Credential Dumping: Clipboard
In this article, we learn about online password mangers and dumping the credentials from such managers via clipboard. Passwords are not easy to remember especially when passwords are made up of alphanumeric and special characters. And these days, there are passwords for everything. And keeping the same password for every account is insecure. Therefore, we have many password managers such as KeePass, bitswarden and many others that help us save all of our passwords.
Table of Content
- PowerShell Empire
- Metasploit Framework
- Koadic
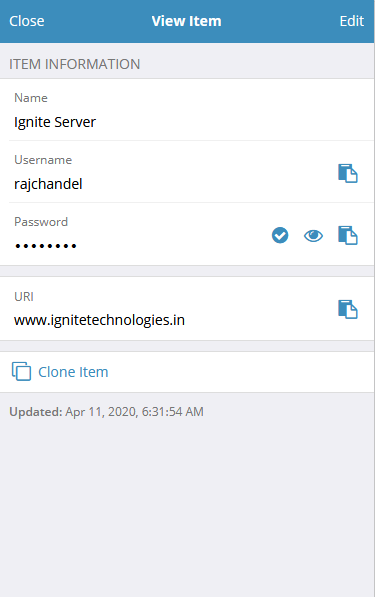
In our practical, we have used bitswarden password manager to keep our password secure. It’s feasible to use and even if we forget our password, we can just copy it from there and paste it where we require it. As you can see in the image below, we have saved our password in bitswarden. And we copy it from there.
PowerShell Empire
Additionally, if someone copies these credentials, you can retrieve them using various methods. PowerShell Empire has such a module; after having a session through the empire, use the following commands to execute the module:
usemodule collection/clipboard_monitor execute
Finally, once you execute the module, the copied password will paste as shown in the image below:

Then those credentials will be displayed in the console as shown in the image below:

Meterpreter Framework
In Metasploit, when you have a meterpreter session, it provides you with a different set of commands. One of those commands is load extapi, this command opens a door to various features of meterpreter session. You can view all of these features using a question mark (?). Extapi includes clipboard management commands as a feature. We will use a clipboard management command through extapi to dump the credentials that you can copy to clipboard. For this, type:
load extapi clipboard_monitor_start

And as you can see in the image above, we have username and password through clipboard management command.
Koadic
Just like PowerShell empire, Koadic has an inbuilt module for dumping the clipboard data. Once you have a session in koadic, type the following commands to get the clipboard data:
use clipboard execute

And this way, again, we have the credentials.
Conclusion
Credential Dumping via Clipboard is a powerful yet stealthy technique that attackers can use to extract sensitive information from compromised systems. Understanding this method is crucial for defenders, as it highlights a critical weakness that can be exploited if clipboard data is not properly secured. By implementing stricter clipboard policies, monitoring clipboard activity, and educating users about this threat, organizations can significantly reduce the risk of credential theft through clipboard dumping.
To learn more on Credential Dumping. Follow this Link.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here

