unknowndevice64 v2.0: Vulnhub Walkthrough
Today we are going to take on another boot2root challenge “uknowndevice64 v2.0” by Ajay Verma. Our goal is to get root and read flag.txt with at least two different ways.
Download it from here: https://download.vulnhub.com/unknowndevice64/unknowndevice64-V2.0.ova
Difficulty: Beginner
Penetrating Methodology:
Scanning
- Netdiscover
- NMAP
Enumeration
- Web Directory search
- Credential harvesting
Exploiting
- SSH login (1st Method)
- ADB login (2nd Method)
Privilege Escalation
- Exploit sudo rights
Capture the Flag
Walkthrough
Scanning:
Let’s start off by scanning the network and identifying host IPs. We can identify our host IP as 192.168.1.22 by using netdiscover. Next, we have to scan this IP using nmap.
netdiscover nmap -p- -A 192.168.1.22
The result shows that freeciv is running on port 5555, ssh is running on port 6465 and netbus is running on 12345.
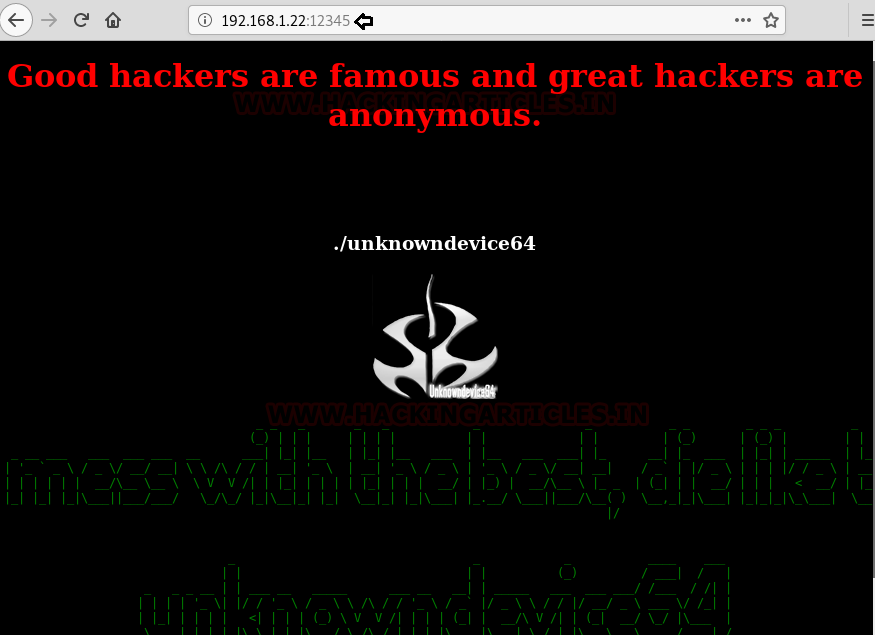
First, we try to open the IP into browser with port 12345 we were prompted to login. So, we tried the basic credentials with different combinations and got succeeded with ‘Administrator’ as username and password as ‘password’.

After logging in, a webpage appeared as you can see here. But nothing of our use.
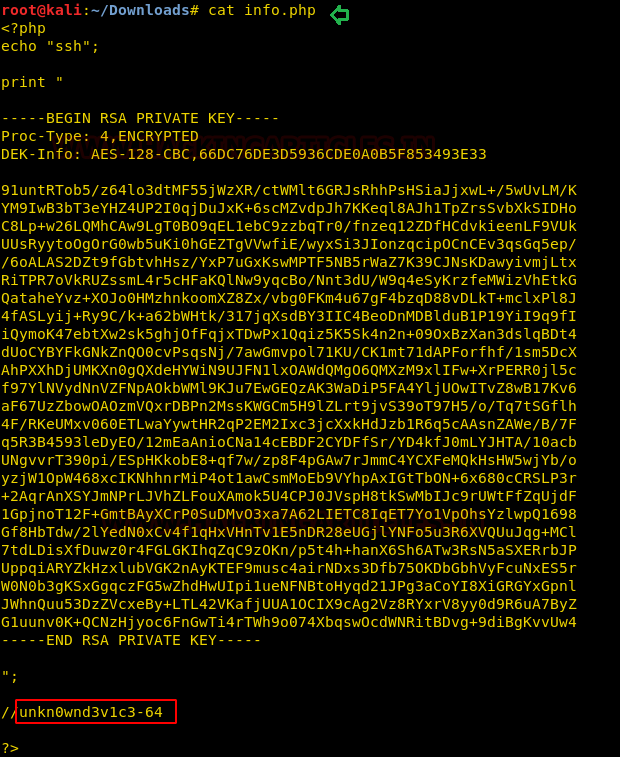
Then tried to access the robots.txt file. We got lucky and found a file here named ‘./info.php’ inside it.

When we opened this in the browser, we are prompted to download it.

When we open this downloaded file, we got an SSH private key inside it. So, we copied the text from “BEGIN RSA PRIVATE KEY” to “END RSA PRIVATE KEY” and saved it in a file named ‘sshkey’. Besides this key we can see “unkn0wnd3vic3-64” at the end of the file, let’s save this as of now.
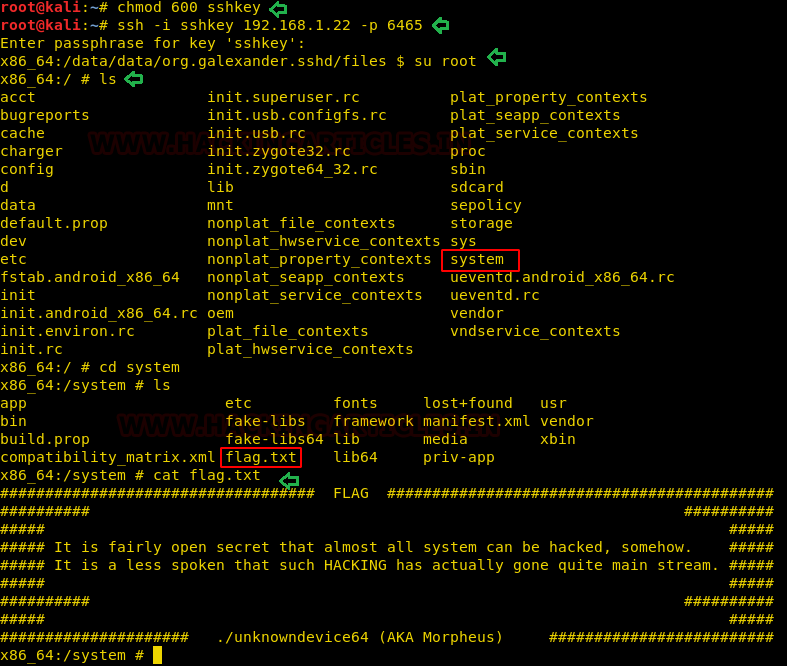
Here first we have changed permission for the file ‘sshkey’. Then login into ssh using this file on port 6465(as ssh is running on port 6465). And we are asked to enter a passphrase for this ssh key.so we used the text “unkn0wnd3vic3-64” that we saved from info.php and it worked. After that, we switched as root user and listed the content of root.
chmod 600 sshkey ssh -i sshkey 192.168.1.22 -p 6465 su root ls
We spotted a directory named ‘system’ and inside system, we found a file ‘flag.txt’. This is our flag!
Another way
We will be using previously gained information to save time. As we knew from Nmap scan that freeciv is running on port 5555 so tried to connect it with adb. After getting a shell, we switched to root and captured the flag (as we already knew the flag is inside flag.txt within system directory).
abd connect 192.168.1.22:5555 abd shell su root cat system/flag.txt
Finally!! The challenge is completed, and we have grabbed the flag.txt file using two different approaches.

Author: Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Ignite Technologies as a Security Analyst. Connect with her here