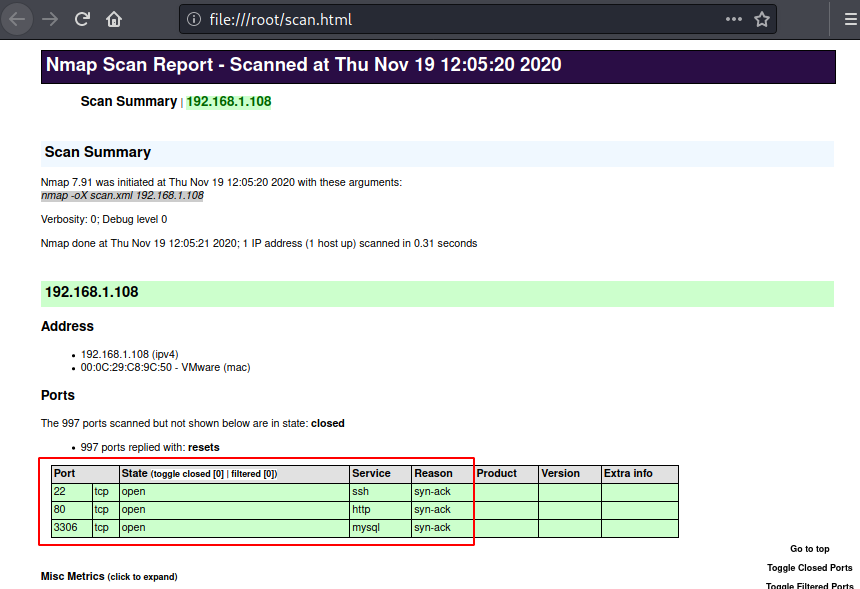
When an XML report is generated, it contains information like an executed command, Host and port states, Nmap Scripting Engine output Services, Timestamps, Run statistics and debugging information.
nmap -oX scan.xml 192.168.1.108

Sometimes, Pentesters prefer getting an html stylesheet as their report as it gives much-organised scan results:
nmap -oX scan.xml --stylesheet=nmap.xsl 192.168.1.108 xsltproc scan.xml -o scan.html firefox scan.html

Appending the output
Nmap by default overwrites logfiles by using any output options. We can use the append option to append the results instead of overwriting them:
nmap --append-output -sV -oN scan.txt 192.168.1.108

Nmap Scan Report in a grepable format
-oG <filespec>
Nmap has different file formats to save the results of a scan. Depending on the needs of the pentester the different formats like the normal, grepable, and XML format can be chosen. The grepable format has been included to help pentester extract information from logs without having the need to write a parser, as this format is meant to be read/parsed with standard Unix tools. It helps in finishing up the scan really quickly.
nmap -oG scan.grep 192.168.1.108 cat scan.grep

Nmap Scan Report in Alias format
-oA <filespec>
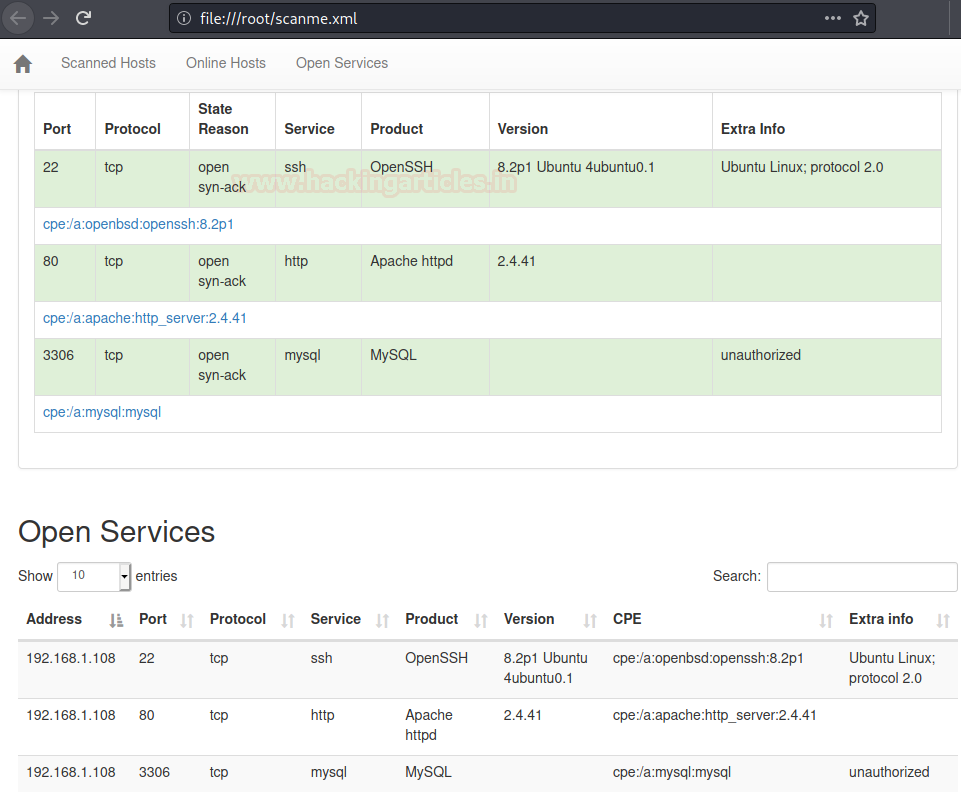
Nmap scan has the alias option which saves the scan results in all the formats. The files will be generated with the extensions .nmap, .xml, and .grep.
nmap -sV -oA scanme --stylesheet https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/master/nmap-bootstrap.xsl 192.168.1.108

nmap -oA scan 192.168.1.108


Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here