Forensic Investigation: Windows Registry Analysis
In this article, we will learn how we can use RegRipper to analyze the windows registry in the forensic investigation environment.
Table of Content
Introduction to RegRipper
Creating a Registry Hives
SAM Hive
- Analyzing Log: SAM
- Analyzing Report: SAM
System Hive
- Analyzing Log: System
- Analyzing Report: System
Software Hive
- Analyzing Log: Software
- Analyzing Report: Software
Security Hive
- Analyzing Log: Security
- Analyzing Report: Security
Conclusion
Let’s begin the Forensic Investigation!!
Introduction to Regripper
RegRipper is an open-source tool, written in Perl. To extracting and parsing information like [keys, values, data] from the Registry and presenting it for analysis.
Its GUI version allows the analyst to select a hive to parse, an output file for the results. It also includes a command-line (CLI) tool called rip.
Rip can be pointed against a hive and can run either a profile (a list of plugins) or an individual plugin against that hive, with the results being sent to STDOUT.
Plugins are extremely valuable in the sense that they can be written to parse data in a manner that is useful to individual analysts.
To learn more about RegRipper click here.
We can download RegRipper for windows from here.
Creating a Registry Hives
A hive is a logical group of keys, subkeys, and values in the registry that has a set of supporting files loaded into memory when the OS is started or user login.
Each time a new user logs on a computer, a new hive file is created for that user with a separate file for the user profile hive.
A user’s hive contains specific registry information about user’s application settings, desktop, environment, network connections, and printers. User profile hives are located under the HKEY_USERS key.
We can learn more about Registry Hives from here.
Use these commands to save a copy of these Registry Hives [SAM, System, Software, and Security].
reg save hklm\sam c:\sam reg save hklm\system c:\system reg save hklm\software c:\software reg save hklm\security c:\security

After saving all these Hive files, we can launch the RegRipper software.
In the Hive file tab, we need to select the location where we saved our Registry hive file. In the Report file tab, select that location where we want our report and log file both saved. Then click on a rip button to get the report and log file.

Now let us learn about all this file information.
SAM Hive
SAM stands for the Security Account Manager is a database file in windows that stores user’s information. The user passwords are stored in a hashed format in a Registry hive either as an LM hash or as an NTLM hash. This file can be found in “%SystemRoot%/system32/config/SAM” and is mounted on HKLM/SAM.
In an attempt to improve the security of the SAM database against offline software cracking, Microsoft introduced the SYSKEY function in Windows NT 4.0. When SYSKEY is enabled, the on-disk copy of the SAM file is partially encrypted, so that the password hash values for all local accounts stored in the SAM are encrypted with a key.
Now, open RegRipper and select the location of the Hive file and Report file. Then click on the Rip! Button to start the Investigation process.

After some time, it will showcase the message on the screen that our work for this investigation process is completed with zero plugins completed with errors.

It will create two files one with logs of the investigation and Second with a Report of the investigation.
Analyzing Log: SAM
Now check the log file with this command.
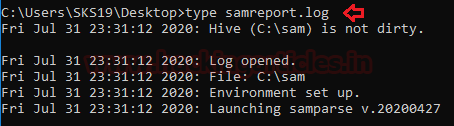
type samreport.log
It will only tell about the environment of this hive file.
Analyzing Report: SAM
Secondly now its Report time. we can access this file with the following commands.
type samreport.txt
As we can see in the below screenshot it will tell about SAM version and User information.

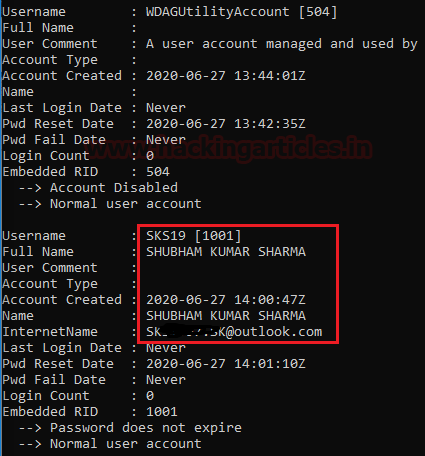
Now, as we can see the main user account got spotted with its major details like.
Username: SKS19 [1001] Full Name: SHUBHAM KUMAR SHARMA Account Created: 2020-06-27 14:00:47Z Name: SHUBHAM KUMAR SHARMA InternetName: S******.SK@outlook.com Pwd Reset Date: 2020-06-27 14:01:10Z Embedded RID: 1001
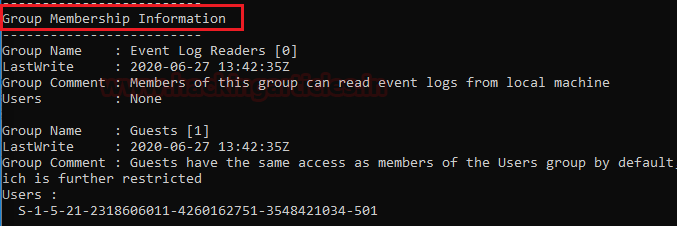
Next, we have spotted Group Membership Information. With its group name Guests and its details.
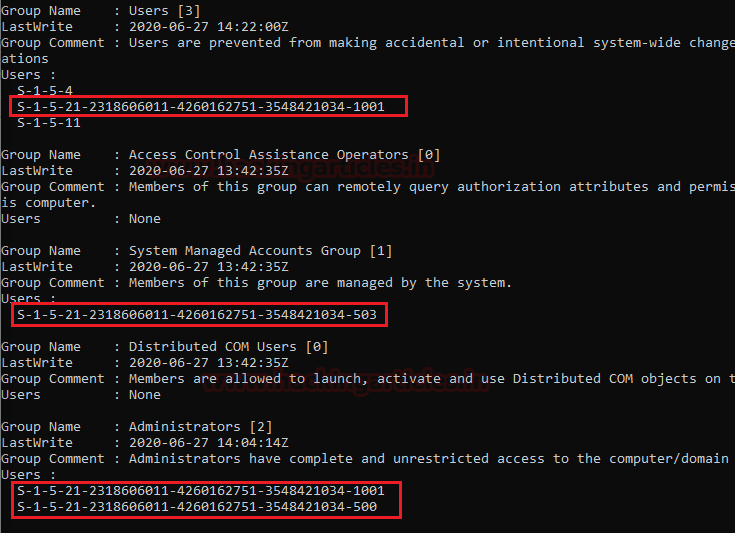
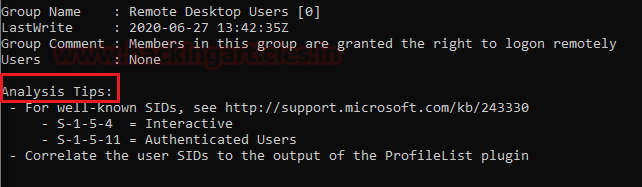
Some more group membership information, the group’s name like Users, System Managed Accounts Group, and Administrators. Their details revel Lastwrite, Group Comment, and Its Users.
Lastly, RDP and some Analysis tips which would be handy for us in the Investigation.
System Hive
The system hive file consists of all basic information regarding the system information. Now, repeat the same steps for RegRipper and select the location of the Hive file and Report file. Then click on the Rip! Button to start the Investigation process.
After some time, it will showcase the message on the screen that our work for this investigation process is completed with zero plugins completed with errors. As we mentioned earlier it will create two files: Log and Report.
Analyzing Log: System
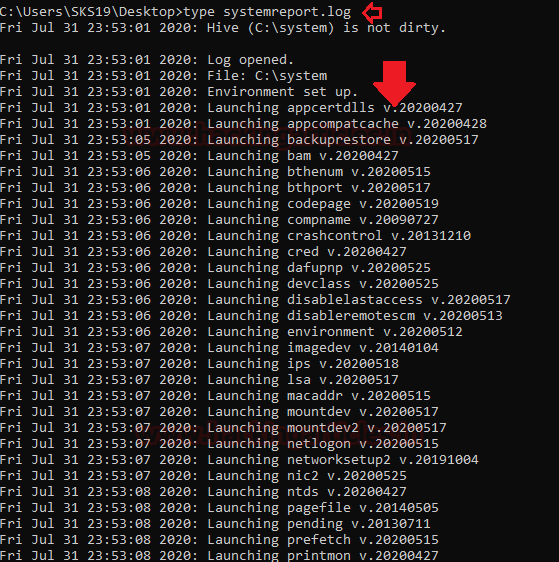
The first file is the log file regarding gathering information from that directory. After seeing the logs regarding system information.
type systemreport.log
Analyzing Report: System
we have opened its report with these commands.
type systemreport.txt
The below screenshot tells about all the software installed with their default directory along with its path.
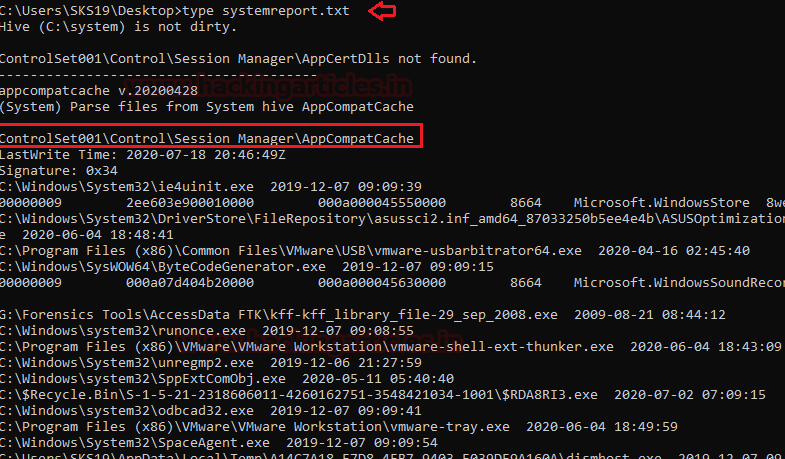
After that, we found out control set backups details in the victim’s system. Along with temp file details.

Now, this result is showing us about the HKLM [ HKEY_LOCAL_MACHINE] user’s BAM. It is a user-specific application.

Now it shows, Some device details, Computer name on diff-diff instances and crash control information.

Now the network media streaming devices connected with the system. In our case, it is from a Sony corporation. We can get along some interesting details with its hardware ID. It also gets some details regarding the connected USB devices no matter their currently connected or not.

After this, it will cover the hardware details along with NTFS disable the last access update. Like, ControlSet001\Control\Session Manager\Environment, Hardware details.

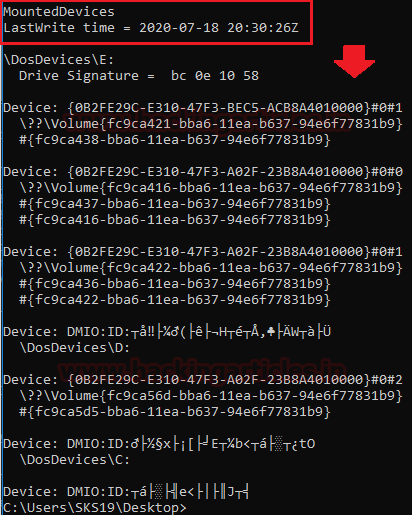
After this IP address and Domain name details with Hint. Analysis Tips and Mounted devices.

Now Finally in the System file, we got details regarding mounted devices details. It gets all details whether they are currently mounted or not.
Software Hive
Software Hive file consists, all the information regarding the software installed in this system.
Now, follow the previous steps for RegRipper and select the location of the Hive file and Report file. Then click on the Rip! Button to start the Investigation process.

After some time, it will showcase the message on the screen that our work for this investigation process is completed with zero plugins completed with errors.
Analyzing Log: Software
As usual, we opened the logfile first to check its log to understand through which file it is detecting to create an Investigation report for this file. Now run this command to view this file.
type softwarereport.log

Analyzing Report: Software
Now we need to view the report file of the software hive file. So, run this command to get this file.
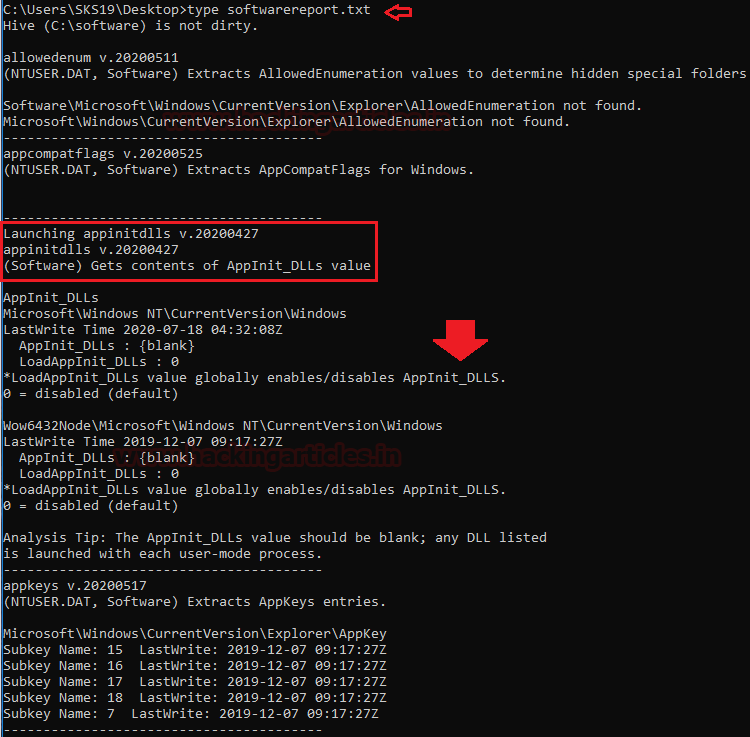
type softwarereport.txt
In this report, the first page shows details regarding AppInit DLLs values. AppInit DLLs is a mechanism that allows an arbitrary list of DLLs to be loaded into each user-mode process on the system.
The next page shows us the details regarding application details and the App Paths subkeys.

After this, it will showcase all the drivers regarding Input and output devices installed in the victim’s system. It will show us Bluetooth driver details and the system doesn’t have a webcam in the system.
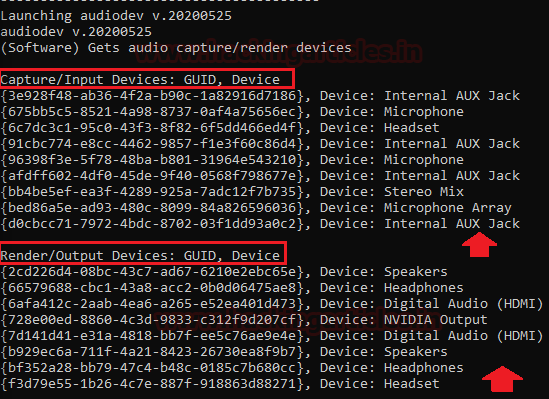
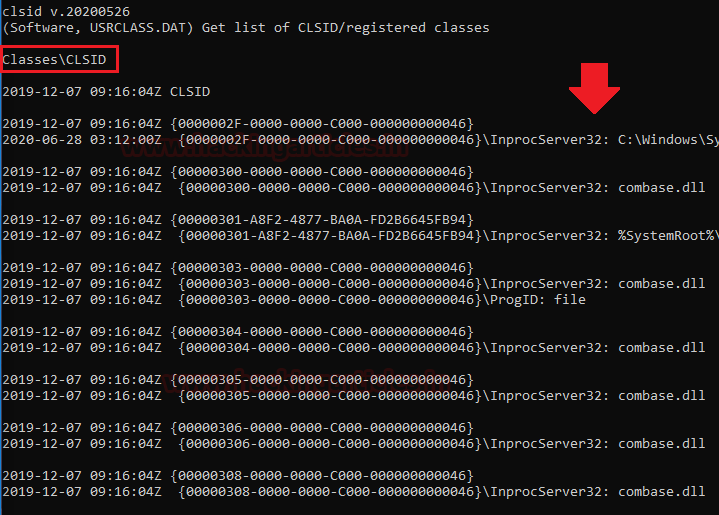
Last page of this report regarding the CLSID key. Where CLSID is a globally unique identifier that identifies a COM class object. If your server or container allows linking to its embedded objects, you need to register a CLSID for each supported class of objects.
The CLSID key contains information used by the default COM handler to return information about a class when it is running. The CLSID is a 128-bit number, in hex, within a pair of curly braces.
Security Hive
Security hive helps us to understand the security measures of the victim’s system in the Forensic Investigation process.
Now, follow the previous steps for RegRipper and select the location of the Hive file and Report file. Then click on the Rip! Button to start the Investigation process.

After some time, it will showcase the message on the screen that our work for this investigation process is completed with zero plugins completed with errors.
Analyzing Log: Security
Now we checked its log file to deeply understand our Investigation report. Run these commands to view the log file in the command prompt.
type securityreport.log
Analyzing Report: Security
To view, the security hive file report follows this command.
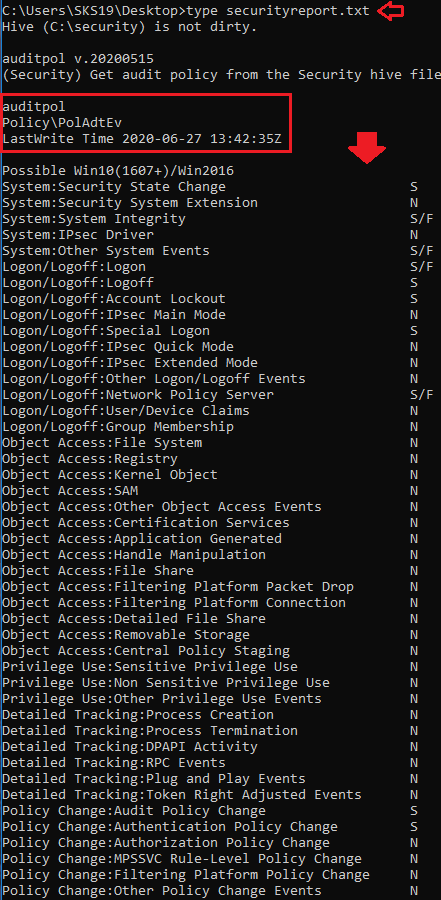
type securityreport.txt
This report page is all about the security hive file audit policy. An audit policy specifies account limits of one or multiple resources for a group of users.
This contains guidelines that establish policy limitations and workflows for processing breaches after they occur.
Where N means No audit, S means Success, and F means failure.
Conclusion
The Windows Registry is a hierarchical database that stores low-level settings for the operating system of Microsoft Windows and for programs choosing to use the registry. The register also offers access to counters for results in profiling systems. In other terms, on all models of Microsoft Windows operating systems, the registry or Windows registry contains information, settings, options, and other values for programs and hardware installed.
These details can be extracted with RegRipper to get a better result in the Forensic Investigation.
Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact Linkedin and twitter.