Get Meterpreter Session Alert over slack
You’re going to learn ShellHerder in this post. It is a technique used to monitor all the sessions of Metasploit/Meterpreter. The basic idea to create it, that new incoming sessions could be easily monitored when Intruder cannot access the listener. This approach is quite helpful when a Pen-tester wants to get an alert for live phishing campaigns or another attack by monitoring for new sessions.
Table of Content
Introduction to ShellHerder
Registering on Slack
- Add WebHooks App
- Configure WebHooks App
Download & Configure ShellHerder
Working Demo
Introduction to ShellHerder
ShellHerder uses session subscriptions to monitor activity and then sends an alert to Slack using Slack’s Incoming WebHooks. The alert is sent using the WebHook URL and a POST request and will tag a specified username and provide the computer name of the server with the session.
Registering on Slack
We need a workspace on slack to use slack. To do this we need to register on slack. To create a new workspace on slack, click here. This will require an email address. After that, it is required to create a channel. Here, we named our channel “live server”.
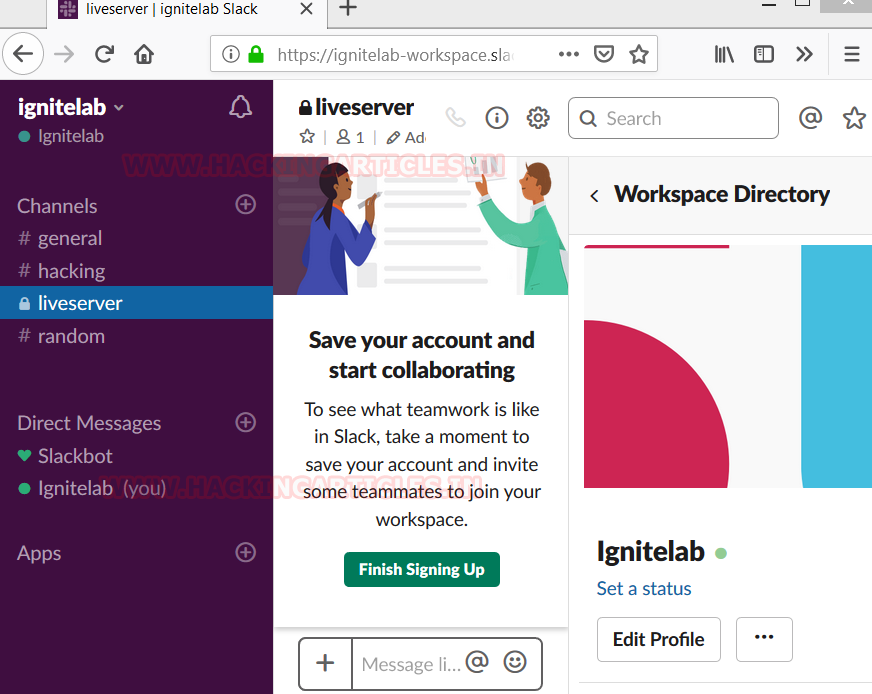
Add WebHooks App
To receive the updates from the Metasploit, we need to an app installed in the channel. Webhooks is the app that is perfect for this job. Now in order to add Webhooks, we first clicked on the Add an app Button inside our channel. Now, we will search for incoming Webhook and add it.
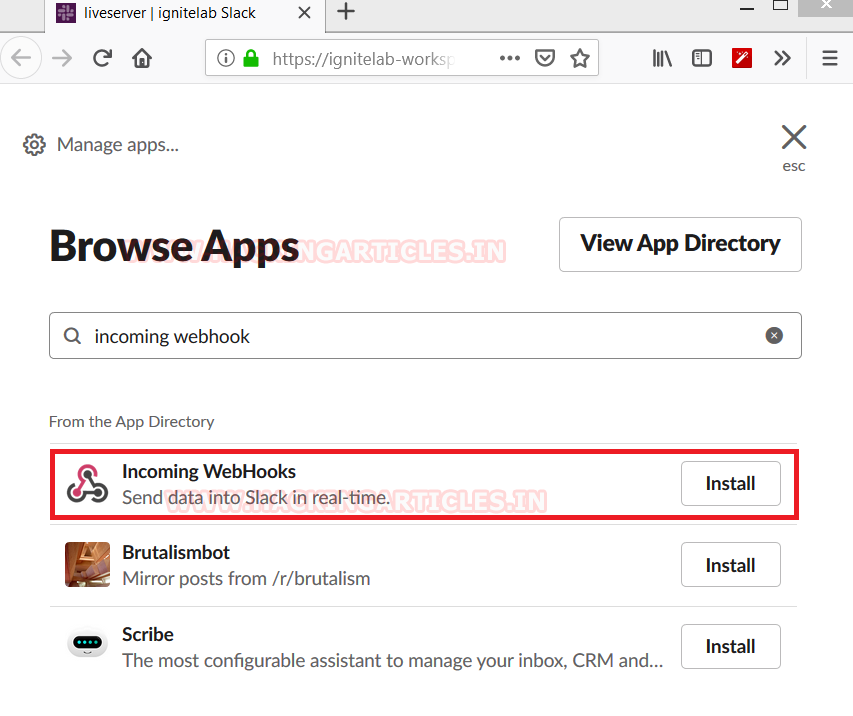
Configure WebHooks App
After adding the Webhooks, we will be asked to configure some settings for the app. This will include the configuring the channel on which the incoming notifications will be broadcasted. Here we select our channel and click on the Add Integration Button.

After clicking the Add integration button, we will be presented with the WebHooks URL. Copy this URL, we are going to need it while we configure Notify.

Download & Configure ShellHerder
Now, we need to work upon our Kali Linux. We are going to use Shell Herder to connect to slack. This Metasploit plugin is aimed to keep an eye on the sessions. All including the ones which are opened or closed. It uses session subscriptions to monitor activities and can be linked to slack, which we just got setup.
git clone https://github.com/chrismaddalena/ShellHerder.git

After downloading Shell Herder via git clone, we moved the directory inside the Metasploit Framework. So that we can use it directly inside the Framework. After copying the directory, we open an instance of the Metasploit Framework and load the notify plugin as shown in the image given image.

Now, we will use the command notify_show_options to check for any pre-configured settings. Now that we can’t find any. It was time to set the Webhook URL, which we copied earlier and add it inside the notify plugin. Also, we set the Slack User id and Source. After entering the relevant data, use the save command to save the configuration. Now that we have configured the Notify, Let us send a test message to see if the configuration is correct and working.
load notify notify_show_options notify_set_webhook <Above webhook URL> notify_set_user @Ignitelab notify_set_source Kali-Linux notify_save notify_test

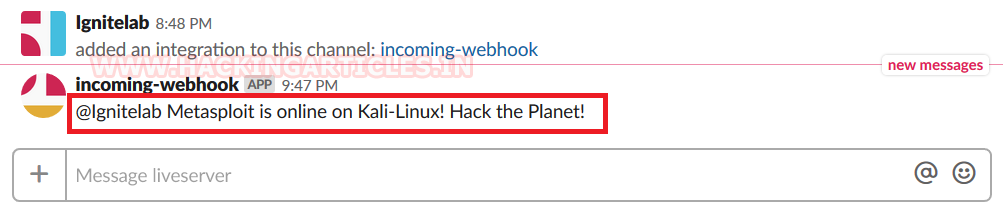
As we can see in the given image that, the slack received the test message we sent via Notify.
Working Demo
Now, to test the real working of Notify, we will exploit a machine, so that we can observe, whether or not it will notify us, when we get a session. We are exploiting a Windows machine using web delivery.
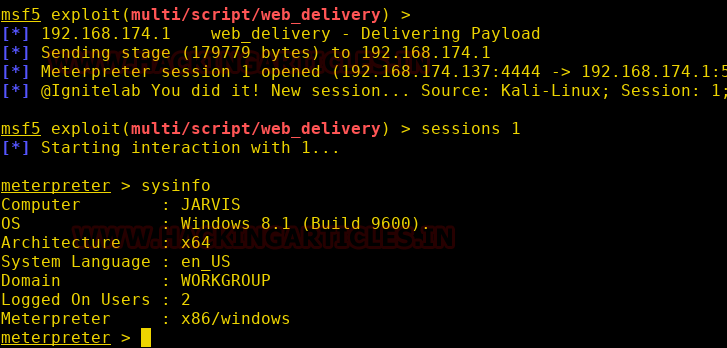
As we expected, we got the notification on our slack channel, as soon as we got the session.

Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here
i am not understanding
Great, i did it.
{*] Started reverse TCP handler on 0.0.0.0:443
[*] Sending stage (73735 bytes) to 10.9.0.1
[*] Meterpreter session 1 opened (10.9.2.30:443 -> 10.9.0.1:25020) at 2020-07-08 02:53:50 -0400
[*] @pentester You did it! New session… Source: Kali-Linux; Session: 1; Platform: android; Type: meterpreter
meterpreter >
[*] 10.9.0.1 – Meterpreter session 1 closed. Reason: Died
[*] @pentester You have made a huge mistake… Source: Kali-Linux; Session: 1; Reason: meterpreter is shutting down – Died
Thanks…