Credential Dumping: Wireless
Today we will be taking a look at how we can dump Wireless Credentials. We will cover Credential Dumping, Red Teaming, Different ways we can get those pesky wireless credentials.
Table of Content
- What is Credential Dumping?
- Credential Dumping in Real Life
- Credential Dumping Methods
- netsh
- WirelessKeyView
- Wifi Network Properties
- LaZagne
- Mimikatz
- Metasploit Framework
- Mitigation
What is Credential Dumping?
When people in the cyber world use the term password cracking, they use it as a broad concept that covers all methods related to attacking, dumping, or retrieving passwords of a victim or target. However, in this article, we will solely focus on a technique called Credential Dumping.
Additionally, people describe Credential Dumping as a technique for extracting usernames and passwords of any login account from the target system. This technique allows an attacker to get credentials of multiple accounts from one person. Moreover, these credentials can include anything, such as bank accounts, email accounts, social media accounts, or wireless networks.
Credential Dumping in Real Life
When an attacker has access to the target system and through that access, they successfully retrieve the whole bunch of their credentials. Once you are inside the target’s system, there are multiple methods to retrieve the credentials of a particular thing. For instance, to redeem all the names and passwords of the wireless networks to which the operating system has connected, there are various methods that an attacker can use and we will try and cover all of those methods here in our article. Now another thing to focus on is that both internal penetration testing and external penetration testing can perform this dumping of credentials. The methodology, perspective, or subjectivity of the attack determines which method is the best suitable.
Credential Dumping Methods
Just like the instance presented above, we will portray various methods to dump wireless credentials from a system in this article. So, let’s get started, shall we?
Manual Credential Dumping
All the Wi-Fi password with their respective SSID are stored in an XML file. The location of these files is C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\***. Here, you will find that SSID of wifi is saved in clear text whereas passwords are stored as keys.
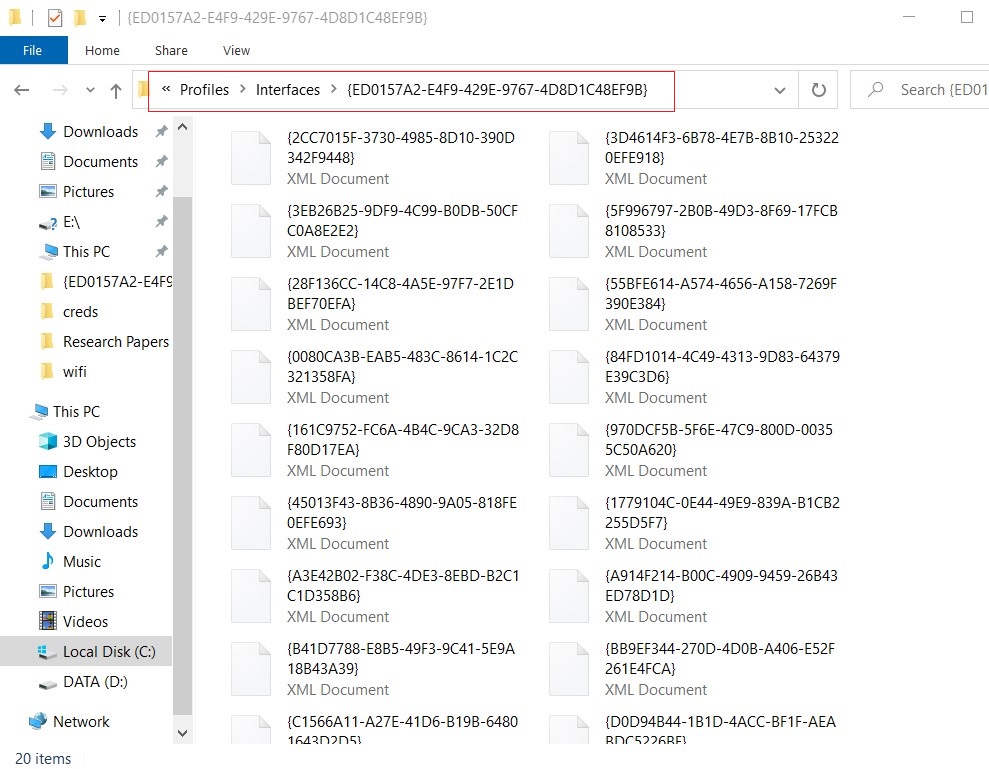
Credential Dumping using netsh
Netsh is a scripting utility provided by Microsoft itself. You can use it both in command prompt or Windows PowerShell. Netsh is short for network shell. When you execute it, it provides detailed information about the configuration of the network that the system ever had; including revealing the credentials of wireless networks that it has ever been connected to. This utility comes with various parameters that you can use to get various information as per the requirement. You can use this method both in internal and external penetration testing as you can execute netsh commands both locally and remotely.
To get the list of the SSIDs that the device has been connected to use the following command:
netsh wlan show profiles
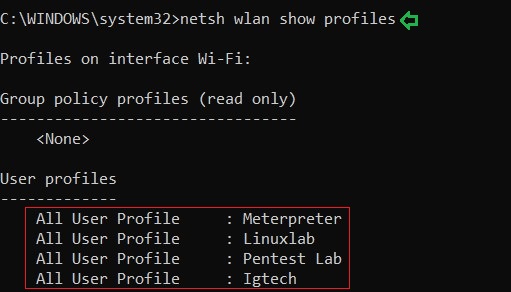
And as a result of the above command, you can see the names of the Wi-Fi networks that the system connected to in the past or present such as Meterpreter, Linuxlab, etc. The image above demonstrates the same.
Further, to know the passwords of any one of the mentioned SSIDs use the following command :
netsh wlan show profile name=<SSID Name> key=clear

And just like it is shown in the image above, the result of the above command will give you the password.
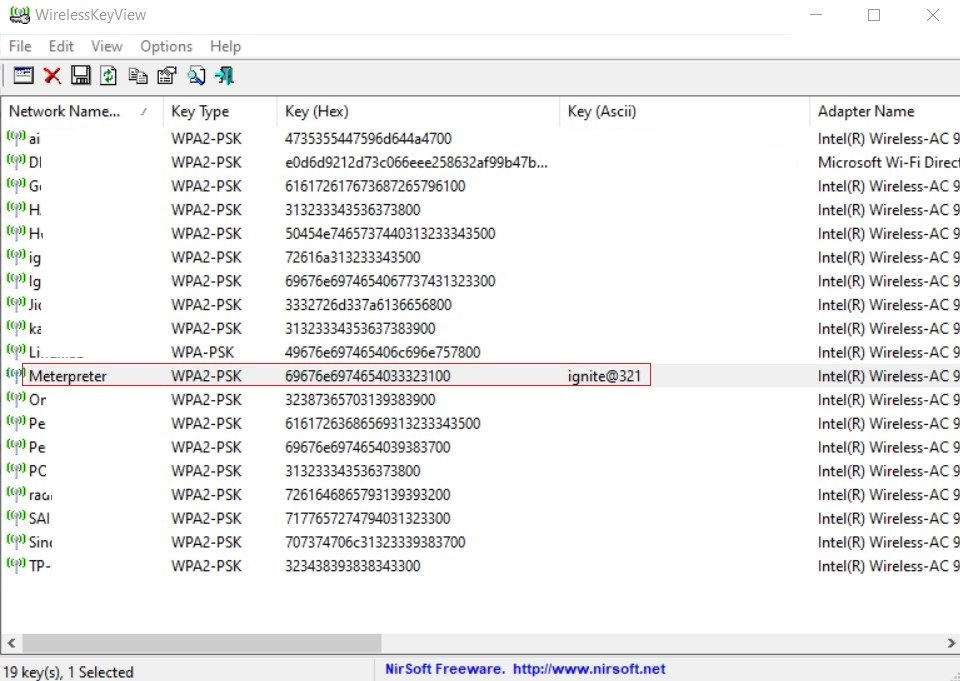
Credential Dumping using WirelessKeyView
A wireless key view is a simple software accesses the XML files where wireless passwords are stored and reveals them in cleartext. This tool was developed to recover lost and forgotten password of a wireless network. This is the perfect method for credential dumping in internal network penetration testing. To utilize this method simply download the tool from here and run it, you will get all the Wi-Fi names and its password as shown in the image below:
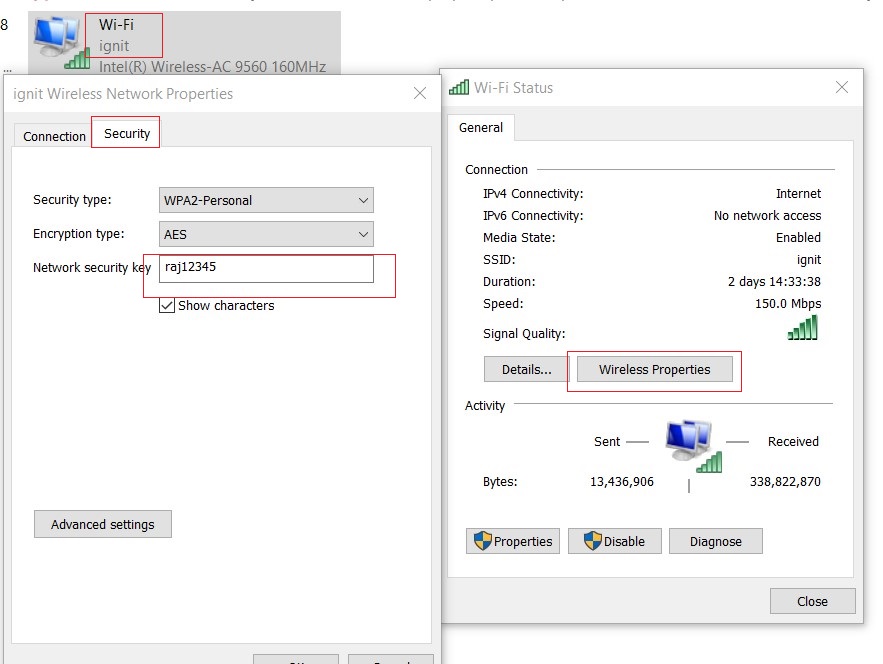
Credential Dumping using Wifi Network Properties
Our next method is manual, it is good when you are introduced to the network to work but for some reason, the password of the network isn’t revealed to you. Then you can use this method, as it falls under the category of internal penetration testing methodology. To reveal the password of a wireless network manually, go to Control Panel > Network and Internet > Network and Sharing Center and then click on Wi-Fi (*SSID*). A dialogue box will open, in that box click Wireless Properties button in the upper pane. Next, go to Security tab and you can see the password there just as it is shown in the image below:
Credential Dumping using LaZagne
LaZagne is an open-source tool that developers created to retrieve all the passwords stored in your machine. We have covered LaZagne in our other article, which you can read from here. In our experience, LaZagne is an amazing tool for credential dumping and it is the best tool to use for external penetration testing. To extract Wi-Fi password with LaZagne, simply download the tool from here and run it remotely using it following command :
lazagne.exe wifi

After running the above command, all the Wi-Fi-related passwords with their respective SSID will be extracted.
Credential Dumping using Mimikatz
Another method that can be very useful in external penetration testing is using Mimikatz. We have covered various features of Mimikatz in our other article, which you can find here. Once you have the victim’s session use the following commands to get the passwords:
getsystem load kiwi wifi_list_shared

And very easily you will have all the passwords at your service as shown in the image above.
Credential Dumping using Metasploit Framework
Then our next method is to use Metasploit to retrieving desired passwords. As all of us know that Metasploit is a framework that provides us with already constructed exploits to make pentesting convenient. And is an amazing platform for a beginner and expert in hacking pentesting world.
Now, to dump credentials there comes an in-built post exploit in the Metasploit and to run the said exploit; go to the terminal of Metasploit by typing msfconsole and get the session of you to the target system using any exploit you prefer. And then background the session use the post-exploit for extracting desired Wi-Fi credentials by using the following commands:
use post/windows/wlan/wlan_profile set session 1 exploit

And just as it is shown in the image above, you will have your credentials.
Mitigation
There are various measures that you can follow in order to protect yourself from credential dumping attacks. These measures are given below:
- Keep you employees/employers aware
- DO NOT use default SSID of a wireless network
- Do not save the passwords on the system
- Always reconnect to a Wi-Fi manually.
- Have a different network for guests
- Use VPN
- Change your Wi-Fi password regularly
- Use a different IP address instead of the default one
- Make sure your modems don’t have reset button as most of the modems come with the reset button. When the said button is pressed, it brings back the default settings which doesn’t have any security layer and allows anyone to connect.
So, these were the methods to dump wireless credentials. Apply the suggested mitigation to your systems or networks in order to keep yourself safe from attackers. I hope these were useful and keep tuning in for various hacking techniques!
We are well aware these are tough times for everyone and, we, here at hacking articles hope and pray that everyone is safe and following the measure of self-quarantine. And for all the hacking/pen-testing enthusiasts we are working hard to bring more and more new content so that you can learn new things and use this self-isolation to its best. Stay Safe and take care! Happy Hacking!
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here

Great article! What was the method for Mac or Linux?
Thanks
Good one.
you are missing the link to download lazagne tool