Multiple Ways to Detect HTTP Options
Hi Friends, today we will walk through various HTTP Protocol methods and the tools used to extract those available HTTP methods in a web server. As we are already aware, the HTTP protocol includes several methods that can not only gather information from the web server but can also perform specific actions on the web server. These techniques and methods are helpful for web application developers in the deployment and testing stage of web applications.
Common HTTP Methods Overview
GET and POST are the most well-known methods that users employ to access and submit information provided by a web server, respectively. The HTTP Protocol allows various other methods as well, like PUT, CONNECT, TRACE, HEAD, and DELETE. If someone leaves a misconfigured web server unattended. Malicious actors can use these methods for harmful purposes. This poses a major security risk for the web application. As this could enable an attacker to modify the files stored on the web server.
OPTIONS: The OPTIONS method is used to request the available HTTP methods on a web server.
GET: GET request is the most common and widely used method for websites. This method retrieves the data from the web server for a specific resource. As the GET method only requests the data and doesn’t modify the content of any resources, it’s considered to be safe.
POST: POST requests allow users to send (or submit) data to the web server to create or update a resource. The request body of the HTTP request stores the information sent and allows for further processing. An example illustrating this is the “Contact us” form page on a website. When we fill a form and submit it, the application stores the input data in the response body of the request and sends it across to the server.
Potentially Dangerous HTTP Methods
PUT: The PUT method allows the end-user (client) to upload new files on the web server. An attacker can exploit it by uploading malicious files or by using the victim’s server as a file repository.
CONNECT: The CONNECT method could allow a client to use the web server as a proxy.
TRACE: This method echoes back to the client the same string that the server has sent across and mainly uses it for debugging purposes.
HEAD: The HEAD method is almost similar to GET, however, without the message body in the response. In other words, if the HTTP request GET /products returns a list of products, then the HEAD /products will trigger a similar HTTP request, however, it won’t retrieve the list of products.
DELETE: This method enables a client to delete a file on the web server. An attacker can exploit it as a very simple and direct way to deface a web site or to perform a DoS attack.
Now, let us use some tools to identify the HTTP methods enabled or supported by the web server
Metasploit
Metasploit Framework is a well-known platform for developing, testing, and executing exploits. It is an open-source tool for performing various exploits against the target machines.
Metasploit has in-built auxiliary modules dedicated to scanning HTTP methods. Through the Metasploit framework command line (CLI), we can identify the HTTP Options available on the target URL as follows:
use auxiliary/scanner/http/options set rhosts 192.168.1.109 set rport 80 exploit

cURL
cURL is a command-line tool to get or send data using the URL syntax. Additionally, it is compatible with various well-known protocols (HTTPS, FTP, SCP, LDAP, Telnet, etc.) along with command line (CLI) options for performing various tasks (Eg: User authentication, FTP uploading, SSL connections etc). The cURL utility by default comes installed in most of the distributions. However, if in case, cURL is not installed, then we can install the same via apt-get install curl command. For more details, refer to the below URL
Through the cURL command, we can identify the HTTP Options available on the target URL as follows :
curl -v -X OPTIONS http://192.168.1.109
The various types of allowed HTTP methods (GET, HEAD, POST, OPTIONS, TRACE) are displayed in the screenshot, along with other server-specific information (Server response, version details, etc).

Nikto
Nikto is a Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software and other issues. It performs generic and server types of specific checks.
Through the Nikto command we can identify the HTTP Options available on the target URL as follows :
nikto -h 192.168.1.109
The screenshot displays the various types of allowed HTTP methods (GET, HEAD, POST, OPTIONS, TRACE), apart from other detailed server-specific information (Server response, version details etc)

Nmap
Nmap is a free and open-source security scanner used to discover hosts and services on the network. This is another method of checking which HTTP methods are enabled by using an NMAP script called http-methods.nse.nse. It can be obtained from https://nmap.org/nsedoc/scripts/http-methods.html.
Let us use the NMAP command to enumerate all of the HTTP methods supported by a web server on the target URL as follows :
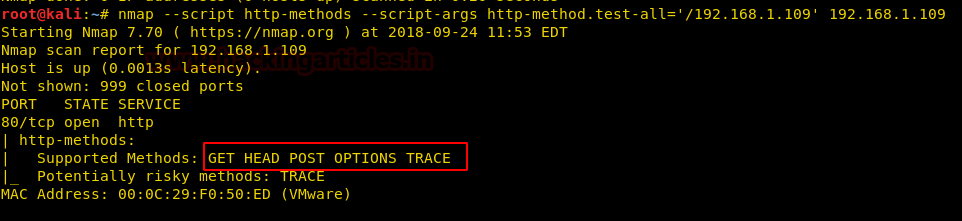
nmap --script http-methods --script-args http-method.test-all ='/192.168.1.109' 192.168.1.109
The screenshot displays the various types of allowed HTTP methods (GET, HEAD, POST, OPTIONS, TRACE) along with highlighting the potential risk methods (i.e, TRACE) among them.
Netcat
Netcat is a utility tool that can write and read data across TCP and UDP network connections. Additionally, along with features like built-in port scanning, network debugging, and file transfer, etc.
Through the Netcat command, we can identify the HTTP Options available on the target URL as follows :
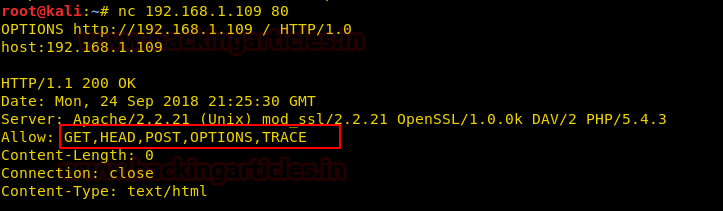
nc 192.168.1.109 80
Press Enter, and the following options appear in the command line. Enter the server details as follows (and as highlighted in red )
OPTIONS http://192.168.1.109 / HTTP/1.0 host:192.168.1.109
The screenshot displays the various types of allowed HTTP methods (GET, HEAD, POST, OPTIONS, TRACE), apart from other server-specific information (Server response, version details etc)
Burpsuite
From preliminary mapping and analysis to locating and taking advantage of application vulnerabilities. Burp Suite provides a platform for carrying out different security tests for online applications.
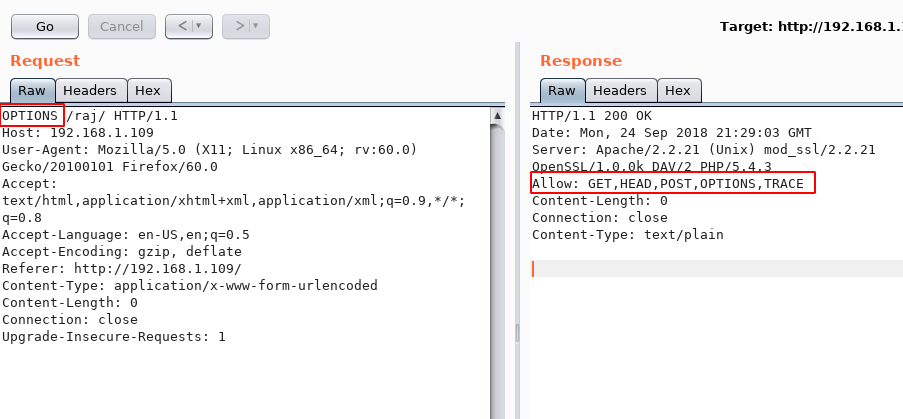
As we are aware that the HTTP OPTIONS method provides us with the most effective way to discover the different methods allowed on an HTTP server. So, let us capture the URL request in Burpsuite GUI and change the HTTP method type in the Request section to OPTIONS, as seen below.
As shown, the RESPONSE from the web server not only displays the list of HTTP methods allowed. However also highlights the server version details (Eg: Apache/2.2.21 (Unix) mod_ssl/2.2.21 OpenSSL 1.0.0/k DAV/2 PHP/5.4.3)
You can learn more about Penetration Testing by following this Link.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here

Hi,
Thanks for the well written article.
Looks like there is a typo :
For POST method:It is written that
“stored in the response body of the request and sent across to the server.”
I think this should be :
“stored in the body of the request and sent across to the server.”
Thanks!
Thank you for your valuable comment. We will take care about it.
Great
Cool, yeah…found its enabled in my server, Gunicorn…Looking for a way to disable it…:-)
hi.
Thank for your post its really helpfull.
Please tell me i need to test head access control bypass on nmap .
what are the commande for that
I have one question. While, you can list HTTP Options with using NC command, for some websites it is not possible to get the information with Nmap. What can be the reason? Thank you,