Forensic Investigation: Shellbags
In this article, we will be focusing on shellbags and its forensic analysis using shellbag explorer. Shellbags are created to enhance the users’ experience by remembering user preferences while exploring folders, the information stored in shellbags is useful for forensic investigation.To learn more about Cyber Forensics. Follow this Link
Table of Contents
- Introduction
- Location of shellbags
- Forensic analysis using Shellbags Explorer
- Active Registry Analysis
- Offline Registry Analysis
Introduction
Microsoft introduced Windows Shell Bags into the Windows 7 operating system, and they remain present on all later Windows platforms. Shellbags are registry keys that improve user experience and recall user preferences whenever needed. The user’s exercises create shellbags.
As a digital forensic investigator, you can use shellbags to prove whether a particular user accessed a specific folder. You can even check whether someone created the specific folder or whether it was available. You can also find out whether someone accessed external directories on external devices.
For the most part, Shell Bags hold data about the user’s activities while exploring Windows. This implies that if the user changes icon sizes from large icons to the grid, the system updates the settings in Shell Bag instantly. When you open, close, or change the review option of any folder on your system, either from Windows Explorer or from the Desktop, even by right-clicking or renaming the organizer, the system creates or updates a Shellbag record.
Location of shellbags
Windows XP
The shellbags for Windows XP are stored in NTUSER.DAT
- Network folders references:\Software\Microsoft\Windows\Shell
- Local folder references: \Software\Microsoft\Windows\ShellNoRoam
- Removable device folders: \Software\Microsoft\Windows\StreamMRU
Windows 7 to Windows 10
Shellbags are a set of subkeys in the UsrClass.dat registry hive of Windows 10 systems. The shell bags are stored in both NTUSER.DAT and USRCLASS.DAT.
- NTUSER.DAT: HKCU\Software\Microsoft\Windows\Shell
- USRCLASS.DAT: HKCU\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell
The majority of the data is found in the USRCLASS.DAT hive-like local, removable, and network folders’ data. You can manually check shellbags entry in the registry editor like so. In the following screenshot, a shellbag entry for a folder named jeenali is shown.

The Shellbag data contains two main registry keys, BagMRU and Bags
- BagMRU: This stores folder names and folder path similar to the tree structure. The root directory is represented by the first bagMRU key i.e. 0. BagMRU contains numbered values that compare to say sub key’s nested subkeys. All of these subkeys contain numbered values aside from the last child in each branch.
- Bag: These stores view preference such as the size of the window, location, and view mode.
We will be analyzing the shellbags using the shellbag explorer.
- ShellBags explorer(SBECmd)
- Shellbags explorer (GUI version)
Shellbags explorer is a tool by Eric Zimmerman to analyze shellbags. The shellbags explorer is available in both versions cmd and GUI. You can download the tool from here.
Forensic Analysis of Shellbag
Analysis using SBECmd
Here we are using the SBECmd.exe (Cmd version of the shellbag explorer tool) by Eric Zimmerman. This cmd tool is great for command prompt lovers who prefer using commands over GUI.
To get a clear idea about how shell bags work and store data and how you can analyze it I have created a new folder named “raaj” which consists of a text document. Further, we will be renaming it to geet and then to jeenali. Let’s analyze the shellbags entries for this.
Run the executable file and browse to the directory where the executable is present. To extract the shellbags data into a .csv file use the following command:
SBECmd.exe –l --csv ./
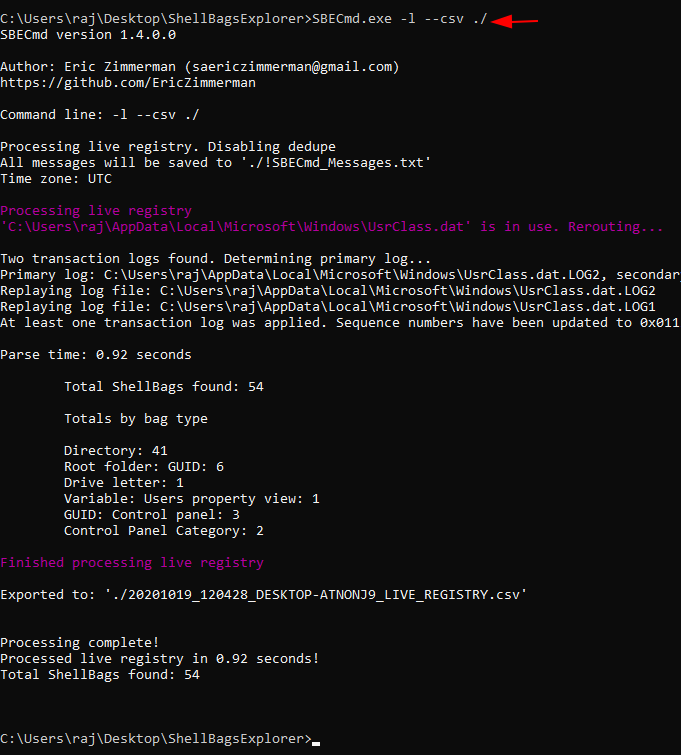
As a result of the above command, a .csv file will be created in the directory.

Lets’ open the .csv file and analyze it.

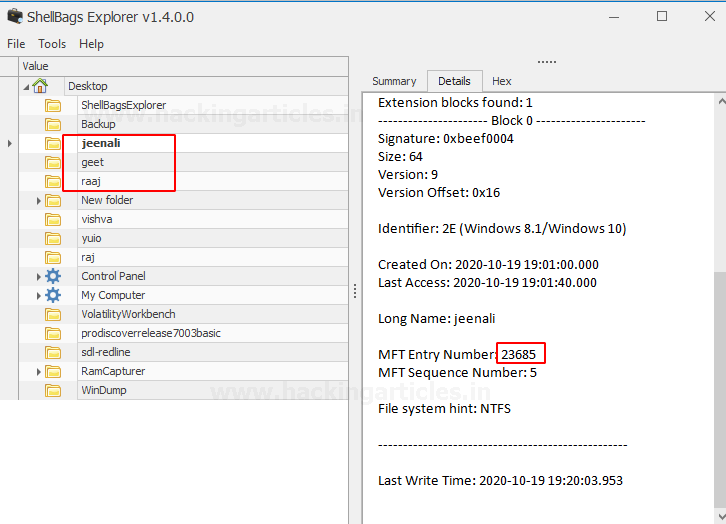
As I mentioned earlier, we renamed the folder named “raaj” to “geet” and then to “jeenali.” As highlighted in the screenshot, the MFT entry number is the same for all three folders, which shows that we renamed the folder.
- Shellbags explorer (GUI version)
Active Registry Analysis
Using the shellbags explorer we can also analyze the active registry. Select load an active registry which will load the registry in use by the active user.

They successfully parse the shellbags from the active registry.

The shellbags parse contains the shellbags entries created based on users’ activities. As depicted earlier the folder renamed will have a similar MFT entry number. Here, I have created a folder named “raaj” and we will be further renaming it to “geet”.

Whenever a folder is renamed an entry is stored in shellbag, the MFT entry number of both the folder will be the same.

Now, once again rename the folder to jeenali. The MFT entry will be similar to the previous one.

Offline registry analysis
For offline analysis, we first have to extract the shellbags file which is USRCLASS.DAT. Let’s extract the shellbag file using FTK imager. Download FTK imager from here.
Lets’ add in the evidence, go to the add evidence item.

Select the source for adding evidence as here I have selected the logical drive as usrclass.dat is present in the C drive.

Next, select the desired user drive. Click Finish.

Expand the window to the location of the usrclass.dat. Select the user you want to investigate go to the following path to extract the UsrClass.dat.
root > users > administrator >Appdata>Local>Microsoft>windows

We will be analyzing the usrclass.dat extracted from the above step using shell bag explorer by Eric Zimmerman.
As we have exported the registry hives we will choose “load offline hive”
After successful parsing of the extracted shellbags file, you will be able to see the entries for folders browsed, created, deleted, etc. Here is the entry of the folders renamed earlier, the MFT entry number is the same for the three folders.
Now here, I have deleted the folder named “jeenali”. Now lets’ check the shellbags data whether the deleted folder still exists or not.
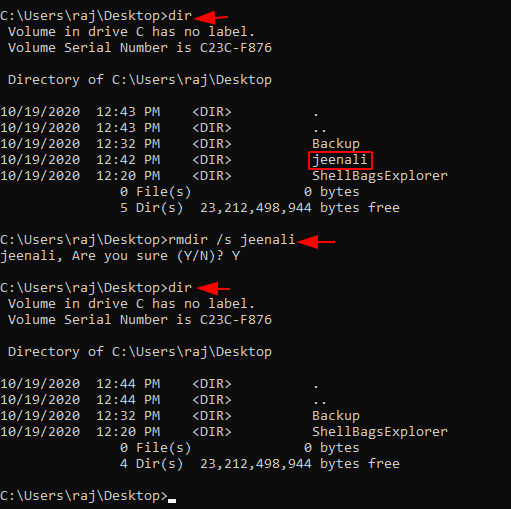
Yes, the shellbags store the entry even though someone deleted the folder later.

Shellbags stores the entries of the directories accessed by the user, user preferences such as window size, icon size. Shellbags explorer parses the shellbags entries shows the absolute path of the directory accessed, creation time, file system, child bags. The tool classifies the folders accessed according to the location of the folder. Users create Shellbags for compressed files (ZIP files), command prompt, search window, renaming, moving, and deleting a folder.
To learn more about Cyber Forensics. Follow this Link
Author: Vishva Vaghela is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
Very useful, thank you for the post.