Linux for Pentester: xxd Privilege Escalation
In this article, we are going to make our readers familiar with another influential command i.e. “xxd” which assist for converting any hex dump to a binary and vice-versa. So, by knowing this certainty now we will check how wisely we can make it applicable in Privilege Escalation.
Note: “The main objective of publishing the series of “Linux for pentester” is to introduce the circumstances and any kind of hurdles that can be faced by any pentester while solving CTF challenges or OSCP labs which are based on Linux privilege escalations. Here we do not criticizing any kind of misconfiguration that a network or system administrator does for providing higher permissions on any programs/binaries/files & etc.”
Table of Content
Introduction to xxd
- Major Operation performed using xxd
Exploiting xxd
- SUID Lab setups for Privilege Escalation
- Exploiting SUID
Introduction to xxd
As we know whenever we want to convert any format of a file into another format then, we can grab that simply by using online converter which helps to convert a file into the desired format such as: “pdf to word, jpg to pdf, excel to pdf” etc. but what if someone desired to get any file into its hexadecimal form or binary??
So, in this article, I’m emphasizing the way through which one can easily get hex dump or binary format for any file. This can be achieved by one of Linux command i.e. “xxd”. The xxd command enables the user to generate a hex dump of a given file and can also reverse a hex dump back to its original ASCII form. This phenomenon can also help in the procedure of encoding and decoding any mysterious file.
First, we will check for its help/man command to identify how we can use xxd for this conversion.
xxd -h
By typing the above command, we can achieve a list of arguments that can be used with xxd for generating hex dump of a given file.
Major Operation performed using xxd
Converts file contents into hex: For instance, I’m creating a new file by the name of “secret.txt” and now I want to convert its whole content into the hexadecimal form so, I will type the below mentioned command to execute the desired output.
Syntax: xxd <options> filename
xxd secret.txt
By the below image it’s clear that xxd has generated the hex dump for the file “secret.txt”.
Here, we can observe the following hex dump are obtained its default format such as:
- Indexing the number of lines. (eg: 00000000, 00000010, 00000020…………00000220)
- The default number of octets per group is 2 (-e: 4 little-endian hexdump) which is groupsize of 4 bytes. (eg: 4967 6e69…………6e67)
- The standard column length is equal to 16 bits with whitespace. (eg: Ignite is Having)

Skip the nth line with xxd: While converting a file there may be lots of data that may not be of our use so, instead of obtaining whole data we can skip those contents that are needless (skip the no. of lines). For this, we can use xxd to skip the nth line and produce hex value after skipped lines.
Suppose in our circumstance we want to generate hex dump from line 5 ahead then this can be attained by using “-s” argument followed by xxd command.
xxd -s 0x50 secret.txt
To limit output up to particular length: As above I have explained how one can retrieve data by skipping no. of lines i.e. output from a specific line but, if we need to limit the length of standard output then we will use “-l” argument instead of “-s”.
Here I’m limiting the length of my contents to print the data up to limited range i.e. 5th line as shown in below screenshot.
xxd -l 0x50 secret.txt
Hence, we can observe the difference between both commands; the first command generates the hex value initialized from the 6th line and the second command ended with the 5th line as per hex indexing, take reference from the above screenshot.

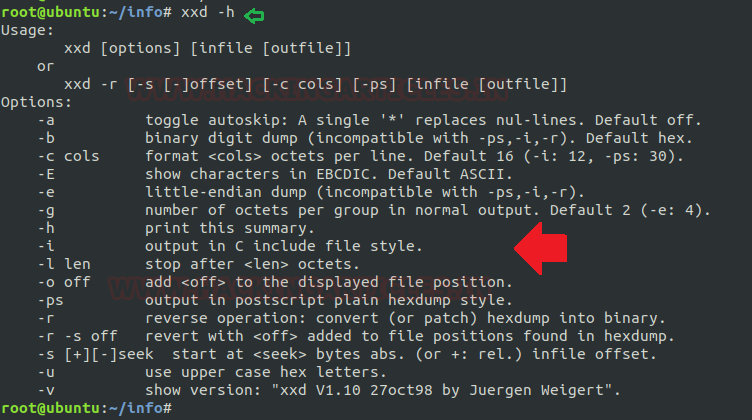
Converts file contents into binary: In above all image we have noticed that file has been dumped into its “hex form” but whenever we wish to produce the “binary form” for any file then we will use “-b” option. On using this option, the result will switch to its bit dump (binary digit) by grouping the output data into its octet using “1 or 0” rather than hex dump. To attain the same as per below image type command:
xxd -b secret.txt
Set column length: As above I have described how we can skip and limits the output up to range. Now I will illustrate how we can set column length. By default, it used to be 12, 16 for any dumped file but now I will explain what else we can do.
For this I’m taking three occurrences:
Default: As we know the default column length is 16. This will print 16 characters including whitespace.
xxd -l 0x20 secret.txt
Set the column length up to 32: I have set end index to limit printing data range by using “-l” option now after doing so I will set column length up to “32” which can be achieved by using “-c” argument.
xxd -l 0x40 -c 32 secret.txt
From the given below screenshot, we can easily realize how xxd has limits the column length.
Set the column length up to 9: As above, now I have set column length up to “9” by following the same process as discussed above.
xxd -l 0x40 -c 9 secret.txt
In all case, xxd has created the hex dump for a file by counting each character with whitespace.

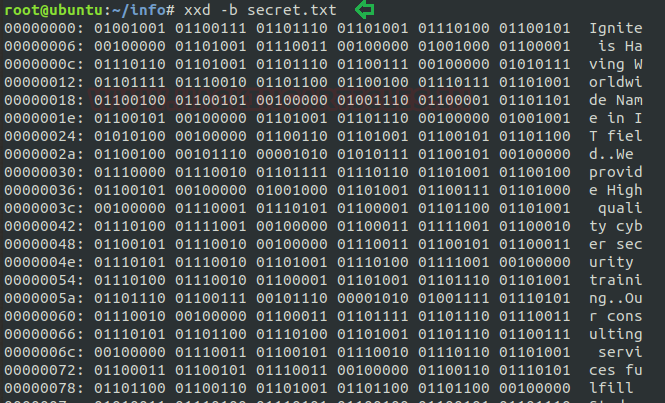
Print Plain hex dump style: The postscript option “-ps” is used only in case when we required our output in plain hex dump style. Here we have saved its output inside hex file to obtain the plain hexadecimal value of the secret.txt file. To ensure the result we have used the cat command to read output from hex file.
xxd -ps secret.txt > hex cat hex
From the below image, it can be cleared that how xxd has created plain hex dump style for file “secret.txt” by restricting the plain text.
To revert any file: To return any generated output into its original form we can use the “-r” option. In our case we have used “-r -p” to print the reverse output from plain hex dump style into its ASCII form.
xxd -r -p hex
Groupsize bytes: If we required to group the output into a number of octets then we can use the “-g” option for this purpose. By default, it is 2 (-e: 4 little-endian hex dump). So, if we set this value to 4 then it will be grouped into 8 bits.
In below screenshot, we have set this value to 8 which will group into 16 bits as desired output to concise the result.
xxd -l 0x30 -g 8 secret.txt

SUID Lab Setups for Privilege Escalation
The SUID bit permission enables the user to perform any files as the ownership of existing file member. Now we are enabling SUID permission on xxd, so that a local user can take the opportunity of xxd as the root user.
Hence type following for enabling SUID bit:
which xxd chmod u+s /usr/bin/xxd ls -al /usr/bin/xxd
Exploiting SUID
Now we will start exploiting xxd service by taking the privilege of SUID permission. For this, I’m creating a session of the victim’s machine which will permit us to develop the local user access of the targeted system.
Now we need to connect with the target machine with ssh, so type the command:
ssh test@192.168.1.103
As we know we have access to victim’s machine so we will use find command to identify binaries having SUID permission.
find / -perm -u=s -type f 2>/dev/null
Here we came to recognize that SUID bit is permitted for so many binary files, but our concerned is: /usr/bin/xxd.

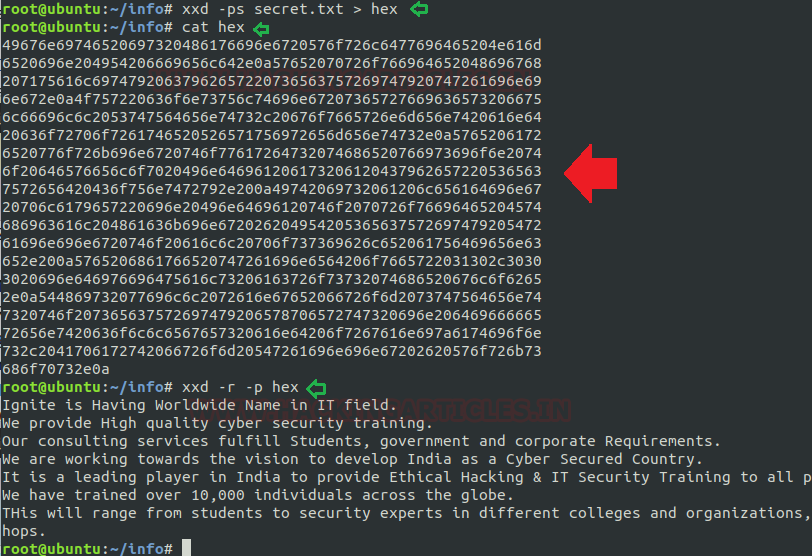
Taking privilege of SUID permission on xxd we are going to grab the shadow’s file for extracting password hash file.
In the below image first, I have requested to expose the /etc/shadow file by the use of xxd which will produce the hex dump for the file along with that I have piped the xxd command to revert its output.
xxd "/etc/shadow" | xxd -r
Now I have use john the ripper tool to crack the password hashes. By doing so we will get credential of the user as shown in below image.
john hash

Once we get the user’s credential then we can switch user. Here first we check sudo rights for user: raj and noticed that user “raj” has ALL privileges.
su raj sudo -l sudo su
Therefore, we switch to the root user account directly and access the root shell as shown in the image. Hence, we have successfully accomplished our task of using xxd command for Privilege Escalation.

Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here